Multifield Classifier Example: Configuring Multifield Classification
Multifield Classification Overview
- Forwarding Classes and PLP Levels
- Multifield Classification and BA Classification
- Multifield Classification Used In Conjunction with Policers
Forwarding Classes and PLP Levels
You can configure the Junos OS class of service (CoS) features to classify incoming traffic by associating each packet with a forwarding class, a packet loss priority (PLP) level, or both:
Based on the associated forwarding class, each packet is assigned to an output queue, and the router services the output queues according to the associated scheduling you configure.
Based on the associated PLP, each packet carries a lower or higher likelihood of being dropped if congestion occurs. The CoS random early detection (RED) process uses the drop probability configuration, output queue fullness percentage, and packet PLP to drop packet as needed to control congestion at the output stage.
Multifield Classification and BA Classification
The Junos OS supports two general types of packet classification: behavior aggregate (BA) classification and multifield classification:
-
BA classification, or CoS value traffic classification, refers to a method of packet classification that uses a CoS configuration to set the forwarding class or PLP of a packet based on the CoS value in the IP packet header. The CoS value examined for BA classification purposes can be the Differentiated Services code point (DSCP) value, DSCP IPv6 value, IP precedence value, MPLS EXP bits, and IEEE 802.1p value. The default classifier is based on the IP precedence value.
-
Multifield classification refers to a method of packet classification that uses a standard stateless firewall filter configuration to set the forwarding class or PLP for each packet entering or exiting the interface based on multiple fields in the IP packet header, including the DSCP value (for IPv4 only), the IP precedence value, the MPLS EXP bits, and the IEEE 802.1p bits. Multifield classification commonly matches on IP address fields, the IP protocol type field, or the port number in the UDP or TCP pseudoheader field. Multifield classification is used instead of BA classification when you need to classify packets based on information in the packet information other than the CoS values only.
With multifield classification, a firewall filter term can specify the packet classification actions for matching packets though the use of the
forwarding-class class-nameorloss-priority (high | medium-high | medium-low | low)nonterminating actions in the term’sthenclause.
BA classification of a packet can be overridden by the stateless firewall filter
actions forwarding-class and
loss-priority.
Misclassification of traffic via Multifield classifier on QFX5k:
-
If BUM traffic is forced to take unicast queue via MF classifier, packets will be classified to MCQ9. Junos releases 21.4R3 , 22.1R3 and from Junos release version 22.2 these packets will be classified to MCQ8.
-
If unicast traffic is forced to take multicast queue via MF classifier, packets will be classified to MCQ9 and from release 19.1R3 it will be classified to best-effort queue.
Multifield Classification Used In Conjunction with Policers
To configure multifield classification in conjunction with rate limiting, a firewall filter term can specify the packet classification actions for matching packets through the use of a policer nonterminating action that references a single-rate two-color policer.
When multifield classification is configured to perform classification through a policer, the filter-matched packets in the traffic flow are rate-limited to the policer-specified traffic limits. Packets in a conforming flow of filter-matched packets are implicitly set to a low PLP. Packets in a nonconforming traffic flow can be discarded, or the packets can be set to a specified forwarding class, set to a specified PLP level, or both, depending on the type of policer and how the policer is configured to handle nonconforming traffic.
Before you apply a firewall filter that performs multifield classification and also a policer to the same logical interface and for the same traffic direction, make sure that you consider the order of policer and firewall filter operations.
As an example, consider the following scenario:
You configure a firewall filter that performs multifield classification (acts on matched packets by setting the forwarding class, the PLP, or both) based on the packet's existing forwarding class or PLP. You apply the firewall filter at the input of a logical interface.
You also configure a single-rate two-color policer that acts on a red traffic flow by re-marking (setting the forwarding class, the PLP, or both) rather than discarding those packets. You apply the policer as an interface policer at the input of the same logical interface to which you apply the firewall filter.
