Understanding DHCP Snooping (ELS)
This topic includes information about enabling Dynamic Host Configuration Protocol (DHCP) snooping when using Junos OS for EX Series switches with support for the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs Junos OS software that does not support ELS, see Understanding DHCP Snooping (non-ELS). For ELS details, see Using the Enhanced Layer 2 Software CLI.
DHCP snooping enables the switching device, which can be either a switch or a router, to monitor DHCP messages received from untrusted devices connected to the switching device. When DHCP snooping is enabled on a VLAN, the system examines DHCP messages sent from untrusted hosts associated with the VLAN and extracts their IP addresses and lease information. This information is used to build and maintain the DHCP snooping database. Only hosts that can be verified using this database are allowed access to the network.
DHCP Snooping Basics
DHCP allocates IP addresses dynamically, leasing addresses to devices so that the addresses can be reused when they are no longer needed by the devices to which they were assigned. Hosts and end devices that require IP addresses obtained through DHCP must communicate with a DHCP server across the LAN.
DHCP snooping acts as a guardian of network security by keeping track of valid IP addresses assigned to downstream network devices by a trusted DHCP server (the server is connected to a trusted network port).
By default, all trunk ports on the switch are trusted and all access ports are untrusted for DHCP snooping.
Starting with Junos OS Release 18.4R1, DHCP snooping occurs on trusted ports for the following Juniper Series switches, EX2300, EX4600, and QFX5K. Prior to Junos OS Release 18.4R1, for these devices, this was true only for DHCPv6 snooping. In addition, DHCP snooping occurs on trusted ports for EX9200 Series switches, and Fusion Enterprises, that are running Junos OS Release 19.1R1 and later.
You can configure an access port as trusted, or a trunk port as untrusted, using the overrides configuration statement with either the trusted or untrusted option.
When DHCP snooping is enabled, the lease information from the server is used to create the DHCP snooping table, also known as the DHCP binding table. The table shows current IP-MAC address bindings, as well as lease time, type of binding, names of associated VLANs and interfaces.
Entries in the DHCP snooping table are updated in the following events:
-
When a network device releases an IP address (sends a DHCPRELEASE message). In this event, the associated mapping entry is deleted from the database.
-
When you move a network device from one VLAN to another. In this event, typically the device needs to acquire a new IP address. Therefore, its entry in the database, including the VLAN name, is updated.
-
When the lease time (timeout value) assigned by the DHCP server expires. In this event, the associated entry is deleted from the database.
-
When the network device renews its lease by sending a unicast DHCPREQUEST message and receiving a positive response from the DHCP server. In this event, the lease time is updated in the database.
-
If the network device cannot reach the DHCP server that originally granted the lease, it sends a broadcast DHCPREQUEST message and rebinds to the DHCP server that responds. In this event, the client receives a new IP address and the binding is updated in the DHCP snooping table.
-
Starting in Junos OS Release 14.1X53-D35, if a network device with a fixed IP allocation from the DHCP server is replaced by a new device with a different MAC address, the new IP-MAC address binding is stored until the server sends a DHCPACK message; then, the entry in the DHCP snooping table is updated with the new address binding.
By default, the IP-MAC bindings are lost when the switch is rebooted, and the DHCP clients (the
network devices, or hosts) must reacquire bindings. However,
you can configure the bindings to persist by setting the
dhcp-snooping-file statement to
store the database file either locally or remotely. When you
configure and enable 802.1x dynamic VLAN, the DHCP snooping
entries also get deleted. Due to this, it is recommended to
configure for a DHCP server to store lease information for
clients and provide them with a predictable IP address even
after you reboot the client (DHCP persistence).
You can configure the switch to snoop DHCP server responses only from specific VLANs. Doing this prevents spoofing of DHCP server messages.
Enabling DHCP Snooping
When you are using the DHCP snooping feature, it is important that you understand about enabling the DHCP snooping feature.
