Webhooks and Alerts
Learn about the various alerts and alarms that you can enable in Juniper Mist™.
Configuring Alerts
You can configure alerts for an entire organization, single sites, or multiple sites from the Alerts Configuration page in the portal.
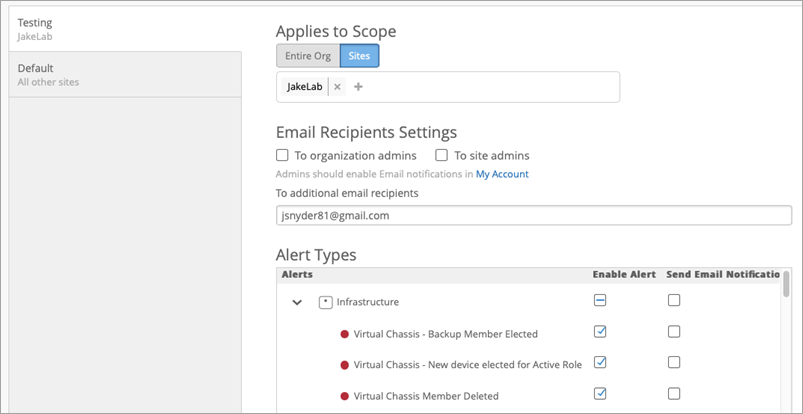
To find this page, select Monitor > Alerts > Alerts Configuration from the left menu of the Juniper Mist portal.
All the alerts visible here are available to send an alert webhook by simply enabling the alert.
The alerts are broken down by color based upon severity, as follows:
-
Red—Critical
-
Orange—Warning
-
Blue—Informational
The alarms are also categorized into these groups:
-
Infrastructure—Infrastructure alarms don’t keep state. They are based directly off device events. When you monitor devices from infrastructure alarms, you typically either treat each event as a standalone event, or you match stateful device changes.
-
Marvis—Marvis events are events identified under Marvis Actions. These events are generally stateful. Inside their payload is a key called
details. Underdetailsyou can seestateand the values:openorvalidated.-
openmeans this issue is currently happening. -
validatedmeans that Marvis has validated that the issue is resolved. After the issue is deemed to be validated, the same webhook type will be set with the updated state.Because of the AI nature of Marvis actions, Marvis requires sufficient data to ensure that these alarms are accurate and actionable. Marvis needs to accumulate enough data to eliminate false positives. This requirement results in a varying number of times for the events to arrive.
-
-
Security—Most of the events in security are single-time events. These alerts will detect only specific attacks and don’t determine if the attack is active. Rogue APs are rate-limited to reporting once every 10 hours. Rogue clients and Honeypot AP events are sent once every 10 minutes.
The following alerts also have configurable failure thresholds:
-
ARP Failure
-
DHCP Failure
-
DNS Failure
-
Device Offline
For information about configuring alerts, see the Alert Configuration information in the Juniper Mist Network Monitoring Guide.
Webhook Alert Types
| Alert/Webhook Name | Group | Category | Description | Triggering Mechanism | Comments |
|---|---|---|---|---|---|
| adhoc_network | Security | AP | Adhoc network detected | One or more APs detected an unauthorized adhoc network. | |
| air_magnet_scan | Security | AP | Air Magnet Scan detected | Someone is running Air Magnet scan for RF analysis. | |
| ap_bad_cable | Marvis | AP | Bad Ethernet cable connected to a Juniper AP | Frequent ethernet disconnects, restarts, increasing ethernet errors, connecting at 100Mbps | Req SUB-VNA |
| ap_offline | Marvis | AP | Offline (Marvis) |
|
Req SUB-VNA |
| arp_failure | Marvis | connectivity | Site-wide wireless connection failures | Sudden increase in failures across the site OR 100% failures on a server/WLAN/AP | Req SUB-VNA |
| authentication_failure | Marvis | Connectivity | Site-wide wireless and wired connection failures | Sudden increase in failures across the site OR 100% failures on a server/switch/WLAN/VLAN/AP | Req SUB-VNAOR SUB-SVNA |
| bad_cable | Marvis | Switch | Faulty cable connected to a Juniper switchport | Port errors, power draw without ethernet link, increase in bytes out and 0 in (and vice versa) | Req SUB-VNA |
| bad_wan_uplink | Marvis | Router | Underperforming/problematic interface (SRX, SSR) | Latency, jitter, packet loss, output drops & drop in transmit packets | Req SUB-WNA |
| beacon_flood | Security | Fake AP Flooding detected - a flood of new BSSIDs | The number of new SSIDs scanned by an AP exceeds the defined threshold during a defined time frame. | ||
| bssid_spoofing | Security | AP | BSSID Spoofing detected | A device with signal strength of -30dBm or worse is broadcasting the same BSSID as an AP with a good signal strength. | |
| device_down | Infrastructure | AP | Device offline | An AP disconnects from the cloud for longer than the configured threshold. | |
| device_restarted | Infrastructure | AP | Device restarted | An AP restarts. | |
| dhcp_failure | Marvis | Connectivity | Site-wide wireless and wired connection failures | Sudden increase in failures across the site OR 100% failures on a server/WLAN/VLAN/AP. | Req SUB-VNAOR SUB-SVNA |
| disassociation_flood | Security | AP | Disassociation Attack detected | Juniper Mist detects a DoS attack in which the attacker disassociates a victim device from an AP by using a specific disassociation frame as specified under IEEE 802.11. | |
