ON THIS PAGE
Using Static, eBGP, PIM, and OSPF Protocols to Connect to Third-Party Network Devices
Starting in Contrail Networking Release 2003, you can use the Contrail Command user interface (UI) to connect the border gateway devices to third-party devices that are not managed by Contrail Networking. In earlier releases, Contrail Networking did not support connecting to an unmanaged third-party device. However, with this release, you can use the Contrail Command UI to configure border leaf devices or spine devices to connect to third-party devices.
Overview
You can use the Contrail Command user interface (UI) to connect to third-party devices that are not managed by Contrail Networking. If you want to connect two border leaf devices to a third-party device, you have to create routed virtual networks. You then create a virtual port group to connect the physical interfaces of the border leaf devices to the unmanaged third-party device. You then create logical routers and associate the routed virtual networks with the logical routers. You can configure eBGP and static routing protocols between the logical router and the unmanaged third-party device. Starting in Contrail Networking Release 2005, you can also configure PIM and OSPF routing protocols between the logical router and the unmanaged third-party device. However, the routing protocol that you can configure depends on the border gateway device that you use. Configuration is then pushed to the border gateway devices and a connection is formed between the fabric and the external network through the third-party unmanaged device.
For example, service chaining through a physical network function (PNF) such as a firewall or a loadbalancer are different use cases that use third-party devices. The PNF is outside the fabric, and you use Contrail Networking to configure border gateway devices to steer traffic through the PNF. Another example is to provide connectivity between tenant virtual networks that are in the fabric, and external layer 3 networks that are connected by a third-party router. This topic is an example of PNF service chaining between tenant virtual networks through an external firewall cluster.
The general workflow is as follows:
-
Create routed virtual networks. Define the routed virtual network for each security zone between border gateway devices and third-party device.
A routed virtual network represents a layer 3 subnet between the fabric (border gateway) and the external physical network function.
-
Configure virtual port groups. Connect the border gateway devices on the fabric to the third-party device by using EVPN Ethernet Segment Identifier-Link Aggregation Group (ESI-LAG) interface.
-
Configure logical routers and configure Integrated Routed and Bridging (IRB) interface by manually configuring the IP address of the IRB interface of the logical router.
-
Configure the routing protocols (eBGP, static, PIM, or OSPF) between the logical router and the external physical network function (for example, a firewall).
Note:The routing protocol that you can configure depends on the border gateway device that you use.
Steps to Connect to a Third-Party Device
- Topology
- Before You Begin
- Create Routed Virtual Networks
- Create Routed Virtual Port Groups
- Create Logical Routers
Topology
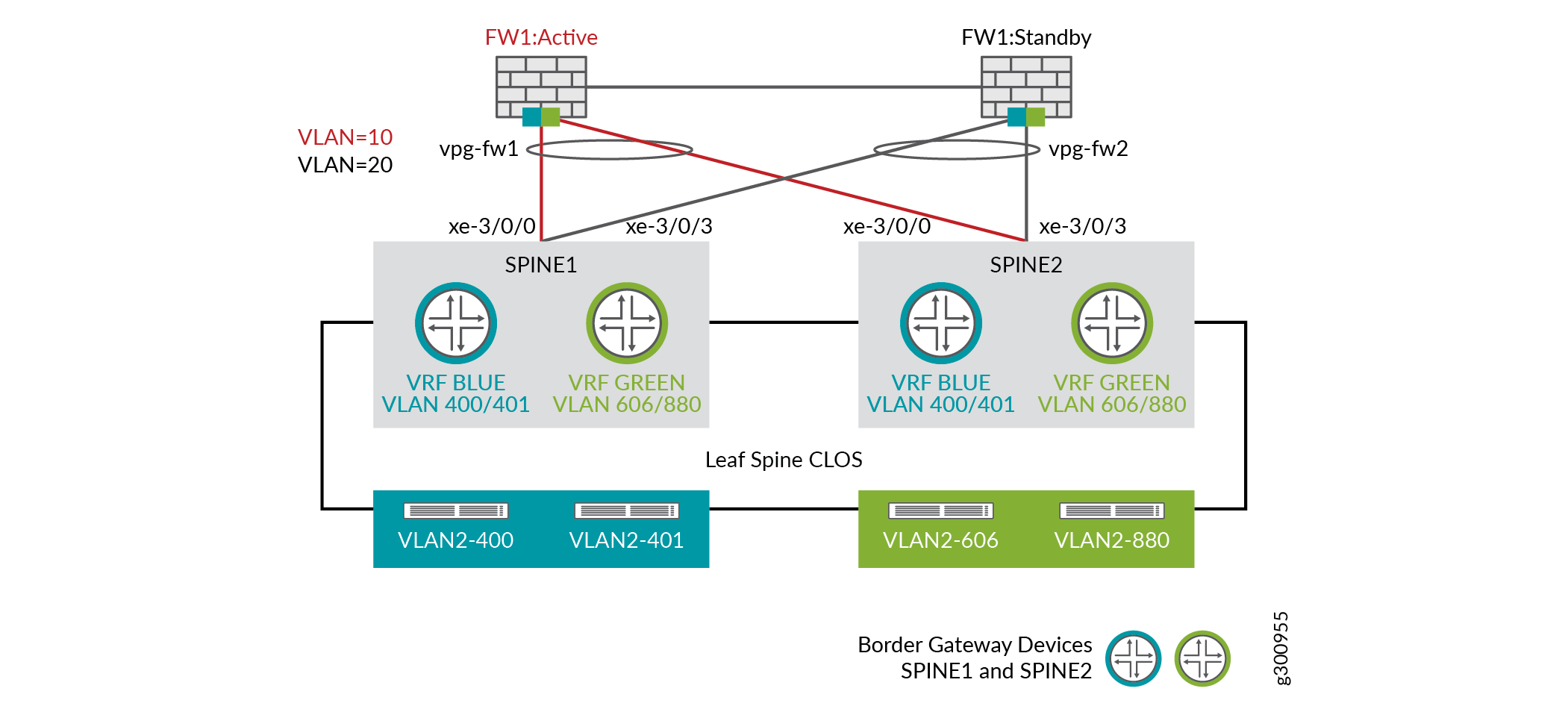
Figure 1 is an example topology of how you can connect to an unmanaged third-party (Firewall) device.
