Identity-Aware Firewall
Learn about identity-aware firewall and its component authentication table.
Identity is the foundation for securing any network, application, device, and user access. User identity (credentials, group information, IP address) and device information, when collected through various sources helps secure your network resources.
Security Operations Centre (SOC) and Network Operations Centre (NOC) teams can use identity parameters to configure security policies. Security policies provide the right level of access to the authenticated users.
Identity helps your organization to mitigate major security threats by securing access to your resources (network components, applications) based on username, roles, and groups.
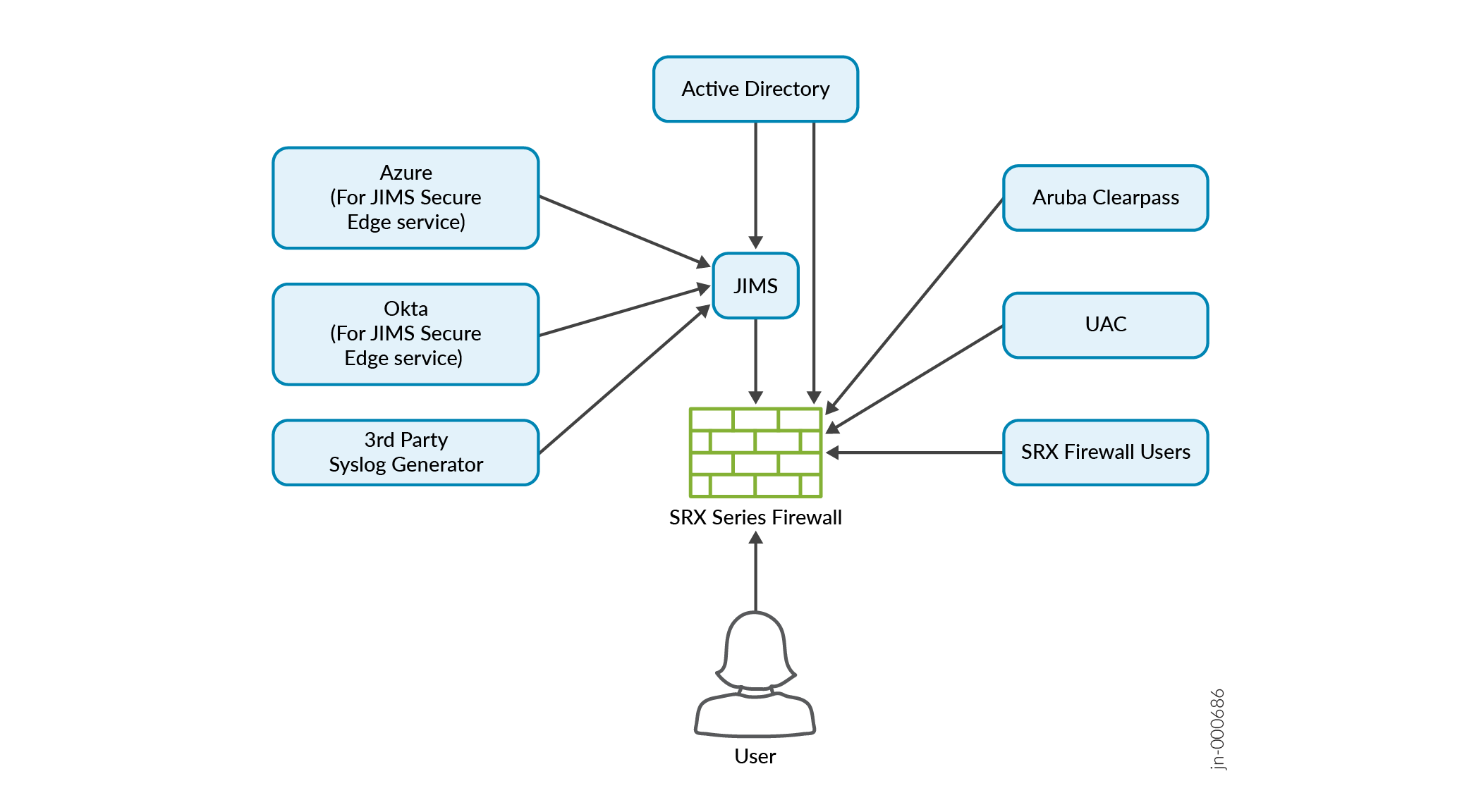
Benefits of Identity-Aware Firewall
An identity-aware firewall:
-
Adds an additional layer of security to your network.
