在 SRX300 服务网关上配置具有主动/备用互联网连接的 SD-WAN
要求
此示例使用以下硬件和软件组件。
一台 SRX300 系列设备(320、340、345、380)
一个用于 SRX300 系列的 Wi-Fi MPIM
一个用于 SRX300 系列的 LTE MPIM
一张订阅数据服务的SIM卡
Junos OS 19.4R1
概述
在此示例中,我们将设置分支机构 SRX320 系列设备,为现场员工提供有线和无线互联网和内联网访问,以及对访客设备的无线互联网访问。主互联网链路通过以太网,而备用连接通过LTE网络。这两个链路配置为主动/备用模式,除非主链路关闭,否则不会通过 LTE 调制解调器路由任何流量。
拓扑
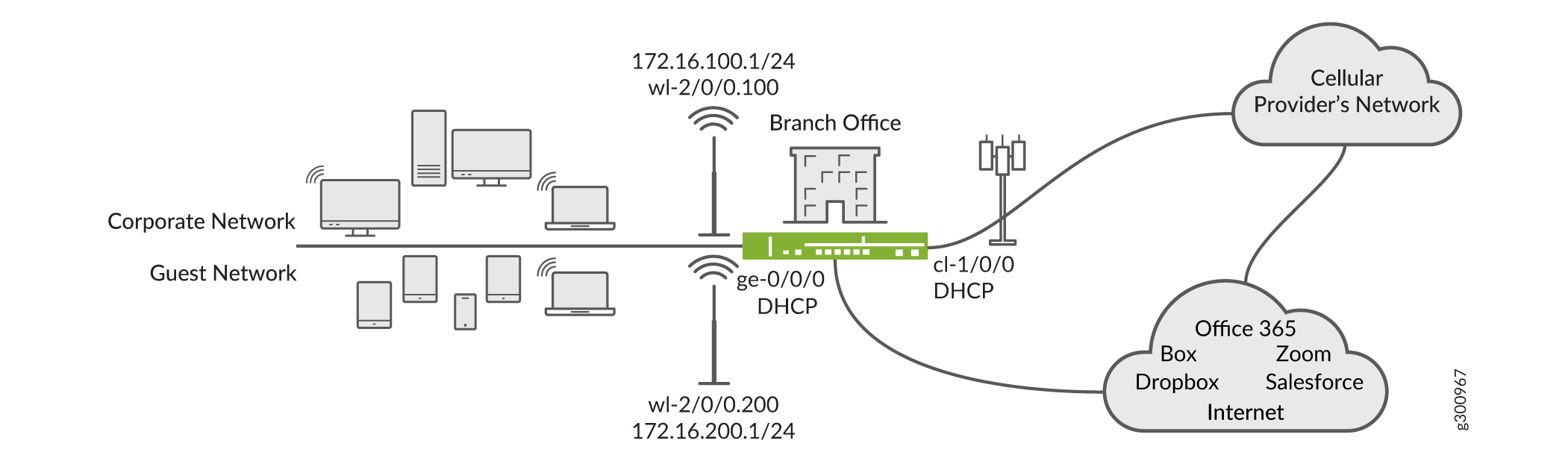
示例的拓扑如图 1 所示。LTE Mini-PIM 安装在插槽 1 中。WI-FI 小型 PIM 安装在插槽 2 中。SIM 卡安装在 LTE 模块的插槽 1 中。主链路连接到接口 ge-0/0/0,并从其连接的设备接收其 IP 地址、网络掩码、默认网关和 DNS 服务器。调制解调器具有接口cl-1/0/0。
PDP 上下文在接口 dl.0 上终止,与 ge-0/0/0 类似,IP 地址、网络掩码和默认网关由 GGSN/PGW 分配。Wi-Fi 接口为 wl-2/0/0.200,为访客网络提供服务,而接口为 wl-2/0/0.100 为企业网络提供服务。安全区域和每个区域的接口列表如图 2 所示。
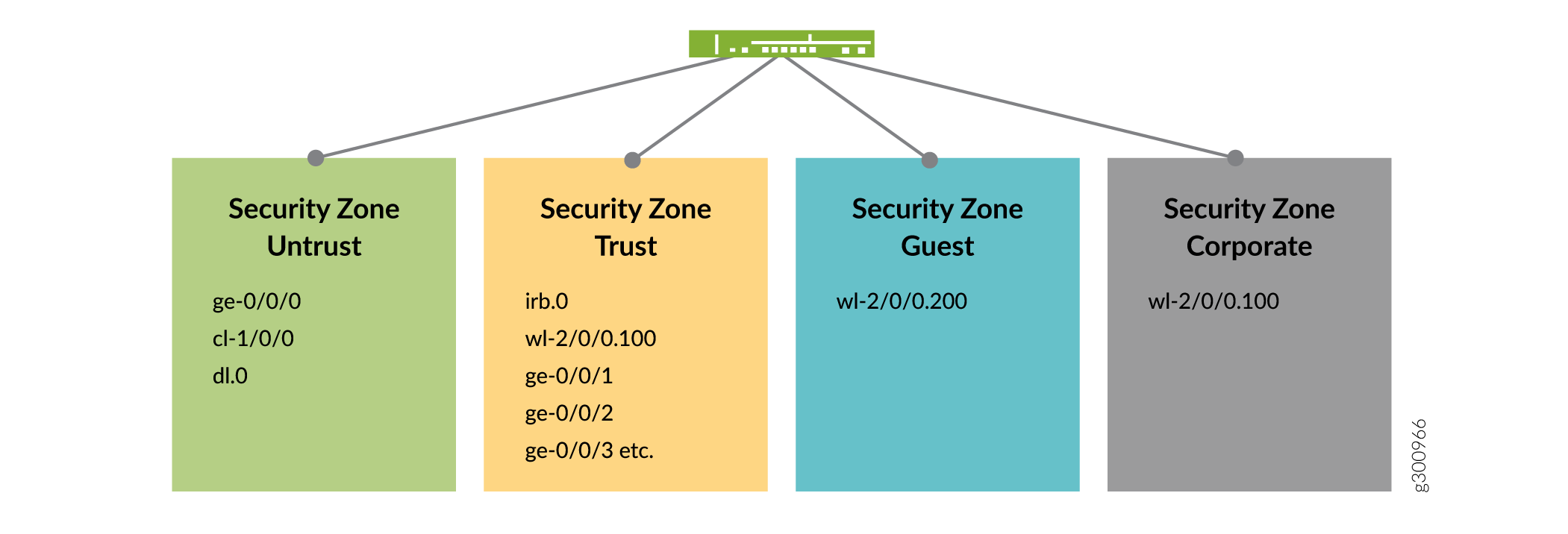
SRX300 系列设备上配置了四个安全区域,特别是不信任、信任、公司和访客。通过将接口分离到安全区域,可以分离流量并降低企业 Intranet 面临的风险,并作为实现清晰和简化安全策略实施的工具。区域不信任托管有权访问互联网的接口。
企业内部网中的内部接口位于区域信任中。组织无线设备在“公司”区域中漫游。仅被授予互联网访问权限的个人移动设备位于“来宾”区域。
表 1 显示了区域间流量安全策略的预期行为。
From-To |
Untrust |
Trust |
Corporate |
Guest |
|---|---|---|---|---|
Untrust |
不 |
仅信任启动 |
仅限企业发起 |
仅限来宾启动 |
Trust |
是的 |
是的 |
仅限企业发起 |
不 |
Corporate |
是的 |
是的 |
是的 |
不 |
Guest |
是的 |
不 |
不 |
不 |
表 2 汇总了接口的 VLAN 信息和 IP 地址信息。
Interface |
VLAN |
IP Adress |
Netmask |
|---|---|---|---|
wl-2/0/0.100 |
100 |
172.16.100.1 |
255.255.255.0 |
WL-2/0/0.200 |
200 |
192.16.200.1 |
255.255.255.0 |
DL.0 |
3 |
Dhcp |
- |
ge-0/0/0 |
3 |
Dhcp |
- |
Irb.0 |
3 |
192.168.1.1 |
255.255.255.0 |
配置和验证
配置
分步过程
此配置中的步骤从逻辑上从下层构建到上层。
为访客设备创建 VLAN。
set vlans guest-ap vlan-id 200 set vlans guest-ap description "VLAN that hosts the guest devices in the Guest security zone"
为公司设备创建 VLAN。
set vlans corporate vlan-id 100 set vlans corporate description "VLAN that hosts the corporate devices in the Trust security zone"
创建接入点。
set wlan access-point branch-ap interface wl-2/0/0 set wlan access-point branch-ap location "TME Lab, Sunnyvale, CA"
设置设备安装的国家/地区。不同的国家/地区有不同的 802.11 频谱可供一般使用。
set wlan access-point branch-ap access-point-options country US
配置接入点的 5GHz 无线电接口。设置其模式、将操作的通道号以及将使用的带宽。此外,设置 5GHz 无线电接口的发射功率(以 % 为单位)。
set wlan access-point branch-ap radio 1 radio-options mode acn set wlan access-point branch-ap radio 1 radio-options channel number 100 set wlan access-point branch-ap radio 1 radio-options channel bandwidth 40 set wlan access-point branch-ap radio 1 radio-options transmit-power 100
为 5GHz 访客网络创建虚拟接入点 (VAP)。Mini-PIM 支持每个无线电接口多达 8 个虚拟接入点。
set wlan access-point branch-ap radio 1 virtual-access-point 0 description Guest set wlan access-point branch-ap radio 1 virtual-access-point 0 ssid Guest set wlan access-point branch-ap radio 1 virtual-access-point 0 vlan 200
