Customizing the Severity Level
The Integrity Check Profile table is used by the user to modify the severity level of each type of integrity check error, as well as to define whether or not to include a particular check in the generated Integrity Checks report. Select Tools > Options > Integrity Checks... to open the following window.
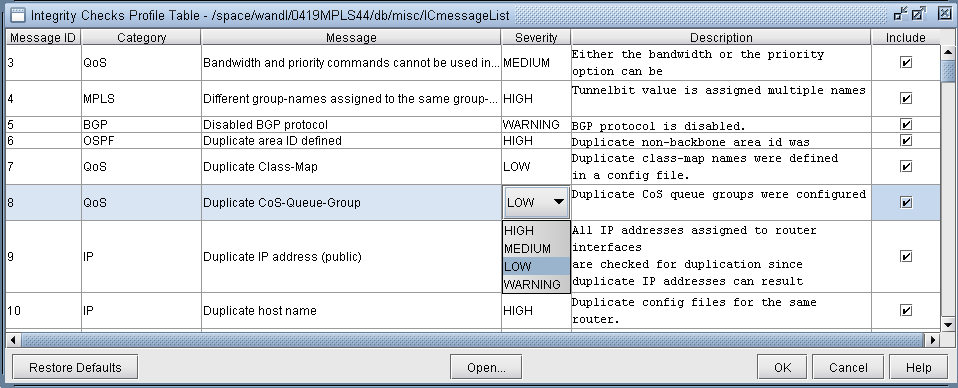
Click the cell in the Severity column that you wish to modify. A drop-down box will appear with choices for HIGH, MEDIUM, LOW, and WARNING. The Include column has a check box for each integrity check. Keep the box checked for integrity checks that you wish to remain in the report. Uncheck the boxes for those integrity checks that you do not wish to be included in the integrity checks report. When you are finished making changes, click OK and chose a file to save the profile to. The Restore Defaults button restores the table to the default settings.