Because of the order of policer and firewall operations, the input policer is executed before the input firewall filter. This means that the multifield classification specified by the firewall filter is performed on input packets that have already been re-marked once by policing actions. Consequently, any input packet that matches the conditions specified in a firewall filter term is then subject to a second re-marking according to the forwarding-class or loss-priority nonterminating actions also specified in that term.
See Also
Multifield Classification Requirements and Restrictions
Supported Platforms
The loss-priority firewall filter action is supported on the following routing platforms only:
EX Series switches
M7i and M10i routers with the Enhanced CFEB (CFEB-E)
M120 and M320 routers
MX Series routers
T Series routers with Enhanced II Flexible PIC Concentrators (FPCs)
PTX Series routers
CoS Tricolor Marking Requirement
The loss-priority firewall filter action has platform-specific requirements dependencies on the CoS tricolor marking feature, as defined in RFC 2698:
On an M320 router, you cannot commit a configuration that includes the
loss-priorityfirewall filter action unless you enable the CoS tricolor marking feature.On all routing platforms that support the
loss-priorityfirewall filter action, you cannot set theloss-priorityfirewall filter action tomedium-lowormedium-highunless you enable the CoS tricolor marking feature. .
To enable the CoS tricolor marking feature, include the tri-color statement at the [edit class-of-service] hierarchy level.
Restrictions
You cannot configure the loss-priority and three-color-policer nonterminating actions for the same firewall filter term. These two nonterminating actions are mutually exclusive.
On a PTX Series router, you must configure the policer action in a separate rule and not combine it with the rule configuring the forwarding-class, and loss-priority actions. See Firewall and Policing Differences Between PTX Series Packet Transport Routers and T Series Matrix Routers.
See Also
Multifield Classification Limitations on M Series Routers
- Problem: Output-Filter Matching on Input-Filter Classification
- Workaround: Configure All Actions in the Ingress Filter
Problem: Output-Filter Matching on Input-Filter Classification
On M Series routers (except M120 routers), you cannot classify packets with an output filter match based on the ingress classification that is set with an input filter applied to the same IPv4 logical interface.
For example, in the following configuration, the filter called ingress assigns all incoming IPv4 packets to the expedited-forwarding class. The filter called egress counts all packets that were assigned to the expedited-forwarding class in the ingress filter. This configuration does not work on most M Series routers. It works on all other routing platforms, including M120 routers, MX Series routers, and T Series routers.
[edit]
user@host # show firewall
family inet {
filter ingress {
term 1 {
then {
forwarding-class expedited-forwarding;
accept;
}
}
term 2 {
then accept;
}
}
filter egress {
term 1 {
from {
forwarding-class expedited-forwarding;
}
then count ef;
}
term 2 {
then accept;
}
}
}
[edit]
user@host# show interfaces
ge-1/2/0 {
unit 0 {
family inet {
filter {
input ingress;
output egress;
}
}
}
}
Workaround: Configure All Actions in the Ingress Filter
As a workaround, you can configure all of the actions in the ingress filter.
user@host # show firewall
family inet {
filter ingress {
term 1 {
then {
forwarding-class expedited-forwarding;
accept;
count ef;
}
}
term 2 {
then accept;
}
}
}
[edit]
user@host# show interfaces
ge-1/2/0 {
unit 0 {
family inet {
filter {
input ingress;
}
}
}
}
See Also
Example: Configuring Multifield Classification
This example shows how to configure multifield classification of IPv4 traffic by using firewall filter actions and two firewall filter policers.
Requirements
Before you begin, make sure that your environment supports the features shown in this example:
The
loss-priorityfirewall filter action must be supported on the router and configurable to all four values.To be able to set a
loss-priorityfirewall filter action, configure this example on logical interfacege-1/2/0.0on one of the following routing platforms:MX Series router
M120 or M320 router
M7i or M10i router with the Enhanced CFEB (CFEB-E)
T Series router with Enhanced II Flexible PIC Concentrator (FPC)
To be able to set a
loss-priorityfirewall filter action tomedium-lowormedium-high, make sure that the CoS tricolor marking feature is enabled. To enable the CoS tricolor marking feature, include thetri-colorstatement at the[edit class-of-service]hierarchy level.
