ON THIS PAGE
Example: Configuring VXLAN to VPLS Stitching with OVSDB
Virtual Extensible LAN (VXLAN) can be utilized with the Open vSwitch Database (OVSDB) management protocol in a VPLS-enabled network to stitch a virtualized data center into a Layer 2 VPN network. This configuration allows for seamless interconnection between different data centers using Layer 2 VPN regardless of whether it is virtualized, physical, or both.
Requirements
This example uses the following hardware and software components:
Two MX Series routers running Junos OS 14.1R2 or later
Two MX Series routers running Junos OS 14.1R2 or later with an OVSDB software package. The release of this package must be the same as the Junos OS release running on the device.
One EX9200 switch
One VMware NSX controller
NSX Manager
Before you start the configuration, you must perform the following tasks:
In NSX Manager or the NSX API, configure a logical switch for each VXLAN that OVSDB will manage. This example implements two OVSDB-managed VXLANs, so you must configure two logical switches. After the configuration of each logical switch, NSX automatically generates a universally unique identifier (UUID) for the logical switch. If you have not done so already, retrieve the UUID for each logical switch. A sample UUID is 28805c1d-0122-495d-85df-19abd647d772. When configuring the equivalent VXLANs on the Juniper Networks device, you must use the UUID of the logical switch as the bridge domain name.
For more information about logical switches and VXLANs, see Understanding How to Manually Configure OVSDB-Managed VXLANs.
Create an SSL private key and certificate, and install them in the
/var/db/certsdirectory of the Juniper Networks device. For more information, see Creating and Installing an SSL Key and Certificate on a Juniper Networks Device for Connection with SDN Controllers.
Overview
In this example, four MX Series routers are configured to function together for VXLAN to virtual private LAN service (VPLS) stitching. Each router performs a different role in the configuration. The following diagram shows the topology of these MX Series routers. MX1 is the core router that handles Layer 3 traffic and protocols. MX2 is the VXLAN gateway router that functions as a virtual tunnel endpoint (VTEP) and handles switching for Layer 2, VPLS, and VXLAN. The MX3 router is configured to handle VPLS traffic. The MX4 router is configured as a VTEP to accept and decapsulate VXLAN packets.
Topology
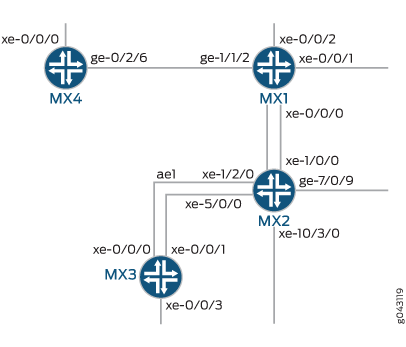
Configuration
To configure VXLAN to VPLS stitching with OVSDB:
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your configuration, copy and
paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
MX1
set interfaces lo0 unit 0 family inet address 10.255.181.13/32 primary set interfaces ge-1/1/2 unit 0 family inet address 10.30.30.2/30 set interfaces xe-0/0/0 unit 0 family inet address 10.20.20.2/30 set protocols ospf area 0.0.0.0 interface all
MX2
set interfaces lo0 unit 0 family inet address 10.255.181.72/32 primary set lag-options interfaces <ae*> mtu 9192 set lag-options interfaces <ae*> aggregated ether-options minimum-links 1 set chassis aggregated-devices ethernet device-count 40 set chassis fpc 1 pic 0 tunnel-services bandwidth 10g set chassis network-services enhanced-ip set interfaces xe-1/2/0 gigether-options 802.3ad ae1 set interfaces xe-0/0/0 unit 0 family inet address 10.20.20.1/30 set interfaces ge-7/0/9 vlan tagging set interfaces ge-7/0/9 unit 1 vlan-id 3 set interfaces ge-7/0/9 unit 1 family vpls set interfaces xe-10/3/0 vlan tagging set interfaces xe-10/3/0 unit 1 vlan-id 3 set interfaces xe-10/3/0 unit 0 family vpls set interfaces ae1 unit 0 family inet address 10.1.1.1/30 set interfaces ae1 unit 0 family mpls set routing-options autonomous-system 100 set protocols rsvp interface all set protocols mpls no cspf set protocols mpls label-switched-path-to-mx3 to 10.255.181.98 set protocols mpls interface all set protocols bgp family l2vpn signaling set protocols bgp group ibgp type internal set protocols bgp group ibgp neighbor 10.255.181.98 local-address 10.255.181.72 set protocols ospf area 0.0.0.0 interface xe-0/0/0.0 set protocols ospf area 0.0.0.0 interface fxp0.0 disable set protocols ospf area 0.0.0.0 