Solution Benefits
Juniper’s approach to a data center security solution starts with operational efficiency, which is the most critical part of any architectural transformation. Following are the various components of this architecture:
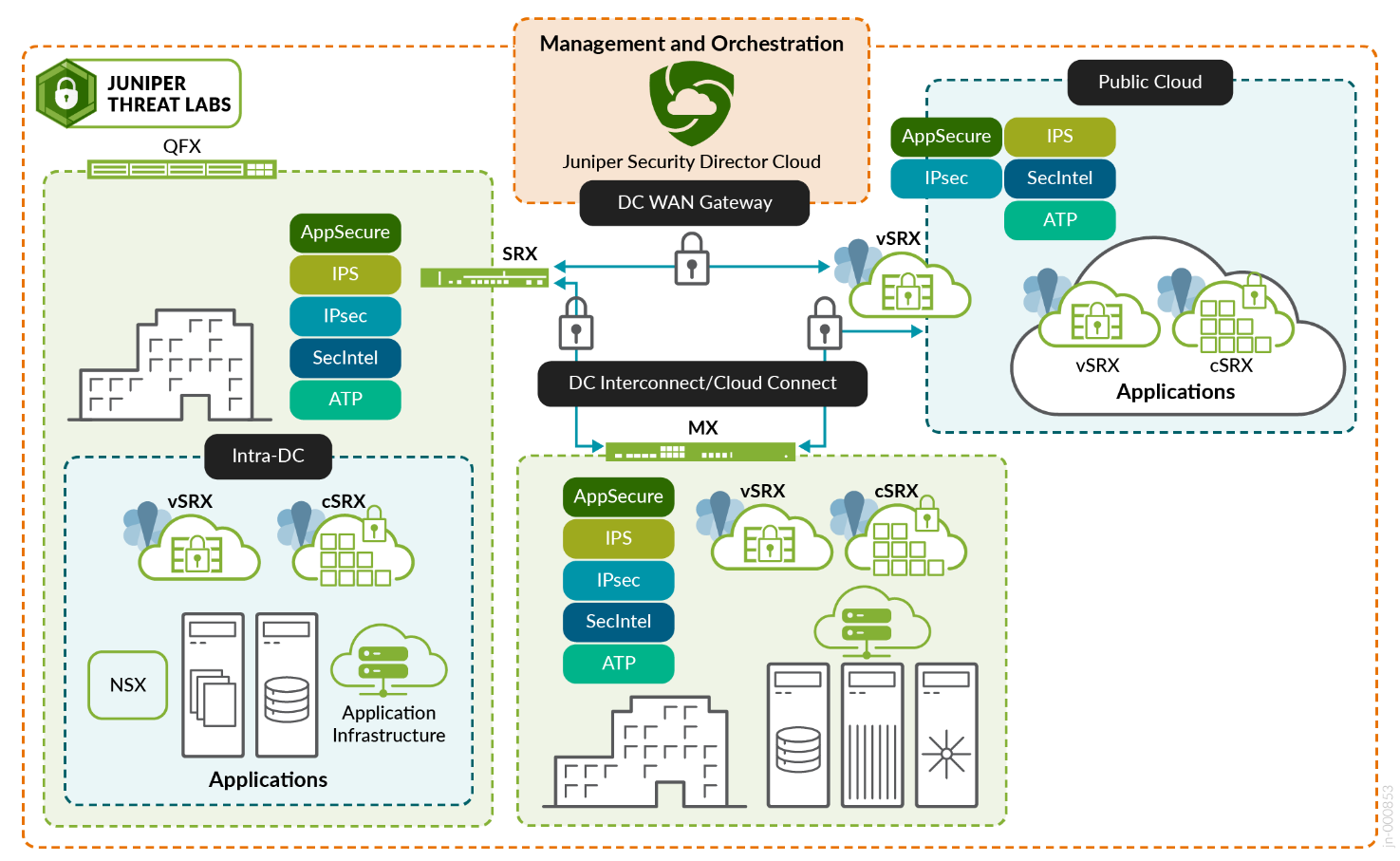
In the data center:
- Data center WAN gateway—This is the main entryway to your data center where you control who and what can access your corporate resources. Using the analogy of fine art in a museum, this is where the balance between availability and security must be struck. Additionally, this is where you control who can access the data in the data center. It is your first line of defence, and access policies at the data center WAN gateway must align with user policies at your edge.
- Cloud/Data Center Interconnect (DCI)—This is the connection between your data center locations where information is exchanged between applications. The most important point to remember here is that the data in transit between data center locations must be secured.
- Intra-data center—Inside your data center, there are physical servers that house your applications and their components. There is a micro perimeter that needs to protect these resources. In a zero trust data center, segmentation between servers limiting the impact of a successful attack is a must.
- Public Cloud—Public Cloud offers tons of scale, redundance, and global reach. Many public cloud environments offer their own native security controls, but within the context of zero trust, access to public cloud resources must align with application access policies in your other data center environments.
- Juniper Security Director Cloud (Management)—Whether edge security is delivered on-premises or from the cloud, one management experience and one policy framework make it very easy to create a policy once and apply it anywhere, providing unbroken visibility regardless of architecture.
Examples of data center traffic profiles with security implemented:
- At the data center edge gateway—ensuring consistent zero trust access to private and public cloud environments.
- Traffic flow between servers (East-West traffic).
- Traffic flow between clouds (DCI).
- Traffic flow at the application level to protect data (microsegmentation).
Features provided by Juniper Security Director Cloud with the same policy framework:
- Consistent threat protection.
- Easy extension of security policies to new environments and applications, reducing misconfigurations and lowering risk.
- Scaling data center security operations. Because visibility is unbroken in a unified console, security integration between multiple environments is not necessary, and automation is built in to identify and resolve threats quickly.
This JVD focuses on the next-generation firewall services that are typically used in the data center. This solution benefits you by providing an example of an optimized configuration for commonly utilized security services in the data center, and a validation that the deployed solutions are working as intended.
The following features are deployed and validated in this JVD:
- Application Security
- Intrusion detection and prevention (IDP)
- Advanced Threat Prevention (ATP)
- Security Intelligence (SecIntel)
- Advanced anti-malware (AAMW)
- DNS security
- Screens
- SSL Proxy (depends on use case implementation)