The
expedited-forwardingandassured-forwardingforwarding classes must be scheduled on the underlying physical interfacege-1/2/0.Make sure that the following forwarding classes are assigned to output queues:
expedited-forwardingassured-forwarding
Forwarding-class assignments are configured at the
[edit class-of-service forwarding-classes queue queue-number]hierarchy level.Note:You cannot commit a configuration that assigns the same forwarding class to two different queues.
Make sure that the output queues to which the forwarding classes are assigned are associated with schedulers. A scheduler defines the amount of interface bandwidth assigned to the queue, the size of the memory buffer allocated for storing packets, the priority of the queue, and the random early detection (RED) drop profiles associated with the queue.
You configure output queue schedulers at the
[edit class-of-service schedulers]hierarchy level.You associate output queue schedulers with forwarding classes by means of a scheduler map that you configure at the
[edit class-of-service scheduler-maps map-name]hierarchy level.
Make sure that output-queue scheduling is applied to the physical interface
ge-1/2/0.You apply a scheduler map to a physical interface at the
[edit class-of-service interfaces ge-1/2/0 scheduler-map map-name]hierarchy level.
Overview
In this example, you apply multifield classification to the
input IPv4 traffic at a logical interface by using stateless firewall
filter actions and two firewall filter policers that are referenced
from the firewall filter. Based on the source address field, packets
are either set to the low loss priority or else policed.
Neither of the policers discards nonconforming traffic. Packets in
nonconforming flows are marked for a specific forwarding class (expedited-forwarding or assured-forwarding), set
to a specific loss priority, and then transmitted.
Single-rate two-color policers always transmit packets
in a conforming traffic flow after implicitly setting a low loss priority.
Topology
In this example, you apply multifield classification to the
IPv4 traffic on logical interface ge-1/2/0.0. The classification
rules are specified in the IPv4 stateless firewall filter mfc-filter and two single-rate two-color policers, ef-policer and af-policer.
The IPv4 standard stateless firewall filter mfc-filter defines three filter terms:
isp1-customers—The first filter term matches packets with the source address 10.1.1.0/24 or 10.1.2.0/24. Matched packets are assigned to theexpedited-forwardingforwarding class and set to thelowloss priority.isp2-customers—The second filter term matches packets with the source address 10.1.3.0/24 or 10.1.4.0/24. Matched packets are passed toef-policer, a policer that rate-limits traffic to a bandwidth limit of 300 Kbps with a burst-size limit of 50 KB. This policer specifies that packets in a nonconforming flow are marked for theexpedited-forwardingforwarding class and set to thehighloss priority.other-customers—The third and final filter term passes all other packets toaf-policer, a policer that rate-limits traffic to a bandwidth limit of 300 Kbps and a burst-size limit of 50 KB (the same traffic limits as defined byef-policer). This policer specifies that packets in a nonconforming flow are marked for theassured-forwardingforwarding class and set to themedium-highloss priority.
Configuration
The following example requires you to navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Use the CLI Editor in Configuration Mode.
To configure this example, perform the following tasks:
- CLI Quick Configuration
- Configuring Policers to Rate-Limit Expedited-Forwarding and Assured-Forwarding Traffic
- Configuring a Multifield Classification Filter That Also Applies Policing
- Applying Multifield Classification Filtering and Policing to the Logical Interface
CLI Quick Configuration
To quickly configure this example, copy the following
configuration commands into a text file, remove any line breaks, and
then paste the commands into the CLI at the [edit] hierarchy
level.
