Configure VRF Route Leaking for Session Smart Routers
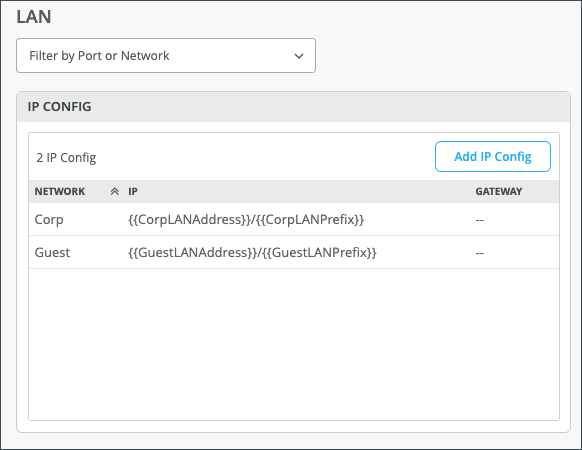
Virtual Routing and Forwarding (VRF) instances enable you to configure multiple routing instances for a single router. For a Session Smart Router deployed as a WAN Edge, you can configure VRF Route Leaking (propagation), which is the intentional sharing of route information across VRF instances. You may want to use VRF Route Leaking so that traffic can be shared or balanced across VRF instances, or maybe you want to share a default route to the internet that can be adopted by each VRF.
Configure VRF Route Leaking on the Session Smart Router
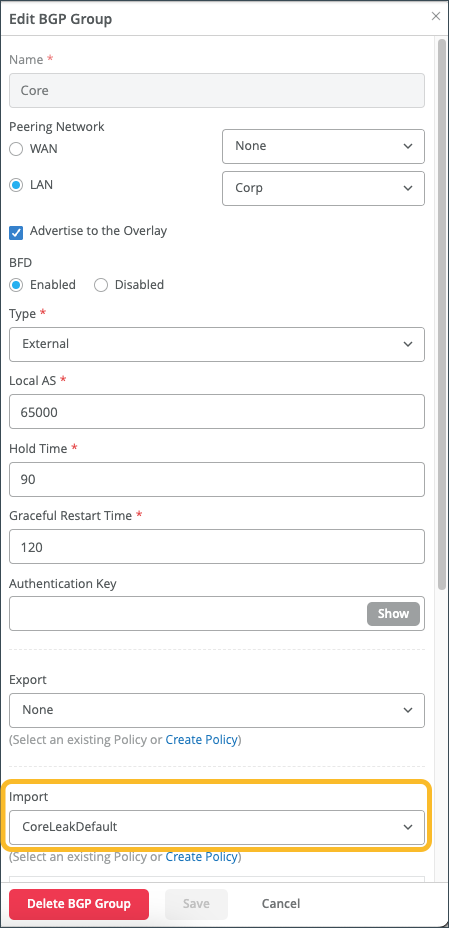
Configure a Routing Policy to Propagate Routes from the Default Instance