In this topology, there are two firewall zones, blue and green. There are two virtual networks associated with each zone. VLAN2-400 and VLAN2-401 are the virtual networks in the blue zone. VLAN-606 and VLAN-880 are the virtual networks in the green zone. Each zone has a logical router that is created on spine devices. These spine devices are configured with CRB-Gateway roles. Traffic between the virtual network subnets within the same zone is routed within the logical router VRF routing table on the spine.
This topology shows that the traffic between the green zone and the blue zone passes through the firewall cluster which is connected to the two spine devices. The spine devices also act as the border gateway devices. The two PNF firewalls are clustered in the A-S (active-standby) mode and is represented as a single device. The routing protocol on the logical router on the QFX device to the firewall cluster, will use the virtual gateway IP (VIP) of the firewall cluster as the next-hop (BGP peer) address.
The logical routers are created on the border gateway devices. You extend the tenant virtual networks and the routed virtual networks to the logical router.
The two blue tenant virtual networks and the two green tenant virtual networks are connected to the border gateway devices. Traffic from the blue tenant virtual networks has to pass through the third-party firewall (FW1:Active) to reach the green tenant virtual networks.
Follow these steps to connect to a third-party device not managed by Contrail Networking.
Before You Begin
Before you begin, ensure that you have
-
Discovered and onboarded fabric devices.
-
Assigned physical and routing-bridging roles to devices.
-
The tenant virtual networks are already created and are associated with TOR switches.
The VPGs are already created on the TOR switches.
-
-
You can use a QFX Series device with CRB-Gateway, CRB-MCAST-Gateway, DCI-Gateway, or DC-Gateway roles assigned, as border gateway device.
However, in this topology, the ERB-UCAST-Gateway role cannot be configured on the border gateway device. You will not be able to reconfigure physical routers and configure routed virtual network properties if you assign ERB-UCAST-Gateway role to border gateway device.
Note:We recommend that you use QFX10000 series switches in border leaf and spine roles for the border function in an EVPN fabric.
If you use a QFX Series switch as the border gateway device, you can configure eBGP, static, PIM, or OSPF routing protocols on the border gateway device.
-
Starting in Contrail Networking Release 2008, you can use MX240, MX480, MX960, or MX10003 device as a border leaf and spine device, to connect to third-party network devices. You can assign CRB-Gateway, CRB-MCAST-Gateway, DCI-Gateway, or DC-Gateway roles to these border gateway devices.
If you use an MX Series router as the border gateway device, you can configure eBGP and static routing protocols on the border gateway device.
-
Create Routed Virtual Networks
Procedure
Step-by-Step Procedure
A routed virtual network is used to extend a fabric that is managed by Contrail Networking to a third-party device. By creating a routed virtual network, you create layer 3 links between border gateway devices and third-party devices. You can run eBGP, static, PIM, or OSPF routing protocols between these border gateway devices and third-party devices.
If you use an MX240, MX480, MX960, or MX10003 device as border gateway devices, you can only configure eBGP and static routing protocols on the border gateway devices.
Contrail Networking Release 2003 supports creating a routed virtual network from the Overlay>Virtual Networks page of the Contrail Command UI.
You create two routed virtual networks, VN-BLUE and VN-GREEN, for this workflow. Follow these steps to create a routed virtual network:
-
Navigate to Overlay>Virtual Networks.
The All Networks page is displayed.
-
Click Create to create a network.
The Create Virtual Network page is displayed.
-
Enter VN-BLUE in the Name field.
-
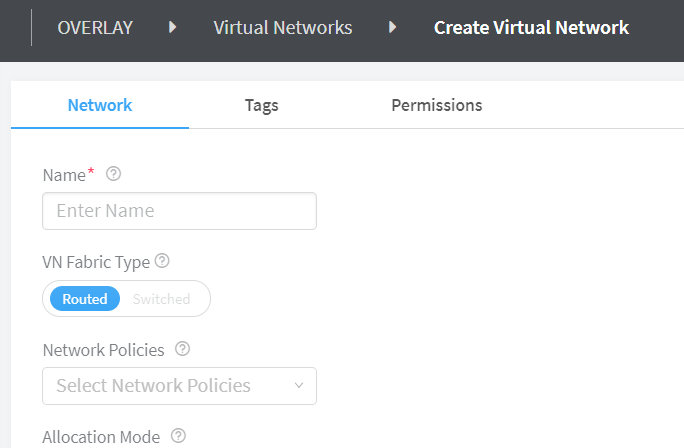
Select Routed VN Fabric Type to create a routed virtual network.
With Contrail Networking Release 2003, you select Routed from the VN Fabric Type field to create a routed virtual network. See Figure 2.
Figure 2: Create Routed Virtual Network -
In the Subnets section, click +Add to add a new subnet.
Enter the CIDR for this routed virtual network in the CIDR field.
You do not configure Allocation Pools, Gateway, DNS or DHCP for the subnet CIDR of a routed virtual network. These fields are greyed out by default.
Note:Do not configure options such as Host Routes; Floating IP Pools; Fat Flows; Routing, Bridging, and Policies; and Advanced options for a routed virtual network. Fields with default values can be left as is.
-
Click Create to create the routed virtual network.
The routed virtual network that you created is displayed on the Virtual Networks page.
Repeat steps 2 through 6 to create the Green-VN routed virtual network.
