Example: Configuring IP Source Guard and Dynamic ARP Inspection on a Specified Bridge Domain to Protect the Devices Against Attacks
This example describes how to enable IP source guard and Dynamic ARP inspection (DAI) on a specified bridge domain to protect the device against spoofed IP/MAC addresses and ARP spoofing attacks. When you enable either IP source guard or DAI, the configuration automatically enables DHCP snooping for the same bridge domain.
Requirements
This example uses the following hardware and software components:
One MX Series router
Junos OS Release 14.1
A DHCP server to provide IP addresses to network devices on the device
Before you configure IP source guard to prevent IP/MAC spoofing or DAI to mitigate ARP spoofing attacks, be sure you have:
Connected the DHCP server to the device.
Configured the bridge domain to which you are adding DHCP security features. See Configuring the Bridge Domain for MX Series Router Cloud CPE Services.
Overview and Topology
Ethernet LAN devices are vulnerable to attacks on security that involve spoofing (forging) of source MAC addresses or source IP addresses. These spoofed packets are sent from hosts connected to untrusted access interfaces on the device. IP source guard checks the IP source address and MAC source address in a packet sent from a host attached to an untrusted access interface on the device against entries stored in the DHCP snooping database. If IP source guard determines that the packet header contains an invalid source IP address or source MAC address, it ensures that the device does not forward the packet—that is, the packet is discarded.
Another type of security attack is ARP spoofing (also known as ARP poisoning or ARP cache poisoning). ARP spoofing is a way to initiate man-in-the-middle attacks. The attacker sends an ARP packet that spoofs the MAC address of another device on the bridge domain. Instead of the device sending traffic to the proper network device, it sends it to the device with the spoofed address that is impersonating the proper device. If the impersonating device is the attacker's machine, the attacker receives all the traffic from the device that should have gone to another device. The result is that traffic from the device is misdirected and cannot reach its proper destination.
When DAI is enabled, the device logs the number of invalid ARP packets that it receives on each interface, along with the sender’s IP and MAC addresses. You can use these log messages to discover ARP spoofing on the network.
This example shows how to configure these important port security features on a device
that is connected to a DHCP server. The setup for this example includes the bridge domain employee-bdomain on the switching device. Figure 1 illustrates the topology
for this example.
The trunk interface connecting to the DHCP server interface is a trusted port by default.
Topology
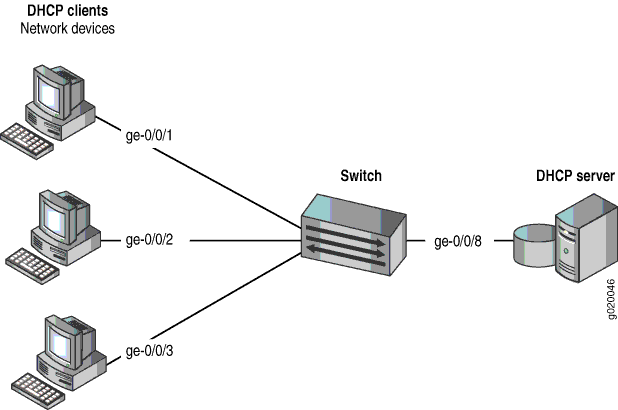
The components of the topology for this example are shown in Table 1.
| Properties | Settings |
|---|---|
Device hardware |
One MX Series router |
Bridge domain name and ID |
|
Bridge domain subnets |
|
Interfaces in |
|
Interface connecting to DHCP server |
|
In this example, the device has already been configured as follows:
All access ports are untrusted, which is the default setting.
The trunk port (ge-0/0/8) is trusted, which is the default setting.
The bridge-domain (
employee-bdomain) has been configured to include the specified interfaces.
