Juniper Mist Access Assurance Authentication Methods
Deploy Juniper Mist Access Assurance with either 802.1X authentication or non-802.1X authentication. Compare the various options to select the best approach for your organization.
IEEE 802.1X is a standard for port-based network access control. It provides a mechanism for authenticating devices that connect to a LAN or WLAN through a switch or access point. Juniper Mist Access Assurance supports both 802.1X authentication and non-802.1X authentication, that is MAC Authentication Bypass (MAB), for uniform access control across wired and wireless networks.
We support the following methods for secure access with 802.1X:
- Extensible Authentication Protocol–Transport Layer Security (EAP-TLS) (digital certificate-based)
- EAP-TTLS/PAP (Tunneled Transport Layer Security) (credential-based)
We support the following non-802.1X authentication methods:
- MAC Authentication Bypass (MAB)
- Multi Pre-Shared Key (MPSK)
Certificate-Based Authentication and Credential-Based Authentication
802.1X authentication method supports credential-based (user name and password) and certificate-based authentication.
Certificate-Based Authentication
- Certificate-based authentication enables mutual authentication between server and client devices and implements cryptography to provide secure network access.
- Digital certificates use a public key infrastructure (PKI) that requires a private-public key pair.
- An identity provider (IdP) is optional in certificate-based authentication. You can use an IdP to check user or device information such as account state and group information.
- Certificates are stored in secured storage.
- Certificate-based authentication requires client device provisioning, for which you typically use mobile device management (MDM).
Juniper Mist Access Assurance can integrate with any existing PKI and cloud-based IdPs such as Microsoft Azure AD, Okta, or Google Workspace to ensure certificate-based authentication is implemented in all applicable use cases.
Password-Based Authentication
- Password-based authentication requires an IdP for authentication. As most IdPs enforce multi-factor authentication (MFA), password-based authentication becomes impractical in 802.1X environments, particularly in wireless networks.
- The risk of person-in-the-middle attacks is significant, as 802.1X does not manage MFA well, especially on a wireless network.
We recommend password-based authentication only for scenarios where a PKI deployment is not immediately feasible or during transitions to certificate-based authentication. Avoid password-based 802.1X authentication in networks that support BYOD because of potential MITM attack vectors.
802.1X Authentication Methods
The 802.1X protocol is an IEEE standard for port-based network access control (NAC) on both wired and wireless access points. The primary function of 802.1X is to define authentication controls for any user or device that attempts to access a LAN or WLAN protecting Ethernet LANs from unauthorized user access. Additionally, 802.1X blocks all traffic to and from a supplicant (client) at the interface until the supplicant presents its credentials and the authentication server (a RADIUS server) validates them.
The basic 802.1X authentication mechanism consists of three components:
- Supplicant—Client devices with authentication software. The client device seeks access to the network. This device could be a desktop or laptop computer, a tablet, a phone, and so on.
- Authenticator—The initial gateway, typically a switch or an access point (AP) that intercepts the supplicant’s access request.
- Authentication Server—Compares the supplicant’s ID with the credentials stored in a database. If the credentials and the supplicant ID match, the supplicant gets to access the network.
Let's understand how Juniper Mist Access Assurance uses each of the 802.1X authentication methods. See Juniper Mist Access Assurance Use Cases.
EAP-TLS
EAP-TLS leverages certificates and cryptography to provide mutual authentication between the client and the server. Both the client and the server must receive a digital certificate signed by a certificate authority (CA) that both the entities trust. This method uses certificates on both the client and server sides for authentication. For this authentication, the client and the server must trust each other's certificate.
Features
- Uses TLS to provide secure identity transaction
- An open IETF standard that is universally supported
- Uses X.509 certificates for authentication
Figure 1 shows the EAP-TLS authentication sequence.