Create Routed Virtual Port Groups
Procedure
Step-by-Step Procedure
A virtual port group (VPG) is a group of one or more physical interfaces attached to one or more virtual machine interfaces (VMI). Each VMI object corresponds to a VLAN ID and is attached to a Virtual Network. For more information, see Virtual Port Groups.
The VPG workflow provides a framework for you to configure the connection between the external device (PNF) and the border gateway devices of the fabric by using the EVPN ESI-LAG. The VPG is configured as a routed VPG and is associated with the routed virtual networks.
Contrail Networking Release 2003 supports creating a routed virtual port group from the Overlay>Virtual Port Group page of the Contrail Command UI. A routed VPG can only contain routed virtual networks.
Follow these steps to create a routed virtual network:
-
Navigate to Overlay>Virtual Port Group>Create Virtual Port Group.
The Create Virtual Port Group page is displayed.
-
Enter a name for the virtual port group in the Virtual Port Group Name field.
-
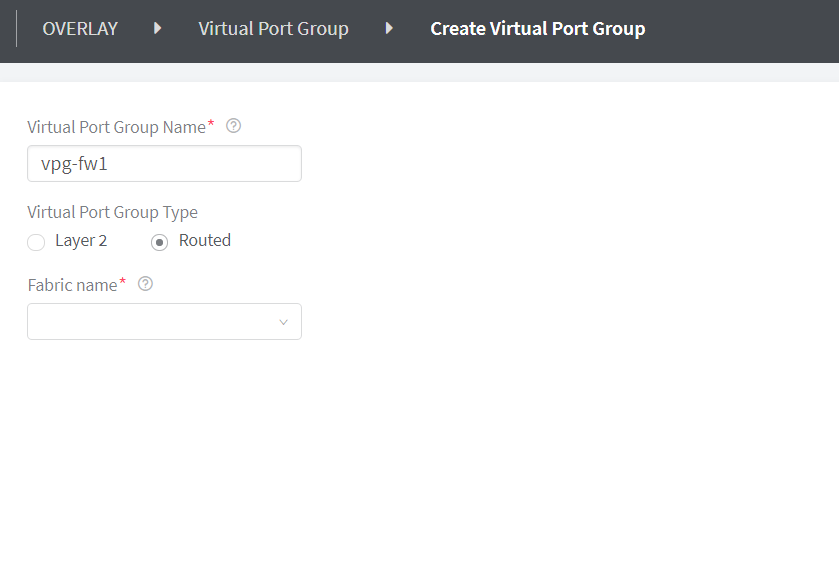
Select Routed virtual port group type.
With Contrail Networking Release 2003, you can create a routed virtual port group from the Contrail Command UI. Select the Routed option button to create a routed virtual port group. Select Layer 2 option button to create a virtual port group. See Figure 3.
Figure 3: Create Routed Virtual Port Group -
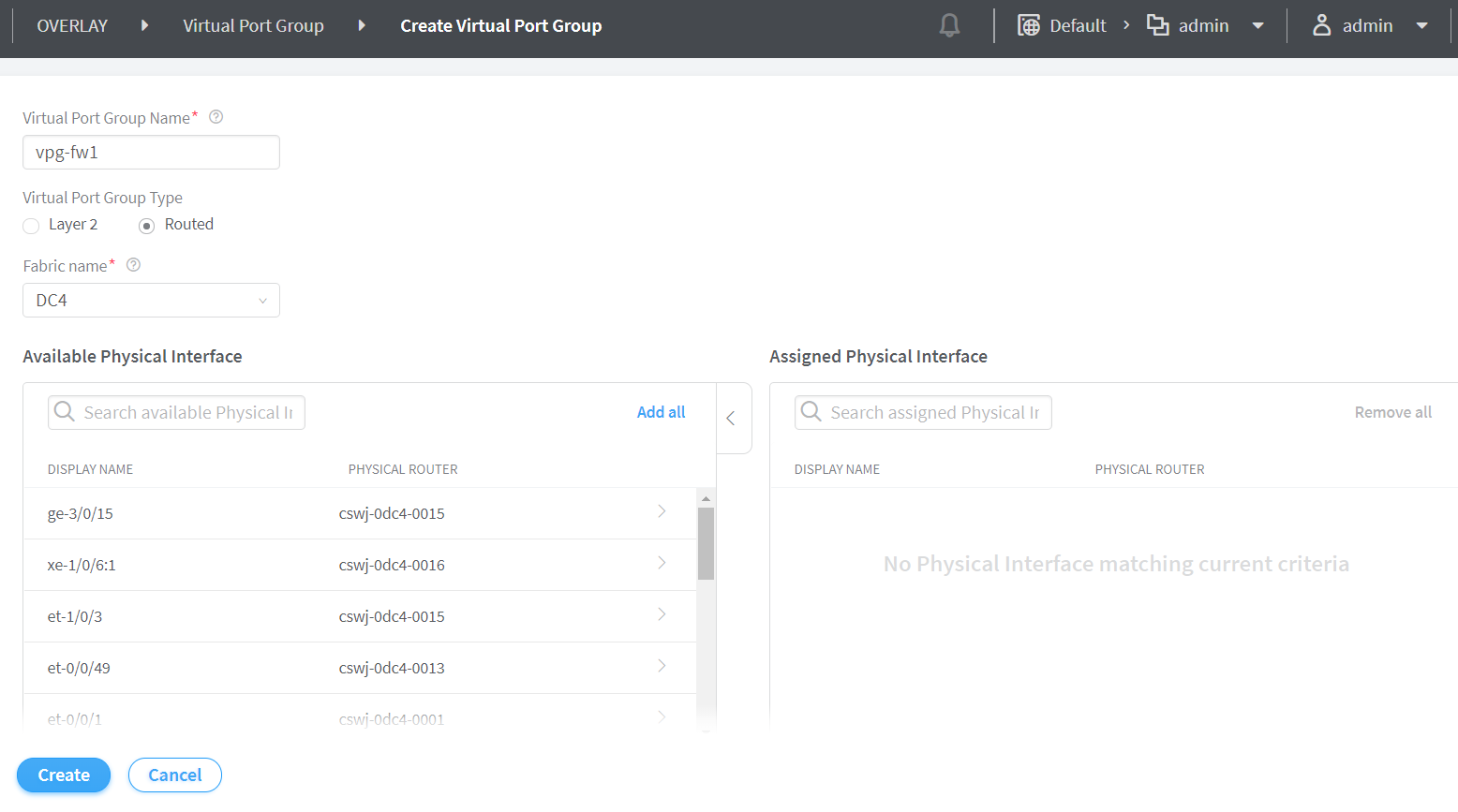
Select the fabric from the Fabric Name list.