将 VAP
wpa-personal的安全性配置为 。设置密码套件、密钥类型和预共享密钥。set wlan access-point branch-ap radio 1 virtual-access-point 0 security wpa-personal wpa-version v2 set wlan access-point branch-ap radio 1 virtual-access-point 0 security wpa-personal cipher-suites ccmp set wlan access-point branch-ap radio 1 virtual-access-point 0 security wpa-personal key-type ascii set wlan access-point branch-ap radio 1 virtual-access-point 0 security wpa-personal key Juniper123
配置接入点的 2.4GHz 无线电接口。设置其模式、将操作的通道号以及将使用的带宽。此外,设置无线电接口的发射功率(以 % 为单位)。
set wlan access-point branch-ap radio 2 radio-options mode gn set wlan access-point branch-ap radio 2 radio-options channel number 6 set wlan access-point branch-ap radio 2 radio-options channel bandwidth 20 set wlan access-point branch-ap radio 2 radio-options transmit-power 100
在 2.4GHz 访客网络上配置 VAP。
set wlan access-point branch-ap radio 2 virtual-access-point 0 description Guest set wlan access-point branch-ap radio 2 virtual-access-point 0 ssid Guest set wlan access-point branch-ap radio 2 virtual-access-point 0 vlan 200
将 VAP
wpa-personal的安全性配置为 。设置密码套件、密钥类型和预共享密钥。set wlan access-point branch-ap radio 2 virtual-access-point 0 security wpa-personal wpa-version v2 set wlan access-point branch-ap radio 2 virtual-access-point 0 security wpa-personal cipher-suites ccmp set wlan access-point branch-ap radio 2 virtual-access-point 0 security wpa-personal key-type ascii set wlan access-point branch-ap radio 2 virtual-access-point 0 security wpa-personal key Juniper123
在 5GHz 企业网络上配置 VAP。
set wlan access-point branch-ap radio 1 virtual-access-point 1 description Corporate set wlan access-point branch-ap radio 1 virtual-access-point 1 ssid Corporate set wlan access-point branch-ap radio 1 virtual-access-point 1 vlan 100
将 VAP
wpa-personal的安全性配置为 。设置密码套件、密钥类型和预共享密钥。set wlan access-point branch-ap radio 1 virtual-access-point 1 security wpa-personal wpa-version v2 set wlan access-point branch-ap radio 1 virtual-access-point 1 security wpa-personal cipher-suites ccmp set wlan access-point branch-ap radio 1 virtual-access-point 1 security wpa-personal key-type ascii set wlan access-point branch-ap radio 1 virtual-access-point 1 security wpa-personal key corpKey123
在 2.4GHz 企业网络上配置 VAP。
set wlan access-point branch-ap radio 2 virtual-access-point 1 description Corporate set wlan access-point branch-ap radio 2 virtual-access-point 1 ssid Corporate set wlan access-point branch-ap radio 2 virtual-access-point 1 vlan 100
将 VAP