set firewall policer ef-policer if-exceeding bandwidth-limit 300k set firewall policer ef-policer if-exceeding burst-size-limit 50k set firewall policer ef-policer then loss-priority high set firewall policer ef-policer then forwarding-class expedited-forwarding set firewall policer af-policer if-exceeding bandwidth-limit 300k set firewall policer af-policer if-exceeding burst-size-limit 50k set firewall policer af-policer then loss-priority high set firewall policer af-policer then forwarding-class assured-forwarding set firewall family inet filter mfc-filter term isp1-customers from source-address 10.1.1.0/24 set firewall family inet filter mfc-filter term isp1-customers from source-address 10.1.2.0/24 set firewall family inet filter mfc-filter term isp1-customers then loss-priority low set firewall family inet filter mfc-filter term isp1-customers then forwarding-class expedited-forwarding set firewall family inet filter mfc-filter term isp2-customers from source-address 10.1.3.0/24 set firewall family inet filter mfc-filter term isp2-customers from source-address 10.1.4.0/24 set firewall family inet filter mfc-filter term isp2-customers then policer ef-policer set firewall family inet filter mfc-filter term other-customers then policer af-policer set interfaces ge-1/2/0 unit 0 family inet address 192.168.1.1/24 set interfaces ge-1/2/0 unit 0 family inet filter input mfc-filter
Configuring Policers to Rate-Limit Expedited-Forwarding and Assured-Forwarding Traffic
Step-by-Step Procedure
To configure policers to rate-limit expedited-forwarding and assured-forwarding traffic:
Define traffic limits for expedited-forwarding traffic.
[edit] user@host# edit firewall policer ef-policer [edit firewall policer ef-policer] user@host# set if-exceeding bandwidth-limit 300k user@host# set if-exceeding burst-size-limit 50k user@host# set then loss-priority high user@host# set then forwarding-class expedited-forwarding
Configure a policer for assured-forwarding traffic.
[edit firewall policer ef-policer] user@host# up [edit firewall] user@host# edit policer af-policer [edit firewall policer af-policer] user@host# set if-exceeding bandwidth-limit 300k user@host# set if-exceeding burst-size-limit 50k user@host# set then loss-priority high user@host# set then forwarding-class assured-forwarding
Results
Confirm the configuration of the policer by entering
the show firewall configuration mode command. If the command
output does not display the intended configuration, repeat the instructions
in this procedure to correct the configuration.
[edit]
user@host# show firewall
policer af-policer {
if-exceeding {
bandwidth-limit 300k;
burst-size-limit 50k;
}
then {
loss-priority high;
forwarding-class assured-forwarding;
}
}
policer ef-policer {
if-exceeding {
bandwidth-limit 300k;
burst-size-limit 50k;
}
then {
loss-priority high;
forwarding-class expedited-forwarding;
}
}
Configuring a Multifield Classification Filter That Also Applies Policing
Step-by-Step Procedure
To configure a multifield classification filter that additionally applies policing:
Enable configuration of a firewall filter term for IPv4 traffic.
[edit] user@host# edit firewall family inet filter mfc-filter
Configure the first term to match on source addresses and then classify the matched packets.
[edit firewall family inet filter mfc-filter] user@host# set term isp1-customers from source-address 10.1.1.0/24 user@host# set term isp1-customers from source-address 10.1.2.0/24 user@host# set term isp1-customers then loss-priority low user@host# set term isp1-customers then forwarding-class expedited-forwarding
Configure the second term to match on different source addresses and then police the matched packets.
[edit firewall family inet filter mfc-filter] user@host# set term isp2-customers from source-address 10.1.3.0/24 user@host# set term isp2-customers from source-address 10.1.4.0/24 user@host# set term isp2-customers then policer ef-policer
Configure the third term to police all other packets to a different set of traffic limits and actions.
[edit firewall family inet filter mfc-filter] user@host# set term other-customers then policer af-policer
Results
Confirm the configuration of the filter by entering the show firewall configuration mode command. If the command output
does not display the intended configuration, repeat the instructions
in this procedure to correct the configuration.
