AI-Predictive Threat Prevention Overview
AI-Predictive Threat Prevention uses artificial intelligence (AI) on packet snippets to predict and prevent both known and zero-day malware on the wire. By actively distinguishing and ignoring non-threatening activities, this system significantly reduces false positives. It enables human experts to concentrate on more critical security tasks and identify genuine, dangerous threats throughout the entire attack life cycle. This process continuously safeguards the network from initial and subsequent attacks.
Users today are increasingly on the move, requiring fast and secure network access from any location. This heightened mobility raises malware vulnerability, as network security administrators often have limited control over the networks users connect to for accessing corporate resources. Therefore, it is crucial to implement a network security solution that is innovative, swift, and adept at detecting and preventing malware. This topic explores how Juniper Networks' AI-Predictive Threat Prevention, a security solution powered by AI and machine learning (ML), functions.
Juniper Networks' AI-Predictive Threat Prevention is an advanced malware detection and prevention solution designed to safeguard your network against threats arising from users accessing corporate resources from various locations and browsing the Internet to many destinations. Powered by AI and ML, this intelligent security solution enhances the ability to predict and identify genuine threats more swiftly, allowing human experts to concentrate on strategic security initiatives.
AI-Predictive Threat Prevention includes the following features:
-
Anti-malware prevention—AI-Predictive Threat Prevention offers effective anti-malware capabilities, scanning vast amounts of data across the network. Traditional solutions require a complete file to determine whether it is malicious. Additionally, the traditional detection process often necessitates enabling a TCP proxy, which can slow down firewall throughput performance. Juniper Networks' organically built anti-malware solution employs a proxy-less architecture with AI to detect threats efficiently.
-
AI-generated custom signatures—Organizations can leverage AI-Predictive Threat Prevention with an advanced anti-malware solution to generate custom signatures tailored to their specific environment. Unlike other technologies, AI-Predictive Threat Prevention ensures that these signatures remain active throughout the attack life cycle. This AI-driven anti-malware solution continuously updates threat signatures, detects abnormal behavior patterns, and offers robust protection against subsequent attacks. As a result, security teams can identify potential threats more quickly and efficiently.
Use Feature Explorer to confirm platform and release support for specific features.
For information about licenses for your supported platforms, see Software Licenses for SRX Series Firewalls.
Benefits
-
Active threat detection for known and unknown threats
-
Improved throughput
-
Reduced false positives by filtering out non-threatening activities
-
Analysis based on AI and ML in addition to autogenerated signatures
Solution
Flow-based Antivirus Scanning
Starting in Junos OS Release 23.4R1, you can use the flow-based antivirus solution to scan your network traffic and prevent threats in real time using a unified pattern-matching engine.
The flow-based antivirus scanning is an organically built solution that operates at line rate, providing superior efficacy and rapid response to ongoing attacks without compromising performance. Utilizing a proxy-less architecture, it intelligently detects malware by scanning packets as they stream in, without requiring full file downloads. It comprises Juniper Networks curated signatures, which are continuously updated from Juniper ATP Cloud and distributed through Juniper Networks' content delivery network (CDN).
With the flow-based antivirus solution, you can enable inline blocking capabilities that are based on threat intelligence and recent threat detection events across all Juniper’s ATP Cloud customer base.
To enforce a flow-based antivirus solution, you must install the Juniper Antivirus license, Juniper AV and enable the antivirus policy. For more information, see Configure Flow-Based Antivirus Policy.
Machine-Learning-based Threat Detection
Starting in Junos OS Release 24.2R1, you can configure ML-based threat detection for zero-day threats.
The ML-based threat detection scans files inline on your firewall and blocks infected files before they are downloaded. This threat detection process occurs without Internet access, and requires only a small section of the file to return a verdict.
ML-based threat detection is enabled on your firewall when the scan engine binary file is automatically downloaded from the Juniper Networks CDN server to your firewall. By default, an ML model binary file is automatically downloaded from the CDN server to your firewall device, generally once a week.