interface lo0.0 passive set protocols ospf area 0.0.0.0 interface ae1.0 set protocols ovsdb traceoptions file ovsdb.log size 100m files 10 set protocols ovsdb traceoptions file ovsdb.level all set protocols ovsdb traceoptions file ovsdb.flag all set protocols ovsdb interfaces xe-10/3/0.1 set protocols ovsdb interfaces ge-7/0/9.1 set protocols ovsdb controller 192.168.182.45 protocol ssl port 6632 set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 vtep-source-interface lo0.0 set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 instance-type vpls set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 vlan-id 3 set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 interface ge-7/0/9.1 set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 interface xe-10/3/0.1 set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 routing-interface irb.3 set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 vxlan ovsdb-managed set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 vxlan vni 3 set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 route-distinguisher 10.255.181.72:3 set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 vrf-target target:3:3 set routing-instances 24a76aff-7e61-4520-a78d-3eca26ad7510 protocols vpls site mx2 site-identifier 1
MX3
set interfaces lo0 unit 0 family inet address 127.0.0.1/32 set interfaces lo0 unit 0 family inet address 10.255.181.98/32 primary set lag-options interfaces <ae*> mtu 9192 set lag-options interfaces <ae*> aggregated-ether-options minimum-links 1 set lag-options interfaces <ae*> aggregated-ether-options lacp active set interfaces xe-0/0/0 gigether-options 802.3ad ae1 set interfaces xe-0/0/1 gigether-options 802.3ad ae1 set interfaces xe-0/0/3 vlan tagging set interfaces xe-0/0/3 unit 1 vlan-id 3 set interfaces xe-0/0/3 unit 1 family vpls set interfaces ae1 unit 0 family inet address 10.1.1.2/30 set interfaces ae1 unit 0 family mpls set routing-options autonomous-system 100 set protocols rsvp interface all set protocols mpls no-cspf set protocols mpls label-switched-path-to-mx2 to 10.255.181.72 set protocols mpls interface all set protocols bgp family l2vpn signaling set protocols bgp group ibgp type internal set protocols bgp group ibgp neighbor 10.255.181.72 local-address 10.255.181.98 set protocols ospf area 0.0.0.0 interface lo0.0 passive set protocols ospf area 0.0.0.0 interface ae1.0 set routing-instances vpls3 instance-type vpls set routing-instances vpls3 vlan-id 3 set routing-instances vpls3 interface xe-0/0/3.1 set routing-instances vpls3 route-distinguisher 10.255.181.98:3 set routing-instances vpls3 vrf-target target:3:3 set routing-instances vpls3 protocols vpls no-tunnel-services set routing-instances vpls3 protocols vpls site mx3 site-identifier 2
MX4
set interfaces lo0 unit 0 family inet address 10.255.181.43/32 primary set interfaces xe-0/0/0 vlan-tagging set interfaces xe-0/0/0 encapsulation flexible-ethernet-services set interfaces xe-0/0/0 unit 0 family bridge interface-mode trunk set interfaces xe-0/0/0 unit 0 family bridge vlan-id-list 1-10 set interfaces ge-0/2/6 unit 0 family inet address 10.30.30.1/30 set protocols ospf area 0.0.0.0 interface ge-0/2/6.0 set protocols ospf area 0.0.0.0 interface fxp0.0 disable set protocols ospf area 0.0.0.0 interface lo0.0 passive set protocols ovsdb traceoptions file ovsdb.log size 100m files 10 set protocols ovsdb traceoptions level all set protocols ovsdb traceoptions flag all set protocols ovsdb interfaces xe-0/0/0.0 set protocols ovsdb controller 192.168.182.45 protocol ssl port 6632 set routing-instances default-vs1 vtep-source-interface lo0.0 set routing-instances default-vs1 instance-type virtual-switch set routing-instances default-vs1 interface xe-0/0/0.1 set bridge-domains 24a76aff-7e61-4520-a78d-3eca26ad7510 vlan-id 3 set bridge-domains 24a76aff-7e61-4520-a78d-3eca26ad7510 vxlan ovsdb-managed set bridge-domains 24a76aff-7e61-4520-a78d-3eca26ad7510 vxlan vni 3 set bridge-domains 24a76aff-7e61-4520-a78d-3eca26ad7510 vxlan ingress-node-replication set switch-options vtep-source-interface lo0.0
Configuring MX1
Step-by-Step Procedure
The first router to be configured is the core router. This MX Series router handles Layer 3 traffic and protocols for the rest of the network.
