Integrating Pulse Policy Secure with Juniper Networks Connected Security
Overview
This topic provides instructions on how to integrate the third-party device Pulse Policy Secure (PPS) with Juniper Networks Connected Security solution to remediate threats from infected hosts for enterprises. The Juniper Connected Security solution provides end-to-end network visibility that enables enterprises to secure their entire physical and virtual networks. PPS provides visibility into the network by detecting and continuously monitoring the network. Using the threat detection and policy enforcement, the PPS and Juniper Connected Security solution automates the network security and supports centralised management, in a multi-vendor environment.
PPS integrates with Juniper Networks Connected Security solution through RESTful APIs and takes appropriate action based on the admission control policies. The PPS integration with Juniper Connected Security solution detects and enforces threat prevention policies and provides a collaborative and comprehensive approach towards complete network security. It enables users to leverage the existing trusted threat feed sources to provide a consistent and automated defense across diverse environments.
Benefits of the Pulse Policy Secure Integration with Juniper Connected Security
-
PPS has more visibility of endpoints connected to the network.
-
Based on the threat alerts received from Juniper Connected Security, PPS enhances the security by isolating or acting at the endpoint level.
Deployment of Pulse Policy Secure with Juniper Connected Security
The following high level workflow describes the deployment of PPS with Juniper Connected Security. PPS receives the threat alert information from Juniper Connected Security solution and takes an action on the endpoint based on the admission control policies.
-
User successfully authenticates with the PPS server.
-
User downloads a file from the Internet. The perimeter firewall (SRX Series device) scans the file and based on the user-defined policies, sends the scanned file to Juniper ATP Cloud for analysis.
-
Juniper ATP Cloud detects that the file contains malware, identifies the endpoint as an infected host, and notifies the SRX Series device and Policy Enforcer.
-
Policy Enforcer downloads the infected host feed and sends a threat action to PPS.
-
The PPS server quarantines or blocks the endpoint.
PPS tracks the infected host and does not allow the infected host to acquire full access until the endpoint is disinfected. When the host is disinfected and cleared from Juniper ATP Cloud or Policy Enforcer, PPS receives a clear event from the Policy Enforcer connector. After receiving the clear event, PPS removes the infected host. The host is now authenticated and an appropriate role is assigned to it.
Configuring Pulse Policy Secure with Juniper Connected Security
The network security devices are configured with PPS for admission access control.
A high-level overview of the configuration steps required to set up and run the integration is described below:
-
The administrator configures the basic PPS configurations such as creating an authentication server, authenticating realm, user roles, and role mapping rules. To know more about configuring your PPS, see Pulse Policy Secure Administration Guide.
-
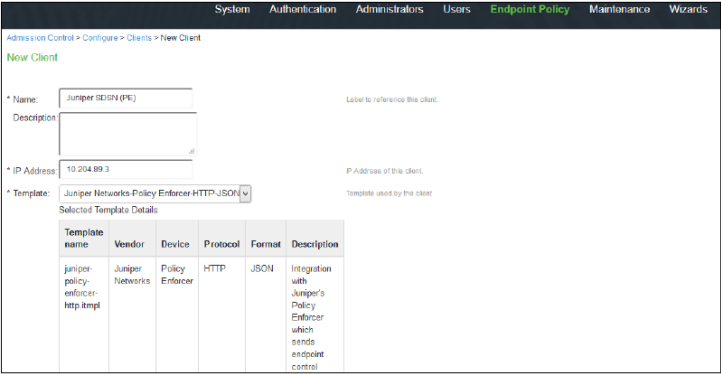
Configure Policy Enforcer as a client in PPS. PPS acts as a RESTful API server for Policy Enforcer.
The RESTful API access for the admin user must be enabled by accessing the serial console or alternatively from the PPS admin user interface (UI). Select Authentication>Auth Server>Administrators>Users. Click Admin and enable the Allow access to REST APIs option.
-
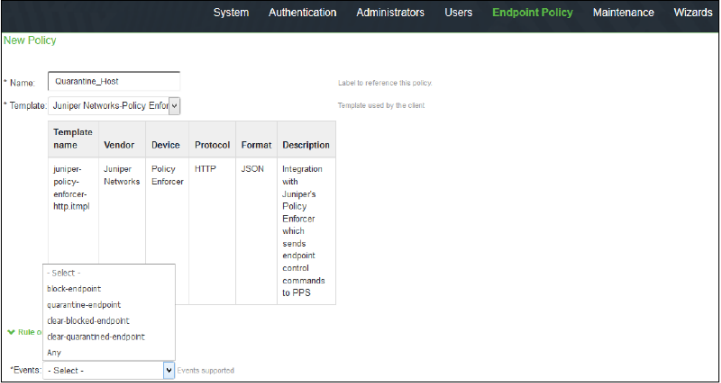
Configure PPS to block or quarantine the endpoint based on the threat prevention policy.