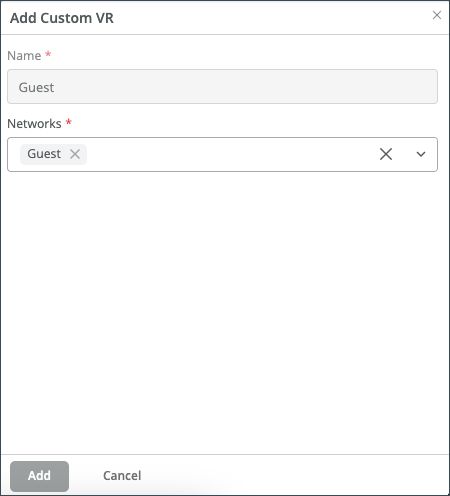
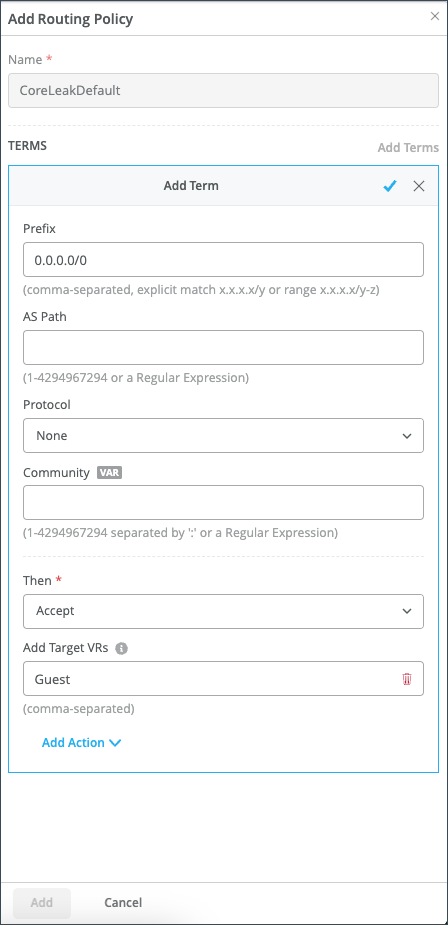
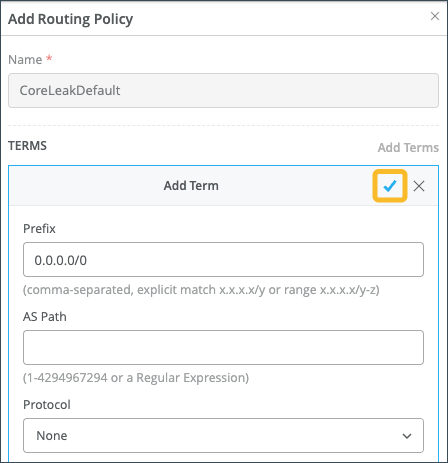
If you want to propagate routes from the default instance to other instances, you must create a Routing Policy and then set that policy as the import policy on the BGP peer. Typically, this policy is associated with a hub (in a hub-to-spoke use case).
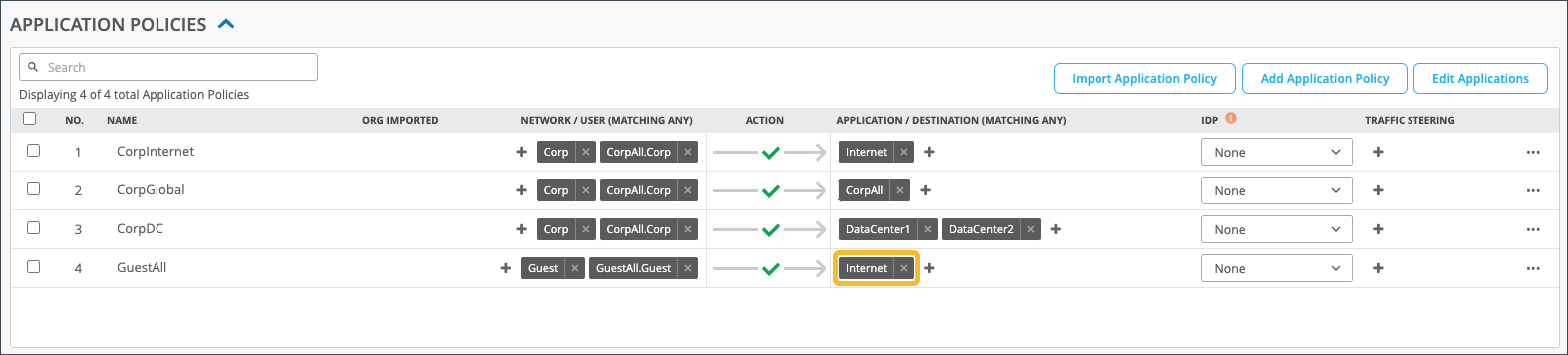
Configure an Application Policy to Steer Traffic
In order to steer traffic from the VRF tenant toward the selected gateway (to create the forwarding plane), you must create an Application Policy. This policy allows the traffic to flow from the VRF toward the next hop of the leaked route.