ON THIS PAGE
Junos Space Security Director Overview
Security Director is a Junos Space management application designed to enable quick, consistent, and accurate creation, maintenance, and application of network security policies. It features an intuitive GUI that provides isolation from the underlying Junos Space Platform, allowing security architects, analysts, and security operators to focus on their jobs. Security Director provides visibility, simplified management, and actionable security intelligence for applications, users, IP addresses, and threats that help network managers make informed security decisions.
Security Director presents the security-focused administrator with a tabbed interface: The tabs across the top of the GUI provide workspaces in which an administrator can perform specific tasks. Table 1 shows the names of the tabs along with brief descriptions of what is accessible in that workspace.
|
Tab Name |
Accesses |
|---|---|
|
Dashboard |
Graphical security widgets that can be added, removed, and rearranged on a per user basis. These widgets offer each user a customized view of network security. |
|
Monitor |
Live threat maps and visual analysis of:
|
|
Devices |
Device discovery and device management. |
|
Configure |
Security-related management including:
|
|
Reports |
Predefined security reports and the ability to create custom reports. |
|
Administration |
User and role management, logging management, and infrastructure management. |
Benefits of Junos Space Security Director
-
Offers a single centralized management interface that enables administrators to manage all phases of the security policy life cycle—stateful firewall, Content Security , intrusion prevention, application firewall (AppFW), VPN, and NAT.
-
Provides a simple user interface that enables new users to quickly become proficient.
-
Automates the deployment of the most recent policy updates through the Policy Enforcer feature. The risk of compromise and human error is reduced as network administrators are able to wok with a simple and concise rule set.
-
Enables effective threat management while producing detailed data access and user activity reports. An action-oriented design enables the network administrator to detect threats across the network as they occur, quickly block the traffic going to or coming from a specific region, and apply immediate remedial action with a single click.
-
Enables administrators to assess the effectiveness of each firewall rule and quickly identify the unused rules, which results in better management of the firewall environment.
-
Simplifies policy creation and maintenance workflows through metadata-based policies, and streamlines threat remediation workflows through dynamic policy actions.
-
Offers a seamless search function when correlating petabytes of data across hundreds of nodes.
Access and Log in
If you are working in the Junos Space Platform, you can access Security Director by selecting Security Director from the Applications drop-down list at the upper left corner of the Space GUI, as shown on the left side of Figure 1.
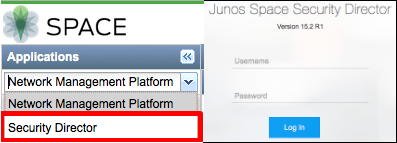
After you log out of the Security Director GUI (or the login timer expires while in Security Director), the next time you log in the Security Director login screen will appear, as shown on the right side of Figure 1. Once you use the Security Director login screen, that will remain your default login location unless and until you navigate to the Space Platform URL or return to the Space Platform GUI and either log out from there or let the login timer expire.
When the Security Director application is accessed for the first time, a getting started guide will overlay the Security Director Dashboard page. The guide is designed to assist new and longtime users by providing a quick reference to where functions are located within the new GUI. The guide can be dismissed for subsequent logins and accessed later through the help button on the right side of the banner.
Using Navigational Elements
For a more personal, helpful, and customizable user experience, Juniper Networks has provided some aids within the GUI. Table 2 shows a sample of navigation, customization, and help icons.
