Understanding Zone Sets
Security zones are the building blocks for policies; they are logical entities to which one or more interfaces are bound. Security zones provide a means of distinguishing groups of hosts (user systems and servers) and their resources from one another to apply different security measures to them.
A zone set is a grouping of two or more zones in a network to regulate and secure the traffic through the security platform running Junos OS. With zone-based security, you can define multiple security zones, group similar interfaces, and apply the same policies to all zones. Zone sets are referenced in the global firewall group to avoid creating multiple policies across every possible interface.
In Security Director, a zone set is a group of multiple zones and not a device-level object.
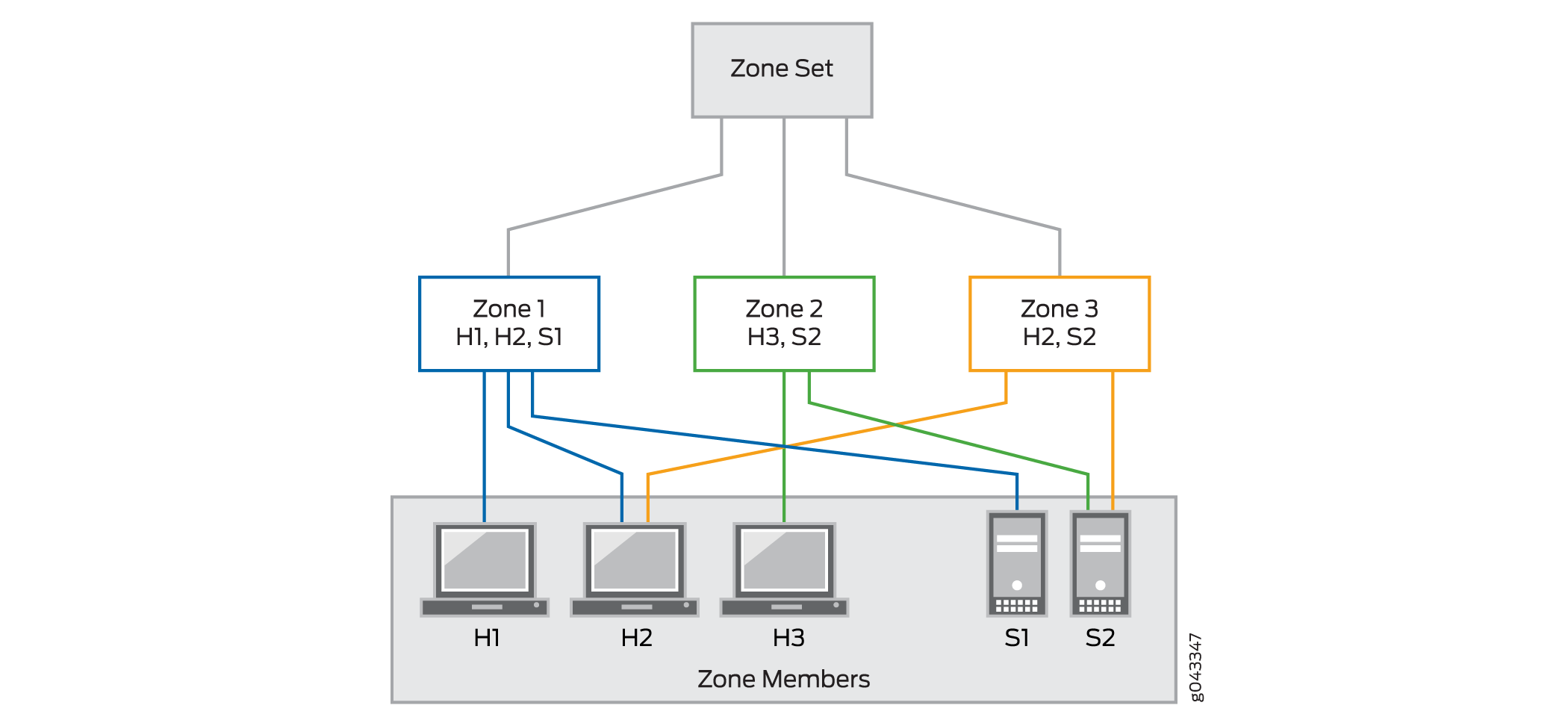
Figure 1 shows a zone set with three zones, Zone 1, Zone 2, and Zone 3. Zone 1 provides access from hosts H1 and H3 to the data residing on server S1. Zone 2 provides access from host H3 to the data residing on server S2. Zone 3 provides access from host H2 to the data residing on server S2.