-
Helps identify the source (user or device) of the traffic in the network.
-
Provides visibility on users and devices that generate alerts, alarms, and cause security incidents.
-
Optimizes user experience by providing users with a streamlined and smooth access to the appropriate resources without compromising on network and application security.
Deploy Identity Source at Firewall Level
How is Identity Source deployed at Firewall level?
A firewall obtain user information from various identity sources such as Active Directory, Juniper® Identity Management Service (JIMS), Aruba ClearPass, and Unified Access Control (UAC). After obtaining user information, the network administrator can deploy the device to receive data from the identity sources.
In this guide, we use firewall to refer to a Juniper Networks® SRX Series Firewall or a Juniper Networks® vSRX Virtual Firewall (vSRX3.0), or a Juniper Networks® cSRX Container Firewall or a Juniper Networks® NFX Series Network Services Platform (NFX Series) devices.
Firewalls can create, manage, and redefine firewall rules that are based on user identity rather than an IP address. The firewalls can query JIMS, obtain the correct user identity information, and then enforce the appropriate security policy decisions to permit or deny access to protected corporate resources and the Internet.
Each component involved in the identity source process has its own security infrastructure where the authorization policies governing access to protected resources are administratively defined. The following tables describe the roles of these components and how the components communicate with each other.
|
Deployment Mode |
Identity Source |
Deployment Mode Details |
|---|---|---|
|
Active Directory as Identity Source |
Active Directory |
Simple configuration and any identity manager outside of firewalls is not required. |
|
Juniper® Identity Management Service (JIMS) as Identity Manager |
Active Directory |
Higher scalability and deployment flexibility. |
| Microsoft Azure | Firewalls can support user identities that are configured in Azure. | |
| Okta | Firewalls can support user identities that are configured in Okta using JIMS. | |
| Third-party Syslog generator | JIMS can gather syslog information that is generated through various third-party sources for obtaining user information. | |
|
Aruba ClearPass as Identity Source |
Aruba ClearPass |
Firewall can obtain user information from Aruba ClearPass. |
|
Unified Access Control as Identity Source |
UAC |
Firewalls can obtain user information that is configured on the UAC. |
|
SRX Firewall Users |
Firewall users |
The user information can be configured on a firewall authentication and can be maintained on a local server, or on an external server such as LDAP or RADIUS server. |
Role of Identity Source and Identity Manager
| Identity Source |
An identity source can manage user or device information, roles, and maintain user events. |
| Identity Manager |
JIMS is an advanced user identity management system. JIMS connects and communicates to various identity sources that are shown in Figure 1 on behalf of the Firewall. |
|
Deployment Mode |
Description |
Benefits of Deployment |
|---|---|---|
| Active Directory as Identity Source |
Active Directory as an Identity Source gathers user and group information for authentication by reading domain controller event logs, probing domain PCs, and querying Lightweight Directory Access Protocol (LDAP) services within the configured Windows domain. |
Centralized management: Centralizes user and group management within an organization, which simplifies administration. Effective authentication: Verifies user and computer identities, enhancing network security. Policy enforcement: Allows administrators to enforce security policies using Group Policy Objects (GPOs). Dependencies: Relies on Active Directory infrastructure. Some organizations might not prefer this infrastructure. |
|
Juniper® Identity Management Service (JIMS) |
Juniper® Identity Management Service (JIMS) is a standalone Windows service application that collects and maintains a large database of user, device, and group information from Identity Source domains or syslog sources. For more information, see JIMS with SRX Series Firewall. |
Efficient management: Simplifies end-user experience by automating the correlation between usernames, devices, and IP addresses. Load reduction: Reduces load on the identity management system by acting as middleware between identity management and firewalls. Access control: Allows policy control that is based on group memberships, enhancing security, and access restrictions. Dependencies: Relies on a standalone Windows service, potentially adding a point of failure or dependency on the Windows environment. |
|
Aruba ClearPass as Identity Source |
A firewall and Aruba ClearPass collaborate to protect your network resources. These devices control user access to the Internet and enforce security at the user identity level that is based on the usernames or by the groups that the network resources belong to. |
Policy management: Facilitates policy management for onboarding new devices and controlling access based on roles and device types. Granular access control: Grants access levels based on user roles and enhances security and compliance. Dependencies: The identity source must be integrated with Aruba ClearPass, which might require additional configuration and setup. |
|
Unified Access Control (UAC) as Identity Source |
A Unified Access Control (UAC) uses IC Series UAC Appliances, intranet Enforcers, and Infranet Agents to protect your network by ensuring only valid users can access the resources. An IC Series appliance is a policy decision point in the network that uses authentication information and policy rules to determine whether or not to provide access to individual resources on the network. |
Simplified configuration: Simplifies configuration by creating user information, groups, and policy rules in a centralized location. Enforced Security: Ensures that only valid users can access network resources through IP-based policies. Dependencies: Requires the deployment of IC Series UAC Appliances, intranet Enforcers, and Infranet Agents. This might make the network more complex. |
Choose Identity-Aware Firewall Components
Customers typically choose identity-aware firewall components that are based on their specific organizational needs, existing infrastructure, and security requirements:
Source of Identity
You must connect the firewall with one of the identity sources or identity manager, described in Table 1.
