고급 보안 및 Data Center Interconnect 구성
이 예시를 사용하여 축소된 스파인 데이터센터 아키텍처에서 고급 보안 및 DCI를 구성할 수 있습니다.
테넌트 간 트래픽에 대한 고급 보안 구성
SRX 시리즈는 테넌트 간 트래픽에 고급 보안 서비스를 제공할 수 있는 차세대 방화벽입니다. 이 섹션을 사용하여 SRX 섀시 클러스터를 통해 DC1의 JNPR_1와 JNPR_2 간에 테넌트 간 트래픽을 라우팅할 수 있습니다.
요구 사항
EVPN 멀티호밍으로 축소된 스파인을 구성하는 방법에서 구성한 디바이스.
SRX 섀시 클러스터가 이미 구성되어 실행 중이어야 합니다. SRX 섀시 클러스터 활성화에 대한 자세한 내용은 SRX 시리즈 디바이스의 섀시 클러스터링 구성을 참조하십시오.
개요
섀시 클러스터의 SRX 시리즈 방화벽은 단일 디바이스로 작동하여 디바이스, 인터페이스 및 서비스 레벨 이중화를 제공합니다. 이 섹션을 사용하여 섀시 클러스터를 여러 영역으로 분리하고 보안 장치를 통해 올바른 트래픽이 라우팅되도록 라우팅 정책을 구성합니다.
위상수학
그림 1과 같이 두 스파인 스위치는 물리적으로 두 SRX 노드에 모두 연결되어 있습니다.
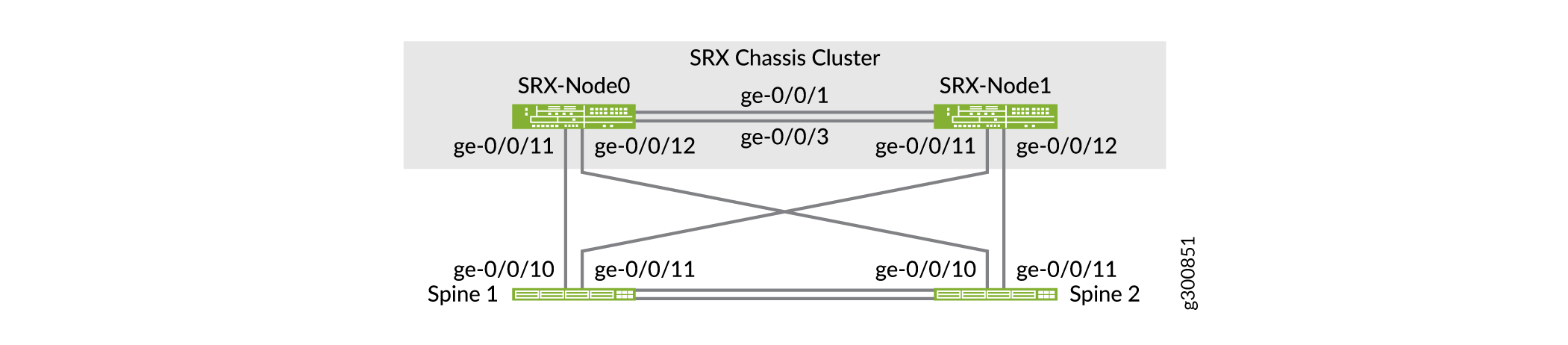 의 물리적 토폴로지
의 물리적 토폴로지
이 예는 SRX345 디바이스를 기준으로 합니다. HA 클러스터에 배치되면 노드 1의 인터페이스는 FPC 슬롯 5와 연결됩니다. 즉, 노드 1에 표시된 ge-0/0/11 인터페이스는 클러스터가 형성되면 실제로 ge-5-0/11로 구성됩니다. HA 클러스터의 노드 1에 대한 FPC 번호는 SRX 모델 유형에 따라 다를 수 있습니다.
