Authentication
You can authenticate NorthStar users in one of three ways by the admin: Local authentication, LDAP authentication against an LDAP server, or, as of NorthStar Controller Release 5.1.0, Remote Authentication Dial-In User Service (RADIUS) authentication. To configure user authentication, select Authentication from the Administration menu and select an authentication method.
LDAP and RADIUS-authenticated users:
Can save user preferences such as time zone and date/time format.
Cannot change their password.
Cannot have their password changed by someone else.
Local authentication—(default) User information is stored in the local database.
User authentication against an LDAP server—Users are authenticated using an external LDAP server rather than the default local authentication. This enables in-house authentication. The client sends an authentication request to the NorthStar Controller, which forwards it to the external LDAP server. Once the LDAP server accepts the request, NorthStar queries the user profile for authorization and sends the response to the client.
Figure 1 shows the Authentication Settings page with the LDAP server option selected. The fields are described in Table 1.
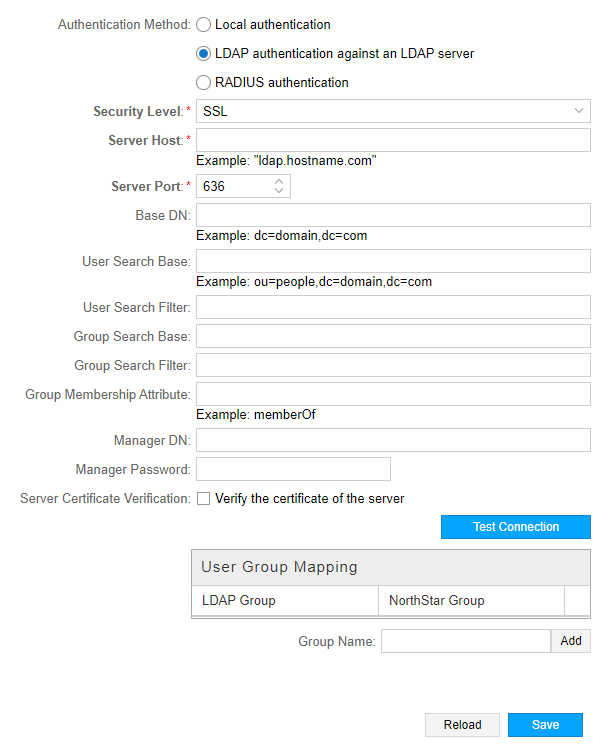
Field |
Description |
|---|---|
Security Level |
Required. Use the drop-down menu to select SSL or None. |
Server Host |
Required. Name of the server host. For example: ldap.hostname.com. |
Server Port |
Required. Port number between 1 and 65000. The default port for LDAP is 636. |
Base DN |
Base distinguished name (DN). The root tree for LDAP searches. For example: dc=company,dc=com. |
User Search Base |
The sub tree for LDAP searches for a specific user. For example: ou=people,dc=company,dc=com. If this field is not set, the LDAP authentication module searches from the base DN. |
User Search Filter |
The attribute for searching for a user. If not specified, “cn” is used. Some Active Directory servers might use “sAMAccountName”. Certain OpenLDAP servers use “uid” if “cn” is not supported. |
Group Search Base |
(placeholder for future use) |
Group Search Filter |
(placeholder for future use) |
Group Membership Attribute |
The attribute in the user record for extracting group membership. Use “memberOf” on Active Directory servers and “member” for OpenLDAP servers. |
Manager DN |
LDAP account (in full DN) for querying a user record for password verification and group association. Used when the server is not configured with anonymous binding (query without a password). |
Manager Password |
Password for the user specified in the Manager DN field. |
Server Certificate Verification |
Click the check box to indicate the certificate of the server is to be validated. |
User Group Mapping |
LDAP user groups map to NorthStar user groups, which the admin users can define, and customize their permissions. |
Click Test Connection to attempt a connection with the LDAP server. If the Manager DN and Manager Password fields are populated, the system also tries to run a bind command to test the manager credentials. Click Save to complete the configuration. Click Reload to discard unsaved changes and return to the server settings.
RADIUS authentication—You can specify that users are to be authenticated using a RADIUS server. The NorthStar server sends authentication requests to the RADIUS server; the RADIUS server authenticates or rejects the requests. The settings associated with this option must coincide with the RADIUS server configuration.
Figure 2 shows the authentication settings for RADIUS authentication. The fields are described in Table 2.
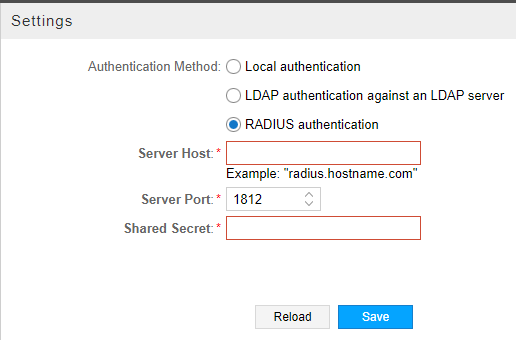
Field |
Description |
|---|---|
Server Host |
Required. IP address of the RADIUS server. |
Server Port |
Required. Port number between 1 and 65000. The default port for RADIUS is 1812. |
Shared Secret |
Required. String known only to the RADIUS server and RADIUS client. Used to secure communication. |
Group membership is not defined in RADIUS. New RADIUS-authenticated users are automatically placed in a default group called “radius”, which is created with view-only permissions if it does not already exist. The admin user can modify the privileges of the radius group and can move radius group members into other groups.