Scaling
For the deployments with higher scaling requirements, Juniper Identity Management Service is recommended.
Before you choose the components of identity-aware firewall, evaluate the complexity of integration and maintenance requirements to ensure that they align with your organizational goals and security requirements.
Authentication Table
- What is Authentication Table?
- How Authentication Table is implemented?
- How Authentication Tables are managed?
- State Information for Identity Source Authentication Table Entries
- Timeout Setting
What is Authentication Table?
The authentication table contains the IP address, username, and group mapping information that serves as the authentication source.
How Authentication Table is implemented?
The user and group mapping information in the authentication table is obtained by user identity information. When JIMS is deployed, the authentication table is obtained by using IP query or batch-query.
The obtained information in the table is generated on the Routing Engine of the device, that push the authentication table to the Packet Forwarding Engine. Security policies use the information in the table to authenticate users and to provide access control for traffic through the firewall.
You must configure Active-Directory authentication table to enable Active Directory as Identity Source information retrieval in the Windows Active Directory environment. See Configure Active Directory as Identity Source on SRX Series Firewall.
The priority option specifies the sequence in which user information
tables are checked. Using the lowest setting for the
identity
source
specifies the highest priority, meaning that the Active Directory
authentication source is searched
first. For more
information, see Active Directory as Identity Source Authentication Table and ClearPass Authentication Table.
How Authentication Tables are managed?
Windows domain environments are constantly changing as users log in and log out of the network and as network administrators modify user group information. The identity source manages changes in the Windows domain and updates periodically. The authentication table is also updated to reflect the up-to-date relevant group information for all listed users.
Additionally, a probe function is provided to address changes that occur between reading event logs, or to address the case where event log information is lost. An on-demand probe is triggered when client traffic arrives at the firewall but a source IP address for that client cannot be found in the table. And at any point, manual probing is available to probe a specific IP address.
See Domain PC Probing.
State Information for Identity Source Authentication Table Entries
Identity source authentication table entries can be in one of four states:
| Initial |
Specifies that IP address-to-user mapping information was obtained by reading domain controller event logs and an entry was added to the authentication table. Entries in this state are changed to valid when the table is pushed from the Routing Engine to the Packet Forwarding Engine. |
| Valid |
Specifies that a valid entry was obtained by reading domain controller event logs or that a valid response was received from a domain PC probe and the user is a valid domain user. |
| Invalid |
Specifies that an invalid response was received from a domain PC probe and the user is an invalid domain user. |
| Pending |
Specifies that a probe event generated an entry in the authentication table, but no probe response has been received from the domain PC. If a probe response is not received within 90 seconds, the entry is deleted from the table. |
Timeout Setting
When a user is no longer active, a timer is started for that user’s entry in the authentication table. When time is up, the user’s entry is removed from the table. Entries in the table remain active as long as there are sessions associated with the entry.
We recommend that you disable timeouts when disabling on-demand probing in order to prevent someone from accessing the Internet without logging in again.
For more information, see Active Directory as Identity Source Timeout Setting and ClearPass Timeout Setting.