Interfaces act as a doorway through which traffic enters and exits a Juniper Networks device. Many interfaces can share exactly the same security requirements; however, different interfaces can also have different security requirements for inbound and outbound data packets. Interfaces with identical security requirements can be grouped together into a single security zone. See Figure 2, which shows a basic zone topology that includes a router connected to three interfaces.
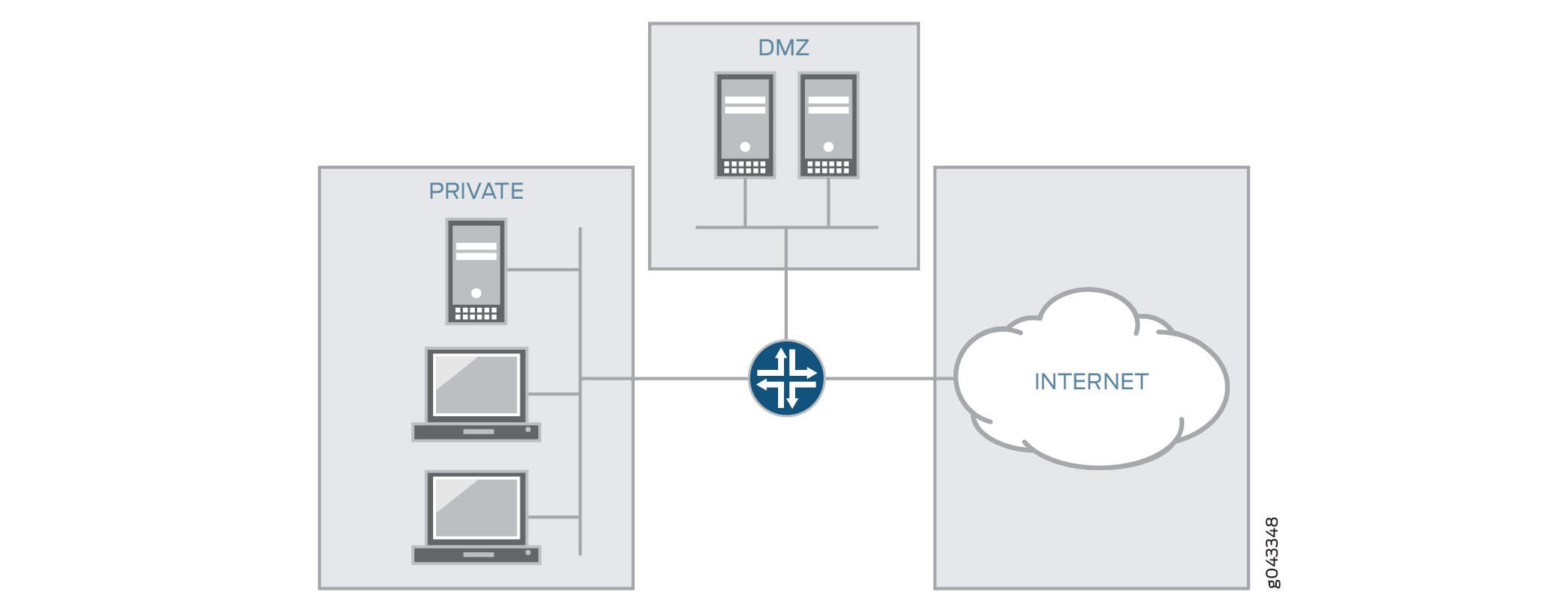
Figure 2 shows a basic zone topology with three zones, private LAN, DMZ, and public Internet. A router within the zone to three interfaces:
-
One interface connected to the public Internet
-
One interface connected to a private LAN that must not be accessible from the public Internet
-
One interface connected to an Internet service demilitarized zone (DMZ), where a webserver, Domain Name System (DNS) server, and e-mail server must be accessible to the public Internet
Each interface in this network is assigned to its own zone, although you might want to allow varied access from the public Internet to specific hosts in the DMZ and varied application use policies for hosts in the protected LAN.
In this network, there are three main policies:
-
Private zone connectivity to the Internet
-
Private zone connectivity to DMZ hosts
-
Internet zone connectivity to DMZ hosts
If an additional interface is added to the private zone, the hosts connected to the new interface in the zone can pass traffic to all hosts on the existing interface in the same zone. Also, the traffic from the hosts to hosts in other zones is similarly affected by existing policies.
