Advanced Threat Prevention Appliance Datasheet
Download DatasheetProduct Overview
Advanced Threat Prevention Appliances are virtual on-premises devices that combine advanced threat detection with consolidated security analytics to protect organizations from known and unknown cyberattacks while improving the productivity of security operations teams.
Working with Juniper Networks SRX Series Firewalls, ATP Appliances detect Web, e-mail, and lateral traffic threats, blocking those threats if the firewall is deployed inline.
ATP Appliances can also ingest logs from existing security devices and apply contextual analysis to provide a consolidated view of the threat landscape.

Product Description
Juniper Networks® Advanced Threat Prevention Appliances address the need for an on-premises virtual threat detection and mitigation solution.
Based on scalability requirements, two versions of the virtual platform are available. The virtual version of the ATP Appliances, running on either VMware vSphere or ESXi, can be deployed with either 8 or 24 virtual CPU cores to process up to 116,000 files per day.
Juniper ATP Appliances collect web, e-mail, and lateral traffic using the Juniper Networks SRX Series Firewalls or its built-in collectors, making it an ideal fit for organizations employing multiple firewall solutions. Collected data is sent to an on-premises ATP Appliance for further processing by the ATP Appliance core, which identifies known and unknown threats and provides comprehensive analytics detailing the threat’s progression within the environment by mapping detections to the attack kill chain. Once a threat is detected, the ATP Appliance sends firewall policy updates to the SRX Series firewalls. The ATP Appliance can be configured to update policies on third-party firewalls from vendors such as Palo Alto Networks, Fortinet, and Cisco. JATP appliances work with Juniper Networks EX Series Ethernet Switches, Juniper Networks QFX Series switches, or other third-party switches. It isolates threats and leverages one-touch mitigation to quarantine compromised hosts, limiting lateral spread.
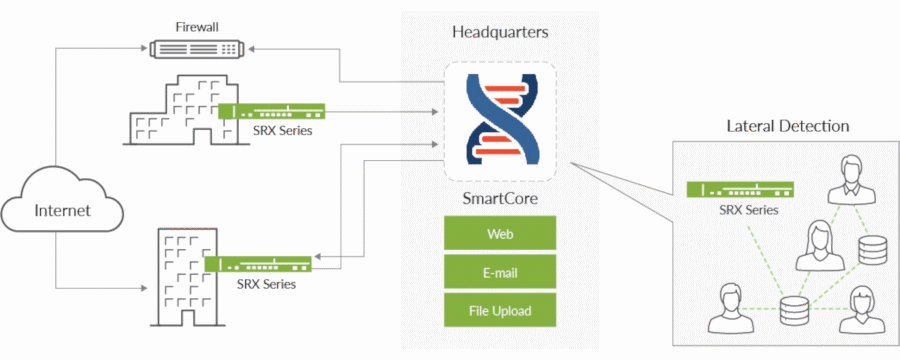
Figure 1: Juniper Networks ATP Appliance architecture
Architecture and Key Components
The on-premises ATP solution can use SRX Series firewalls as collectors for inline detection and blocking. JATP Appliances can also use their built-in collectors with third-party firewalls. For MSSP environments, the ATP Appliance can be deployed as a separate collector and core supporting multi-tenancy. A collector is deployed at each customer location, and a core or cluster of cores analyzes all traffic. The Juniper ATP Appliance can run in private mode for air-gapped environments, providing malware detection, mitigation, and even correlation when Internet access is unavailable.
Files and related executables collected across the network are delivered to the SmartCore detection and analytics engine on a virtualized ATP Appliance for further analysis. The SRX Series firewalls can block threats detected by the SmartCore engine.
ATP Appliances can also ingest logs from other identity and security solutions such as Active Directory, endpoint antivirus, firewalls, Secure Web Gateways (SWGs), intrusion detection systems, and endpoint detection and response tools. The logs can be ingested either directly from third-party devices or forwarded by existing security information and event management (SIEM)/syslog servers.
| Feature | Description | Benefits |
| Traffic Inspection | Protects multiple vectors, including Web, e-mail, and lateral spread | Provides a broad range of protocol support to cover the most common methods for malware and ransomware distribution |
| Inline Threat Mitigation | Offers inline blocking when an SRX Series firewall is deployed | Offers the ability to block known and unknown threats |
| Attack Analytics | Provides a real-time and historical view of the threat landscape across the network, including from third-party security solutions | Gives security operations employees visibility into correlated threat activity occurring inside their network, allowing them to identify high-priority threats quickly, understand how to respond, and/or quarantine to remediate the outbreak |
| Third-Party Interoperability | Includes comprehensive APIs and a custom log ingestion framework that easily integrate with third-party security devices, enabling threat log collection and aggregation from any security products already deployed | Ensures easy integration with third-party security devices using APIs and supports threat log collection and aggregation from any existing security products |
| Centralized Management | Includes Manager of Central Managers (MCM) functionality | Provides comprehensive, centralized, single-pane-of-glass management of clustered core appliances in large deployments requiring multiple cores |
| Flexible Deployment | Supports virtual on-premises deployments | Provides flexible options depending on your scalability and performance requirements for threat processing and analytics |
| Distributed Architecture | Leverages collectors that can be deployed at any number of network locations, all feeding into an analytics engine residing at headquarters or in the cloud | Increases threat coverage across your networks, including public and private clouds |
| Clustering | Allows clustering of multiple secondary cores via scalable architecture | Enables a quick increase in threat process capacity if more than a single appliance is required |
| Authentication | Supports access and authentication using SAML and RADIUS | Works with existing authentication solutions |
Product Options
ATP Appliances are available with 8 or 24-core options to best fit the requirements for your network. The virtual appliances can be deployed in distributed mode with SmartCore and Fabric Collector installed on separate appliances.