To configure the MX1 router:
Specify the IPv4 address for the loopback interface.
[edit interfaces] user@MX1# set lo0 unit 0 family inet address 10.255.181.13/32 primary
Configure the Layer 3 network.
[edit interfaces] user@MX1# set ge-1/1/2 unit 0 family inet address 10.30.30.2/30 user@MX1# set xe-0/0/0 unit 0 family inet address 10.20.20.2/30
Enable OSPF on all interfaces.
[edit protocols] user@MX1# set ospf area 0.0.0.0 interface all
Configuring MX2
Step-by-Step Procedure
The second router to be configured is the VXLAN gateway router. This MX Series router is configured as a VTEP, and it handles switching for Layer 2, VPLS, and VXLAN.
To configure the MX2 router:
Configure interfaces for the VXLAN gateway.
[edit interfaces] user@MX2# set lo0 unit 0 family inet address 10.255.181.72/32 primary user@MX2# set xe-1/2/0 gigether-options 802.3ad ae1 user@MX2# set xe-0/0/0 unit 0 family inet address 10.20.20.1/30 user@MX2# set ge-7/0/9 vlan tagging user@MX2# set ge-7/0/9 unit 1 vlan-id 3 user@MX2# set ge-7/0/9 unit 1 family vpls user@MX2# set xe-10/3/0 vlan tagging user@MX2# set xe-10/3/0 unit 1 vlan-id 3 user@MX2# set xe-10/3/0 unit 0 family vpls user@MX2# set ae1 unit 0 family inet address 10.1.1.1/30 user@MX2# set ae1 unit 0 family mpls
Set up LAG options
[edit lag-options] user@MX2# set interfaces <ae*> mtu 9192 user@MX2# set interfaces <ae*> aggregated ether-options minimum-links 1
Configure chassis settings.
[edit chassis] user@MX2# set aggregated-devices ethernet device-count 40 user@MX2# set fpc 1 pic 0 tunnel-services bandwidth 10g user@MX2# set network-services enhanced-ip
Configure routing options.
[edit routing-options] user@MX2# set autonomous-system 100
Set up RSVP, MPLS, and BGP protocols.
[edit protocols] user@MX2# set rsvp interface all user@MX2# set mpls no cspf user@MX2# set mpls label-switched-path-to-mx3 to 10.255.181.98 user@MX2# set mpls interface all user@MX2# set bgp family l2vpn signaling user@MX2# set bgp group ibgp type internal user@MX2# set bgp group ibgp neighbor 10.255.181.98 local-address 10.255.181.72
Configure OSPF interface settings.
[edit protocols] user@MX2# set ospf area 0.0.0.0 interface xe-0/0/0.0 user@MX2# set ospf area 0.0.0.0 interface fxp0.0 disable user@MX2# set ospf area 0.0.0.0 interface lo0.0 passive user@MX2# set ospf area 0.0.0.0 interface ae1.0
Set up OVSDB tracing operations.
[edit protocols] user@MX2# set ovsdb traceoptions file ovsdb.log size 100m files 10 user@MX2# set ovsdb traceoptions file ovsdb.level all user@MX2# set ovsdb traceoptions file ovsdb.flag all
Specify that interfaces xe-10/3/0.1 and ge-7/0/9.1 are managed by OVSDB.
[edit protocols] user@MX2# set ovsdb interfaces xe-10/3/0.1 user@MX2# set ovsdb interfaces ge-7/0/9.1
Configure a connection with an NSX controller.
[edit protocols] user@MX2# set ovsdb controller 192.168.182.45 protocol ssl port 6632
Create a VPLS routing instance with VXLAN functionality.
