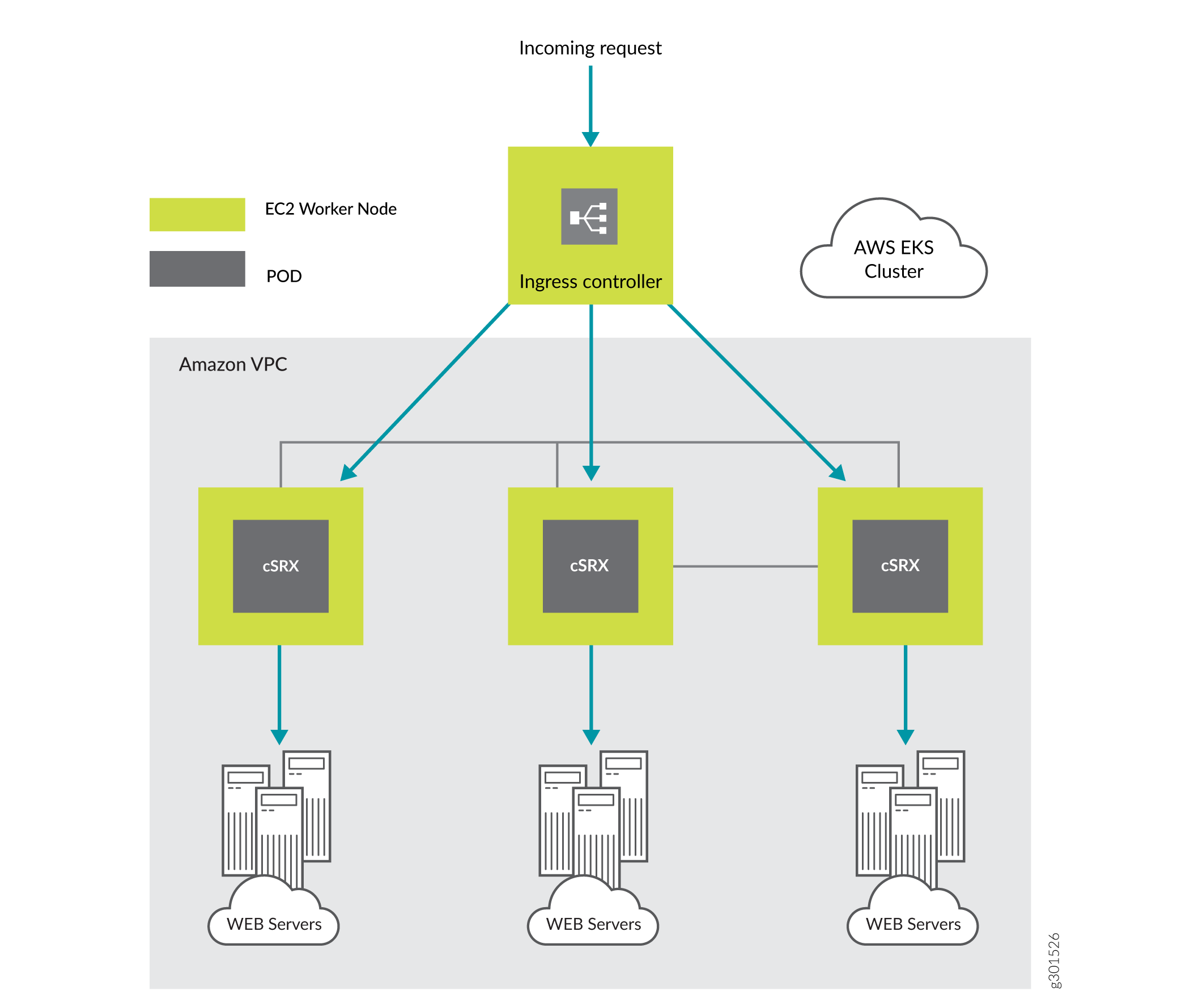
cSRX as a Service with Ingress Controller in Amazon EKS
The cSRX Container Firewall can be deployed as a service using a Network Load Balancer
with NGINX Ingress Controller on Amazon EKS. The cSRX deployed as a service in a deployment
object allows you to scale up and scale down by distributing the traffic among different cSRX
PODs. Also, cSRX functions as a firewall, protecting workloads deployed in the cluster with
rich advanced security services.
Figure 1 illustrates Amazon EKS ingress controller.
Figure 1: Amazon EKS Ingress Controller

To deploy the cSRX as Ingress controller on Amazon EKS:
- Define and deploy cSRX as K8s POD or as ReplicaSet. This type of deployment is the standard K8s to define and to manage resource. Also, allows you to deploy cSRX container on specified work nodes, update or rollback based on your request.
- Use Kubectl and YAML templates to define and to deploy cSRX related resource on command line. K8s API server can process the request from other applications.
- Expose cSRX as K8s service with load balancing. Amazon EKS supports Kubernetes Network Load Balancer (NLB) and Amazon EKS specific Application Load Balancer (ALB).
- The cSRX POD is identified with predefined selectors and exposed with supported load balancer. The load balancer is the NGINX ingress controller and AWS NLB as external load balancer.
- Connect cSRX container to the external network using Multus with flannel CNI. cSRX requires at least three interfaces (1 management port and 2 revenue ports).
