Reference Architecture
This JVD covers a combination of network architectures where MX Series Routers and SRX Series Firewalls are connected in either single or double configurations (see Figure 1). It uses network redundancy mechanisms to provide flow resiliency between the MX Series Router Forwarding Layer and SRX Series Firewall Services Layer (MNHA, aka L3 cluster is explained later in the document). On configuring dual MX Series Router with ECMP, a Service Redundancy Daemon (SRD) is used to monitor the failure events that triggers a failover to the second MX Series Router. Note this is not needed with Traffic Load Balancer (TLB). Also, BFD protocol is used to capture a failover mechanism from the routing point of view when any other failure occurs. SRX’s MNHA allows to synchronize sessions (stateful sessions) between the two nodes so that the existing traffic and tunnels can continue uninterrupted.
Figure 1 shows the four main topologies covered in the JVD, combining single or dual MX Series Routers with standalone MNHA for SRX Series Firewalls, each on a particular load balancing mechanism (ECMP or TLB). It uses three SRX Series Firewalls for the first topology and doubles them to three pairs of firewalls for the other topologies.
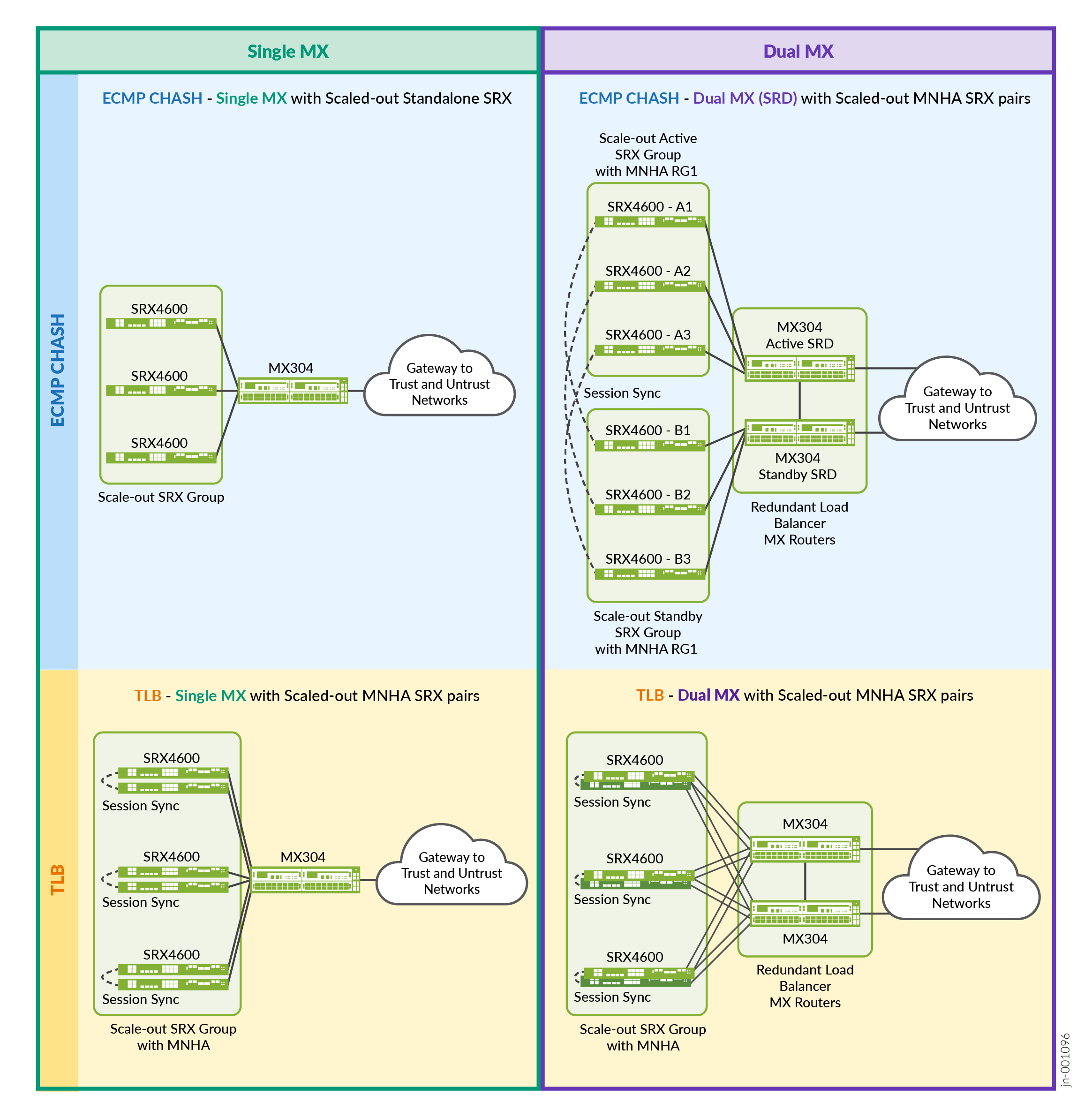
There are certain trade-offs with each of the architectural choices coming to complexity, high availability, feature parity and backward compatibility with earlier Junos OS releases. In general, complexity increases as more redundancy is added. For example, SRX MNHA pairs introduce some specificity in traffic switchover between MNHA node. There are certain dependencies for which load balancing method is used on the MX Series Routers (namely ECMP Consistent Hashing or TLB). This selection of topologies covers the most important considerations from simple to more redundancy scenarios.