[edit]
user@host# show firewall
family inet {
filter mfc-filter {
term isp1-customers {
from {
source-address 10.1.1.0/24;
source-address 10.1.2.0/24;
}
then {
loss-priority low;
forwarding-class expedited-forwarding;
}
}
term isp2-customers {
from {
source-address 10.1.3.0/24;
source-address 10.1.4.0/24;
}
then {
policer ef-policer;
}
}
term other-customers {
then {
policer af-policer;
}
}
}
}
policer af-policer {
if-exceeding {
bandwidth-limit 300k;
burst-size-limit 50k;
}
then discard;
}
policer ef-policer {
if-exceeding {
bandwidth-limit 200k;
burst-size-limit 50k;
}
then {
loss-priority high;
forwarding-class expedited-forwarding;
}
}
Applying Multifield Classification Filtering and Policing to the Logical Interface
Step-by-Step Procedure
To apply multifield classification filtering and policing to the logical interface:
Enable configuration of IPv4 on the logical interface.
[edit] user@host# edit interfaces ge-1/2/0 unit 0 family inet
Configure an IP address for the logical interface.
[edit interfaces ge-1/2/0 unit 0 family inet ] user@host# set address 192.168.1.1/24
Apply the firewall filter to the logical interface input.
[edit interfaces ge-1/2/0 unit 0 family inet ] user@host# set filter input mfc-filter
Note:Because the policer is executed before the filter, if an input policer is also configured on the logical interface, it cannot use the forwarding class and PLP of a multifield classifier associated with the interface.
Results
Confirm the configuration of the interface by entering
the show interfaces configuration mode command. If the
command output does not display the intended configuration, repeat
the instructions in this procedure to correct the configuration.
[edit]
user@host# show interfaces
ge-1/2/0 {
unit 0 {
family inet {
filter {
input mfc-filter;
}
address 192.168.1.1/24;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
Displaying the Number of Packets Processed by the Policer at the Logical Interface
Purpose
Verify the traffic flow through the logical interface and that the policer is evaluated when packets are received on the logical interface.
Action
Use the show firewall operational mode command
for the filter you applied to the logical interface.
user@host> show firewall filter rate-limit-in Filter: rate-limit-in Policers: Name Packets ef-policer-isp2-customers 32863 af-policer-other-customers 3870
The command output lists the policers applied by the firewall
filter rate-limit-in, and the number of packets that matched
the filter term.
The packet count includes the number of out-of-specification (out-of-spec) packet counts, not all packets policed by the policer.
The policer name is displayed concatenated with the name of the firewall filter term in which the policer is referenced as an action.
Example: Configure and Apply a Firewall Filter for a Multifield Classifier
This example shows how to configure a firewall filter to classify traffic using a multifield classifier. The classifier detects packets of interest to CoS as the packets arrive on an interface. Use multifield classifiers when a simple BA classifier is insufficient to classify a packet, when peering routers do not have CoS bits marked, or when the peering router’s marking is untrusted.
Requirements
To verify this procedure, this example uses a traffic generator. The traffic generator can be hardware-based, or it can be software running on a server or host machine.
The functionality in this procedure is widely supported on devices that run Junos. The example shown here was tested and verified on MX Series routers running Junos OS Release 10.4.
Overview
A classifier is a software operation that inspects a packet as it enters the router or switch. The packet header contents are examined, and this examination determines how the packet is treated when the network becomes too busy to handle all of the packets and you want your devices to drop packets intelligently, instead of dropping packets indiscriminately. One common way to detect packets of interest is by source port number. The TCP port numbers 80 and 12345 are used in this example, but many other matching criteria for packet detection are available to multifield classifiers, using firewall filter match conditions. The configuration in this example specifies that TCP packets with source port 80 are classified into the BE-data forwarding class and queue number 0. TCP packets with source port 12345 are classified into the Premium-data forwarding class and queue number 1.
