About Juniper ATP Cloud
Juniper® Advanced Threat Prevention Cloud (Juniper ATP Cloud) is a security framework that protects all hosts in your network against evolving security threats by employing cloud-based threat detection software with a next-generation firewall system. See Figure 1.
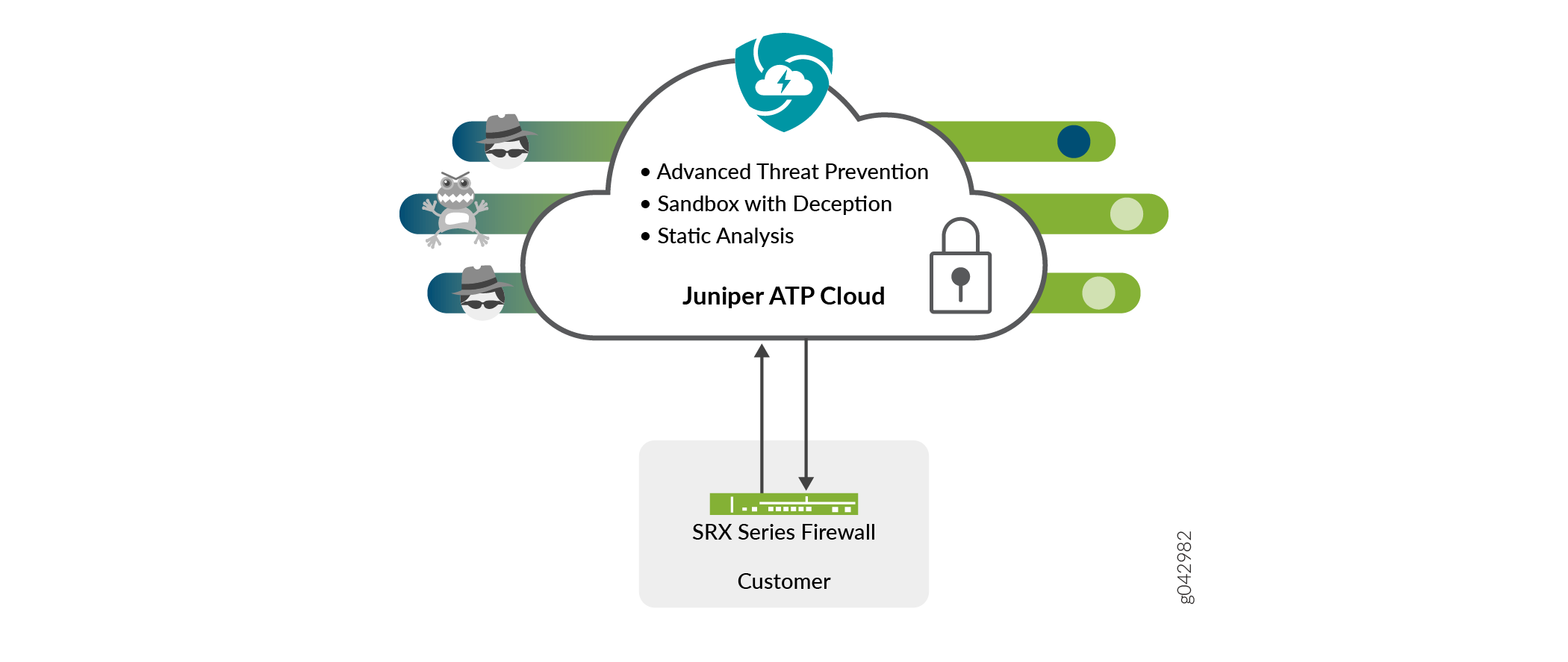
Juniper ATP Cloud protects your network by performing the following tasks:
-
The SRX Series Firewall extracts potentially malicious objects and files and sends them to the cloud for analysis.
-
Known malicious files are quickly identified and dropped before they can infect a host.
-
Multiple techniques identify new malware, adding it to the known list of malware.
-
Correlation between newly identified malware and known Command and Control (C&C) sites aids analysis.
-
The SRX Series Firewall blocks known malicious file downloads and outbound C&C traffic.
Juniper ATP Cloud supports the following modes:
-
Layer 3 (L3) mode
-
Tap mode
-
Transparent mode using MAC address
For more information, see Transparent mode on SRX Series Firewalls.
-
Secure wire mode (high-level transparent mode using the interface to directly passing traffic, not by MAC address.) For more information, see Understanding Secure Wire.