Reth1은 SRX 클러스터의 논리적 인터페이스입니다. SRX 클러스터의 노드 중 하나에서 활성화됩니다. SRX 디바이스와 스파인 스위치 간의 기본 노드 또는 인터커넥트 링크가 실패하면 Reth1은 보조 노드로 페일오버됩니다. 그림 2 에는 SRX 디바이스와 스파인 스위치 간의 논리적 인터페이스가 나와 있습니다.
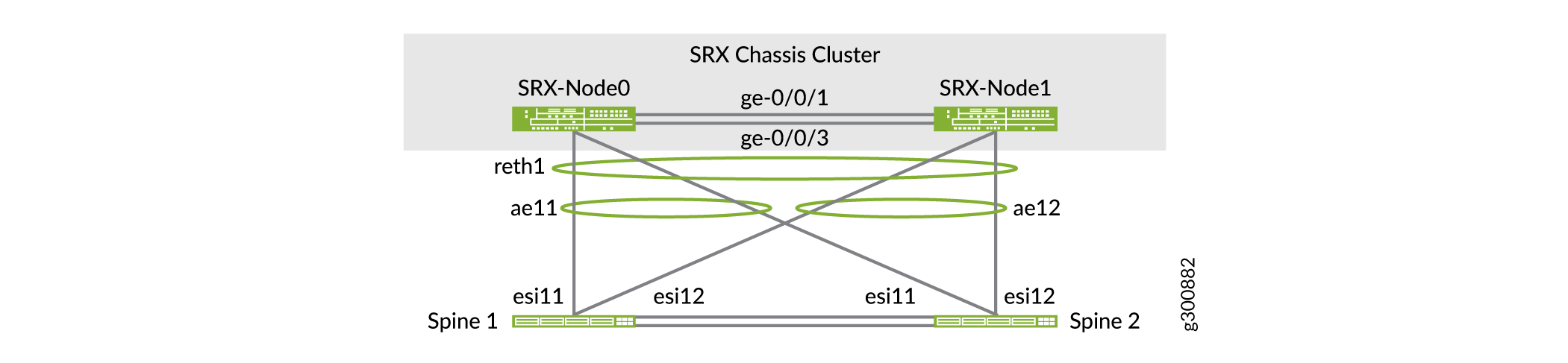 의 오버레이 토폴로지
의 오버레이 토폴로지
각 스파인 스위치는 그림 3과 같이 각 라우팅 인스턴스 또는 테넌트에서 SRX 클러스터와 별도의 EBGP 피어링을 설정합니다. 예를 들어, 스파인 1은 SRX 클러스터와 두 개의 피어링을 가지며, 각 라우팅 인스턴스에 하나씩 JNPR_1와 JNPR_2. Reth1.991은 스파인 스위치의 JNPR_1 라우팅 인스턴스와 피어링되며 JNPR_1 보안 영역에 속합니다. Reth1.992는 스파인 스위치의 JNPR_2 라우팅 인스턴스와 피어링하며 JNPR_2 보안 영역에 속합니다.
SRX 시리즈 방화벽은 모든 접두사(예: 192.168.0.0/16)를 포함하는 요약 경로를 보급합니다. 스파인 스위치는 각 라우팅 인스턴스에서 특정 서브넷을 보급합니다.