The available interfaces and physical routers in the selected fabric are listed in the Available Physical Interface box.
-
From the Available Physical Interface box, select the physical interfaces to be included in the virtual port group by clicking the arrow next each physical interface. The available physical interfaces are the interfaces available on TORs that are already onboarded. It also includes the associated physical router.
The selected interfaces are displayed in the Assigned Physical Interface box.
Figure 4: Assign Physical Interface -
Enter the following information in the VLAN section.
-
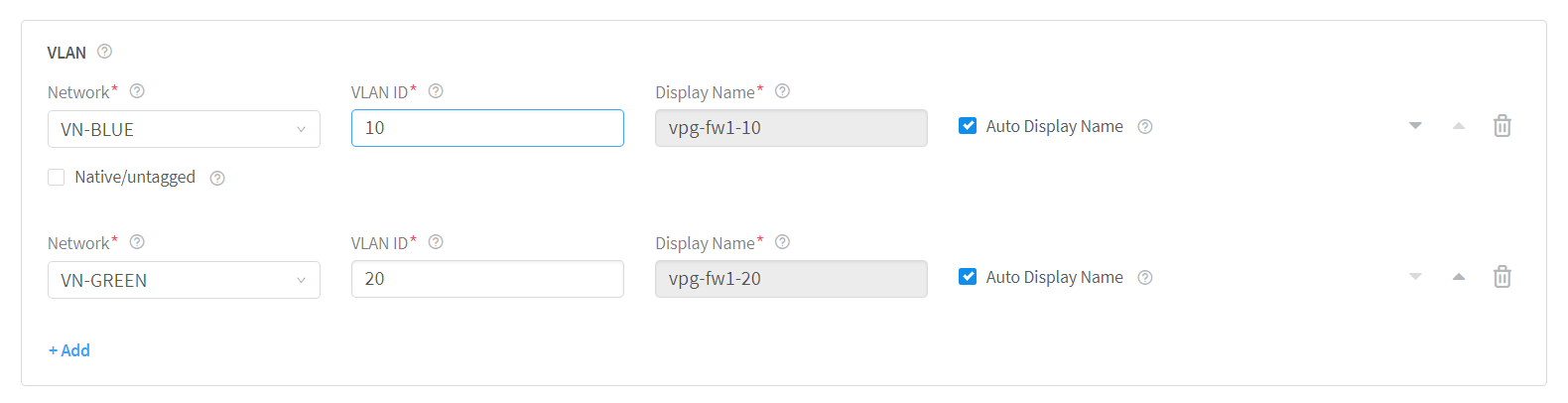
Select the routed virtual network from the Network list.
For the blue network, select VN-BLUE. See Figure 5. For the green network, select VN-GREEN.
-
Enter VLAN ID and the network to which the VLAN is associated.
For VN-BLUE virtual network, enter 10. For VN-Green virtual network, enter 20.
-
Enter the VPG name. If the Auto Display Name field is selected, this field is autogenerated from the virtual port group name.
-
Select Auto Display Name if you want the VLAN name to be autogenerated from the virtual port group name.
-
Select the Native/untagged check box to allow untagged virtual network. You cannot select the same virtual network more than once if the check box is not selected.
Click +Add to add VN-GREEN routed virtual network information. Repeat steps provided in step 6.
Figure 5: Select Network -
-
Click Create.
The newly created routed virtual port group is displayed on the Virtual Port Group page.
Create Logical Routers
Procedure
Step-by-Step Procedure
A logical router performs a set of tasks and replicates the functions that can be handled by a physical router. A logical router connects multiple virtual networks.
You create two logical routers, LR-BLUE and LR-Green, for this workflow. Follow these steps to create LR-Blue.
-
Navigate to Overlay>Logical Routers page.
The Logical Routers page is displayed.
-
Click Create.