[edit routing-instances] user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 vtep-source-interface lo0.0 user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 instance-type vpls user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 vlan-id 3 user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 interface ge-7/0/9.1 user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 interface xe-10/3/0.1 user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 routing-interface irb.3 user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 vxlan ovsdb-managed user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 vxlan vni 3 user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 route-distinguisher 10.255.181.72:3 user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 vrf-target target:3:3 user@MX2# set 24a76aff-7e61-4520-a78d-3eca26ad7510 protocols vpls site mx2 site-identifier 1
Note:After completing this configuration, you must configure a gateway, which is the NSX equivalent of a hardware VTEP. This configuration implements one hardware VTEP, so you must configure one gateway, a gateway service, and a logical switch port using NSX Manager or the NSX API. For more information about the tasks you must perform as well as key NSX Manager configuration details, see VMware NSX Configuration for Juniper Networks Devices Functioning as Virtual Tunnel Endpoints.
Configuring MX3
Step-by-Step Procedure
The third MX Series router must be configured to handle VPLS traffic.
To configure the MX3 router:
Specify the IPv4, IPv6, and ISO addresses for the loopback interface.
[edit interfaces] user@MX3# set lo0 unit 0 family inet address 127.0.0.1/32 user@MX3# set lo0 unit 0 family inet address 10.255.181.98/32 primary
Configure the network interfaces.
[edit interfaces] user@MX3# set xe-0/0/0 gigether-options 802.3ad ae1 user@MX3# set xe-0/0/1 gigether-options 802.3ad ae1 user@MX3# set xe-0/0/3 vlan tagging user@MX3# set xe-0/0/3 unit 1 vlan-id 3 user@MX3# set xe-0/0/3 unit 1 family vpls user@MX3# set ae1 unit 0 family inet address 10.1.1.2/30 user@MX3# set ae1 unit 0 family mpls
Set up LAG options
[edit lag-options] user@MX3# set interfaces <ae*> mtu 9192 user@MX3# set interfaces <ae*> aggregated-ether-options minimum-links 1 user@MX3# set interfaces <ae*> aggregated-ether-options lacp active
Configure routing options.
[edit routing-options] user@MX3# set autonomous-system 100
Set up RSVP, MPLS, and BGP protocols.
[edit protocols] user@MX3# set rsvp interface all user@MX3# set mpls no cspf user@MX3# set mpls label-switched-path-to-mx2 to 10.255.181.72 user@MX3# set mpls interface all user@MX3# set bgp family l2vpn signaling user@MX3# set bgp group ibgp type internal user@MX3# set bgp group ibgp neighbor 10.255.181.72 local-address 10.255.181.98
Configure OSPF interface settings.
[edit protocols] user@MX3# set ospf area 0.0.0.0 interface lo0.0 passive user@MX3# set ospf area 0.0.0.0 interface ae1.0
Create a VPLS routing instance.
[edit routing-instances] set vpls3 instance-type vpls set vpls3 vlan-id 3 set vpls3 interface xe-0/0/3.1 set vpls3 route-distinguisher 10.255.181.98:3 set vpls3 vrf-target target:3:3 set vpls3 protocols vpls no-tunnel-services set vpls3 protocols vpls site mx3 site-identifier 2
Configuring MX4
Step-by-Step Procedure
The fourth MX Series router is configured as a VTEP to accept and decapsulate VXLAN packets.
To configure the MX4 router:
Specify the IPv4, IPv6, and ISO addresses for the loopback interface.
[edit interfaces] user@MX4# set lo0 unit 0 family inet address 10.255.181.43/32 primary
Configure the interfaces.
[edit interfaces] user@MX4# set xe-0/0/0 vlan-tagging user@MX4# set xe-0/0/0 encapsulation flexible-ethernet-services user@MX4# set xe-0/0/0 unit 0 family bridge interface-mode trunk user@MX4# set xe-0/0/0 unit 0 family bridge vlan-id-list 1-10 user@MX4# set ge-0/2/6 unit 0 family inet address 10.30.30.1/30
Configure OSPF interface settings.
[edit protocols] user@MX4# set ospf area 0.0.0.0 interface ge-0/2/6.0 user@MX4# set ospf area 0.0.0.0 interface fxp0.0 disable user@MX4# set ospf area 0.0.0.0 interface lo0.0 passive
Set up OVSDB tracing operations.