You must configure the admission control client to obtain the Policy Enforcer IP address that sends events to PPS and admission control policy to understand the PPS event types such as, events-block-endpoint, quarantine-endpoint, clear-blocked-endpoint, and clear-quarantine-endpoint.
-
Configure the Switches or WLC as RADIUS Client in PPS by selecting Endpoint Policy>Network Access>Radius Clients>New Radius Client. The switch is configured with PPS as a RADIUS server.
-
Configure RADIUS return attribute policies, to define the action upon receiving the quarantine event.
-
Quarantine using VLANs:
The PPS determines which quarantine VLAN to send to RADIUS Client when a quarantine-endpoint event is received, as shown in Figure 1.
Figure 1: RADIUS Return Attributes for Quarantine-Host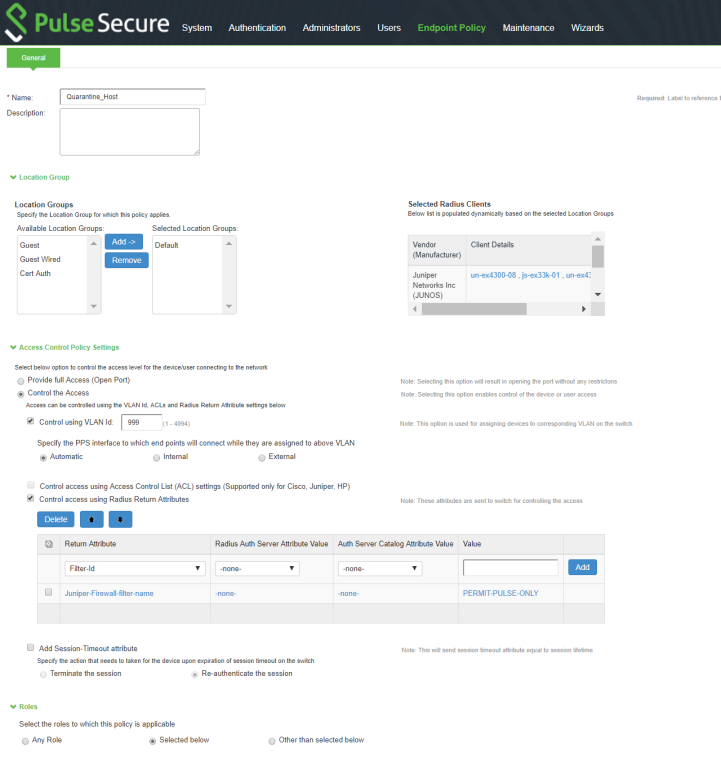
-
Quarantine using ACLs:
For environments that has flat VLAN, the PPS provides the ability to quarantine users by applying a preconfigured firewall filter. Also, this is a preferred method in environments that use static IP address assignment for end devices.
The following example shows the firewall filter configuration on the switch. The firewall filter name is then passed on as RADIUS return attribute, as shown in Figure 2.
Configure the PERMIT-PULSE-ONLY and PERMIT-ALL firewall filters on the switch using the following commands:
set firewall family ethernet-switching filter PERMIT-PULSE-ONLY term pps from destination-address 10.92.81.113/32set firewall family ethernet-switching filter PERMIT-PULSE-ONLY term pps then acceptset firewall family ethernet-switching filter PERMIT-PULSE-ONLY term dhcp_allow from destination-port 67set firewall family ethernet-switching filter PERMIT-PULSE-ONLY term dhcp_allow then acceptset firewall family ethernet-switching filter PERMIT-PULSE-ONLY term pps-discard then discarddeactivate firewall family ethernet-switching filter PERMIT-PULSE-ONLYset firewall family ethernet-switching filter PERMIT-ALL term ALLOW-ALL from destination-address 0.0.0.0/0set firewall family ethernet-switching filter PERMIT-ALL term ALLOW-ALL then acceptdeactivate firewall family ethernet-switching filter PERMIT-ALL
To assign these filters in PPS, select Endpoint Policy>Network Access>Radius Attributes>Return Attributes.