|
Element |
Icon |
Location |
|---|---|---|
|
Breadcrumbs—Trace your location in the GUI. The breadcrumbs provide a path back to one of the six starting tabs: Dashboard, Monitor, Devices, Configure, Reports, and Administration. |


|
Upper left part of main screen below the Monitor tab. Not visible on the Dashboard. |
|
Info Tips—Hover your mouse over any available question mark icon for quick pop-up guidance. |
|
Various places around the GUI. |
|
Show and Hide Left-Nav—Click the hamburger icon to show or hide the left-nav section. |

|
Left side of tab bar, below the Juniper Networks logo. |
|
Show Hide Columns—In tabular displays, you can choose which columns are visible by clicking the icon and then selecting the check boxes on the menu. |

|
Upper right corner of some tabular display windows such as the Reports tab and Devices tab. |
|
Table Search—You can click this magnifying glass icon, within large tabular views, to search for specific text within any of the visible fields in the display. |

|
Upper right corner of tabular views. Next to the Show Hide Columns icon. |
Banner Overview
The dark gray bar at the top of the screen is called the Banner. It provides access to system-wide utilities such as a link back to Junos Space Platform, a global search utility, a domain switcher, a notification center, a profile management access menu, and a help button.

Junos Space Platform Link

The GUI for Security Director is designed to enhance security focus. Therefore, for administration or other tasks that are not security related, you will need a way to switch back to the Space Platform GUI. In Security Director, this can be accomplished by simply clicking the Juniper Networks logo in the upper left corner of the banner.
Search Utility

Sometimes you just need to search for things. Did I already create an address object for the corporate management network? Is there a URL category for gambling? If you find yourself in need of search capabilities, the Global Search Utility will fulfill your needs. Type a term into the search field and Security Director will show you all of the places where that term is found. The results lists are clickable, so that you can go directly to the found object simply by clicking.
Domain Switcher

Security Director supports multitenancy in the form of domains. Domains provide a customizable separation of managed assets and their configuration elements. See Domains Overview for more information.
Notification Center

On the right side of the banner is a bell-shaped icon called the Notification Center. Clicking this icon reveals lists of the top alerts and alarms in Security Director. Clicking the View All Alarms or View All Alerts links at the bottom of the drop-down menu takes you to the detail page for the respective topic.
User Functions Menu
To the right of the Notification Center, there is a head-and-shoulders icon and a field showing the logged in user. Clicking your user name will allow you to access your user profile or log out of Security Director.
Help Button

Access to the online Help system and the Getting Started Guide are available by clicking the right-most icon on the banner, shaped like a question mark. The help system includes access to a list of supported web browsers, user interface assistance, as well as links to technical support and full Security Director documentation.
Search Overview
You can search objects and devices from various tabs using a partial or full name, IP address, or other values. There are different categories of search in Security Director and supported patterns are regular expressions, partial word search, special character search, and so on.
Search Patterns
You can use the following regular expressions to search the objects.
-
* (multiple character search)—If you do not know the full name of an object, use * at the start or end of the name.
For example, when you search with test* on the Addresses page, ILP displays the following results:
-
test-2-SRX
-
test_1-SRX
-
-
? (single character search)—You can replace a single character with ? in search text.
For example, when you search with test?org?net on the Addresses page, ILP displays test.org.net result.
Search limitations
-
A partial name search with a single character replacement does not work. If the search text is split by any special character such as - , _ , /, :, ., and ; and if you try to search with a partial name, results will not be displayed.
For example, if address object name is test-2-SRX, and you try to search test?2, then results will not be displayed.
However, you can do a full text search including as many ? in between the name, for example, test?2?S?X.
Search Categories
Global Search
Using global search, users can search any Security Director object including SRX Series devices with a name or an IP address. Global search checks the search text or IP address across all objects or devices of Security Director and displays the results in the user interface.
For example, if you create a firewall rule, scheduler, address, and service with same name in Security Director and search that name using the global search text box, the results are displayed with domains.
Global search results are displayed in the format Name of the Object | Type of the Object | Domain Name.
ILP Search
All objects and devices pages such as, address, service, firewall policy, firewall rule, and so on have search boxes at the top right corner (ILP search box). You can search using a name, a device IP address, and so on.
For example, in a firewall rules table, you can search the rule by using a name, a zone, an address, a scheduler name, and so on.
Column Search
You can perform a granular level of search using column level search in the complex tables, which has more data, such as firewall, NAT, IPS, VPN policies, rules table, and devices table.