Juniper ATP Cloud Features
Juniper ATP Cloud is a cloud-based solution. Cloud environments are flexible and scalable, and a shared environment ensures that everyone benefits from new threat intelligence in near real-time. Your sensitive data is secured even though it is in a cloud shared environment. Security analysts can update their defense when new attack techniques are discovered and distribute the threat intelligence with very little delay.
In addition, Juniper ATP Cloud offers the following features:
-
Integrated with the SRX Series Firewall to simplify deployment and enhance the anti-threat capabilities of the firewall.
-
Delivers protection against “zero-day” threats using a combination of tools to provide robust coverage against sophisticated, evasive threats
-
AI-Predictive Threat Prevention, an intelligent and fast malware detection and prevention solution, protects your network wherever users connect from. This solution leverages flow-based antivirus and machine learning-based zero-day threat detection to protect users from malware attacks and to prevent spreading of malware in your system. See Configure Flow-Based Antivirus Policy and Configure Machine Learning-Based Threat Detection.
-
Checks inbound and outbound traffic with policy enhancements that allow users to stop malware, quarantine infected systems, prevent data exfiltration, and disrupt lateral movement.
-
High availability to provide uninterrupted service.
-
Scalable to handle increasing loads that require more computing resources, increased network bandwidth to receive more customer submissions, and a large storage for malware.
-
Provides deep inspection, actionable reporting, and inline malware blocking
-
API for C&C feeds, allowlist and blocklist operations, and file submission. See the Threat Intelligence Open API Setup Guide for more information.
-
Domain Name System (DNS), Encrypted Traffic Insights (ETI) and Internet of Things (IoT) security. For licensing information specific to these features, see Software Licenses for ATP Cloud.
Figure 2 lists the Juniper ATP Cloud components.
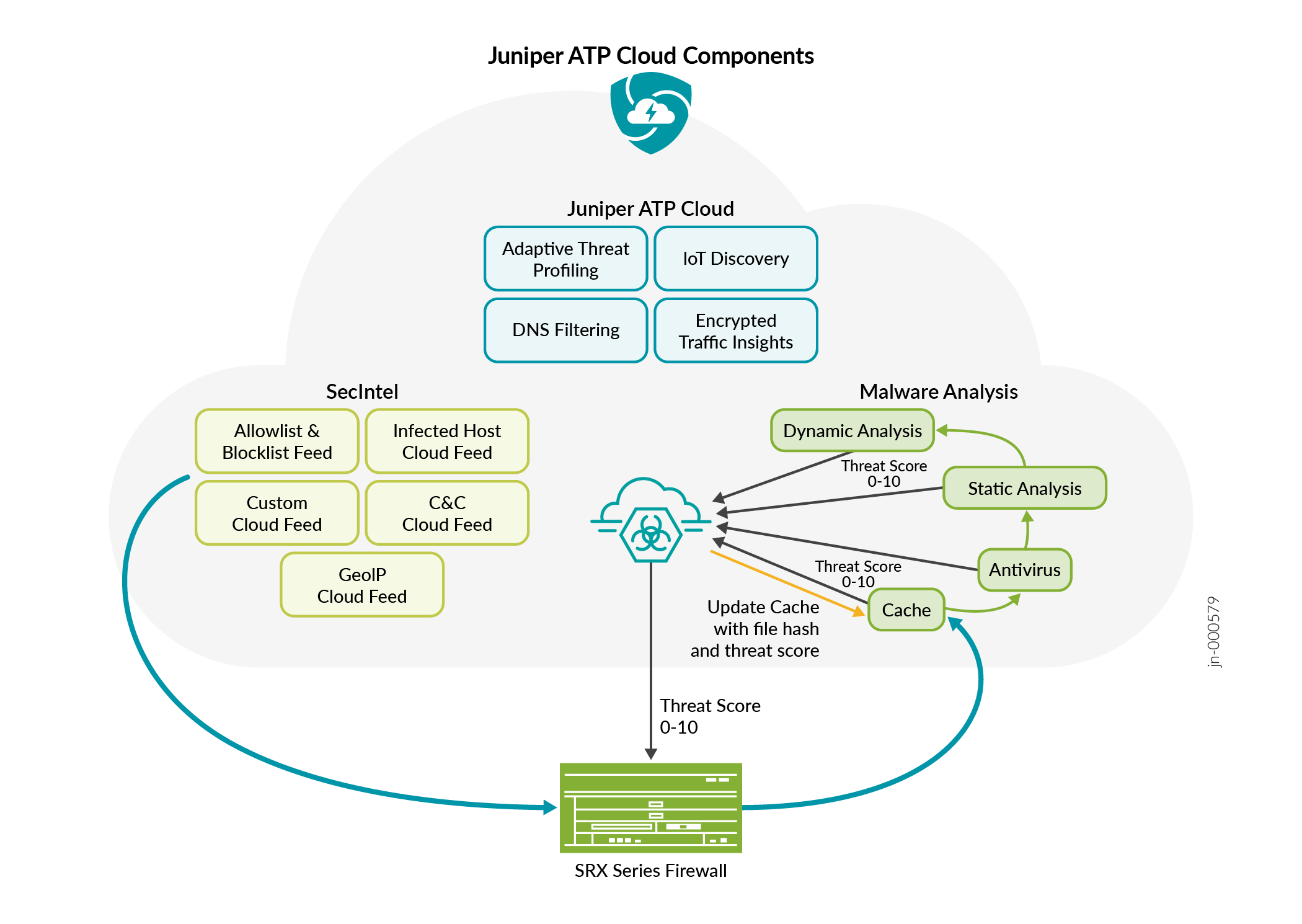
Table 1 briefly describes each Juniper ATP Cloud component’s operation.