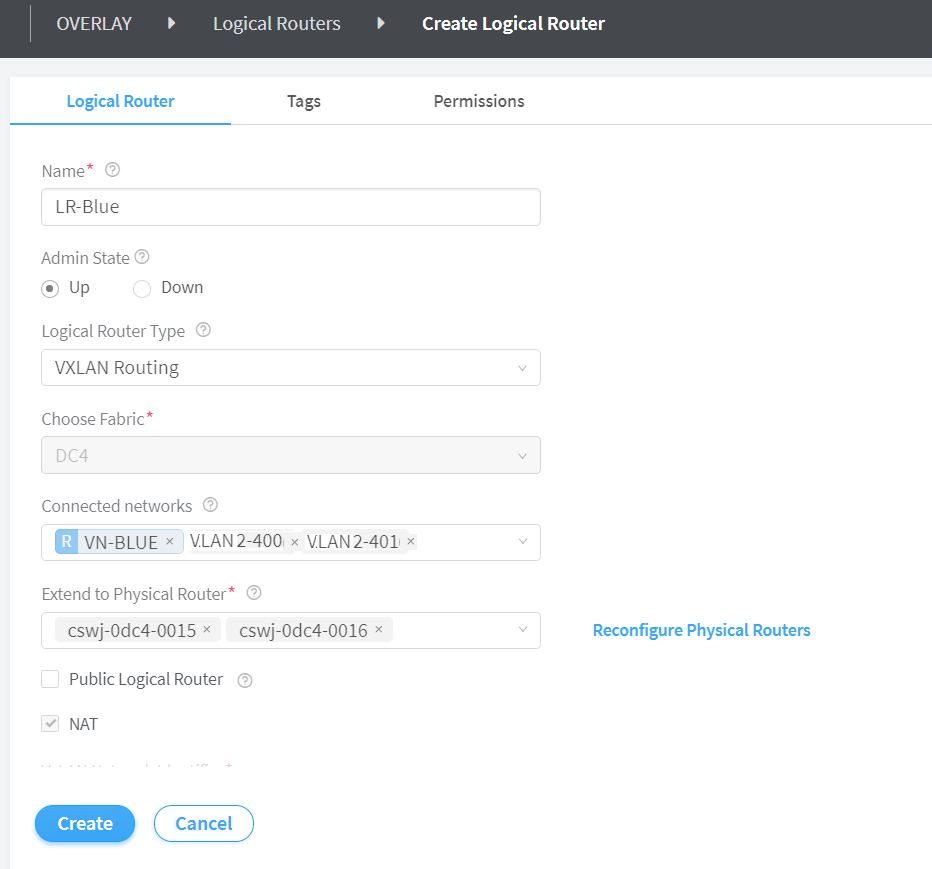
The Create Logical Router page is displayed. See Figure 6.
-
Enter LR-Blue in the Name field.
-
Select Up from the Admin State list.
This is the administrative state that you want the device to be in when the router is activated.
-
Select VXLAN Routing from the Logical Router Type list.
-
Select the fabric from the Choose Fabric list.
-
Select the networks you want to connect to this logical router from the Connected Networks list.
When you want overlay tenant traffic to pass through a third-party device, select both tenant virtual networks and routed virtual network from the from the Connected Networks list.
In this step, select VN-BLUE as the routed virtual network and select VLAN2-400 and VLAN2-401 as its two associated tenant virtual networks. See Figure 6.
When you create the LR-Green logical router, you select VN-GREEN as the routed virtual network and select VLAN2-606 and VLAN2-880 as its two associated tenant virtual networks in this step.
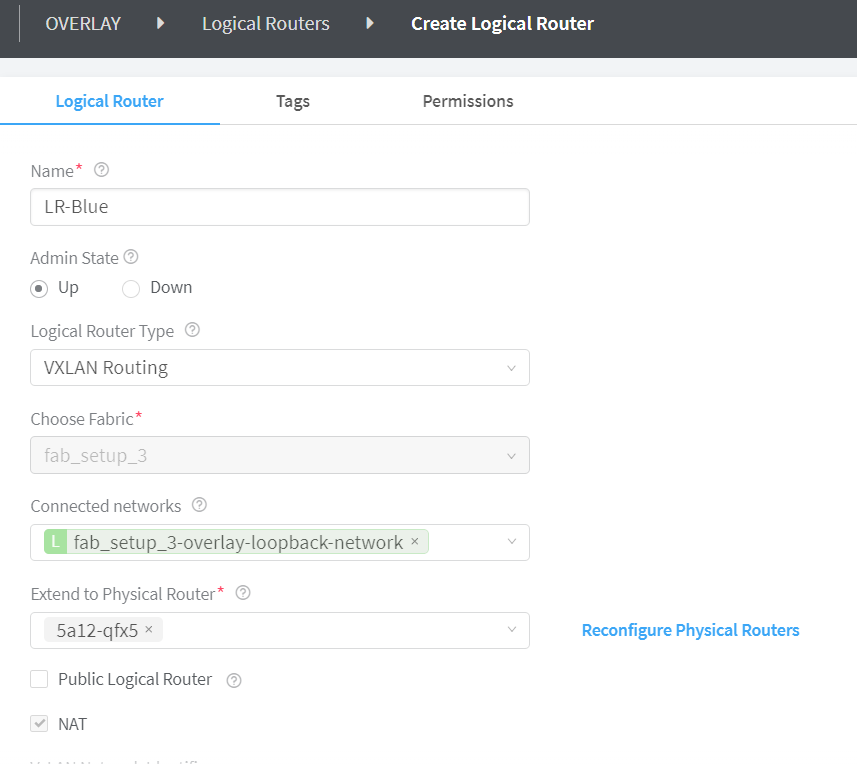
Figure 6: Create Logical RouterAdding a Loopback Routed Virtual Network—Starting in Contrail Networking Release 2005, you can connect a loopback routed virtual network to a logical router. You can select a loopback routed virtual network from the Connected Networks list only if you have provided loopback subnet information during the fabric onboarding process. For more information, see Create a Fabric. Loopback subnet information can also be added after fabric onboarding from the Infrastructure>Fabric> Fabric Name >Namespaces page.
Note:If you have not provided loopback subnet information during fabric onboarding, you will not be able to select a loopback routed virtual network from the Connected Networks list.
When you select a routed virtual network from the Connected Networks list, the letter R is automatically added before the name to denote that the virtual network selected is a routed virtual network. See Figure 6.
When you select a loopback routed virtual network from the Connected Networks list, the letter L is automatically added before the name to denote that the virtual network selected is a lookback routed virtual network. See Figure 7.
When you select a routed virtual network, the Reconfigure Physical Routers link is enabled.
Figure 7: Adding a Loopback Routed Virtual Network -
Select the physical router(s) to which you want to extend virtual networks or routed virtual networks to, from the Extend to Physical Router list.