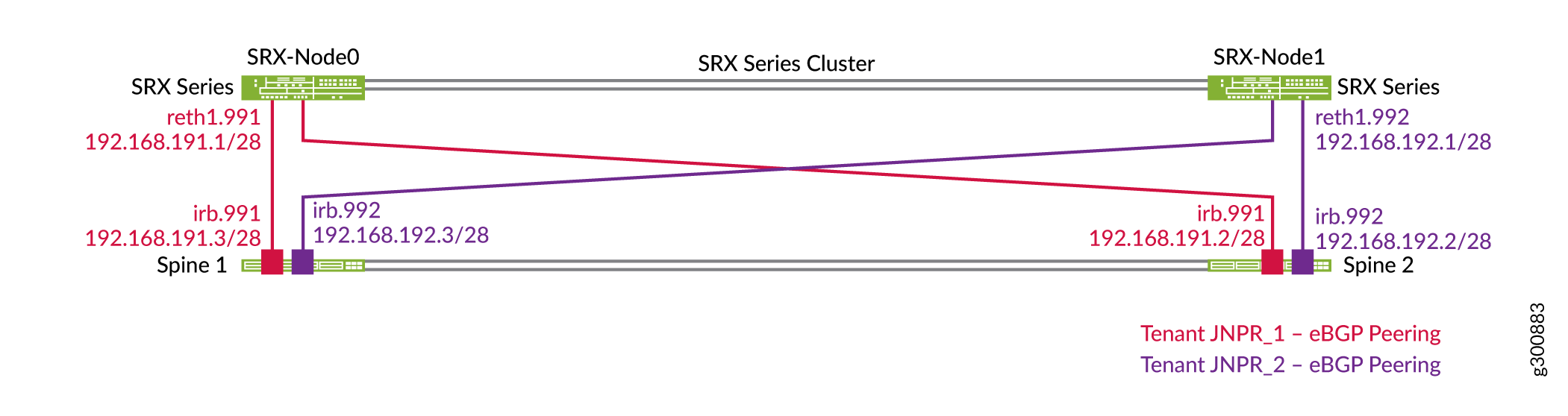 을 사용하는 SRX 클러스터의 토폴로지
을 사용하는 SRX 클러스터의 토폴로지
인터페이스 구성
SRX 디바이스 구성
단계별 절차
SRX 디바이스의 논리적 인터페이스에 대한 그룹을 구성합니다.
set chassis cluster reth-count 3 set chassis cluster redundancy-group 0 node 0 priority 100 set chassis cluster redundancy-group 0 node 1 priority 1 set chassis cluster redundancy-group 1 node 0 priority 200 set chassis cluster redundancy-group 1 node 1 priority 100 set chassis cluster redundancy-group 1 preempt set chassis cluster redundancy-group 1 interface-monitor ge-0/0/11 weight 255 set chassis cluster redundancy-group 1 interface-monitor ge-0/0/12 weight 255 set chassis cluster redundancy-group 1 interface-monitor ge-5/0/11 weight 255 set chassis cluster redundancy-group 1 interface-monitor ge-5/0/12 weight 255
논리적 인터페이스를 구성합니다. RETH1은 SRX 클러스터에서 태그가 지정된 레이어 3 인터페이스입니다. Reth1.991은 스파인 스위치의 JNPR_1 라우팅 인스턴스와 피어링됩니다. Reth1.992는 스파인 스위치의 JNPR_2 라우팅 인스턴스와 피어링됩니다.
set interfaces reth1 vlan-tagging set interfaces reth1 redundant-ether-options redundancy-group 1 set interfaces reth1 redundant-ether-options lacp active set interfaces reth1 redundant-ether-options lacp periodic fast set interfaces reth1 unit 991 description "Spine Interconnect for JNPR_1" set interfaces reth1 unit 991 vlan-id 991 set interfaces reth1 unit 991 family inet address 192.168.191.1/28 set interfaces reth1 unit 992 description "Spine Interconnect for JNPR_2" set interfaces reth1 unit 992 vlan-id 992 set interfaces reth1 unit 992 family inet address 192.168.192.1/28 set interfaces ge-0/0/11 description "To Spine1 | ge-0/0/10" set interfaces ge-0/0/11 gigether-options no-auto-negotiation set interfaces ge-0/0/11 gigether-options redundant-parent reth1 set interfaces ge-5/0/11 description "To Spine1 | ge-0/0/11" set interfaces ge-5/0/11 gigether-options no-auto-negotiation set interfaces ge-5/0/11 gigether-options redundant-parent reth1 set interfaces ge-0/0/12 description "To Spine2 | ge-0/0/10" set interfaces ge-0/0/12 gigether-options no-auto-negotiation set interfaces ge-0/0/12 gigether-options redundant-parent reth1 set interfaces ge-5/0/12 description "To Spine2 | ge-0/0/11" set interfaces ge-5/0/12 gigether-options no-auto-negotiation set interfaces ge-5/0/12 gigether-options redundant-parent reth1
논리적 인터페이스를 별도의 보안 영역에 배치합니다. Reth1.991은 JNPR_1 보안 영역에 속하고 Reth1.992는 JNPR_2 보안 영역에 속합니다.