If you click the column search icon placed at the top right corner of the table, near the search icon, the column search text box is displayed in the user interface. You can filter records using one or more columns.
Item Selector Search
You can use a search text box to select items for inclusion in a rule or policy.
For example, when creating an address or service group, you can first search for the address or service object. Similarly, in firewall, IPS, and NAT rule creation, source and destination addresses can be searched in the item selector using a regular expression, a full name, and a partial name.
Delimiter Search Limitations
The search text should not contain a delimiter that marks the beginning or end, such as a comma, hyphen, and so on. You can search the object by partial word or with * at the end of the text.
For example, if object names are test-SRX, test-SRX-UK, test-SRX_US, and so on, then you cannot search with test-, results will not be displayed.
However, if you search with the text test, then the object that contains the name as test (either before or after a delimiter) is displayed.
Refresh Search Index
If you have any issues while searching for newly added or existing object in any category, such as global, ILP, and column search, then you can trigger the refresh search index from the Junos Space Network Management Platform page. Based on the number of objects, such as the number of addresses, service, and firewall policies in Security Director, the refresh search index might take time.
In Junos Space Network Management Platform page, select Administrator > Application. Right-click Security Director and click Refresh Search Index. See Figure 9.
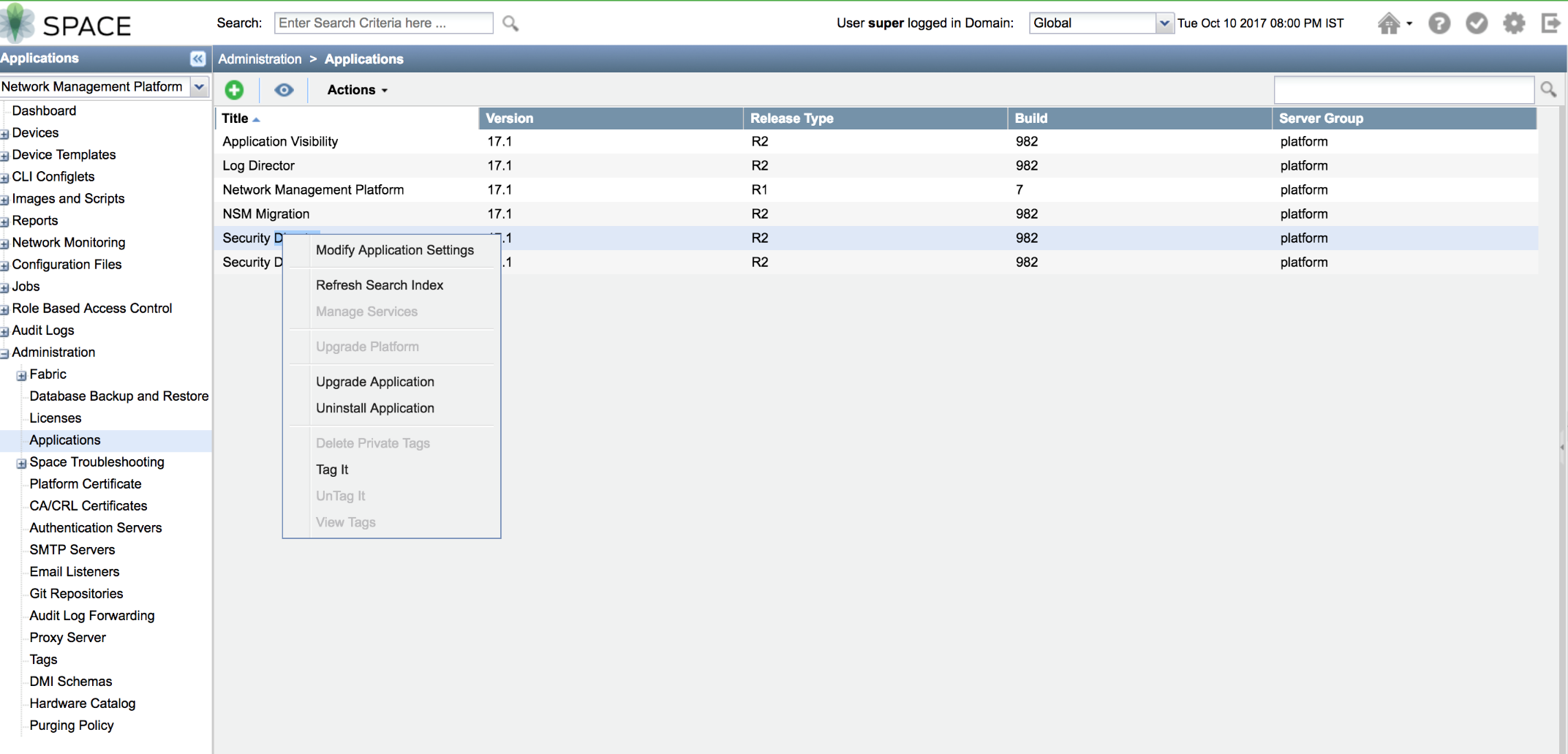
Wait for about 10-15 minutes, and then try to search objects again in Security Director.
This operation should not be performed frequently. This can impact the overall Security Director performance.
Main Workspace Overview
The main workspace of Security Director takes up the remainder of the browser window and is divided by six horizontal tabs just below the Banner. The six tabs are: Dashboard, Monitor, Devices, Configure, Reports, and Administration. Each workspace and its accessible functions are described later in this document.
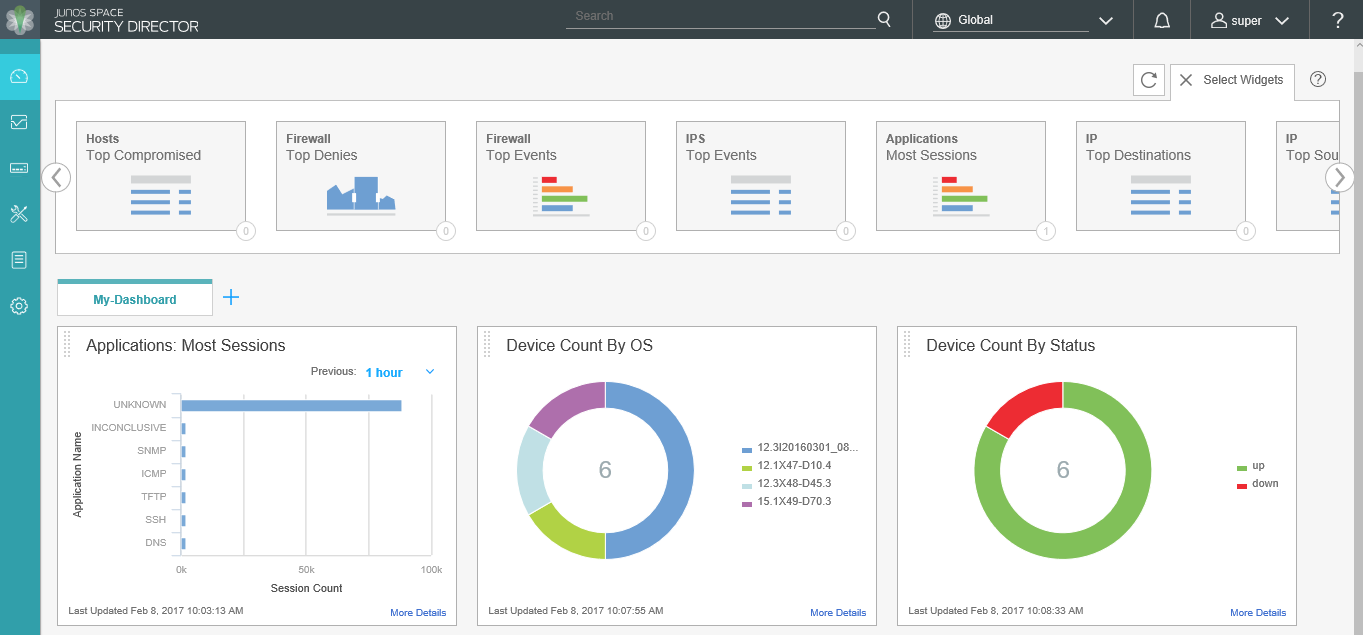
Dashboard
The Dashboard is the main landing page for Security Director. It is the first thing you will see each time you log in. Therefore, Juniper Networks has provided a means for you to be presented with the network security information that you are most interested in. You can customize the workspace in your Dashboard by adding widgets from the carousel below the banner. The placement of, and settings within, widgets are saved so that anything from device information to firewall event information or from top blocked viruses to live threat maps can be unique for each user. Once you decide on the widgets that you want to see, you can close the carousel to regain some screen space.