A physical router provides routing capability to the logical router. You can extend the networks that you selected in step 7 to multiple physical routers.
-
After you extend the networks to the physical router, you can reconfigure the physical router by clicking Reconfigure Physical Router. See Figure 6.
Step-by-Step Procedure
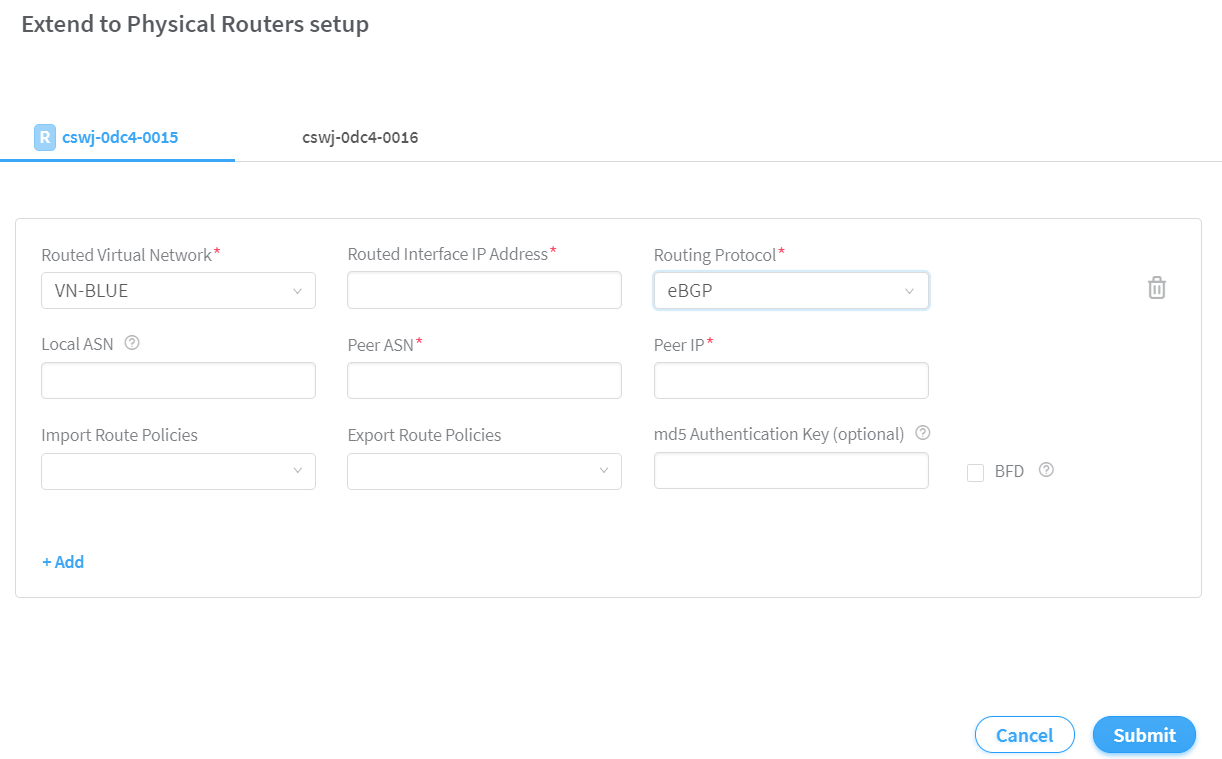
After you click Reconfigure Physical Router, the Extend to Physical Routers setup page is displayed. See Figure 8.
Enter the following information for each router.
Figure 8: Extend to Physical RouterNote:Loopback routed virtual network can only be configured with eBGP routing protocol.
-
Select the VN-BLUE routed virtual network from the Routed Virtual Network list.
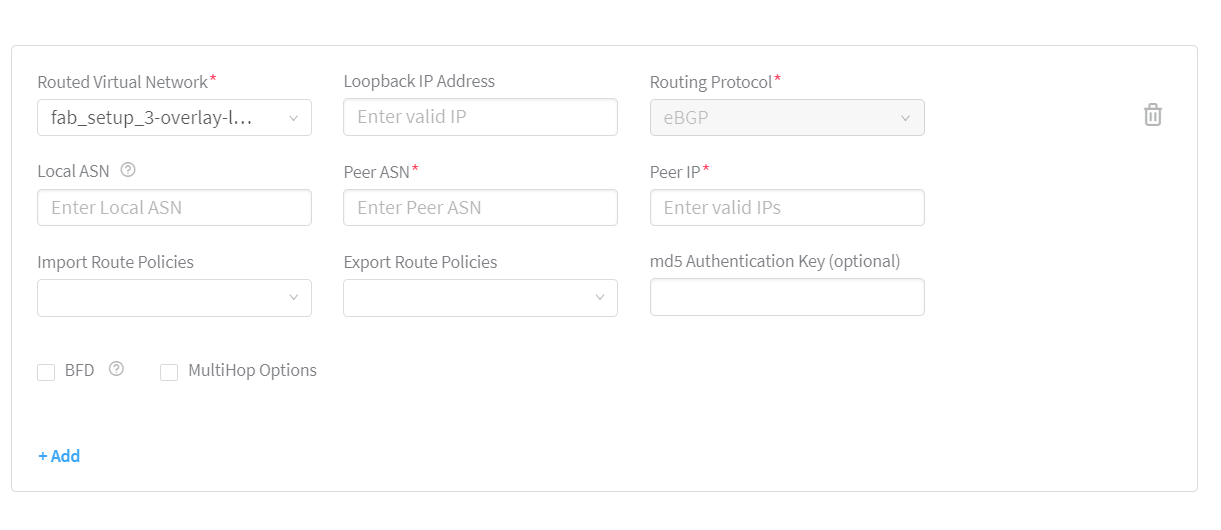
If you select a loopback routed virtual network from the Routed Virtual Network list, the Routing Protocol list is disabled. The default protocol selected is eBGP. For example, see Figure 9.