- ECMP CHASH is simpler to use as it is only routing based, however, it is limited in failover capabilities.
- TLB is more focused on the services to load balance, offers more redundancy capabilities, and can be multiplied with different local groups. It is useful when there is a need to combine different use cases with the same architecture.
| Load-Balancing Method |
Junos OS for MX Series Router |
Number of MX Series Routers | Security Features |
SRX Standalone |
SRXs MNHA Cluster |
|---|---|---|---|---|---|
| ECMP with Consistent Hashing | 23.4R2 | Single MX | SFW / SNAT | Yes | No |
| Dual MX (SRD) | SFW / SNAT | No | Yes | ||
| Traffic Load Balancer (TLB) with Health Checkin | 23.4R2 | Single MX | SFW / SNAT | Yes | Yes |
| Dual MX | SFW / SNAT | Yes | Yes |
The Scale-Out solution only uses standard mechanisms and protocols between the components and does not require any special proprietary protocols. The exception is how load balancing is implemented internally (how the MX Series Router handles and distributes sessions). From a networking point of view, this solution uses standard protocols.
The following networking features are deployed and validated in this JVD:
- Dynamic Routing using BGP
- Dynamic fault detection using BFD
- Load Balancing of sessions across multiple SRX Series Firewalls in the standalone or high availability environment
- Load Balancing using ECMP Consistent Hashing (CHASH, first appeared in Junos OS Release 13.3R3)
- Load Balancing using Traffic Load Balancer on the MX Series Router (TLB, first appeared in Junos OS Release 16.1R6)
- MX series routers redundancy using SRD between two MX Series Routers with ECMP CHASH
- MX series routers redundancy using BGP Dynamic Routing between two MX Series Routers with TLB
- SRX Series Firewalls redundancy using Multi-Node High Availability (MNHA) as Active or Backup with sessions synchronization
- Dual stack solution with IPv4 and IPv6
- Stateful Firewall (SFW) is validated with simple long protocol sessions (HTTP, UDP). Applications and Advanced Security features (AppID, IDP, URL filtering and other layer 7 features) are not used as part of this JVD.
- Source NAT (SNAT) is using NAPT44
Each JVD is tested with the following platforms:
- Routing and Load Balancer: MX304 with Junos OS Release 23.4R2
- Security Services: vSRX and SRX4600 with Junos OS Release 23.4R2
vSRX Setup and Sizing
This JVD focuses only on the functional aspect of the solution such as a powerful server is not required for hosting the vSRX(s), and vSRX size is not dependent on the JVD results. For real time performances, high end servers (like Dell or HPE servers with Intel Gold or AMK 9K CPUs, 256GB RAM and ConnectX6 or X7 or later interfaces) with large vSRX sizing are proposed (such as 16 vCPU and 32GB RAM). For more information about the vSRX requirements, see https://www.juniper.net/documentation/us/en/software/vsrx/vsrx-consolidated-deployment-guide/vsrx-kvm/topics/concept/security-vsrx-kvm-understanding.html or https://www.juniper.net/documentation/us/en/software/vsrx/vsrx-consolidated-deployment-guide/vsrx-vmware/topics/concept/security-vsrx-vmware-overview.html