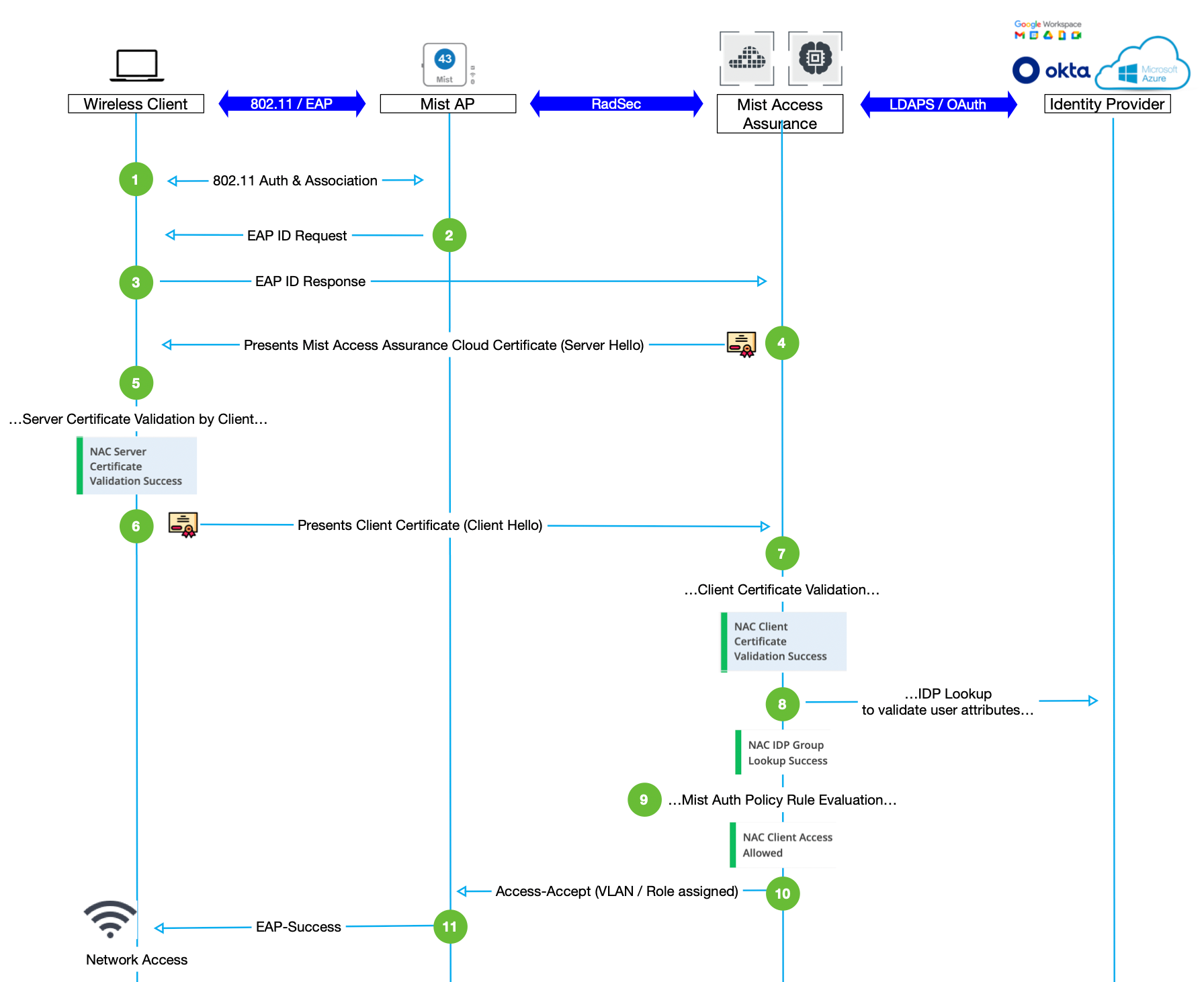
The 802.1X standard specifies EAP as the encryption format for data transmission between a supplicant and an authenticator.
This method performs a four-way handshake with the following steps:
- Either the authenticator (for example an AP) initiates a session request or the supplicant (a wireless client device) sends a session initiation request to the authenticator.
- The authenticator sends an EAP request to the supplicant asking for the supplicant's identity.
- The supplicant sends an EAP response to the authentication server (Juniper Mist Access Assurance cloud) through the authenticator.
- The authentication server responds to the client device with a "Server Hello" message that includes a certificate.
- The supplicant validates the server certificate. That is, the supplicant verfies whether the server certificate is signed by a trusted CA.
- The supplicant sends a "Client Hello" message through the authenticator to present the client certificate to the Juniper Mist Access Assurance service
- Juniper Mist Access Assurance validates that the client certificate is signed by a trusted CA.
- Juniper Mist Access Assurance looks up the configured identity provider (IdP) sources and connects to an IdP to verify the user's name and some basic attributes.
- Juniper Mist Access Assurance performs policy lookup and applies role and permission-based access to the client device.
- Juniper Mist Access Assurance sends information about the VLAN and the assigned role to the authenticator so that it can assign the supplicant to the right network.
- The authenticator sends an EAP-success message and provides access to the supplicant.
Extensible Authentication Protocol–Tunneled TLS (EAP-TTLS/PAP)
EAP-TTLS-PAP uses user credentials, such as username and password on the client side and server certificate on the server side to perform authentication. When a client device establishes a secure TLS tunnel with authentication server, it passes credentials using PAP protocol inside an encrypted tunnel.
Figure 2 shows the EAP-TTLS/PAP authentication sequence.