|
Component |
Operation |
|---|---|
|
C&C cloud feeds |
C&C feeds are essentially a list of servers that are known C&C for botnets. The list also includes servers that are known sources for malware downloads. |
|
GeoIP cloud feeds |
GeoIP feeds is an up-to-date mapping of IP addresses to geographical regions. This gives you the ability to filter traffic to and from specific geographies in the world. |
|
Infected host cloud feeds |
Infected hosts indicate local devices that are potentially compromised because they appear to be part of a C&C network or other exhibit other symptoms. |
|
Allowlist, blocklists and custom cloud feeds |
An allowlist is simply a list of known IP addresses that you trust and a blocklist is a list that you do not trust. |
|
SRX Series Firewall |
Submits extracted file content for analysis and detected C&C hits inside the customer network. Performs inline blocking based on file signature database provided by Juniper ATP Cloud. |
|
Malware inspection pipeline |
Performs malware analysis and threat detection |
|
Internal compromise detection |
Inspects files, metadata, and other information. |
|
Service portal (Web UI) |
Graphics interface displaying information about detected threats inside the customer network. Configuration management tool where customers can refine which file categories can be submitted into the cloud for processing. |
|
Encrypted Traffic Insights |
Encrypted Traffic Insights restores visibility lost due to encrypted traffic without the heavy burden of full TLS/SSL decryption. |
|
SecIntel |
Provides curated SecIntel in the form of threat feeds that include malicious domains, URLs, and IP addresses used in known attack campaigns. SecIntel also enables customers to feed and distribute their own threat intelligence for inline blocking. |
|
Adaptive Threat Profiling |
Automatically create SecIntel threat feeds based on who and what is currently attacking the network to combat the continuous onslaught of new threats. Adaptive Threat Profiling leverages Juniper Security Services to classify endpoint behavior and build custom threat intelligence feeds that can be used for further inspection or blocking at multiple enforcement points. |
|
DNS Security |
Provides threat prevention from attacks that utilize DGA and DNS tunneling techniques. Protect against DNS exploits for C&C communications, data exfiltration, phishing attacks, and ransomware that commonly exploit DNS using a variety of techniques. |
| IoT Threat Prevention |
ATP Cloud allows customers to control the IoT attack surface on their network by providing an easy way to identify and categorize the IoT devices |
How the SRX Series Firewall Remediates Traffic
The SRX Series Firewalls use intelligence provided by Juniper ATP Cloud to remediate malicious content through the use of security policies. If configured, security policies might block that content before it is delivered to the destination address.
For inbound traffic, security policies on the SRX Series Firewall look for specific types of files, like .exe files, to inspect. When one is encountered, the security policy sends the file to the Juniper ATP Cloud cloud for inspection. The SRX Series Firewall holds the last few KB of the file from the destination client while Juniper ATP Cloud checks if this file has already been analyzed. If so, a verdict is returned and the file is either sent to the client or blocked depending on the file’s threat level and the user-defined policy in place. If the cloud has not inspected this file before, the file is sent to the client while Juniper ATP Cloud performs an exhaustive analysis. If the file’s threat level indicates malware (and depending on the user-defined configurations) the client system is marked as an infected host and blocked from outbound traffic. For more information, see How is Malware Analyzed and Detected?.
Figure 3 shows an example flow of a client requesting a file download with Juniper ATP Cloud.