On Junos OS device, you cannot configure DHCP snooping feature as an independent feature. Whenever you configure DHCP security for a specific VLAN of the device, the DHCP snooping is automatically enabled on that VLAN to perform it’s task.
For example:
- When you enable DHCP security on a specific VLAN, DHCP snooping gets automatically enabled on that VLAN.
Junos OS enables DHCP snooping on a switch:
-
When you configure the following option for any port security features:
-
dhcp-securitystatement at the [edit vlans vlan-name forwarding-options] hierarchy level.
-
Prior to Junos OS Release 17.1, Junos OS enabled DHCP snooping automatically if you configure any of the following port security features within [edit vlans vlan-name forwarding-options] hierarchy:
- Dynamic ARP inspection (DAI
- IP source guard
- DHCP option 82
- Static IP
Starting in Junos OS Release 17.1R1, you can configure DHCP snooping or DHCPv6 snooping on a VLAN without enabling other port security features. Use the following configuration statement to enable DHCP snooping:
[set vlans vlan-name forwarding-options dhcp-security].
To disable DHCP snooping, you must delete the dhcp-security statement from the configuration. DHCP snooping is not disabled automatically when you disable other port security features.
DHCP Snooping Process
The DHCP snooping process consists of the following steps:
When DHCP snooping is enabled for a VLAN, all DHCP packets sent from network devices in that VLAN are subjected to DHCP snooping. The final IP-MAC binding occurs when the DHCP server sends a DHCPACK packet to the DHCP client.
-
The network device sends a DHCPDISCOVER packet to request an IP address.
-
The switch forwards the packet to the DHCP server.
-
The server sends a DHCPOFFER packet to offer an address. If the DHCPOFFER packet is from a trusted interface, the switch forwards the packet to the network device.
-
The network device sends a DHCPREQUEST packet to accept the IP address. The switch adds an IP-MAC placeholder binding to the DHCP snooping table. The entry is considered a placeholder until a DHCPACK packet is received from the server. Until then, the IP address could still be assigned to some other host.
-
The server sends a DHCPACK packet to assign the IP address or a DHCPNAK packet to deny the address request.
-
The switch updates the DHCP database according to the type of packet received:
-
If the switch receives a DHCPACK packet, it updates lease information for the IP-MAC address bindings in its database.
-
If the switch receives a DHCPNACK packet, it deletes the placeholder.
-
The DHCP database is updated only after the DHCPREQUEST packet is sent.
For general information about the messages that the DHCP client and DHCP server exchange during the assignment of an IP address for the client, see the Junos OS System Basics Configuration Guide .
DHCPv6 Snooping
Starting in Junos OS Release 14.1X53-D10, DHCP snooping is supported for IPv6 packets on EX 9200 Switches.DHCP snooping is also supported for IPv6 packets. The process for DHCPv6 snooping is similar to that for DHCP snooping, but uses different names for the messages exchanged between the client and server to assign IPv6 addresses. Table 1 shows DHCPv6 messages and their DHCPv4 equivalents.
|
Sent by |
DHCPv6 Messages |
DHCPv4 Equivalent Messages |
|---|---|---|
|
Client |
SOLICIT |
DHCPDISCOVER |
|
Server |
ADVERTISE |
DHCPOFFER |
|
Client |
REQUEST, RENEW, REBIND |
DHCPREQUEST |
|
Server |
REPLY |
DHCPACK/DHCPNAK |
|
Client |
RELEASE |
DHCPRELEASE |
|
Client |
INFORMATION-REQUEST |
DHCPINFORM |
|
Client |
DECLINE |
DHCPDECLINE |
|
Client |
CONFIRM |
none |
|
Server |
RECONFIGURE |
DHCPFORCERENEW |
|
Client |
RELAY-FORW, RELAY-REPLY |
none |
Rapid Commit for DHCPv6
The DHCPv6 Rapid Commit option can shorten the exchange of messages between the client and server. When supported by the server and set by the client, this option shortens the exchange from a four-way relay to a two-message handshake. For more information about enabling the Rapid Commit option, see Configuring DHCPv6 Rapid Commit (MX Series, EX Series).
