Replace SSL Certificate for Apstra ZTP Server GUI
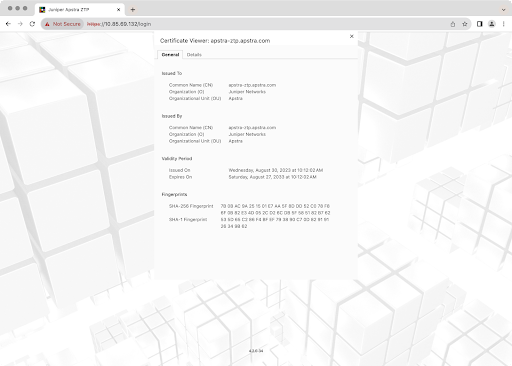
For security, we recommend that you replace the Apstra ZTP default self-signed SSL certificate with one from your own certificate authority. Web server certificate management is the responsibility of the end user. Juniper support is best effort only.
When you boot up the Apstra ZTP server for the first time, a unique self-signed certificate and key are automatically generated and stored on the Apstra ZTP NGINX container. The certificate is used for encrypting the Apstra ZTP server. We recommend replacing the default SSL certificate.
Next Step: Configure credentials for the Apstra ZTP server
GUI.