Configure SecIntel Feeds for MX Series Routers
Overview
SecIntel provides carefully curated, verified threat intelligence from Juniper ATP Cloud to MX Series routing platforms, blocking command-and-control (C&C) communications to and from malicious IPs at unparalleled line rate.
With SecIntel and MX Series router integration, you can:
- Detect and block known malicious IPs, infected C&C hosts, and DDoS attacks.
- Sinkhole malicious DNS requests.
- Enable customer IP threat feeds.
Starting in Junos OS 19.3R1 and later releases, SecIntel feeds are supported on MX240, MX480, and MX960 routers with the use of Policy Enforcer.
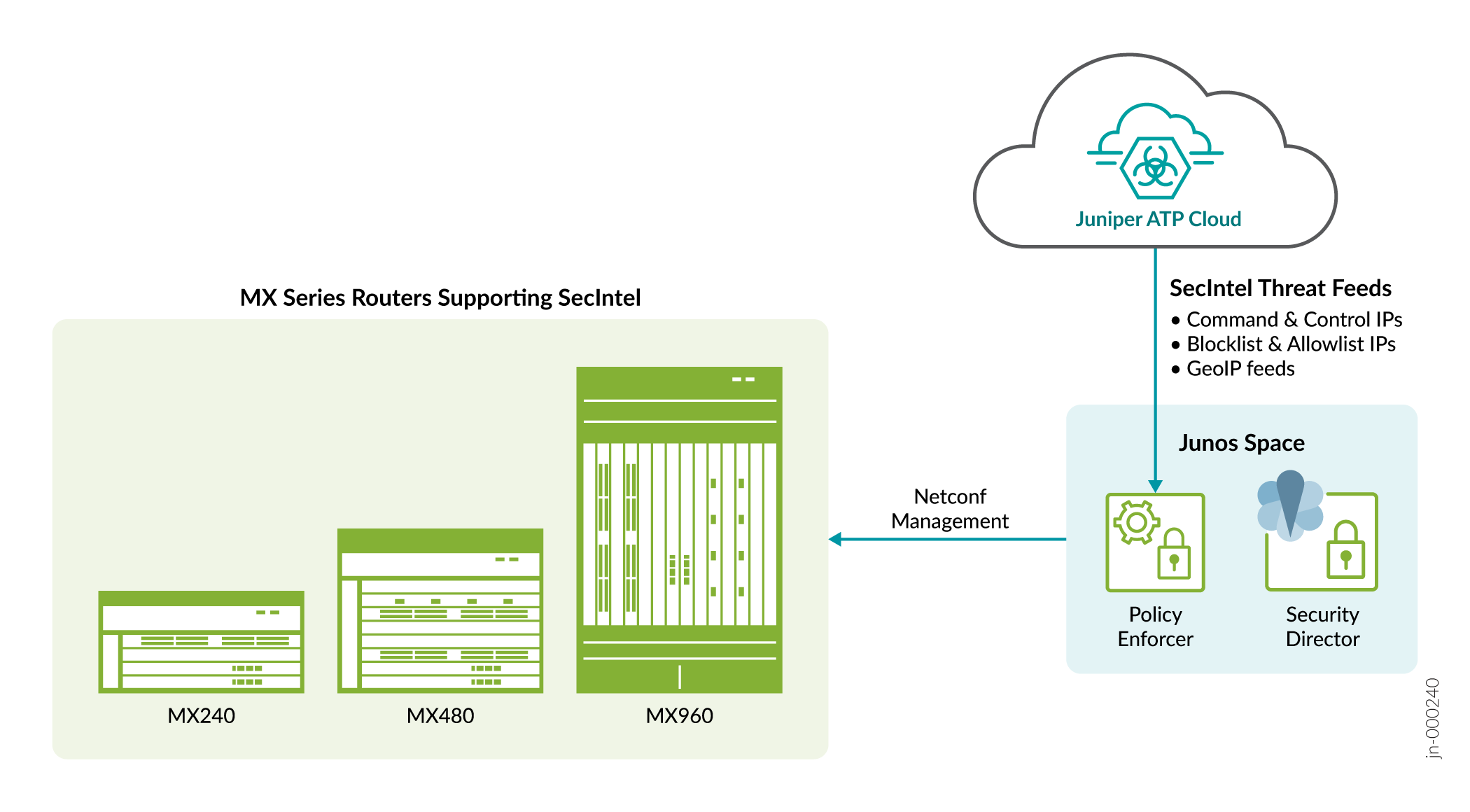
Starting in Junos OS 22.1R1 and later releases, SecIntel feed on the MX devices include GeoIP filtering as well as direct enrollment option to Juniper ATP Cloud.