[edit protocols] user@MX4# set ovsdb traceoptions file ovsdb.log size 100m files 10 user@MX4# set ovsdb traceoptions level all user@MX4# set ovsdb traceoptions flag all
Specify that the xe-0/0/0.0 interface is managed by OVSDB.
[edit protocols] user@MX4# set ovsdb interfaces xe-0/0/0.0
Configure a connection with an NSX controller.
[edit protocols] user@MX4# set ovsdb controller 192.168.182.45 protocol ssl port 6632
Configure the VPLS interface.
[edit routing-instances] user@MX4# set default-vs1 vtep-source-interface lo0.0 user@MX4# set default-vs1 instance-type virtual-switch user@MX4# set default-vs1 interface xe-0/0/0.1
Configure a set of VXLAN-enabled bridge domains.
[edit bridge-domains] user@MX4# set 24a76aff-7e61-4520-a78d-3eca26ad7510 vlan-id 3 user@MX4# set 24a76aff-7e61-4520-a78d-3eca26ad7510 vxlan ovsdb-managed user@MX4# set 24a76aff-7e61-4520-a78d-3eca26ad7510 vxlan vni 3 user@MX4# set 24a76aff-7e61-4520-a78d-3eca26ad7510 vxlan ingress-node-replication
Configure the loopback interface to be used as the tunnel source address.
[edit switch-options] user@MX4# set vtep-source-interface lo0.0
Note:After completing this configuration, you must configure a gateway, which is the NSX equivalent of a hardware VTEP. This configuration implements one hardware VTEP, so you must configure one gateway, a gateway service, and a logical switch port using NSX Manager or the NSX API. For more information about the tasks you must perform as well as key NSX Manager configuration details, see “VMware NSX Configuration for Juniper Networks Devices Functioning as Virtual Tunnel Endpoints”.
Results
From configuration mode, confirm your configuration by entering the following commands on each router. If the output does not display the intended configuration, repeat the instructions in this example to correct the configuration.
Verification
Confirm that the configuration is working properly.
Verifying MX1
Purpose
Verify your configuration on MX1.
Action
Verify that the interfaces are configured properly.
user@MX1# show interface
lo0 {
unit 0 {
family inet {
address 10.255.181.13/32 {
primary;
}
}
}
}
ge-1/1/2 {
unit 0 {
family inet {
address 10.30.30.2/30;
}
}
}
xe-0/0/0 {
unit 0 {
family inet {
address 10.20.20.2/30;
}
}
}
Verify that OSPF is configured correctly.
user@MX1# show protocols
ospf {
area 0.0.0.0 {
interface all;
}
}
Verifying MX2
Purpose
Verify your configuration on MX2.
Action
Verify that the interfaces are configured properly.
user@MX2# show interfaces
lo0 {
unit 0 {
family inet {
address 10.255.181.72/32 {
primary;
}
}
}
}
xe-1/2/0 {
gigether-options {
802.3ad ae1;
}
}
xe-0/0/0 {
unit 0 {
family inet {
address 10.20.20.1/30;
}
}
}
ge-7/0/9 {
vlan-tagging;
unit 0 {
family vpls;
}
unit 1 {
vlan-id 3;
}
}
xe-10/3/0 {
vlan-tagging;
unit 0 {
family vpls;
}
unit 1 {
vlan-id 3;
}
}
ae1 {
unit 0 {
family inet {
address 10.1.1.1/30;
}
family mpls;
}
}
Verify that OSPF is configured properly.
user@MX2# show protocols ospf
ospf {
area 0.0.0.0 {
interface xe-0/0/0.0;
interface fxp0.0 {
disable;
}
interface lo0.0 {
passive;
}
interface ae1.0;
}
}
Verify that OVSDB is configured properly.
user@MX2# show protocols ovsdb
ovsdb {
traceoptions {
file ovsdb.log size 100m files 10;
level all;
flag all;
}
interfaces {
xe-10/3/0.1;
ge-7/0/9.0;
ge-7/0/9.1;
}
controller 192.168.182.45 {
protocol {
ssl port 6632;
}
}
}
Verify the default-VS1 routing instance configuration.
