ON THIS PAGE
Dashboard Overview
What is J-Web Dashboard
The J-Web dashboard provides a unified overview of the system and network status retrieved from SRX Series devices.
To use the dashboard at the top-level menu, select Dashboard. By default, the Dashboard page displays all the widget thumbnails.
Figure 1 shows an example of the Dashboard page of SRX345 Services Gateway.
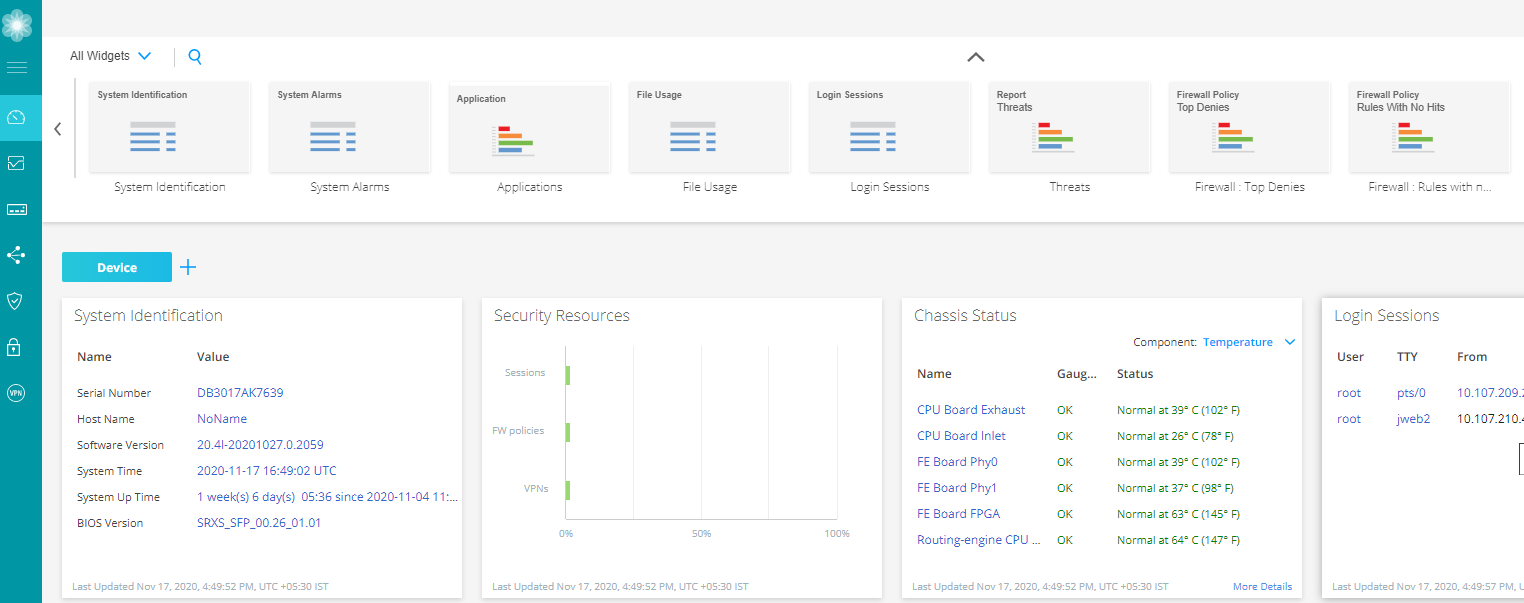
Work with Widgets
Each widget pane acts as a separate frame. You can click + icon to add separate dashboard and name it as per your ease. You can refresh the display of the Dashboard page by clicking the refresh icon at the top right-hand corner above the widget pane.
You can choose any one of the categories to view widgets on your device:
-
All Widgets—Displays all the supported widgets
Applications—Displays only the supported application related widgets
Devices—Displays only the supported device related widgets
Security—Displays only the supported security related widgets
The Threat Activity pane is not available on SRX5400, SRX5600, and SRX5800 devices.
For SRX Series devices configured for logical systems, the Logical System Identification and Logical System Profile panes are displayed when you log in as a user logical system administrator. These are the only logical system panes available in Dashboard Preferences.
If the rescue configuration is not set, the set rescue configuration link directs you to the Device Administration > Configuration Management > Rescue page to set the rescue configuration.
To use a widget on the Dashboard:
Drag the widgets from the palette or thumbnail container to your dashboard.
When you add more widgets on the J-Web Dashboard, you can observe high CPU usage on the Routing Engine for a short span of time on every refresh. We recommend that you use four widgets for lower CPU consumption.
Mouse over the top of each widget to minimize, refresh, and close by using the respective icons.
Note:The dashlet data is refreshed every minute by default. You cannot manually configure the refresh interval of the dashlet. If the data is not aged in the cache, data loads from the cache during the dashlet refresh. If the data is aged, it is retrieved from the device during the next refresh interval cycle.
Table 1 provides the dashboard widgets options based on the selected device.