Direct Enrollment to Juniper ATP Cloud is supported on MX240, MX480, and MX960 routers.
For more information, see Juniper SecIntel on MX.
Benefits
With SecIntel and MX Series router integration, you can:
-
Shut down attacks before they start.
-
Protect users, applications, and infrastructure from compromise—including subscribers.
-
Turn connectivity layers into security layers without additional infrastructure.
Use Case 1: Direct Enrollment to Juniper ATP Cloud
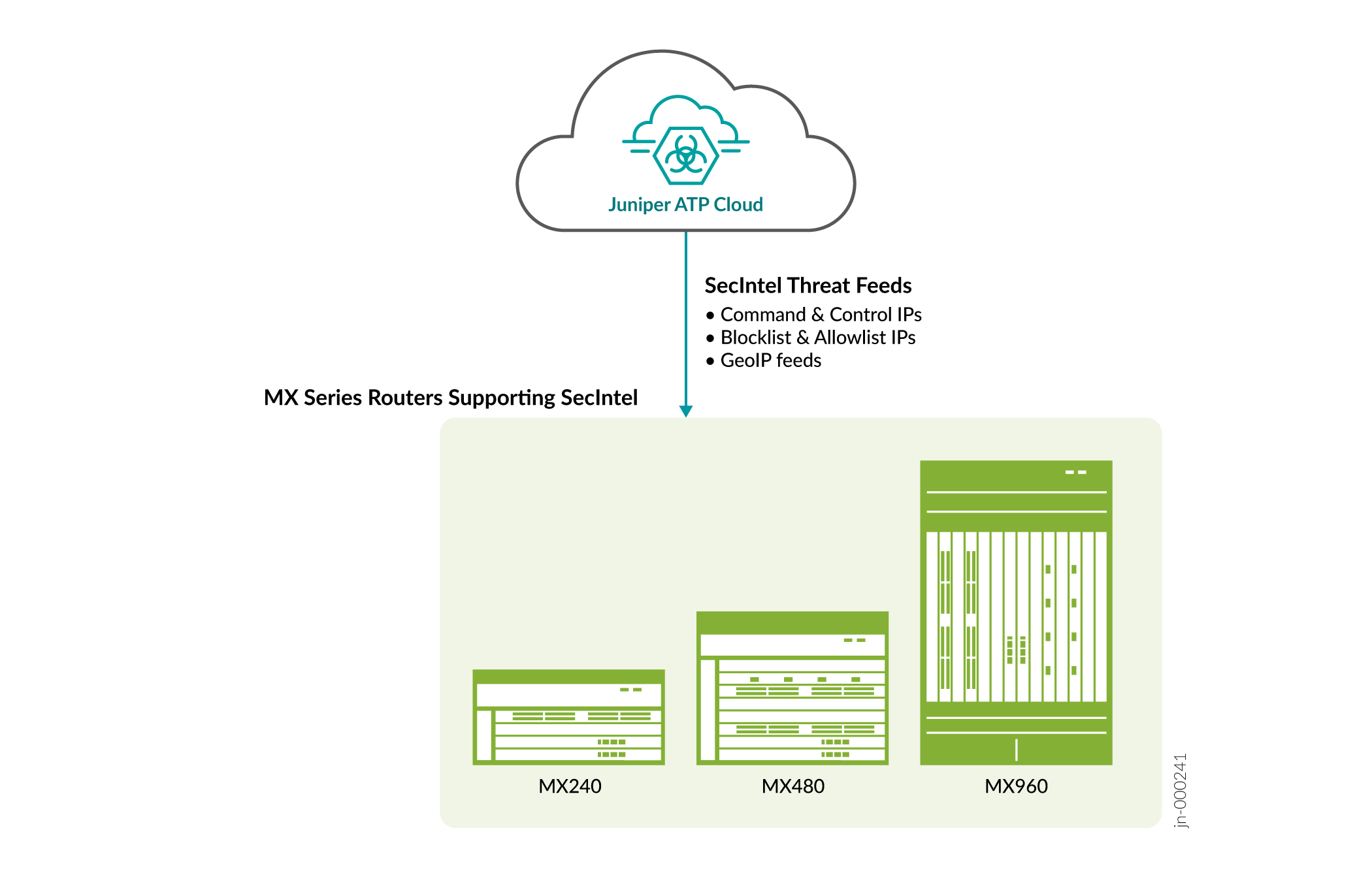
In earlier releases, MX Series routers downloaded SecIntel feeds through Junos Space Security Director/ Policy Enforcer. Starting in Junos OS Release 22.1R1, MX Series routers can download global SecIntel feeds directly from Cloud Feeds without enrolling to Juniper ATP Cloud.