Figure 2: RADIUS Return Attributes for Clear-Quarantine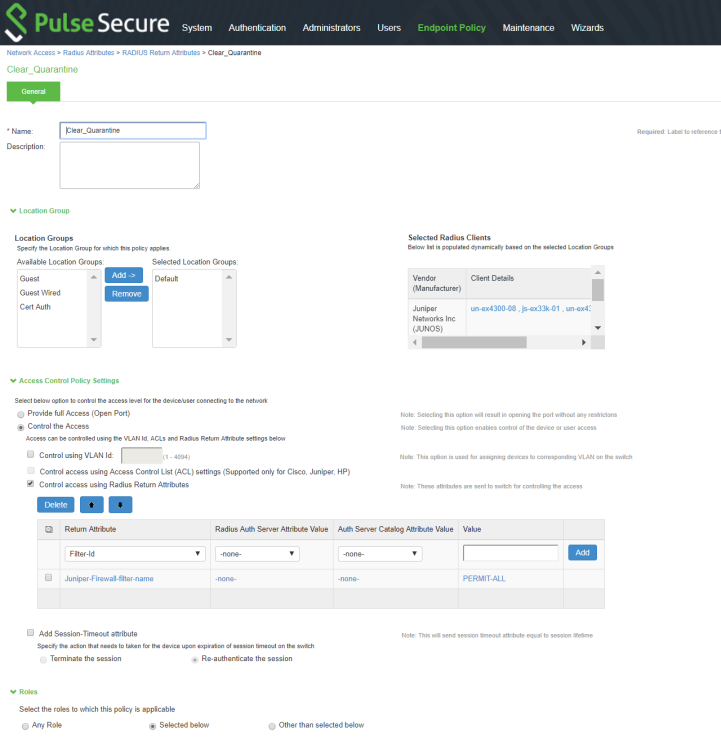
-
-
Ensure that PPS has the endpoint IP address for the enforcement to work correctly.
-
Since the endpoint IP address is mandatory, deployments where the user is behind a NAT might not work as expected. This is because PPS might have the actual IP address, and Juniper Connected Security might send the NATed IP address.
-
To receive the endpoint IP address (accounting information) by PPS, you must use the Pulse Secure client on endpoints when they are connected to EX4300 Series switches.
Admission Control Template
The admission control template provides a list of possible events that can be received from the network security device along with the regular expression to parse the message. The template also provides possible actions that can be taken for an event.
PPS is loaded with default templates for Policy Enforcer. The administrators can create templates for other security devices and upload those templates.
To view the admission control templates, select Endpoint Policy>Admission Control>Templates, as shown in Figure 3. You can view the list of configured integration templates with the list of network security devices and the supported protocol types.
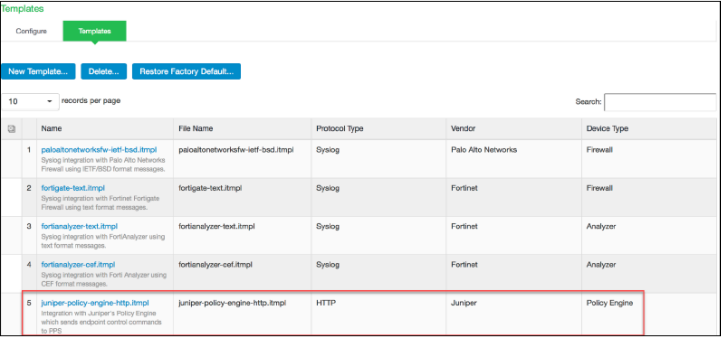
Admission Control Policies
The admission control policies define the list of actions to be performed on PPS for the user sessions. The actions are based on the event and the severity of the information received from the network security device.
To view and add the new integration policy:
Once the policy is created, you can see the summary page. Figure 5 shows the different policies created for different events with different user roles.
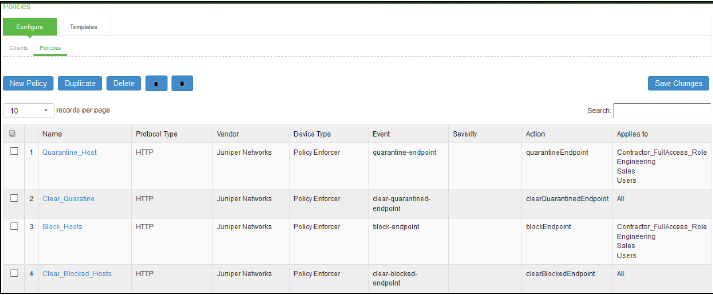
Admission Control Client
The admission control clients are the network security devices on which the syslog forwarding is enabled. The messages are received by the syslog server module running on PPS.