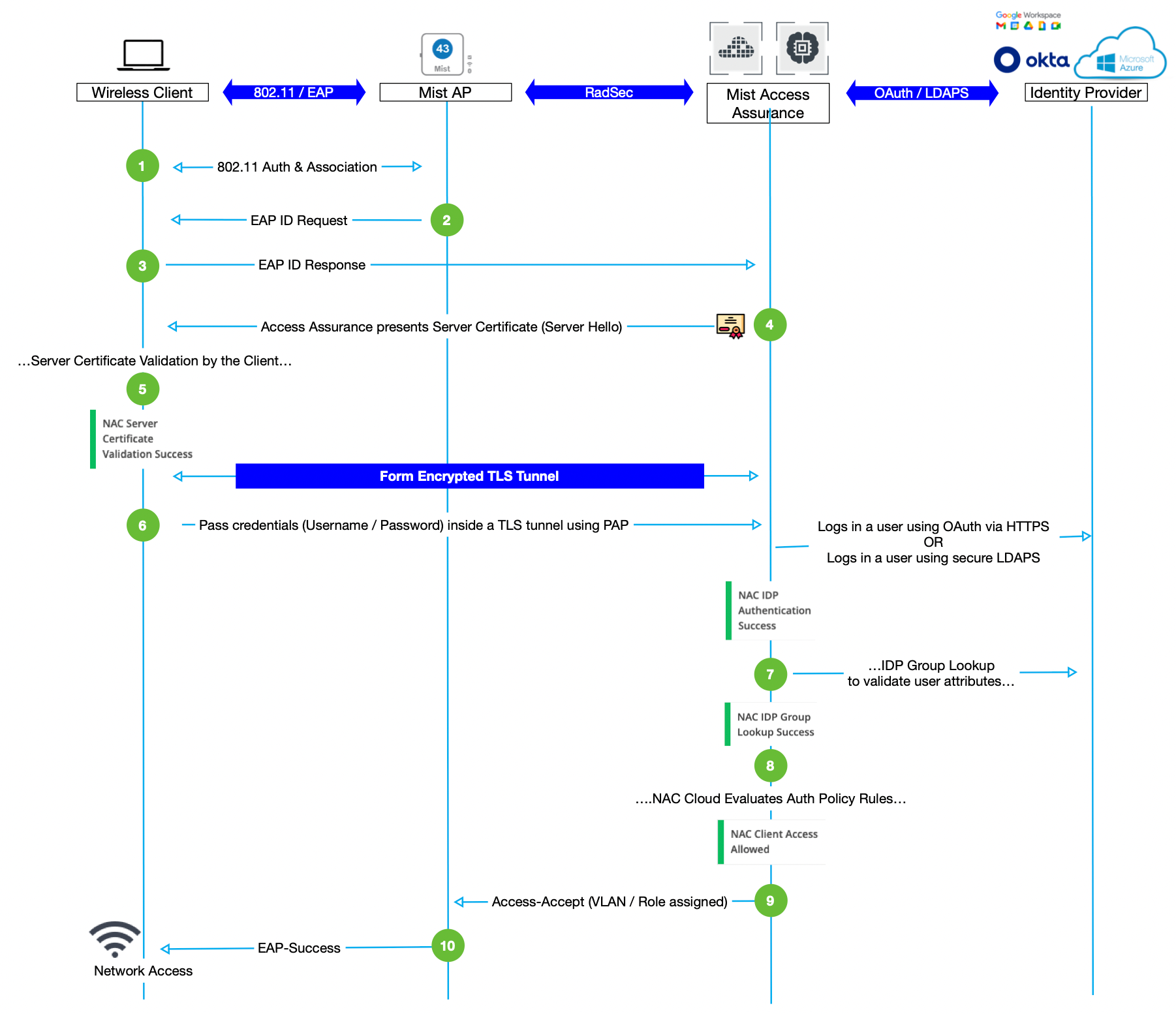
EAP-TTLS/PAP authentication involves the following steps:
- Either the authenticator (for example an AP) initiates a session request or the supplicant (a wireless client device) sends a session initiation request to the authenticator.
- The authenticator sends an EAP request asking for identification information to the supplicant.
- A supplicant sends an EAP response to the authentication server (example: Juniper Mist Access Assurance cloud).
- The authentication server responds to the client device with a "Server Hello" message that includes a certificate. The server sends the message through the authenticator.
- The supplicant validates the server certificate. That is, the supplicant verifies whether the server certificate is signed by a trusted CA. This validation sets up an encrypted TLS tunnel.
- The supplicant sends account credentials, such as user name and password, through a TLS tunnel to the server. The supplicant encrypts the information with Lightweight Directory Access Protocol over SSL (LDAPS) or OAuth (HTTPS).
- Juniper Mist Access Assurance performs a lookup against its configured identity provider sources to find the user's name along with some basic attributes.
- Juniper Mist Access Assurance performs policy lookup and applies role and permission-based access to the client device.
- Juniper Mist Access Assurance sends information about the VLAN and the assigned role to the authenticator so that it can assign the supplicant to the right network.
- The authenticator sends an EAP-success message and provides access to the supplicant.