wpa-personal的安全性配置为 。设置密码套件、密钥类型和预共享密钥。set wlan access-point branch-ap radio 2 virtual-access-point 1 security wpa-personal wpa-version v2 set wlan access-point branch-ap radio 2 virtual-access-point 1 security wpa-personal cipher-suites ccmp set wlan access-point branch-ap radio 2 virtual-access-point 1 security wpa-personal key-type ascii set wlan access-point branch-ap radio 2 virtual-access-point 1 security wpa-personal key corpKey123
创建将充当访客 VAP 中设备的默认网关的 IP 接口(一个 VAP 在 5GHz 上工作,另一个在 2.4GHz 上工作)。
set interfaces wl-2/0/0 unit 200 vlan-id 200 set interfaces wl-2/0/0 unit 200 family inet address 172.16.200.1/24
创建 IP 接口,该接口将充当公司 VAP 中设备的默认网关(一个 VAP 在 5GHz 上工作,另一个在 2.4GHz 上工作)。
set interfaces wl-2/0/0 unit 200 vlan-id 100 set interfaces wl-2/0/0 unit 200 family inet address 172.16.100.1/24
为访客设备创建安全区域,并允许 DHCP 和其中的所有其他必要协议。确保将正确的 wl 接口也添加到区域中。
set security zones security-zone guest host-inbound-traffic system-services dhcp set security zones security-zone guest host-inbound-traffic system-services all set security zones security-zone guest host-inbound-traffic protocols all set security zones security-zone guest interfaces wl-2/0/0.200
为公司设备创建安全区域,并允许 DHCP 和其中的所有其他必要协议。确保将正确的 wl 接口也添加到区域中。
set security zones security-zone corporate host-inbound-traffic system-services dhcp set security zones security-zone corporate host-inbound-traffic system-services all set security zones security-zone corporate host-inbound-traffic protocols all set security zones security-zone corporate interfaces wl-2/0/0.100
为访客 VAP 创建唯一的 DHCP 服务器组(两个访客 VAP 只需要一个服务器组)。
set system services dhcp-local-server group jdhcp-guest-group interface wl-2/0/0.200
为企业 VAP 创建唯一的 DHCP 服务器组。
set system services dhcp-local-server group jdhcp-corporate-group interface wl-2/0/0.100
创建要分配给设备的 IP 地址池,在访客 VAP 中漫游。设置要分配给此池中设备的最低和最高 IP 地址、DNS 服务器以及池的默认网关的 IP 地址。
set access address-assignment pool junosDHCPPoolGuest family inet network 172.16.200.0/24 set access address-assignment pool junosDHCPPoolGuest family inet range junosRangeGuest low 172.16.200.10 set access address-assignment pool junosDHCPPoolGuest family inet range junosRangeGuest high 172.16.200.200 set access address-assignment pool junosDHCPPoolGuest family inet dhcp-attributes name-server 8.8.8.8 set access address-assignment pool junosDHCPPoolGuest family inet dhcp-attributes router 172.16.200.1
创建要分配给设备的 IP 地址池,在公司 VAP 中漫游。设置要分配给此池中设备的最低和最高 IP 地址、DNS 服务器以及池的默认网关的 IP 地址。