When the Rapid Commit option is enabled, the exchange of messages is as follows:
-
The DHCPv6 client sends out a SOLICIT message that contains a request that rapid assignment of address, prefix, and other configuration parameters be preferred.
-
If the DHCPv6 server supports rapid assignment, it responds with a REPLY message, which contains the assigned IPv6 address and prefix and other configuration parameters.
DHCP Server Access
A switch’s access to the DHCP server can be configured in three ways:
- Switch, DHCP Clients, and the DHCP Server Are All on the Same VLAN
- Switch Acts as the DHCP Server
- Switch Acts as a Relay Agent
Switch, DHCP Clients, and the DHCP Server Are All on the Same VLAN
When the switch, DHCP clients, and DHCP server are all members of the same VLAN, the DHCP server can be connected to the switch in one of two ways:
To enable DHCP snooping on the VLAN, configure the
dhcp-security statement at the [edit vlans vlan-name forwarding-options] hierarchy.
-
(See Figure 1.) The server is directly connected to the same switch as the one connected to the DHCP clients (the hosts, or network devices, that are requesting IP addresses from the server). The VLAN is enabled for DHCP snooping to protect the untrusted access ports. The trunk port is configured by default as a trusted port.
-
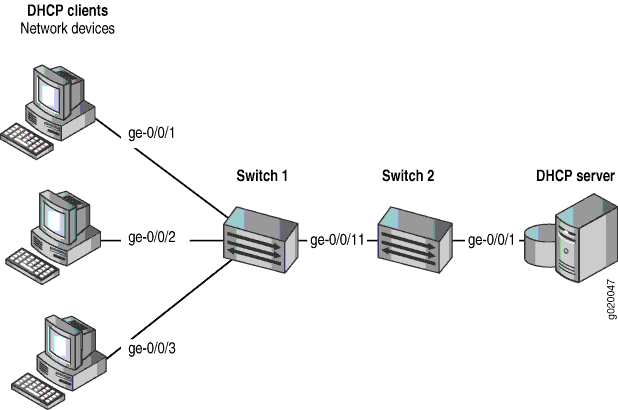
(See Figure 2.) The server is connected to an intermediary switch (Switch 2) that is connected through a trunk port to the switch (Switch 1) that the DHCP clients are connected to. Switch 2 is being used as a transit switch. The VLAN is enabled for DHCP snooping to protect the untrusted access ports of Switch 1. The trunk port is configured by default as a trusted port. In Figure 2, ge-0/0/11 is a trusted trunk port.

Switch Acts as the DHCP Server
You can configure DHCP local server options on the switch, which enables the switch to function as an extended DHCP local server. In Figure 3, the DHCP clients are connected to the extended DHCP local server through untrusted access ports.

Switch Acts as a Relay Agent
The switch functions as a relay agent when the DHCP clients or the DHCP server is connected to the switch through a Layer 3 interface (on a switch or a router). The Layer 3 interfaces on the switch are configured as routed VLAN interfaces (RVIs)—also called integrated routing and bridging (IRB) interfaces. The trunk interfaces are trusted by default.
The switch can act as a relay agent in these two scenarios:
-
The DHCP server and clients are in different VLANs.
-
The switch is connected to a router that is, in turn, connected to the DHCP server. See Figure 4.

Static IP Address Additions to the DHCP Snooping Database
You can add static (fixed) IP addresses and bind them to fixed MAC addresses in the DHCP snooping database. These bindings are labeled static in the database, while those bindings that have been added through the process of DHCP snooping are labeled dynamic. Static IPv6 address assignment is also available for DHCPv6. For configuration details, see Configuring Static DHCP IP Addresses for DHCP snooping.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
dhcp-security CLI statement at the [edit vlans vlan-name forwarding-options dhcp-security].