To add a client:
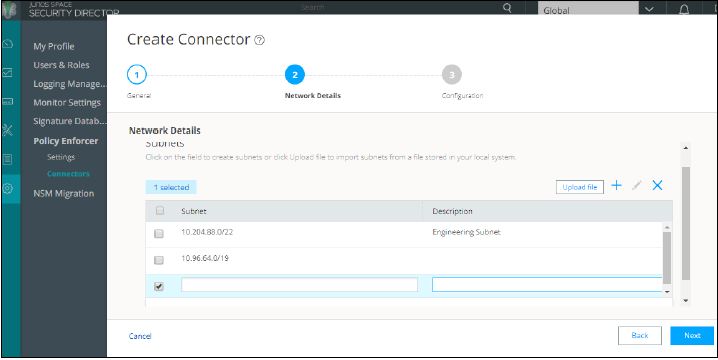
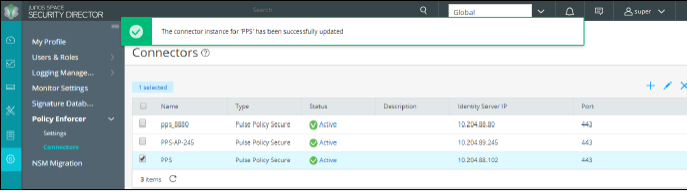
Creating Pulse Policy Secure Connector in Security Director
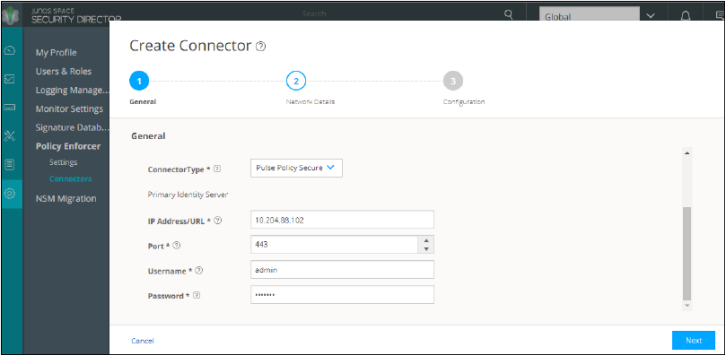
Once you add Policy Enforcer as a client in PPS, create a connector for PPS to configure the Juniper Connected Security to send the event information.
To create a connector for PPS and configure Juniper Connected Security using Security Director:
Troubleshooting
The following troubleshooting logs are available:
-
To verify the event logs on PPS, select System>Log/Monitoring>Events.
You can verify that the event logs are generated every time when an event is received from Policy Enforcer, as shown in Figure 10.
Figure 10: Pulse Secure Events Page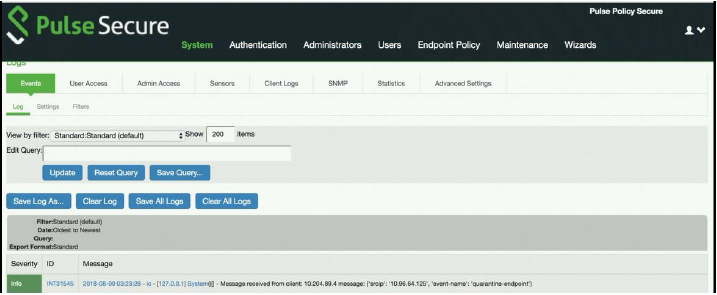
-
To verify the user login related logs such as realm, roles, username, and IP address, select System>Logs & Monitoring>User Access.
-
To verify the reports, select System>Reports>Infected Hosts.
You can verify whether the quarantined or blocked host is listed in the Infected Devices report. This report lists the MAC address, IP address, and the device status, as shown in Figure 11.
Figure 11: Infected Hosts Reports Page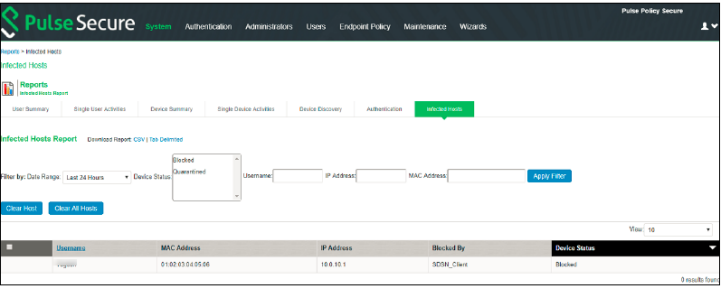
-
To enable the debug logs for troubleshooting, select Maintenance>Troubleshooting>Monitoring>Debug Log, as shown in Figure 12.