To implement machine-learning-based threat detection, you must install the Juniper Antivirus license, Juniper AV and enable machine learning. For more information, see Configure Machine Learning-Based Threat Detection.
Workflow
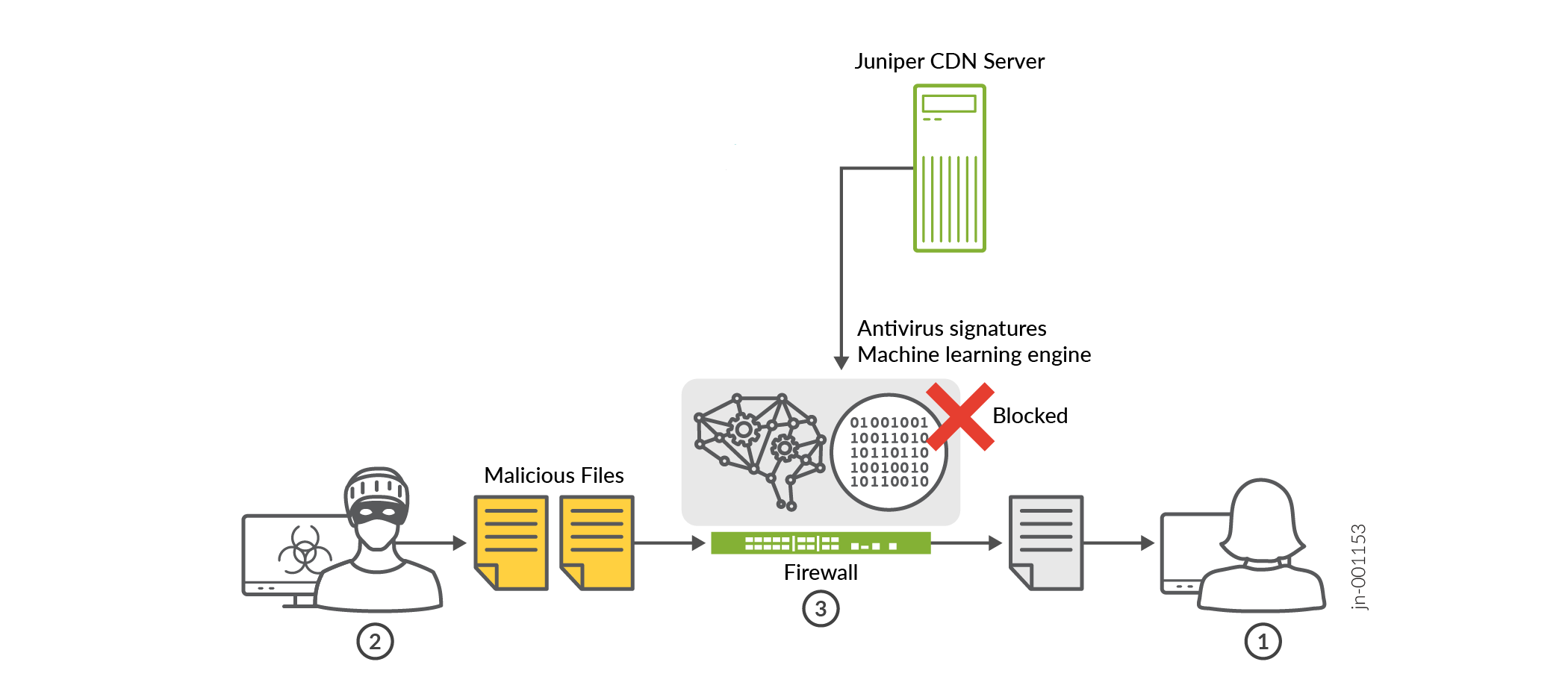
Here is a high-level workflow for AI-Predictive Threat Prevention:
|
Step |
Description |
|---|---|
| 1 | The client configures the antivirus policy and CDN server URL on SRX Series Firewall to receive the latest antivirus signatures and ML scan engine updates from the CDN server. |
| 2 | The client requests a file to be downloaded from the Internet. |
| 3 |
As the file passes through the SRX Series Firewall, some portions of the file are matched against the latest antivirus signatures that are received from the CDN server. If a matching signature is found, the file can be blocked and not allowed to be downloaded, depending on the policy action. For .exe and .dll file types, if no matching antivirus signature is found, the ML scan engine analyzes the file inline on the SRX Series Firewall and immediately provides a verdict. Based on this verdict, the SRX Series Firewall can block any infected files before they are downloaded, depending on the policy action. |
-
If the SRX Series Firewall is enrolled to Juniper ATP Cloud, then in addition to flow-based antivirus scanning and ML-based threat detection, the file is also submitted to Juniper ATP Cloud for analysis.