| dns_failure | Marvis | Connectivity | Site-wide wireless connection failures | Sudden increase in failures across the site OR 100% failures on a server/WLAN/AP. | Req SUB-VNA |
| eap_dictionary_attack | Security | AP | EAP Dictionary Attack detected | Multiple password failures in which someone attempts to guess a password by trying different dictionary words. | |
| eap_failure_injection | Security | AP | EAP Failure Injection detected | Someone sends fake EAP failures. | |
| eap_handshake_flood | Security | AP | EAP Handshake Flood detected | Some client or simulator generates a floods of EAPOL messages requesting 802.1x authentication. | |
| eap_spoofed_success | Security | AP | EAP Spoofed Success detected | Someone sniff EAP packets and tries to send fake EAP success. | |
| eapol_logoff_attack | Security | AP | EAPOL-Logoff Attack detected | Some client or simulator is sending excessive EAP logoff messages. | |
| essid_jack | Security | AP | ESSID Jack detected | Some client or simulator tries to send a broadcast probe request. | |
| excessive_client | Security | AP | Excessive Clients detected | The number of clients associated with an AP exceeds the configured threshold. | |
| excessive_eapol_start | Security | AP | Excessive EAPOL-Start detected | Some client or simulator is sending excessive EAP START messages. | |
| gateway_down | Infrastructure | SRX | WAN Edge offline | An SRX is offlin. | |
| gw_bad_cable | Marvis | Router | Faulty cable connected to a Juniper gateway (SRX only) port | Interface stat errors, input/output bytes being 0 | Req SUB-WNA |
| gw_dhcp_pool_exhausted | Infrastructure | SRX | WAN Edge DHCP Pool Exhausted | WAN Edge DHCP pool has been exhausted, | |
| gw_negotiation_mismatch | Marvis | Router | Difference in MTU packet size seen in the network (SRX only) | Packets being fragmented, MTU errors. | Req SUB-WNA |
| health_check_failed | Marvis | AP | Unhealthy APs to be replaced | Failure of auto-remediation/self-healing on an AP. | Req SUB-VNA |
| honeypot_ssid | Security | AP | Honeypot SSID | Unauthorized APs advertising your SSID. | |
| idp_attack_detected | Security | SRX/SSR | IDP attack detected | SRX or Session SMart Router reports IDP_ATTACK_LOG_EVENT type events. | |
| infra_arp_failure | Infrastructure | AP | Gateway Arp failure | The ARP request for the default gateway is not receiving any response. | |
| infra_dhcp_failure | Infrastructure | AP | DHCP Failure | More than 10 clients are impacted by a failing/unresponsive DHCP server within a window of 10 minutes. | |
| infra_dns_failure | Infrastructure | AP | DNS Failure | More than 10 clients are impacted by a failing/unresponsive DNS server within a window of 10 minutes, an email will be triggered for this event. | |
| insufficient_capacity | Marvis | AP | AP(s) with low Wi-Fi capacity | After RRM changes, one or more clients have heavy consumption that results in high AP channel utilization. | Req SUB-VNA |
| insufficient_coverage | Marvis | AP | Areas around AP(s) with consistent poor Wi-Fi coverage | After RRM changes, clients still have consitently low RSSI. | Req SUB-VNA |
| krack_attack | Security | AP | Replay Injection detected - KRACK Attack | One or more APs detect KRACK attack attempts. | |
| loop_detected_by_ap | Infrastructure | Wireless | AP has detected loop via reflection | An AP recieves a frame that it sent out. | |
| missing_vlan | Marvis | Switch | VLAN configured on AP missing on switch port or upstream | An AP observes traffic on each VLAN and compares between APs on the same switch and other APs in the site. | Req SUB-VNAOR SUB-SVNA |
| monkey_jack | Security | AP | Monkey Jack detected | An AP detects a Man In the Middle attack attempt. | |
| negotiation_mismatch | Marvis | Switch | Difference in settings between a wired client & connected port | Duplex mismatch and/or auto-negotiation failing | Req SUB-VNA |
| non_compliant | Marvis | AP | APs with mismatched firmware | APs have a different firmware version than most other APs of that model model at that site. | Req SUB-VNA |
| out_of_sequence | Security | AP | Out of Sequence detected | Excessive out of sequence packets. | |
| port_flap | Marvis | Switch | Port constantly going up & down | Port flapping with high frequency and continuously. | Req SUB-VNA |
| repeated_auth_failures | Security | AP | Clients with Repeated Client Authentication Failures | A client faces continues client authentication failures due to an unreachable RADIUS server, wrong shared secret etc. | |
| rogue_ap | Security | AP | Rogue AP detected | Juniper Mist detects an AP not claimed into your organization but connected on the same wired network. | |