In this use case, we'll see how to enroll an MX Series router to Juniper ATP Cloud without connecting to Junos Space Security Director or Policy Enforcer.
Topology
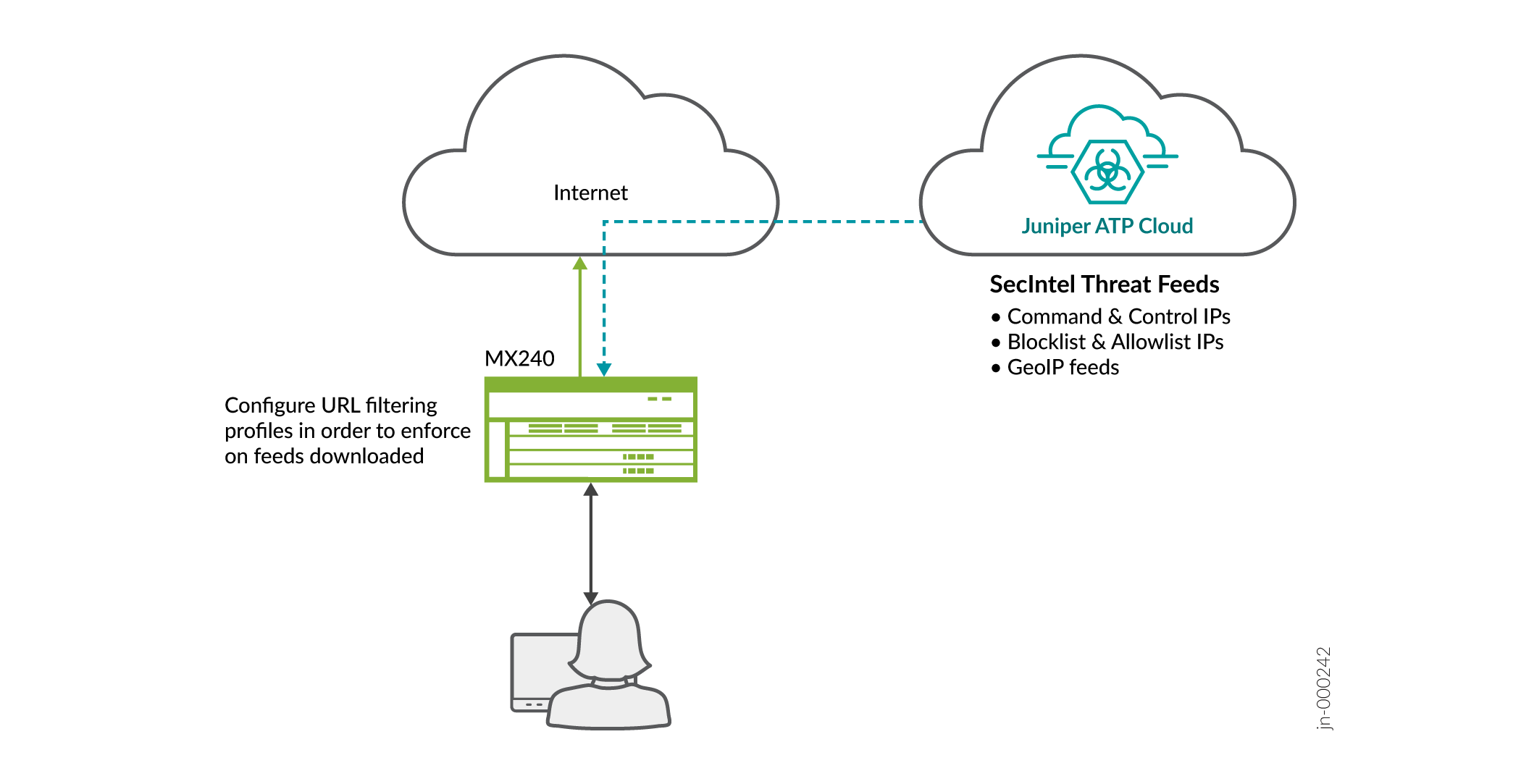
Prerequisites
- Juniper SecIntel for MX Series Universal Router license ( -S-MXxxx-CSECINTELx).