-
You can configure AI-Predictive Threat Prevention on the SRX Series Firewall without enrolling to Juniper ATP Cloud.
Personas
|
Personas |
Benefits |
|---|---|
|
Chief information security officer (CISO) |
|
|
InfoSec director |
|
|
InfoSec architect |
|
|
Network architect |
|
Use Cases
AI-Predictive Threat Prevention is ideal for customers who need to protect their business assets from today’s advanced cyberthreat, especially in the following use cases:
-
Campus
-
Enterprise
-
Data center
-
Public, private, and hybrid cloud
-
Service provider
Solution Comparison Matrix
Here’s a comparison table that outlines key features and differences between Juniper ATP Cloud, flow-based antivirus solution, and machine learning-based security solution.
|
Requirements |
Juniper ATP Cloud |
Flow-Based Antivirus |
ML-Based Threat Detection |
|---|---|---|---|
|
Services |
Advanced anti-malware |
Static antivirus engine with frequent signature updates |
Static antivirus engine with frequent signature updates + ML scan engine |
|
File submission |
Cloud |
Block mode, no submission to cloud |
Block mode, no submission to cloud |
|
Internet access |
Access required for feature to function |
Required to download antivirus database from Juniper CDN server. |
Required to download ML models from Juniper CDN server. |
|
AAMW role |
Works with cloud to download AI-generated signatures. |
Works offline after database download |
Works offline after ML engine download |
|
CLI configuration |
set services advanced-anti-malware
|
set services anti-virus
|
set services anti-virus policy <policy name>
machine-learning-scan
|
|
Supported protocols |
HTTP and HTTPS IMAP and IMAPS SMTP and SMTPS SMB |
HTTP and HTTPS IMAP and IMAPS SMTP and SMTPS SMB |
HTTP and HTTPS IMAP and IMAPS SMTP and SMTPS SMB |
| Supported release | See Feature Explorer | See Feature Explorer | See Feature Explorer |
|
Juniper ATP Cloud enrollment |
Yes |
Not required |
Not required |
| Summary | Leverages cloud infrastructure for scalability and quick response times. Offers a combination of signature-based and behavior analysis for detecting threats. | Primarily relies on signature-based detection and flow inspection. Easier to deploy; performs frequent signature updates. | Uses advanced algorithms for anomaly detection and pattern recognition, offering robust protection against both known and unknown threats. Provides real-time analysis and adapts over time to new threats. |
Juniper ATP Cloud and AI-Predictive Threat Prevention are licensed as separate products. Flow-based antivirus and ML-based threat detection are components of AI-Predictive Threat Prevention. These components can be used independently and do not require enrollment in Juniper ATP Cloud. For licensing information about AI-Predictive Threat Prevention, see Software Licenses for SRX Series Firewalls.
You can choose a solution that aligns with the specific needs, infrastructure, and resources of your organization, or you can layer these solutions for more effective enforcement. Apply all of these solutions in a security policy.
What's Next?
In the next section, you'll learn how to configure flow-based antivirus and ML-based threat detection on your firewall. You can also update the flow-based antivirus policy and ML-based threat detection on your SRX Series Firewall in offline mode.