user@MX2# show routing-instances
routing-instances {
24a76aff-7e61-4520-a78d-3eca26ad7510 {
vtep-source-interface lo0.0;
instance-type vpls;
vlan-id 3;
interface ge-7/0/9.1;
interface xe-10/3/0.1;
routing-interface irb.3;
vxlan {
ovsdb-managed;
vni 3;
encapsulate-inner-vlan;
decapsulate-accept-inner-vlan;
ingress-node-replication;
}
route-distinguisher 10.255.181.72:3;
vrf-target target:3:3;
protocols {
vpls {
traceoptions {
file vpls.log;
flag all;
}
site MX2 {
site-identifier 1;
}
}
}
}
cadbc185-f60f-48a6-93fd-dc14a6420c60 {
vtep-source-interface lo0.0;
instance-type vpls;
vlan-id 2;
interface ge-7/0/9.0;
interface xe-10/3/0.0;
routing-interface irb.2;
vxlan {
ovsdb-managed;
vni 2;
encapsulate-inner-vlan;
decapsulate-accept-inner-vlan;
ingress-node-replication;
}
route-distinguisher 10.255.181.72:10;
vrf-target target:10:10;
protocols {
vpls {
traceoptions {
file vpls.log;
flag all;
}
site MX2 {
site-identifier 1;
}
}
}
}
vpls11 {
vtep-source-interface lo0.1;
instance-type vpls;
vlan-id 11;
interface ge-7/0/9.11;
interface xe-10/3/0.11;
routing-interface irb.11;
vxlan {
ovsdb-managed;
vni 11;
ingress-node-replication;
}
route-distinguisher 10.255.181.72:11;
vrf-target target:11:11;
protocols {
vpls {
traceoptions {
file vpls.log;
flag all;
}
site MX2 {
site-identifier 1;
}
}
}
}
vpls12 {
vtep-source-interface lo0.1;
instance-type vpls;
vlan-id 12;
interface ge-7/0/9.12;
interface xe-10/3/0.12;
routing-interface irb.12;
vxlan {
ovsdb-managed;
vni 12;
ingress-node-replication;
}
route-distinguisher 10.255.181.72:12;
vrf-target target:12:12;
protocols {
vpls {
traceoptions {
file vpls.log;
flag all;
}
site mx2 {
site-identifier 1;
}
}
}
}
vpls13 {
vtep-source-interface lo0.1;
instance-type vpls;
vlan-id 13;
interface ge-7/0/9.13;
interface xe-10/3/0.13;
routing-interface irb.13;
vxlan {
vni 13;
multicast-group 233.252.0.13;
}
route-distinguisher 10.255.181.72:13;
vrf-target target:13:13;
protocols {
vpls {
traceoptions {
file vpls.log;
flag all;
}
site mx2 {
site-identifier 1;
}
}
}
}
vpls14 {
vtep-source-interface lo0.1;
instance-type vpls;
vlan-id 14;
interface ge-7/0/9.14;
interface xe-10/3/0.14;
routing-interface irb.14;
vxlan {
vni 14;
multicast-group 233.252.0.14;
}
route-distinguisher 10.255.181.72:14;
vrf-target target:14:14;
protocols {
vpls {
traceoptions {
file vpls.log;
flag all;
}
site mx2 {
site-identifier 1;
}
}
}
}
vpls15 {
vtep-source-interface lo0.1;
instance-type vpls;
vlan-id 15;
interface ge-7/0/9.15;
interface xe-10/3/0.15;
routing-interface irb.15;
vxlan {
vni 15;
multicast-group 233.252.0.15;
}
route-distinguisher 10.255.181.72:15;
vrf-target target:15:15;
protocols {
vpls {
traceoptions {
file vpls.log;
flag all;
}
site mx2 {
site-identifier 1;
}
}
}
}
vpls4 {
vtep-source-interface lo0.0;
instance-type vpls;
vlan-id 4;
interface ge-7/0/9.4;
interface xe-10/3/0.4;
routing-interface irb.4;
vxlan {
vni 4;
multicast-group 233.252.0.4;
}
route-distinguisher 10.255.181.72:4;
vrf-target target:4:4;
protocols {
vpls {
traceoptions {
file vpls.log;
flag all;
}
site mx2 {
site-identifier 1;
}
}
}
}
vpls5 {
vtep-source-interface lo0.0;
instance-type vpls;
vlan-id 5;
interface ge-7/0/9.5;
interface xe-10/3/0.5;
routing-interface irb.5;
vxlan {
vni 5;
multicast-group 233.252.0.5;
}
route-distinguisher 10.255.181.72:5;
vrf-target target:5:5;
protocols {
vpls {
traceoptions {
file vpls.log;
flag all;
}
site mx2 {
site-identifier 1;
}
}
}
}
vrf1 {
instance-type vrf;
interface ae2.0;
interface lo0.1;
route-distinguisher 100:100;
vrf-target target:100:100;
protocols {
ospf {
area 0.0.0.0 {
interface ae2.0;
interface lo0.1 {
passive;
}
}
}
pim {
rp {
static {
address 10.255.181.13;
}
}
interface all;
}
}
}
}
Verify the vrf1 routing instance configuration.
