ON THIS PAGE
About the Log Sources Page
To access this page, select Configure > Insights > Log Sources.
Security products such as Juniper Secure Analytics (JSA) can act as a log source. You can create multiple log parsers for different log sources. The log source name is the hostname portion of the syslog message that Security Director Insights uses to identify the log source, and how Security Director Insights will parse its logged events.
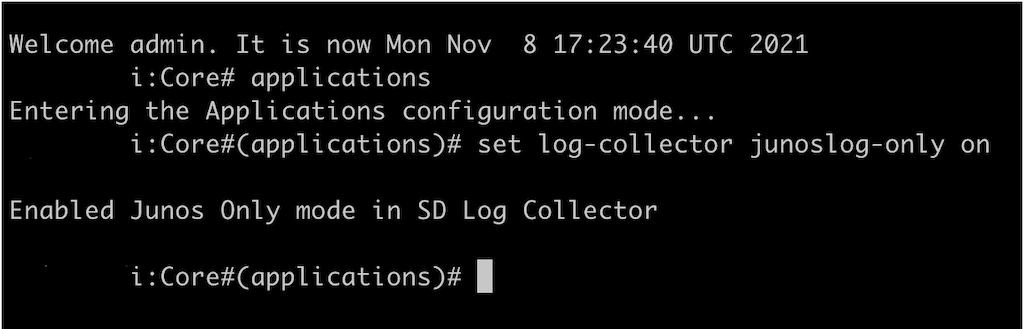
Starting in Security Director Insights Release 21.3, you can
enable Security Director log collector to receive logs from Junos
only. Use the set log-collector junoslog-only on CLI command
in the application mode, as shown in Figure 1.
Tasks You Can Perform
You can perform the following tasks from the Log Sources page:
-
Add log sources. See Add a Log Source.
-
Edit and delete log sources. See Edit and Delete a Log Source.
-
View log statistics. See View Log Statistics.
-
Enable or disable the third-party log sources by toggling the Enable Third-Party Log Sources option.
If you enable this option, support for Junos Release 21.X logs is disabled. If you disable this option, support for Junos Release 21.X logs is enabled.
Field Descriptions
Table 1 provides guidelines on using the fields on the Log Sources page.
|
Field |
Description |
|---|---|
|
Log Source Identifier |
Specifies the unique string that needs to be looked for. |
|
Parser |
Specifies the name of the log parser assigned to that particular log source. |
|
Severity |
Specifies the severity of the log parser. |
|
Actions |
Specifies different actions that you can take for a log source. |