set access address-assignment pool junosDHCPPoolCorporate family inet network 172.16.100.0/24 set access address-assignment pool junosDHCPPoolCorporate family inet range junosRangeCorporate low 172.16.100.10 set access address-assignment pool junosDHCPPoolCorporate family inet range junosRangeCorporate high 172.16.100.200 set access address-assignment pool junosDHCPPoolCorporate family inet dhcp-attributes name-server 8.8.8.8 set access address-assignment pool junosDHCPPoolCorporate family inet dhcp-attributes name-server 1.1.1.1 set access address-assignment pool junosDHCPPoolGuest family inet dhcp-attributes router 172.16.100.1
创建源 NAT 以将 NAT 应用于来宾区域中的外部接口的设备。
set security nat source rule-set guest-to-untrust from zone guest set security nat source rule-set guest-to-untrust to zone untrust set security nat source rule-set guest-to-untrust rule r1 match source-address 0.0.0.0/0 set security nat source rule-set guest-to-untrust rule r1 then source-nat interface
创建源 NAT 以将 NAT 应用于企业区域中的外部接口的设备。
set security nat source rule-set corporate-to-untrust from zone corporate set security nat source rule-set corporate-to-untrust to zone untrust set security nat source rule-set corporate-to-untrust rule r-c2u-1 match source-address 0.0.0.0/0 set security nat source rule-set corporate-to-untrust rule r-c2u-1 then source-nat interface
创建允许来宾和不信任区域之间的流量的安全策略。确保策略中包含所需的网段和/或应用程序。
set security policies from-zone guest to-zone untrust policy allow-in-zone match source-address any set security policies from-zone guest to-zone untrust policy allow-in-zone match destination-address any set security policies from-zone guest to-zone untrust policy allow-in-zone match application any set security policies from-zone guest to-zone guest policy allow-in-zone then permit
创建允许“公司”区域和“不信任”区域之间的流量的安全策略。此步骤使应用了 NAT 的流量能够在区域之间流动。
set security policies from-zone corporate to-zone untrust policy internet-acces match source-address any set security policies from-zone corporate to-zone untrust policy internet-acces match destination-address any set security policies from-zone corporate to-zone untrust policy internet-acces match application any set security policies from-zone corporate to-zone untrust policy internet-acces then permit
创建一个安全策略,以允许公司区域和信任区域之间的流量,并使应用 NAT 的流量能够在区域之间流动。
set security policies from-zone corporate to-zone trust policy internet-acces match source-address any set security policies from-zone corporate to-zone trust policy internet-acces match destination-address any set security policies from-zone corporate to-zone trust policy internet-acces match application any set security policies from-zone corporate to-zone trust policy internet-acces then permit
设置主互联网链路的接口说明。设置接口以通过 DHCP 协议获取配置。确保将 LTE 接口设置为互联网链路的备份接口。