Field |
Description |
|---|---|
|
System Alarms |
Provides the received time, severity, description of the alarms and the action to be taken. |
|
System Identification |
Provides system details such as serial number of the software, hostname, software version, BIOS version, system uptime, and system time. |
|
Login Sessions |
Provides the user credentials, login time, idle time, and host. |
|
File Usage |
Provides current space requirements for log, temporary, crash, and database files. Click Maintain to download or delete some or all of these files. Note:
File Usage widget supports RE3 line cards for SRX5000 line of devices. |
|
Applications |
Displays top 10 applications based on sessions or bandwidth. |
|
Threats |
Displays top 10 IPS sources, antispam sources, and antivirus name, sorted by count. |
|
Resource Utilization |
Provides a graphical representation of the CPU, memory, and storage used for both the data and the control planes. The CPU control also shows the load average value for 1 minute when you mouse over CPU Control. Note:
Resource Utilization widget supports RE3 line cards for SRX5000 line of devices. |
|
Firewall: Top Denies |
Displays top requests denied by the firewall based on their source IP addresses, sorted by count. |
|
Firewall Policy: Rules With No Hits |
Displays firewall policies with the most rules not hit, sorted by count. |
|
Threat Activity |
Provides the most current threats received on the device. |
|
Firewall: Top Events |
Displays all top 10 firewall events of the network traffic, sorted by count. |
|
IDP: Top Events |
Displays top 10 IDP events grouped by event-type, sorted by count. |
|
Signal Strength |
Displays the signal strength of the device. |
|
Interface: Most Dropped Packets |
Displays top 5 interfaces based on the CLI response; top-count will increase to 10. |
|
Interface: Most Sessions |
Displays top 10 interfaces with most sessions. |
|
IP: Top Destinations |
Displays top 10 destination-address, sorted by count or volume. |
|
IP: Top Sources |
Displays top 10 source-address of the network traffic, sorted by count or volume. |
|
Virus: Top Blocked |
Displays top 10 blocked viruses, sorted by count. |
|
Zones: Top Bandwidth by Packets |
Displays top 10 zones with maximum throughput rate in packets. |
|
Web Filtering: Top Web Blocked |
Displays top 5 Web Blocked based on the CLI response. |
|
Web Filtering: Top Source Address |
Displays top 4 Source Address Web Filter based on the CLI response. |
|
Web Filtering: Top Destination Address |
Displays top 4 Destination Address Web Filter based on the CLI response. |
|
Application & Users: High Risk Applications Blocked Per User |
Displays top 4 High Risk Applications Blocked per user based on the CLI response. |
|
Application & Users: High Risk Applications Allowed Per User |
Displays High Risk Applications allowed per user. |
|
Security Resources |
Provides the maximum, configured, and activated number of sessions, firewall/VPN policies, and IPsec VPNs. |
|
Content Filtering: Top Content Filters |
Displays top 10 Protocol, Reason, and Source-address. |
|
Web Filtering: Top Web Categories |
Displays top 10 Web categories, Security risk, Productivity loss, Legal-liability and Blocked. |
|
Threat Monitoring |
Displays top Malwares identified, Threats and Infected categories. |
|
Top Users of High Risk Applications by Volume/Count |
Displays top users of High Risk Applications by volume. |
|
Application & Users: Top Categories |
Displays top 4 Categories of Application & Users sorted by count and volume. |
|
Application & Users: Top Users |
Displays top 4 Users sorted by count and volume. |
|
Application & Users: Top IPs |
Displays top 4 IPs of Application & Users sorted by count and volume. |
|
Application & Users: Top High Risk Applications |
Displays top 4 High Risk Applications sorted by risk, count and volume. |
|
Antispam: Top Source Address |
Displays top 4 Antispam group by source address and sorted by count. |
|
Application & Users: Application Usage by Category/Type |
Displays top 5 Application Usage by Category group. |
|
Application & Users: Users with the Most Critical Application Usage |
Displays top 5 Users with the Most Critical Application Usage volume. |
|
Storage Usage |
Displays used and available storage and usage information about other system components. |
|
Logical System Identification |
Provides the logical system name, the security profile assigned to the logical system, the software version, and the system time. |
|
Logical System Profile |
Displays the types of resources that are allocated to the user logical system, the number of resources used and reserved, and the maximum number of resources allowed. |
|
Threat Maps: Virus |
Displays last one hour data. Click More Details to view antivirus event logs at Monitor > Logs > Threats. |
|
Threat Maps: IPS |
Displays last one hour data. Click More Details to view IPS event logs at Monitor > Logs > Threats. |
|
NAT - Top Source Translation Hits |
Displays the top 10 source translation hits. Click More Details to view source NAT logs at Monitor > Logs > All Events. |
|
NAT - Top Destination Translation Hits |
Displays the top 10 destination translation hits. Click More Details to view destination NAT logs at Monitor > Logs > All Events. |
|
Incidents By Severity |
Displays the top four incidents of last one hour data. |
|
C&C Server and Malware Source Locations |
You can view either C&C server or malware source through the widget. Both displays last one hour data. Click More Details to view:
|
|
IPsec VPNs (IKE Peers) |
Displays status count of IPsec VPN topologies, such as ADVPN Hub and Spoke, Remote Access, and Site-to-Site/Hub & Spoke. Click More Details to redirect to the Monitor > Network > IPsec VPN page. |