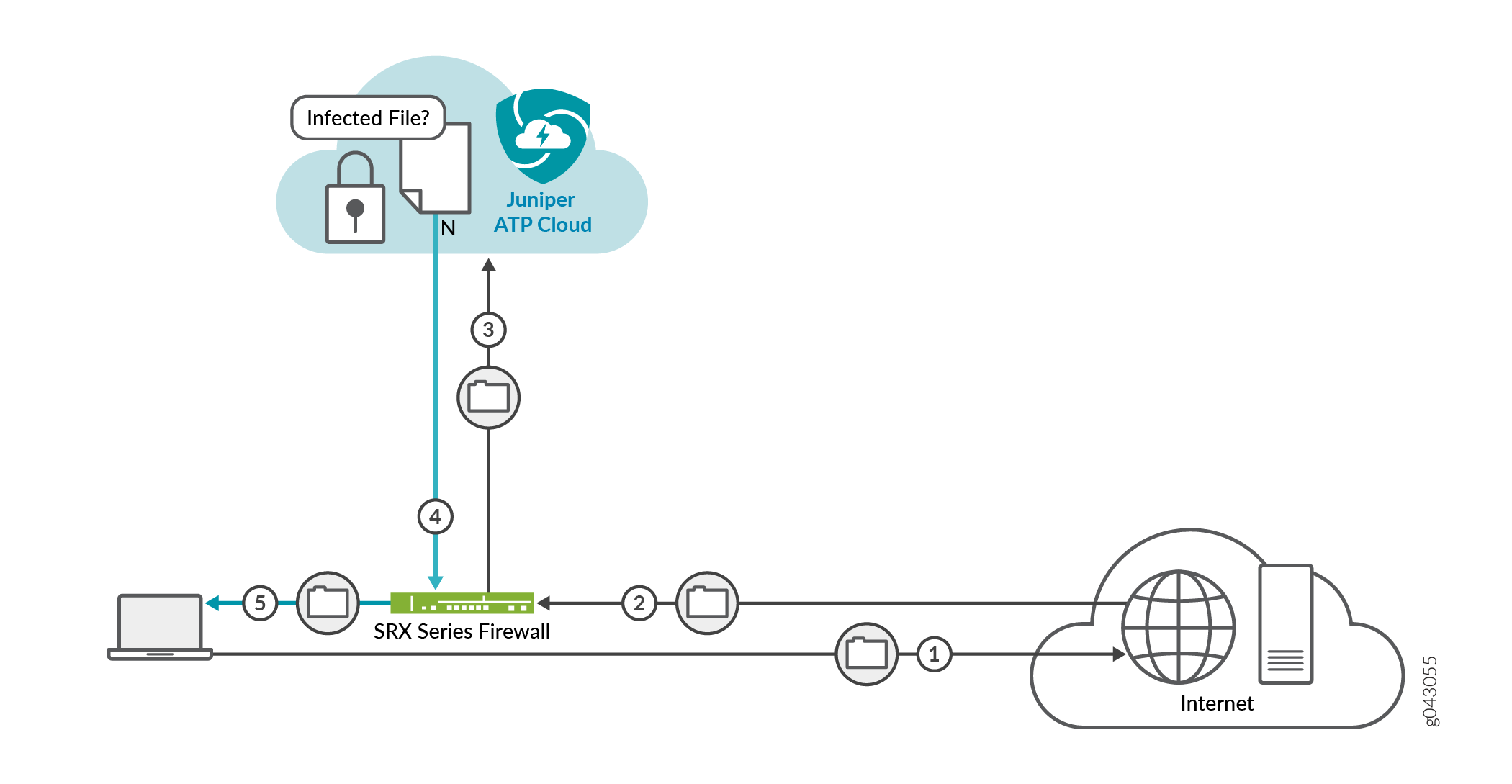
|
Step |
Description |
|---|---|
|
1 |
A client system behind an SRX Series Firewalls requests a file download from the Internet. The SRX Series Firewall forwards that request to the appropriate server. |
|
2 |
The SRX Series Firewall receives the downloaded file and checks its security profile to see if any additional action must be performed. |
|
3 |
The downloaded file type is on the list of files that must be inspected and is sent to the cloud for analysis. |
|
4 |
Juniper ATP Cloud has inspected this file before and has the analysis stored in cache. In this example, the file is not malware and the threat level verdict is sent back to the SRX Series Firewall. |
|
5 |
Based on user-defined policies and threat level verdict, the SRX Series Firewall sends the file to the client. |
For outbound traffic, the SRX Series Firewall monitors traffic that matches C&C feeds it receives, blocks these C&C requests, and reports them to Juniper ATP Cloud. A list of infected hosts is available so that the SRX Series Firewall can block inbound and outbound traffic.