Workflow
-
Get a SecIntel license from Juniper for your MX Series Universal Router. For MX Series Universal Router licenses, see Software Licenses for MX Series Routers and MPC Service Cards. You will need the Software Serial Number (SSRN).
-
Enroll the MX Series router to Juniper ATP Cloud.
-
Verify the feeds from Juniper ATP Cloud.
-
Implement filtering configuration to enforce the downloaded feeds.
Configurations required on MX Series router
- Enrollment script
- Filter configuration
You can only configure US region cloud feed endpoint. All the MX cloud feed request are served only from US region CF.
Software Support Reference Number (SSRN) is a software serial number provided on the fulfillment document which ships electronically following the purchase of your Juniper software license.
If the license has already
been installed for your software, the Software Support Reference Number (SSRN) might be
obtained by running the show system license command. The SSRN is included
as the first 12 numerical digits of the 'Software Serial Number' listed in JUNOS.
Some products will report their SSRN in the below format, which creates a unique identifier for each software instance purchased. In this scenario, remove the suffix letters, which will leave the actual numeric SSRN to be used for support entitlement purposes.
> show system license Software Serial Number: XXXXXXXXXXXX-abcdef Support Reference Number: XXXXXXXXXXXX
To receive feeds from Cloud feeds, first enroll the MX Series router with Juniper ATP Cloud. Sample command to enroll is:
rootuser> op url https://amer.sky.junipersecurity.net/v2/skyatp/ui_api/bootstrap/enroll/secintel/mx/mx-secintel.slax version 21.3XYZ is valid for bootstrapping. Please provide the Juniper SecIntel license SSRN or press 0 to cancel Secintel license SSRN: XXXXXXXXXXXXXXXX
To remove the SecIntel configuration from MX Series router, you must dis-enroll the device. Sample command to dis-enroll is:
rootuser> op url https://amer.sky.junipersecurity.net/v2/skyatp/ui_api/bootstrap/disenroll/secintel/mx/mx-secintel.slaxversion 21.3XYZ is valid for bootstrapping. Please provide the activation code or press 0 to cancel SSRN: XXXXXXXXXXXXXXXX
The following global SecIntel feeds are available for MX series routers:
- cc_ip_data
- cc_ipv6_data
- cc_ip_blocklist
- geoip_country
- geoip_country_ipv6
Benefits
- No complex setup using Junos Space SD or PE.
- Simple configuration to enforce downloaded feeds.
Use Case 2: Enrollment to Juniper ATP Cloud Using Junos Space Security Director and Policy Enforcer.
In this use case, we'll see how to enroll an MX Series router to Juniper ATP Cloud using Junos Space Security Director and Policy Enforcer.