set security zones security-zone JNPR_1-Zone host-inbound-traffic system-services ping set security zones security-zone JNPR_1-Zone host-inbound-traffic protocols bgp set security zones security-zone JNPR_1-Zone interfaces reth1.991 set security zones security-zone JNPR_2-Zone host-inbound-traffic system-services ping set security zones security-zone JNPR_2-Zone host-inbound-traffic protocols bgp set security zones security-zone JNPR_2-Zone interfaces reth1.992
섀시 클러스터의 상태를 확인합니다.
user@srx1> show chassis cluster status Monitor Failure codes: CS Cold Sync monitoring FL Fabric Connection monitoring GR GRES monitoring HW Hardware monitoring IF Interface monitoring IP IP monitoring LB Loopback monitoring MB Mbuf monitoring NH Nexthop monitoring NP NPC monitoring SP SPU monitoring SM Schedule monitoring CF Config Sync monitoring RE Relinquish monitoring Cluster ID: 1 Node Priority Status Preempt Manual Monitor-failures Redundancy group: 0 , Failover count: 1 node0 100 primary no no None node1 1 secondary no no None Redundancy group: 1 , Failover count: 5 node0 200 primary yes no None node1 100 secondary yes no None
스파인 1 구성
단계별 절차
스파인 1에서 SRX 시리즈 방화벽 상호 연결 인터페이스를 구성합니다.
set interfaces ge-0/0/10 ether-options 802.3ad ae11 set interfaces ge-0/0/11 ether-options 802.3ad ae12 set interfaces ae11 description "to SRX Cluster | SRX-0" set interfaces ae11 mtu 9216 set interfaces ae11 esi 00:00:00:00:00:00:00:00:01:11 set interfaces ae11 esi all-active set interfaces ae11 aggregated-ether-options lacp active set interfaces ae11 aggregated-ether-options lacp periodic fast set interfaces ae11 aggregated-ether-options lacp system-id 00:00:00:00:01:11 set interfaces ae11 unit 0 family ethernet-switching interface-mode trunk set interfaces ae11 unit 0 family ethernet-switching vlan members VLAN-991 set interfaces ae12 description "to SRX Cluster | SRX-1" set interfaces ae12 mtu 9216 set interfaces ae12 esi 00:00:00:00:00:00:00:00:01:12 set interfaces ae12 esi all-active set interfaces ae12 aggregated-ether-options lacp active set interfaces ae12 aggregated-ether-options lacp periodic fast set interfaces ae11 aggregated-ether-options lacp system-id 00:00:00:00:01:12 set interfaces ae12 unit 0 family ethernet-switching interface-mode trunk set interfaces ae12 unit 0 family ethernet-switching vlan members VLAN-992
IRB 인터페이스를 구성합니다.
set interfaces irb unit 991 description "Tenant1 SRX Interconnect" set interfaces irb unit 991 family inet address 192.168.191.3/28 set routing-instances JNPR_1_VRF interface irb.991 set interfaces irb unit 992 description "Tenant2 SRX Interconnect" set interfaces irb unit 992 family inet address 192.168.192.3/28 set routing-instances JNPR_2_VRF interface irb.992
VLAN을 구성합니다.
set vlans VLAN-991 vlan-id 991 set vlans VLAN-991 l3-interface irb.991 set vlans VLAN-991 vxlan vni 5991 set vlans VLAN-992 vlan-id 992 set vlans VLAN-992 l3-interface irb.992 set vlans VLAN-992 vxlan vni 5992
VNI를 EVPN MP-BGP 도메인의 일부로 구성합니다.