You typically use multifield classifiers at the network edge as packets enter an autonomous system (AS).
In this example, you configure the firewall filter mf-classifier and specify some custom forwarding classes on Device R1. In specifying the custom forwarding classes, you also associate each class with a queue.
The classifier operation is shown in Figure 1.
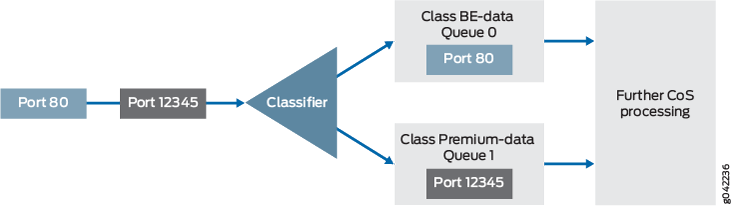
You apply the multifield classifier’s firewall filter as an input filter on each customer-facing or host-facing interface that needs the filter. The incoming interface is ge-1/0/1 on Device R1. The classification and queue assignment is verified on the outgoing interface. The outgoing interface is Device R1’s ge-1/0/9 interface.
Topology
Figure 2 shows the sample network.
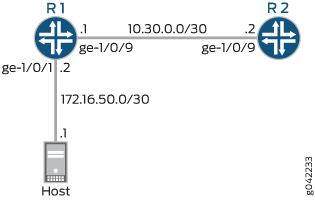
CLI Quick Configuration shows the configuration for all of the Juniper Networks devices in Figure 2.
Step-by-Step Procedure describes the steps on Device R1.
Classifiers are described in more detail in the following Juniper Networks Learning Byte video.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them into a text file, remove any line breaks, change any details necessary to match your network configuration, copy and paste the commands into the CLI at the [edit] hierarchy level, and then enter commit from the configuration mode.
Device R1
set interfaces ge-1/0/1 description to-host set interfaces ge-1/0/1 unit 0 family inet filter input mf-classifier set interfaces ge-1/0/1 unit 0 family inet address 172.16.50.2/30 set interfaces ge-1/0/9 description to-R2 set interfaces ge-1/0/9 unit 0 family inet address 10.30.0.1/30 set class-of-service forwarding-classes class BE-data queue-num 0 set class-of-service forwarding-classes class Premium-data queue-num 1 set class-of-service forwarding-classes class Voice queue-num 2 set class-of-service forwarding-classes class NC queue-num 3 set firewall family inet filter mf-classifier term BE-data from protocol tcp set firewall family inet filter mf-classifier term BE-data from port 80 set firewall family inet filter mf-classifier term BE-data then forwarding-class BE-data set firewall family inet filter mf-classifier term Premium-data from protocol tcp set firewall family inet filter mf-classifier term Premium-data from port 12345 set firewall family inet filter mf-classifier term Premium-data then forwarding-class Premium-data set firewall family inet filter mf-classifier term accept-all-else then accept
Device R2
set interfaces ge-1/0/9 description to-R1 set interfaces ge-1/0/9 unit 0 family inet address 10.30.0.2/30
Step-by-Step Procedure
The following example requires that you navigate various levels in the configuration hierarchy. For information about navigating the CLI, see Using the CLI Editor in Configuration Mode in the Junos OS CLI User Guide.
To configure Device R1:
-
Configure the device interfaces.
[edit interfaces] user@R1# set ge-1/0/1 description to-host user@R1# set ge-1/0/1 unit 0 family inet address 172.16.50.2/30 user@R1# set ge-1/0/9 description to-R2 user@R1# set ge-1/0/9 unit 0 family inet address 10.30.0.1/30
-
Configure the custom forwarding classes and associated queue numbers.
[edit class-of-service forwarding-classes] user@R1# set BE-data queue-num 0 user@R1# set Premium-data queue-num 1 user@R1# set Voice queue-num 2 user@R1# set NC queue-num 3
-
Configure the firewall filter term that places TCP traffic with a source port of 80 (HTTP traffic) into the BE-data forwarding class, associated with queue 0.