Juniper ATP Cloud Use Cases
Juniper ATP Cloud can be used anywhere in an SRX Series deployment. See Figure 4
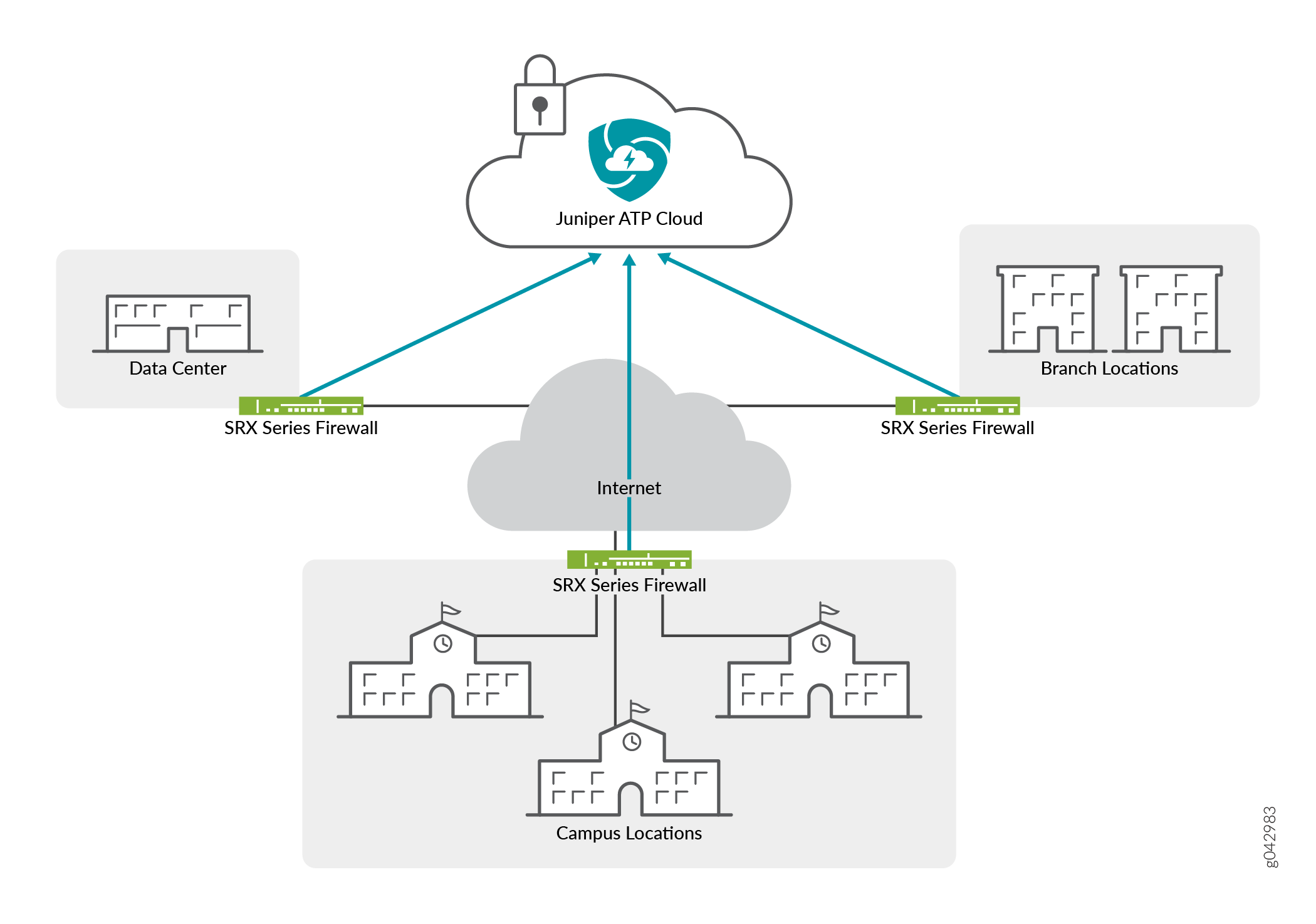
-
Campus edge firewall—Juniper ATP Cloud analyzes files downloaded from the Internet and protects end-user devices.
-
Data center edge—Like the campus edge firewall, Juniper ATP Cloud prevents infected files and application malware from running on your computers.
-
Branch router—Juniper ATP Cloud provides protection from split-tunneling deployments. A disadvantage of split-tunneling is that users can bypass security set in place by your company’s infrastructure.