Malware detection for MacOS is also supported. Customers must provide Mac mini hardware to be deployed as a secondary core. The MacOS sandboxing image is available on the ATP Appliances’ software downloads page.
| Product Name | Virtual Memory/Disk | Collector Performance | E-Mail MTA Receiver | Performance (Objects Detonations)1 |
| 1Numbers based on a traffic mix that approximates real-world performance. Actual numbers may differ based on traffic mix, repeat objects, and other factors unique to user environments. | ||||
| Virtual JATP Appliances solution (8-core CPU) | 32 GB/1.5 TB | 1.5 Gbps | 720,000 | Up to 46,000 objects/day |
| Virtual JATP Appliances solution (24-core CPU) | 96 GB/1.5 TB | 4 Gbps | 2.4 million | Up to 116,000 objects/day |
| Product Name | Hypervisor Support | Versions |
| Virtual JATP Appliances | VMware vSphere, ESXi | vSphere (5.5, 6.0, 6.5), ESXi (5.5.1, 5.5, 7.0) |
Specifications
| Specification | JATP400 | JATP700 |
| Weight | 30.4 lbs (13.79kg) | 42 lbs (19 kg) |
| Dimensions (WxHxD) | 17.2 x 1.7 x 25.6 in (43.7 x 4.3 x 65 cm) | 17.2 x 3.5 x 24.8 in (43.7 x 8.9 x 63 cm) |
| Form Factor | 1 U (rack-mountable) | 2 U (rack-mountable) |
| AC Power Supply | 500 W high efficiency (94%+) AC-DC redundant power; AC input: -100 to -240 V, 50-60 Hz, 11-4.4 amp | 920 W high efficiency (94%+) AC-DC redundant power; AC input: -100 to -240 V, 50-60 Hz, 11-4.4 amp |
| DC Power Supply | 650 W high-efficiency redundant DC-to-DC power supply; DC input: 650 W; -44 to -74 VDC, 20 amp | 850 W/1010 W high-efficiency redundant DC-to-DC power supply; DC input: 850 W; -35 to -42 VDC, 30-25 amp |
| Fans | 1.6 x 1.6 x 2.2 in (4 x 4 x 5.6 cm) 13K-11K RPM counter rotating fan, RoHS/REACH | 1.6 x 1.6 x 2.2 in (4 x 4 x 5.6 cm) 13K-11K RPM counter-rotating fan, RoHS/REACH |
| Operating Temperature | 50° to 104° F (10° to 40° C) | 50° to 104° F (10° to 40° C) |
| Storage Temperature | -40° to 158° F (-40° to 70° C) | -40° to 158° F (-40° to 70° C) |
| Relative Humidity (Operating) | 8 to 90 percent noncondensing | 8 to 90 percent noncondensing |
| Relative Humidity (Storage) | 5 to 95 percent noncondensing | 5 to 95 percent noncondensing |
| Altitude (Operating) | 6500 ft max | 6500 ft max |
| Altitude (Storage) | 35,000 ft max | 35,000 ft max |
| Safety Certifications | CAN/CSA-C22.2 No. 60950-1 Safety of Information Technology Equipment EN 60950-1 UL 60950-1 (2nd Edition) IEC 60950-1: 2005/A2:2013 | CAN/CSA-C22.2 No. 60950-1 Safety of Information Technology Equipment EN 60950-1 UL 60950-1 (2nd Edition) IEC 60950-1: 2005/A2:2013 |
| Emissions Certifications | 47CFR Part 15, (FCC) Class A ICES-003 Class A EN 55022 Class A CISPR 22 Class A EN 55024 CISPR 24 EN 300 386 AS/NZA CISPR22 Class A CNS13438 Class A EN 61000-3-3 VCCI Class A KN22 Class A EN 61000-3-2 BSMI CNS 13438 | 47CFR Part 15, (FCC) Class A ICES-003 Class A EN 55022 Class A CISPR 22 Class A EN 55024 CISPR 24 EN 300 386 AS/NZA CISPR22 Class A CNS13438 Class A EN 61000-3-3 VCCI Class A KN22 Class A EN 61000-3-2 BSMI CNS 13438 |
| NEBS | No | No |
| RoHS | Yes | Yes |
| CPU | Ten cores | 2x10 cores |
| Memory | 32 GB | 128 GB |
| Storage | 8 TB (4 x 2 TB), RAID 6 | 8x900 GB 2.5 in 10K SAS, RAID 6 |
| Traffic Ports | 2xSFP+ 10GbE; 4xRJ-45 GbE | 2xSFP+ 10GbE; 4xRJ-45 GbE |
Ordering Information
Juniper Networks Advanced Threat Prevention Appliances support flexible deployment options. Required components vary based on the deployment model.
- Physical deployments require a physical ATP Appliance solution and an associated software subscription.
- Virtual deployments require a software subscription only.
For information about the virtual ATP Appliance, software licensing, or answers to general ordering questions, please visit our How to Buy page at https://www.juniper.net/us/en/how-to-buy/form.html.
About Juniper Networks
At Juniper Networks, we are dedicated to dramatically simplifying network operations and driving superior experiences for end users. Our solutions deliver industry-leading insight, automation, security and AI to drive real business results. We believe that powering connections will bring us closer together while empowering us all to solve the world’s greatest challenges of well-being, sustainability and equality.
1000627 - 010 - EN MARCH 2023






