user@MX2# show routing-instances
24a76aff-7e61-4520-a78d-3eca26ad7510 {
vtep-source-interface lo0.0;
instance-type vpls;
vlan-id 3;
interface ge-7/0/9.1;
interface xe-10/3/0.1;
routing-interface irb.3;
vxlan {
ovsdb-managed;
vni 3;
}
route-distinguisher 10.255.181.72:3;
vrf-target target:3:3;
protocols {
vpls {
site mx2 {
site-identifier 1;
}
}
}
}
Verifying MX3
Purpose
Verify your configuration on MX3.
Action
Verify that the interfaces are configured properly.
user@MX3# show interfaces
xe-0/0/0 {
gigether-options {
802.3ad ae1;
}
}
xe-0/0/1 {
gigether-options {
802.3ad ae1;
}
}
xe-0/0/3 {
vlan-tagging;
unit 1 {
vlan-id 3;
family vpls;
}
}
ae1 {
unit 0 {
family inet {
address 10.1.1.2/30;
}
family mpls;
}
}
Verify the RSVP, MPLS, BGP and OSPF protocols are configured properly.
user@MX3# show protocols
protocols {
rsvp {
interface all;
}
mpls {
no-cspf;
label-switched-path to-mx2 {
to 10.255.181.72;
}
interface all;
}
bgp {
family l2vpn {
signaling;
}
group ibgp {
type internal;
neighbor 10.255.181.72 {
local-address 10.255.181.98;
}
}
}
ospf {
area 0.0.0.0 {
interface lo0.0 {
passive;
}
interface ae1.0;
}
}
}
Verify the VPLS routing instance configuration.
user@MX3# show routing-instances
routing-instances {
vpls3 {
instance-type vpls;
vlan-id 3;
interface xe-0/0/3.1;
route-distinguisher 10.255.181.98:3;
vrf-target target:3:3;
protocols {
vpls {
no-tunnel-services;
site mx3 {
site-identifier 2;
}
}
}
}
}
Verifying MX4
Purpose
Verify your configuration on MX4.
Action
Verify that the global group interfaces are configured properly.
user@MX4# show groups global interfaces
Verify that the interfaces are configured properly.
user@MX4# show interfaces
lo0 {
unit 0 {
family inet {
address 10.255.181.43/32 {
primary;
}
}
}
}
xe-0/0/0 {
vlan-tagging;
encapsulation flexible-ethernet-services;
unit 0 {
family bridge {
interface-mode trunk;
vlan-id-list 1-10;
}
}
}
ge-0/2/6 {
unit 0 {
family inet {
address 30.30.30.1/30;
}
}
}
Verify that the OSPF interface settings are configured properly.
user@MX4# show protocols ospf
area 0.0.0.0 {
interface ge-0/2/6.0;
interface fxp0.0 {
disable;
}
interface lo0.0 {
passive;
}
}
Verify that OVSDB is configured properly.
user@MX4# show protocols ovsdb
traceoptions {
file ovsdb.log size 100m files 10;
level all;
flag all;
}
interfaces {
xe-0/0/0.0;
}
controller 192.168.182.45 {
protocol {
ssl port 6632;
}
}Verify the default-VS1 routing instance configuration
and bridge domains.
user@MX4# show routing-instances default-VS1
vtep-source-interface lo0.0;
instance-type virtual-switch;
interface xe-0/0/0.1;
Verify that the bridge domains are configured properly.
user@MX4# show bridge-domains
24a76aff-7e61-4520-a78d-3eca26ad7510 {
vlan-id 3;
vxlan {
ovsdb-managed;
vni 3;
ingress-node-replication;
}
}
Verify that the loopback interface is used as the tunnel source address.
user@MX4# show switch-options
vtep-source-interface lo0.0;