Starting in Contrail Networking Release 2005, you can configure BFD with eBGP, static Route, OSPF, and PIM protocols.
Note:If you use an MX240, MX480, MX960, or MX10003 device as border gateway devices, you can only configure eBGP and static routing protocols on the border gateway devices.
-
Enter IP address in the Routed Interface IP Address field.
The routed IP address that you enter must be from the subnet that you provided while creating the routed virtual network.
If you have selected a loopback routed virtual network from the Routed Virtual Network list, the Loopback IP Address field is displayed instead of the Routed Interface IP Address field. In this case, the loopback IP address that you enter must be from the loopback subnet that you provided during the fabric onboarding process.
Figure 9: Selecting a Loopback Routed Virtual Network -
Select eBGP, Static Routes, OSPF, or PIM routing protocols from the Routing Protocol list.
Note:If you use an MX240, MX480, MX960, or MX10003 device as border gateway devices, you can only configure eBGP and static routing protocols on the border gateway devices.
-
Step-by-Step Procedure
Follow these steps if you have either selected eBGP as the routing protocol (Figure 8) or if you have selected a loopback routed virtual network from the Routed Virtual Network list (Figure 7):
-
Enter Autonomous System (AS) number in the Local ASN field.
This is the logical router (VRF routing instance) AS number. If you do not provide an AS number, the overlay iBGP AS number provided during fabric onboarding will be used.
-
Enter peer AS number in the Peer ASN field.
This is the AS number of the third-party device.
-
Enter the IP address of the unmanaged third-party device in the Peer IP field.
Note:The IP address that you enter must be from the subnet that you provided while creating the routed virtual network.
-
Select import routing policies that you want to apply to this eBGP session from the Import Route Policies list.
Note:You can add routing policies from the Overlay>Routing>Routing Policies page of the Contrail Command UI.
-
Select export routing policies that you want to apply to this eBGP session from the Export Route Policies list.
-
(Optional) Enter md5 authentication key in the md5 Authentication Key field.
You can enter the key in plain text or in encrypted format that starts with $9.
-
(Optional) Select BFD check box to enable bidirectional forward detection.
After you enable BFD, provide detection time and multiplier information in the Interval (ms) and Multiplier fields respectively.
-
If you have selected another physical router in step 8, click the next tab to enter information.
-
Click Submit to submit configuration information.
-
-
Step-by-Step Procedure
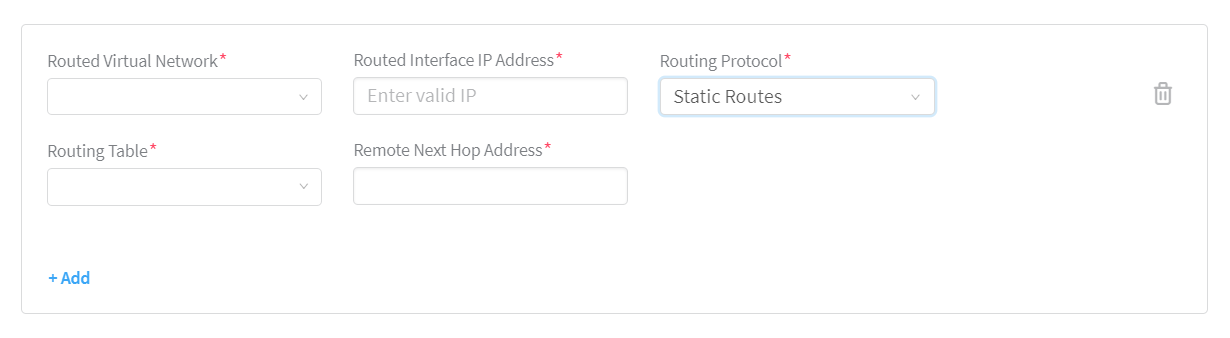
Enter the following information if you have selected Static Routes as the protocol:
Note:In order to select Static Routes as the protocol, you must create an interface route table.
Follow these steps to create an interface route table:
-
Navigate to Overlay>Routing>Interface Route Tables and click Add.
The Create Interface Route Tables page is displayed.
-
Enter a name for the interface route table in the Name field.
-
Click Add to add Prefix and Community information.
-
(Optional) Click Add to define another prefix list.
-
Click Create to create the interface route table.
-
Select the interface route table from the Routing Table list. See Figure 10.
The interface route table lists the prefixes that can be used in the static route configuration.
-
Enter next hop IP address in the Remote Next Hop Address field.
-
Click Submit to submit configuration information.