Figure 12: Debug Log Monitoring Page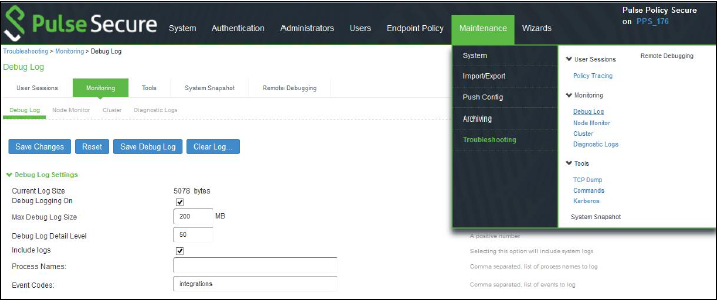
-
To troubleshoot any issues on the Policy Enforcer, download and verify the Policy Enforcer logs from Security Director>Administration>Policy Enforcer>Settings page, as shown in Figure 13.
Figure 13: Policy Enforcer Settings Page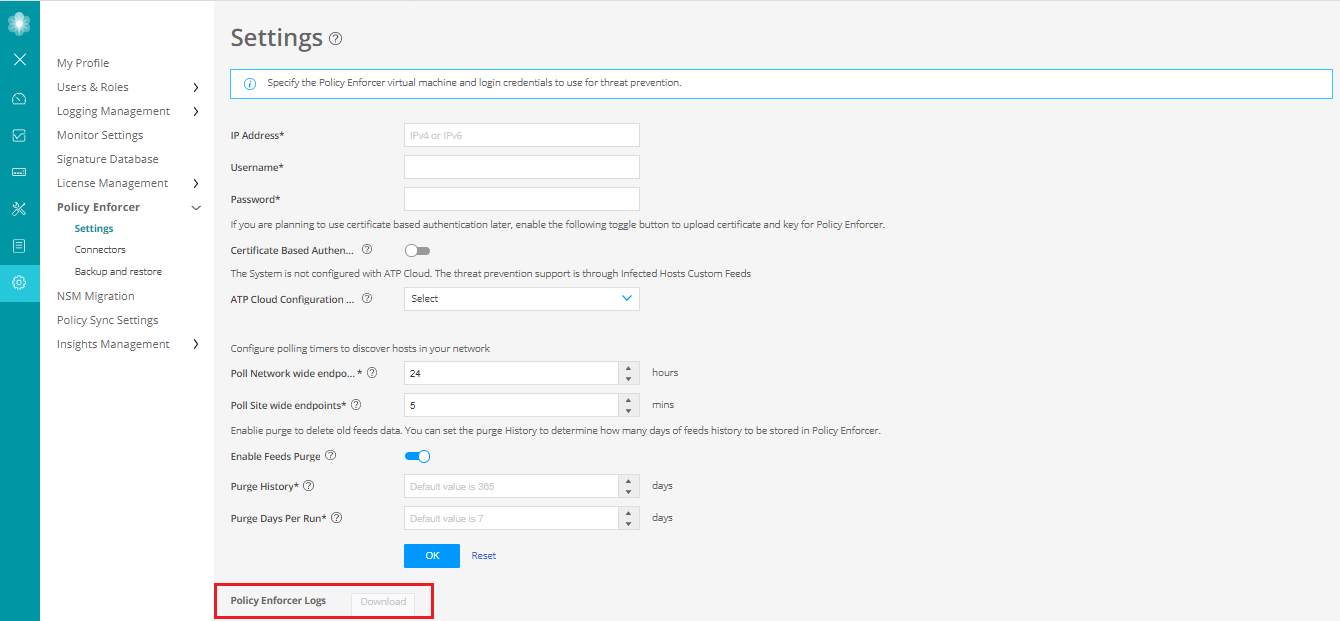
-
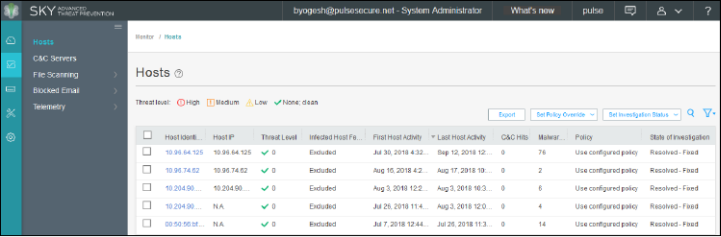
The administrators can also verify the Hosts table from Juniper ATP Cloud to check the status of the host, as shown in Figure 14.
You can clear the host entry if the State Of Investigation field value is Resolved-Fixed.
Figure 14: Juniper ATP Cloud Hosts Page