Topology
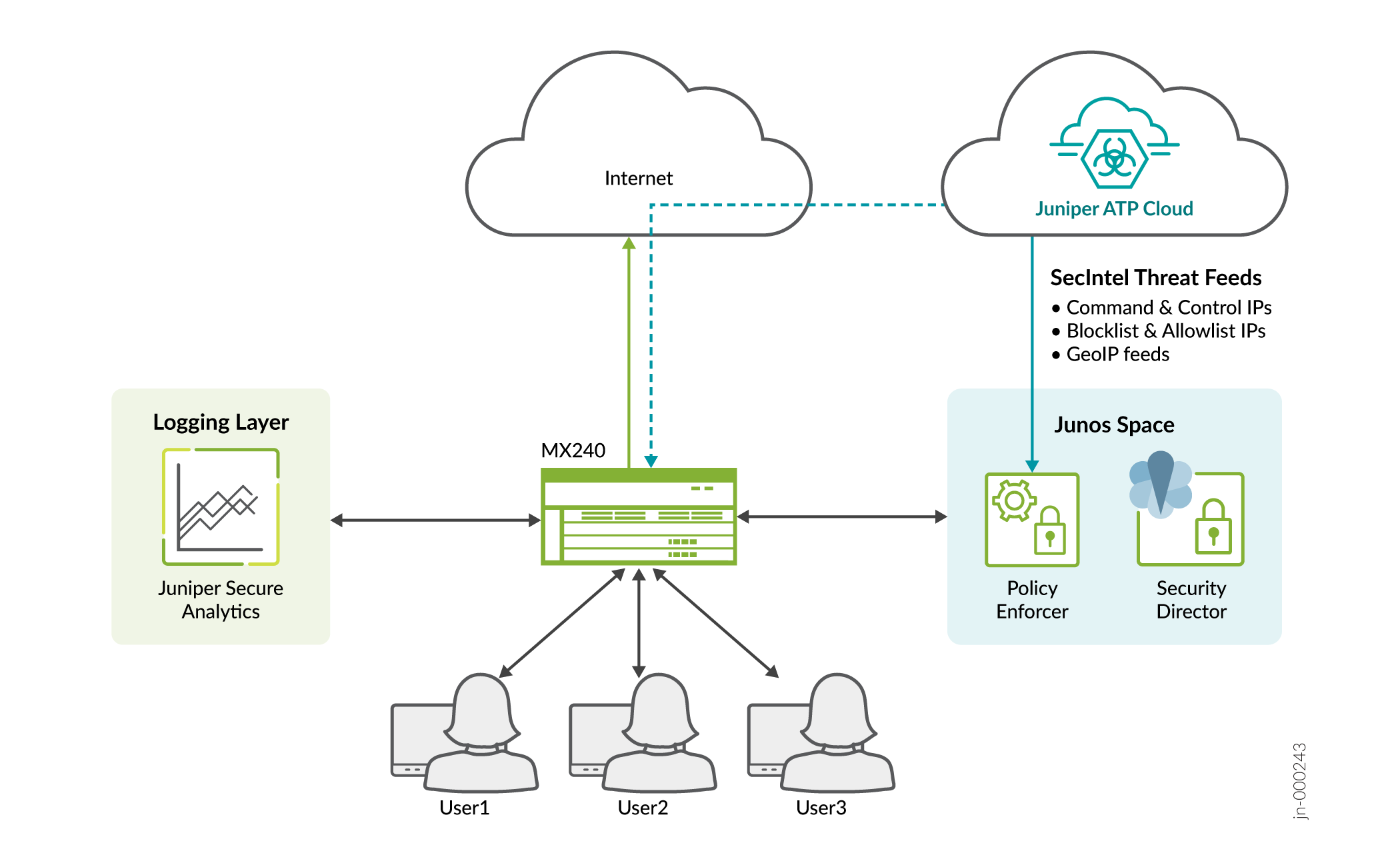
Workflow
- Configuration of Junos Space Security Director and Policy Enforcer.
- Discovery of MX Series router in Junos Space added as a device in Threat Protection Fabric (This is enrollment process for MX Series router to Policy Enforcer).
- License requirements (Reach out to Juniper Sales / Account Team).
Configuration required on MX Series router and SD/PE
- Custom feed configuration in SD.
- Understanding how feeds are applied on MX Series router.
- Filter configuration on MX Series router.
Benefits
- Feeds can be customized for each customer’s serviced by a VRF on the service providers router.
- All threat mitigation are processed at line rate improving performance.
Use Case 3: Identify and Block Command-and-Control Traffic on MX Series Router
In this use case, we'll see how to block C&C traffic at the network edge in a connected security setup. Here, the client is trying to reach a C&C server and the MX router is used to block the traffic.