Figure 10: Static Route Routing Protocol
-
-
Step-by-Step Procedure
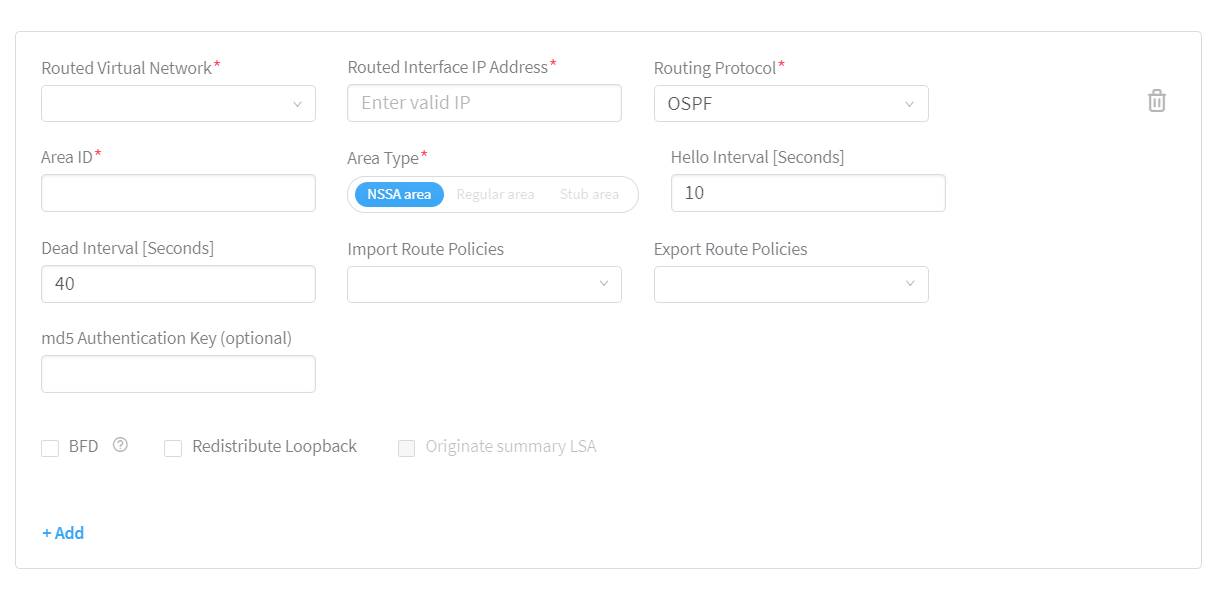
Enter the following information if you have selected OSPF as the routing protocol:
Note:You cannot configure OSPF routing protocol on the border gateway devices if you use MX240, MX480, MX960, or MX10003 devices as border gateway devices.
-
Enter the area ID in the Area ID field. See Figure 11.
The area ID is provided in x.x.x.x format.
-
Select any one of the following area type.
-
NSSA Area—An NSSA Area or a not-so-stubby area allows external routes to be flooded within the area.
-
Regular Area—Regular areas are areas that are not backbone areas (Area ID: 0.0.0.0), Stub areas, or NSSA areas.
-
Stub Area—Stub areas are areas through which autonomous system (AS) external advertisements are not flooded.
For more information, see Configuring OSPF Areas.
Note:If the area ID that you enter is 0.0.0.0, the Area Type field is disabled.
-
-
Enter hello interval in the Hello Interval [Seconds] field. The default value is 10 seconds.
-
Enter dead interval in the Dead Interval [Seconds] field. The default value is 40 seconds.
-
Select import routing policies that you want to apply to this OSPF session from the Import Route Policies list.
Note:You can add routing policies from the Overlay>Routing>Routing Policies page of the Contrail Command UI.
-
Select export routing policies that you want to apply to this OSPF session from the Export Route Policies list.
-
(Optional) Enter md5 authentication key in the md5 Authentication Key field.
You can enter the key in plain text or in encrypted format that starts with $9.
-
(Optional) Select BFD check box to enable bidirectional forward detection.
After you enable BFD, provide detection time and multiplier information in the Interval (ms) and Multiplier fields respectively.
-
Select Redistribute Loopback to advertise loopback IP address in an area type.
Redistribute loopback IP address can be selected only for one OSPF area type.
-
Select Originate Summary LSA check box to flood link-state advertisement (LSA) summary in to the selected area type.
This check box is disabled if
-
the area ID that you enter is 0.0.0.0.
-
you do not define an area type.
-
-
Click Submit to submit configuration information.
Figure 11: OSPF Routing Protocol
-
-
Step-by-Step Procedure
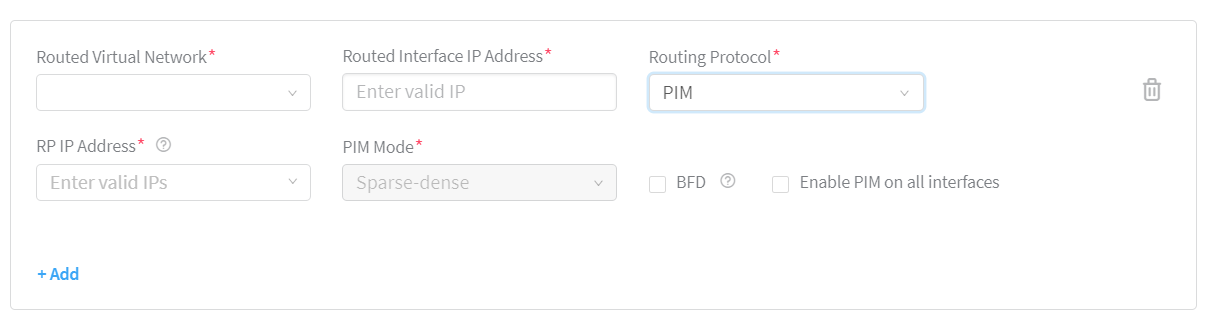
Enter the following information if you have selected PIM as the routing protocol:
Note:You cannot configure PIM routing protocol on the border gateway devices if you use MX240, MX480, MX960, or MX10003 devices as border gateway devices.
-
Enter rendezvous point (RP) IP address in the RP IP Address field. See Figure 12.
The RP IP address is the IP address of the router that receives multicast traffic. This IP address is autopopulated for every physical router. If the same physical router is allocated an RP IP address when configuring another router virtual network, this RP IP Address field is autopopulated with the same RP IP address.
-
PIM Mode field is disabled. The default PIM mode is Sparse-dense.
-
(Optional) Select BFD check box to enable bidirectional forward detection.
After you enable BFD, provide detection time and multiplier information in the Interval (ms) and Multiplier fields respectively.
-
Select Enable PIM on all interfaces check box to enable PIM on all IRB interfaces of the VRF.
-
Click Submit to submit configuration information.
Figure 12: PIM Routing Protocol
-
-
-
-
Enter the routed VXLAN ID in the VxLAN Network Identifier field,
-
Click Create to create the logical router.
Repeat steps 2 through 11 to create LR-Green logical router.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.