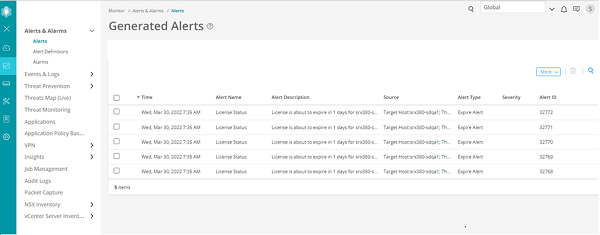
Monitor
The Monitor tab provides a workspace in which graphical representations of network traffic, firewall events, live threats, and network user data are available. There is also detailed data for alerts and alarms and job management information. In this workspace, you can review the detailed information needed to understand what is happening to the managed security devices and traffic in your network.
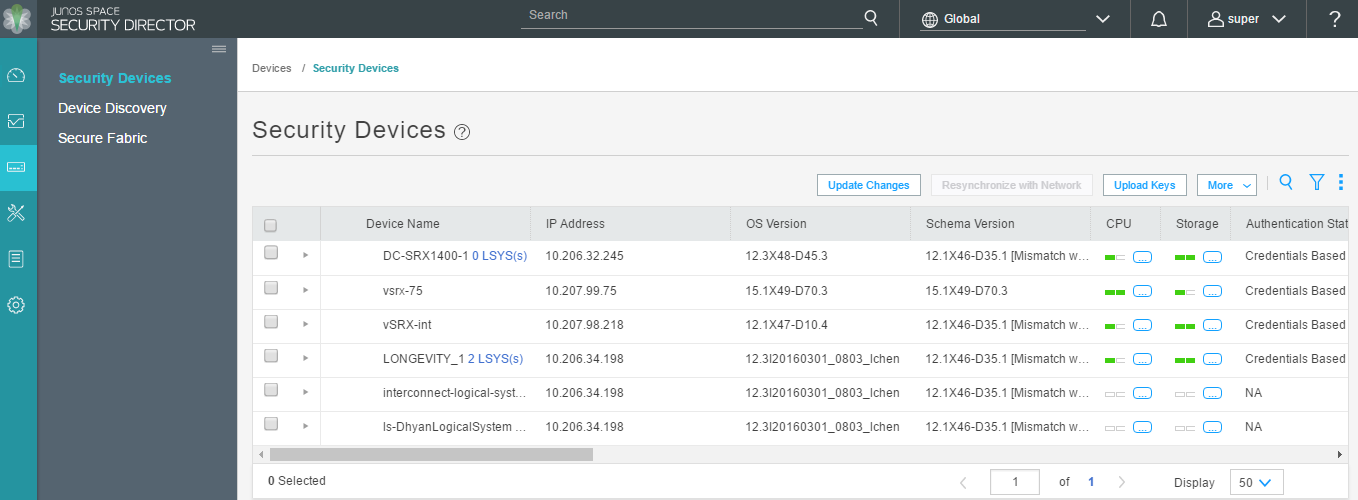
Devices
The Devices tab provides a workspace in which you can add and manage Security Director devices. There are several columns of information available by default. This includes live CPU and memory data, and running software version and platform information. Schema mismatches are easily visible so that you can correct them before updating a device.