Configuration
Procedure
CLI Quick Configuration
To quickly configure IP source guard and DAI (and thereby, also automatically configure DHCP snooping to protect the device against IP spoofing and ARP attacks), copy the following commands and paste them into the device terminal window:
[edit] set bridge-domains employee-bdomain forwarding-options dhcp-security ip-source-guard set bridge-domains employee-bdomain forwarding-options dhcp-security arp-inspection
Step-by-Step Procedure
To configure IP source guard and DAI (and thereby, also automatically configure DHCP snooping) on the bridge domain:
Configure IP source guard on the bridge domain:
[edit bridge-domains employee-bdomain forwarding-options dhcp-security] user@device# set ip-source-guard
Enable DAI on the bridge domain:
[edit bridge-domains employee-bdomain forwarding-options dhcp-security] user@device# set arp-inspection
Results
Check the results of the configuration:
user@device> show bridge-domains employee-bdomain forwarding-options
employee-bdomain {
forwarding-options {
dhcp-security {
arp-inspection;
ip-source-guard;
}
}
}
Verification
Confirm that the configuration is working properly.
- Verifying That DHCP Snooping Is Working Correctly on the Device
- Verifying That IP Source Guard Is Working on the Bridge Domain
- Verifying That DAI Is Working Correctly on the Device
Verifying That DHCP Snooping Is Working Correctly on the Device
Purpose
Verify that DHCP snooping is working on the device.
Action
Send some DHCP requests from network devices (here they are DHCP clients) connected to the device.
Display the DHCP snooping information when the port on which the DHCP server connects to the device is trusted. The following output results when requests are sent from the MAC addresses and the server has provided the IP addresses and leases:
user@device> show dhcp-security binding IP Address MAC Address Vlan Expires State Interface 192.0.2.17 00:05:85:3A:82:77 employee-vlan 86265 BOUND ge-0/0/1.0 192.0.2.18 00:05:85:3A:82:79 employee-vlan 86265 BOUND ge-0/0/1.0 192.0.2.19 00:05:85:3A:82:80 employee-vlan 86287 BOUND ge-0/0/2.0 192.0.2.20 00:05:85:3A:82:81 employee-vlan 86287 BOUND ge-0/0/2.0 192.0.2.21 00:05:85:3A:82:83 employee-vlan 86287 BOUND ge-0/0/2.0 192.0.2.22 00:05:85:27:32:88 employee-vlan 86254 BOUND ge-0/0/3.0
Meaning
When the interface on which the DHCP server connects to the device has been set to trusted, the output (see the preceding sample) shows, for the assigned IP address, the device’s MAC address, the VLAN name, and the time, in seconds, remaining before the lease expires.
Verifying That IP Source Guard Is Working on the Bridge Domain
Purpose
Verify that IP source guard is enabled and working on the bridge domain.
Action
Send some DHCP requests from network devices (here they are DHCP clients) connected to the device. View the IP source guard information for the data bridge domain.
user@device> show dhcp-security binding ip-source-guard IP Address MAC Address Vlan Expires State Interface 192.0.2.17 00:05:85:3A:82:77 employee-vlan 86265 BOUND ge-0/0/1.0 192.0.2.18 00:05:85:3A:82:79 employee-vlan 86265 BOUND ge-0/0/1.0 192.0.2.19 00:05:85:3A:82:80 employee-vlan 86287 BOUND ge-0/0/2.0 192.0.2.20 00:05:85:3A:82:81 employee-vlan 86287 BOUND ge-0/0/2.0 192.0.2.21 00:05:85:3A:82:83 employee-vlan 86287 BOUND ge-0/0/2.0 192.0.2.22 00:05:85:27:32:88 employee-vlan 86254 BOUND ge-0/0/3.0
Meaning
The IP source guard database table contains the VLANS and bridge domains enabled for IP source guard.
Verifying That DAI Is Working Correctly on the Device
Purpose
Verify that DAI is working on the device.
Action
Send some ARP requests from network devices connected to the device.
Display the DAI information:
user@device> show dhcp-security arp inspection statistics ARP inspection statistics: Interface Packets received ARP inspection pass ARP inspection failed ge-0/0/1.0 7 5 2 ge-0/0/2.0 10 10 0 ge-0/0/3.0 12 12 0
Meaning
The sample output shows the number of ARP packets received and inspected per interface, with a listing of how many packets passed and how many failed the inspection on each interface. The device compares the ARP requests and replies against the entries in the DHCP snooping database. If a MAC address or IP address in the ARP packet does not match a valid entry in the database, the packet is dropped.