Topology
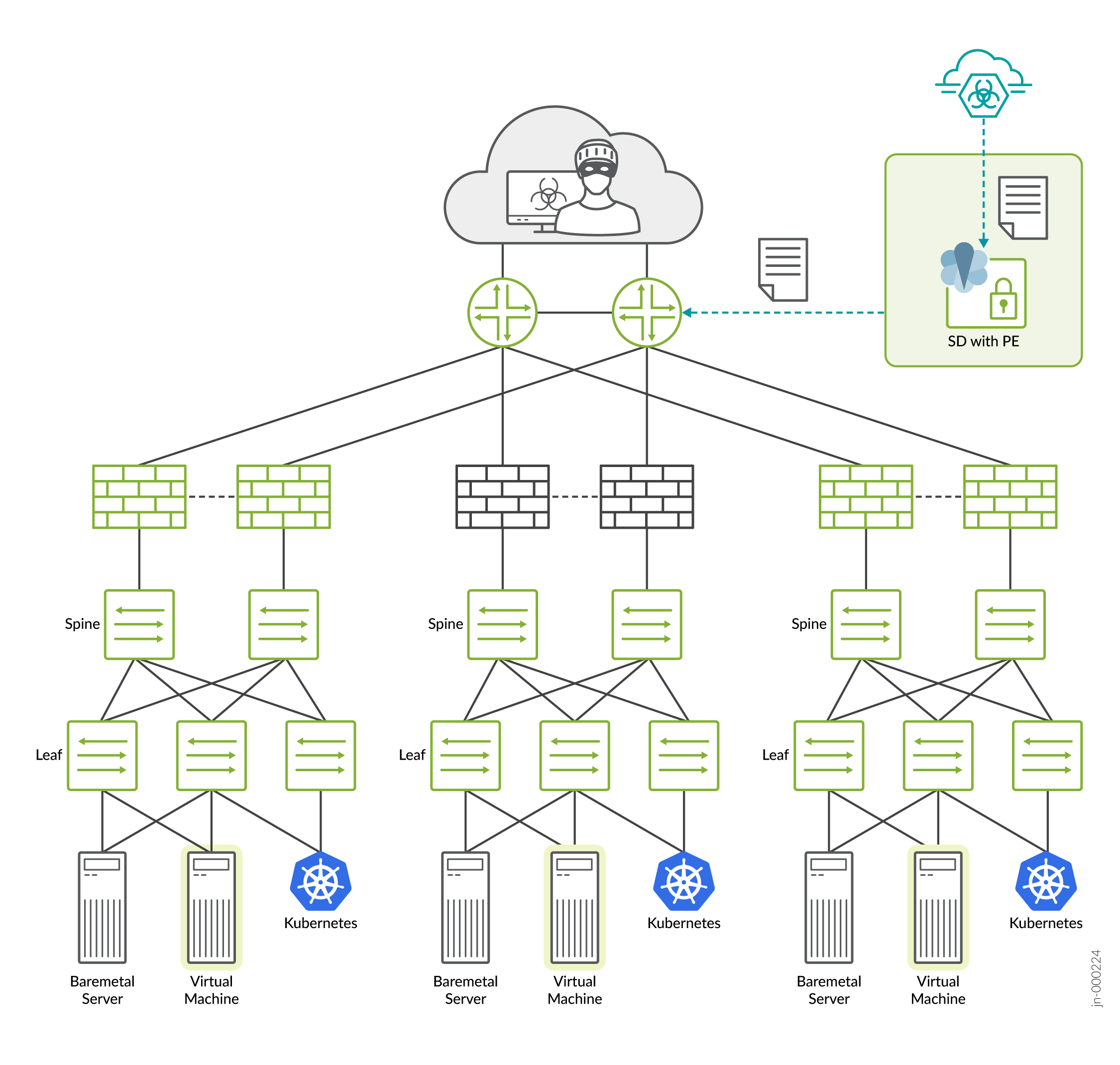
Configurations required on MX Series router and SD/PE
-
Juniper ATP Cloud C&C feed and Security Director with Policy Enforcer.
-
Juniper MX Series router
Workflow
-
Policy Enforcer downloads C&C feed from Juniper ATP Cloud.
-
Juniper MX Series router downloads C&C feed from Policy Enforcer.
-
Juniper MX Series router adds IP data to Ephemeral DB filter.
-
Juniper MX Series router drops traffic to/from C&C servers listed in C&C feed, protecting against Botnets & Malware.
-
Juniper MX Series router offloads C&C protection from firewalls that are under load or cannot support C&C feeds.
For configuration details, see SecIntel on MX Demo.