Before working with a particular device in Security Director, ensure that the proper DMI Schema is available. If there is a mismatch between the device’s software image and the schema version that Security Director is using to manage the device, unexpected behavior will result. DMI Schema management is performed in the Junos Space Platform Administration workspace.
Configure
The Configure tab is the workspace where all of the security configuration happens. You can configure firewall, IPS, NAT, and Content Security policies, assign policies to devices, create and apply policy schedules, create and manage VPNs, and create and manage all of the shared objects needed for managing your network security.
Reports
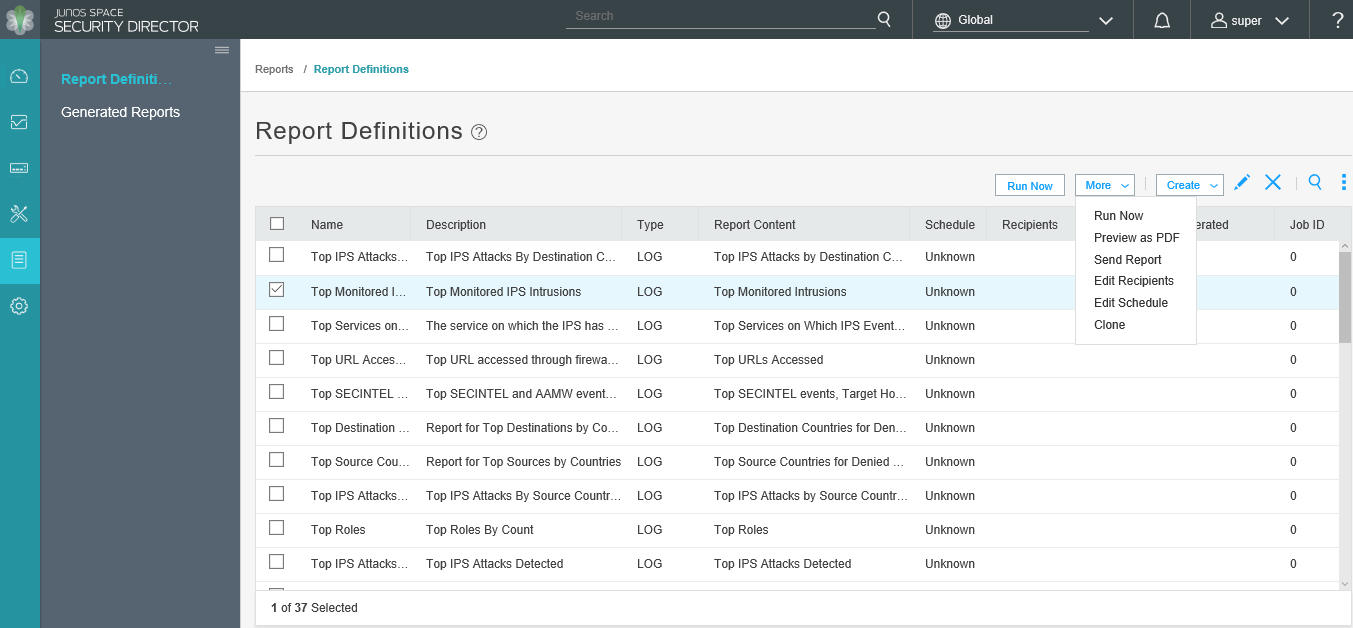
The Reports tab provides a workspace in which you can create and send reports to other interested parties. The reports available on the Dashboard tab are a subset of the reports available here. When run, the report engine provides both graphic and numeric data for a complete visualization of the log data. Security Director comes with a predefined set of reports, and you can add your own customized reports from scratch or by cloning any of the predefined reports.