[edit firewall family inet filter mf-classifier] user@R1# set term BE-data from protocol tcp user@R1# set term BE-data from port 80 user@R1# set term BE-data then forwarding-class BE-data
-
Configure the firewall filter term that places TCP traffic with a source port of 12345 into the Premium-data forwarding class, associated with queue 1.
[edit firewall family inet filter mf-classifier] user@R1# set term Premium-data from protocol tcp user@R1# set term Premium-data from port 12345 user@R1# set term Premium-data then forwarding-class Premium-data
-
At the end of your firewall filter, configure a default term that accepts all other traffic.
Otherwise, all traffic that arrives on the interface and is not explicitly accepted by the firewall filter is discarded.
[edit firewall family inet filter mf-classifier] user@R1# set term accept-all-else then accept
-
Apply the firewall filter to the ge-1/0/1 interface as an input filter.
[edit interfaces] user@R1# set ge-1/0/1 unit 0 family inet filter input mf-classifier
Results
From configuration mode, confirm your configuration by entering the show interfaces, show class-of-service, show firewall commands. If the output does not display the intended configuration, repeat the instructions in this example to correct the configuration.
user@R1# show interfaces
ge-1/0/1 {
description to-host;
unit 0 {
family inet {
filter {
input mf-classifier;
}
address 172.16.50.2/30;
}
}
}
ge-1/0/9 {
description to-R2;
unit 0 {
family inet {
address 10.30.0.1/30;
}
}
}
user@R1# show class-of-service
forwarding-classes {
class BE-data queue-num 0;
class Premium-data queue-num 1;
class Voice queue-num 2;
class NC queue-num 3;
}
user@R1# show firewall
family inet {
filter mf-classifier {
term BE-data {
from {
protocol tcp;
port 80;
}
then forwarding-class BE-data;
}
term Premium-data {
from {
protocol tcp;
port 12345;
}
then forwarding-class Premium-data;
}
term accept-all-else {
then accept;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
Checking the CoS Settings
Purpose
Confirm that the forwarding classes are configured correctly.
Action
From Device R1, run the show class-of-service forwardng-classes command.
user@R1> show class-of-service forwarding-class Forwarding class ID Queue Restricted queue Fabric priority Policing priority SPU priority BE-data 0 0 0 low normal low Premium-data 1 1 1 low normal low Voice 2 2 2 low normal low NC 3 3 3 low normal low
Meaning
The output shows the configured custom classifier settings.
Sending TCP Traffic into the Network and Monitoring the Queue Placement
Purpose
Make sure that the traffic of interest is sent out the expected queue.
Action
Clear the interface statistics on Device R1’s outgoing interface.
user@R1> clear interfaces statistics ge-1/0/9
Use a traffic generator to send 50 TCP port 80 packets to Device R2 or to some other downstream device.
On Device R1, check the queue counters.
Notice that you check the queue counters on the downstream output interface, not on the incoming interface.
user@R1> show interfaces extensive ge-1/0/9 | find "Queue counters" Queue counters: Queued packets Transmitted packets Dropped packets 0 50 50 0 1 0 57 0 2 0 0 0 3 0 0 0Use a traffic generator to send 50 TCP port 12345 packets to Device R2 or to some other downstream device.
[root@host]# hping 172.16.60.1 -c 50 -s 12345 -k
On Device R1, check the queue counters.
user@R1> show interfaces extensive ge-1/0/9 | find "Queue counters" Queue counters: Queued packets Transmitted packets Dropped packets 0 50 50 0 1 50 57 0 2 0 0 0 3 0 0 0
Meaning
The output shows that the packets are classified correctly. When port 80 is used in the TCP packets, queue 0 is incremented. When port 12345 is used, queue 1 is incremented.