set interfaces ge-0/0/0 unit 0 description "WAN Interface 1 - Primary" set interfaces ge-0/0/0 unit 0 family inet dhcp vendor-id Juniper-srx320 set interfaces ge-0/0/0 unit 0 backup-options interface dl0.0
配置调制解调器接口。确保包含 SIM 卡的 SIM 卡插槽设置为活动状态。
set interfaces cl-1/0/0 dialer-options pool 1 priority 100 set interfaces cl-1/0/0 act-sim 1 set interfaces cl-1/0/0 cellular-options sim 1 radio-access automatic
配置拨号器接口。
set interfaces dl0 unit 0 family inet negotiate-address set interfaces dl0 unit 0 family inet6 negotiate-address set interfaces dl0 unit 0 dialer-options pool 1 set interfaces dl0 unit 0 dialer-options dial-string "*99#"
将无线接口配置为接受 VLAN 未标记数据包。
set interfaces wl-2/0/0 flexible-vlan-tagging
在调制解调器中设置 SIM 卡的接入点名称。
request modem wireless create-profile profile-id 10 access-point-name broadband cl-1/0/0 slot 1
提交配置
验证
分步过程
确保接口已启动并正在运行。
> show interfaces terse wl-2/0/0 up up wl-2/0/0.100 up up inet 172.16.100.1/24 wl-2/0/0.200 up up inet 172.16.200.1/24 wl-2/0/0.32767 up up
检查接入点的状态,确保无线电接口的状态为ON,其运行的信道和带宽与配置一致。
> show wlan access-points branch-ap detail Active access point detail information Access Point : branch-ap Type : Internal Location : TME Lab, Sunnyvale, CA Serial Number : EV2619AF0051 Firmware Version : v1.2.8 Alternate Version : v1.1.0 Country : US Access Interface : wl-2/0/0 System Time : Mon Mar 23 22:36:43 UTC 2020 Packet Capture : Off Ethernet Port: MAC Address : 0c:81:26:58:04:26 Radio1: Status : On MAC Address : 0c:81:26:58:04:28 Temperature : 50 Mode : IEEE 802.11a/n/ac Channel : 108 Bandwidth : 40 Transmit Power : 100 Radio2: Status : On MAC Address : 0c:81:26:58:04:27 Temperature : 52 Mode : IEEE 802.11g/n Channel : 6 Bandwidth : 20 Transmit Power : 100检查所有 VAP 的状态。确保 SSID 和安全设置与配置一致。
> show wlan access-points branch-ap virtual-access-points all detail Virtual access points information Access point name: branch-ap Radio1: VAP0: SSID : Guest Description : Guest MAC Address : 0c:81:26:58:04:28 Maximum Station : 127 Broadcast SSID : Enable Station Isolation : Disable Upload Limit : Disable Download Limit : Disable VLAN ID : 200 Station MAC Filter : Disable VAP Security : wpa-personal WPA Version: WPA2 : Enable WPA : Disable Ciper-Suites: CCMP : Enable TKIP : Disable Traffic Statistics: Input Bytes : 79470 Output Bytes : 99937 Input Packets : 479 Output Packets : 498 VAP1: SSID : Corporate Description : Corporate MAC Address : 16:81:26:58:04:28 Maximum Station : 127 Broadcast SSID : Enable Station Isolation : Disable Upload Limit : Disable Download Limit : Disable VLAN ID : 100 Station MAC Filter : Disable VAP Security : wpa-personal WPA Version: WPA2 : Enable WPA : Disable