| rogue_client | Security | AP | Client Connection to rogue AP detected | A Client associates to a Rogue AP (an AP not claimed into your organization but connected to the same wired network). | |
| ssid_injection | Security | AP | SSID Injection detected: Detects malicious looking SSID names with possible code injection in name | Juniper Mist detects potential code injection language in an SSID name. | |
| sw_alarm_chassis_partition | Infrastructure | Switch | Switch Storage Partition Alarm | Partition usage is high. | |
| sw_alarm_chassis_pem | infrastructue | Switch | Switch PEM Alarm | PEM issues, fault slot,high CPU, issues with CB, and so on. | |
| sw_alarm_chassis_poe | Infrastructure | Switch | Junos POE Controller Alarm | Hardware issues. | |
| sw_alarm_chassis_psu | Infrastructure | Switch | Junos Power Supply Alarm | Missing power supply. | |
| sw_bad_optics | Infrastructure | Switch | Switch Bad Optics | Bad transceiver. | |
| sw_bgp_neighbor_state_changed | Infrastructure | Switch | BGP Neighbor State Changed | BGP peering goes up or down. | |
| sw_bpdu_error | Infrastructure | Switch | Switch BPDU Error | Possible bridging loop. | |
| sw_dhcp_pool_exhausted | Infrastructure | Switch | Switch DHCP pool has been exhausted, | The switch's DHCP pool has been exhausted. | |
| switch_down | infrastructue | Switch | Switch offline | A switch is offline. | |
| switch_restarted | Infrastructure | Switch | Switch restarted | A switch restarted. | |
| switch_stp_loop | Marvis | Switch | Same frame is seen by a switch multiple times | Frequent STP topology changes along with sudden increase in TX/RX. | Req SUB-VNA |
| tkip_icv_attack | Security | AP | TKIP ICV Attack | An AP detects TKIP MIC failures in excess of the configured threshold. | |
| url_blocked | Security | SRX/SSR | URL blocked | SRX or SSR reports WEBFILTER_URL_BLOCKED type events. | |
| vc_backup_failed | Infrastructure | Switch | Virtual Chassis - Backup Member Elected | ||
| vc_master_changed | Infrastructure | Switch | Virtual Chassis - New device elected for Active Role | ||
| vc_member_added" | Infrastructure | Switch | Adding a new VC member | A new VC member was added. | |
| vc_member_deleted | Infrastructure | Switch | Virtual Chassis Member Deleted | A VC member was deleted. | |
| vendor_ie_missing | Security | AP | Mist vendor IE missing in beacon or probe response | Impersonation of sanctioned Mist APs. | |
| vpn_path_down | Marvis | Router | VPN peer path down (SSR only) | 100% failure of a peer path. | Req SUB-WNA |
| vpn_peer_down | Infrastructure | SRX | VPN Peer Down | An IPSec tunnel goes down for WAN interfaces between hub and spoke. | |
| WAN Edge Offline | Infrastructure | SSR | WAN Edge offline | A WAN Edge device is offline. | |
| watched_station | Security | AP | Active Watched Station detected | Juniper Mist detects a client or station that is listed in the Watched Station list. | |
| zero_ssid_association | Security | AP | Zero SSID Association Request detected | An AP scans a beacon that contains a zero length SSID. |
Viewing Alert Details
To see the full list of alarm types and their definitions, you can issue the following request:
GET /api/v1/const/alarm_defs
The following animation demonstrates issuing a GET call from the Mist API Reference in
order to get a list of the definitions for all of the supported alarm types. The Response
displays useful information such as the key, group, severity, and example, which shows
examples of the messages you receive from that particular webhook.
To try this out, see List Alarm Definitions.
The table presents detailed information for just some of the alerts.
In the following table, you can see the subscription requirements for the given webhook. Common webhooks alerts related to audit logs, alarms, or device events, for example, will require you to have a subscription to one of the following: Wireless, Wired, or WAN Assurance.
Within each alarm is contextual data that you can extrapolate for event correlation
comparing multiple devices. You can find examples of all the existing alert (alarm)
definitions with the function /api/v1/const/alarm_defs (link requires you
to be logged in to Juniper Mist).
Event Aggregation
Juniper Mist aggregates events based on topics that you’ve set up. However, not all events are aggregated. Events are aggregated for any topics related to location services, for example, the location, asset-raw-rssi, sdkclient-scan-data, and rssi-zone topics.
If multiple events occur for the same topic during the specified aggregation window, Juniper Mist groups them into a single message. Because of message aggregation, you will need to parse the events from each message when they are received.