Administration
The Administration tab provides a workspace in which you can manage role-based access control (RBAC), review and manage audit logs, manage logging, review and update the IPS signature database, and manage your login profile. Domain RBAC allows system administrators to logically divide Security Director into sections called domains. Policies, objects, logs, and services created for devices within any one domain are available for use only within that domain. User access can also be restricted to individual domains. For more information regarding RBAC, see Domain RBAC Overview.
Global Features
Security Director contains assistive workflow wizards that guide you through some of its security functions. These include a rule-creation wizard and an add-device-profile wizard.
The publish workflow allows security configurations to be created or changed, assigned to devices, published and then updated to those devices. Policy changes, whether to IPS, Firewall, or any other managed policy can be staged by network operations center (NOC) personnel, previewed and approved by network administrators, and updated to the devices individually or all at once during maintenance windows or as often as needed by using the publish workflow.
Cloning allows quick duplication of everything from objects, to rules, to entire policies. When dealing with complex rules or policies, cloning to make changes can ensure that there is a consistent starting point from which to make changes.
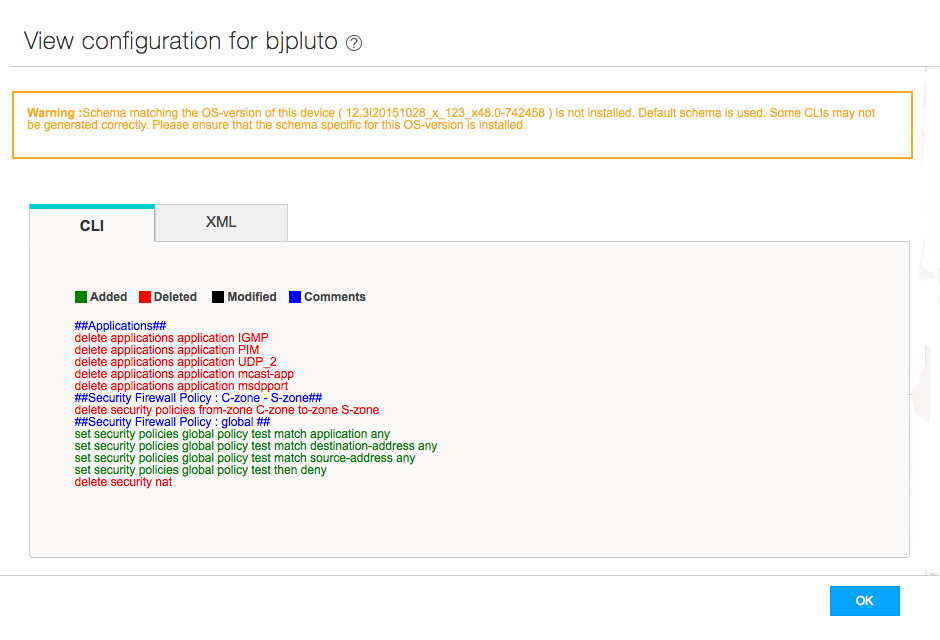
The configuration preview is available as CLI commands or as XML.
Conclusion
Security Director is a security management application designed with speed and scale in mind. Shared objects can be created and used across many security policies and devices. Firewall policies, NAT policies, and others can be created, changed, managed, and applied to individual devices or to groups of devices.
RBAC and domain features enable the Security Director administrator to allow access to many levels of users while restricting the visibility that they have into sensitive security information. Security devices, users, shared objects, and policies in one domain remain inaccessible to users who do not have access to that domain. Thus service provider organizations can provide customer isolation, allowing them to diversify their customer base. User management can be performed locally within Security Director, or remotely using central user management systems such as RADIUS.
And finally, events received by Security Director are logged and correlated in various ways, providing graphical and numerical charts that are understandable and actionable. Reports based on this information can be run and sent directly to stakeholders within an organization. The reports can show security and user trends over time, helping decision makers to craft concise and accurate security policies.