Ciper-Suites: CCMP : Enable TKIP : Disable Traffic Statistics: Input Bytes : 2495033 Output Bytes : 3480274 Input Packets : 30241 Output Packets : 29412 Radio2: VAP0: SSID : Guest Description : Guest MAC Address : 0c:81:26:58:04:27 Maximum Station : 127 Broadcast SSID : Enable Station Isolation : Disable Upload Limit : Disable Download Limit : Disable VLAN ID : 200 Station MAC Filter : Disable VAP Security : wpa-personal WPA Version: WPA2 : Enable WPA : Disable Ciper-Suites: CCMP : Enable TKIP : Disable Traffic Statistics: Input Bytes : 2025 Output Bytes : 2603 Input Packets : 15 Output Packets : 19 VAP1: SSID : Corporate Description : Corporate MAC Address : 16:81:26:58:04:27 Maximum Station : 127 Broadcast SSID : Enable Station Isolation : Disable Upload Limit : Disable Download Limit : Disable VLAN ID : 100 Station MAC Filter : Disable VAP Security : wpa-personal WPA Version: WPA2 : Enable WPA : Disable Ciper-Suites: CCMP : Enable TKIP : Disable Traffic Statistics: Input Bytes : 75308 Output Bytes : 70057 Input Packets : 498 Output Packets : 389检查有关接入点每个无线电上的客户端关联的摘要。此命令显示每个无线电接口上的关联用户数。
> show wlan access-points branch-ap radio 1 client-associations Access point client associations summary Access point: branch-ap Client number on radio 1 (5.0 GHz) : 1
检查有关接入点每个无线电上的客户端关联的详细信息。用户的 MAC 地址以及流量统计信息显示在输出中。
> show wlan access-points branch-ap radio 1 client-associations detail Access point client associations information Access point: branch-ap VAP Client MAC Address Auth Packets Rx/Tx Bytes Rx/Tx Radio1:Corporate 24:77:03:80:52:68 OK 42501/25026 2579601/2742637
检查 Junos 是否检测到小型 PIM 模块。
> show chassis hardware Hardware inventory: Item Version Part number Serial number Description Chassis CX0916AF0004 SRX320-POE Routing Engine REV 0x05 650-065041 CX0916AF0004 RE-SRX320-POE FPC 0 FPC PIC 0 6xGE,2xGE SFP Base PIC FPC 1 REV 02 650-073958 AH06074206 FPC PIC 0 LTE for AE FPC 2 REV 03 650-096889 EV2619AF0051 FPC PIC 0 WAP for WW mPIM Power Supply 0
检查 Mini-PIM 的固件版本,并根据需要进行更新。
> show system firmware Part Type Tag Current Available Status version version FPC 1 PIC 0 MLTE_FW 1 17.1.80 0 OK FPC 2 PIC 0 MWAP_FW 1 1.2.8 0 OK Routing Engine 0 RE BIOS 0 3.0 3.6 OK Routing Engine 0 RE BIOS Backup 1 3.0 3.6 OK获取 VAP 上的数据包捕获以进行故障排除。
> request wlan access-point packet-capture start branch-ap promiscuous size 4096 duration 120 filename wlan-cap.pcap interface Radio1VAP0 Starting packet capture Capture interface: Radio1VAP0 File : wlan-cap.pcap Duration : 120 seconds File size max : 4096 kilobytes
该文件保存在 /var/tmp 中。您可以下载该文件并使用数据包跟踪应用程序(如 WIreshark)打开。