set protocols evpn extended-vni-list 5991 set protocols evpn extended-vni-list 5992
스파인 2 구성
단계별 절차
스파인 2에서 SRX 시리즈 방화벽 상호 연결 인터페이스를 구성합니다.
set interfaces ge-0/0/10 ether-options 802.3ad ae11 set interfaces ge-0/0/11 ether-options 802.3ad ae12 set interfaces ae11 description "to SRX Cluster | SRX-0" set interfaces ae11 mtu 9216 set interfaces ae11 esi 00:00:00:00:00:00:00:00:01:11 set interfaces ae11 esi all-active set interfaces ae12 aggregated-ether-options lacp active set interfaces ae12 aggregated-ether-options lacp periodic fast set interfaces ae11 aggregated-ether-options lacp system-id 00:00:00:00:01:11 set interfaces ae11 unit 0 family ethernet-switching interface-mode trunk set interfaces ae11 unit 0 family ethernet-switching vlan members VLAN-991 set interfaces ae12 description "to SRX Cluster | SRX-1" set interfaces ae12 mtu 9216 set interfaces ae12 esi 00:00:00:00:00:00:00:00:01:12 set interfaces ae12 esi all-active set interfaces ae12 aggregated-ether-options lacp active set interfaces ae12 aggregated-ether-options lacp periodic fast set interfaces ae11 aggregated-ether-options lacp system-id 00:00:00:00:01:12 set interfaces ae12 unit 0 family ethernet-switching interface-mode trunk set interfaces ae12 unit 0 family ethernet-switching vlan members VLAN-992
IRB 인터페이스를 구성합니다.
set interfaces irb unit 991 description "Tenant1 SRX Interconnect" set interfaces irb unit 991 family inet address 192.168.191.2/28 set routing-instances JNPR_1_VRF interface irb.991 set interfaces irb unit 992 description "Tenant2 SRX Interconnect" set interfaces irb unit 992 family inet address 192.168.192.2/28 set routing-instances JNPR_2_VRF interface irb.992
VLAN을 구성합니다.
set vlans VLAN-991 vlan-id 991 set vlans VLAN-991 l3-interface irb.991 set vlans VLAN-991 vxlan vni 5991 set vlans VLAN-992 vlan-id 992 set vlans VLAN-992 l3-interface irb.992 set vlans VLAN-992 vxlan vni 5992
VNI를 EVPN MP-BGP 도메인의 일부로 구성합니다.
set protocols evpn extended-vni-list 5991 set protocols evpn extended-vni-list 5992
EBGP를 구성합니다
SRX 디바이스 구성
단계별 절차
EBGP 상호 연결을 구성합니다.
set protocols bgp group INTERCONNECT type external set protocols bgp group INTERCONNECT import INTERCONNECT-IMPORT set protocols bgp group INTERCONNECT family inet unicast set protocols bgp group INTERCONNECT authentication-key "$ABC123" set protocols bgp group INTERCONNECT export INTERCONNECT-EXPORT set protocols bgp group INTERCONNECT local-as 65200 set protocols bgp group INTERCONNECT multipath multiple-as set protocols bgp group INTERCONNECT bfd-liveness-detection minimum-interval 1000 set protocols bgp group INTERCONNECT bfd-liveness-detection multiplier 3 set protocols bgp group INTERCONNECT neighbor 192.168.191.2 peer-as 65112 set protocols bgp group INTERCONNECT neighbor 192.168.191.3 peer-as 65113 set protocols bgp group INTERCONNECT neighbor 192.168.192.2 peer-as 65212 set protocols bgp group INTERCONNECT neighbor 192.168.192.3 peer-as 65213
라우팅 옵션을 구성합니다.
set routing-options static route 192.168.0.0/16 discard
정책 옵션을 구성합니다.
set policy-options policy-statement INTERCONNECT-EXPORT term Tenant_Aggregate from protocol static set policy-options policy-statement INTERCONNECT-EXPORT term Tenant_Aggregate from route-filter 192.168.0.0/16 exact set policy-options policy-statement INTERCONNECT-EXPORT term Tenant_Aggregate then accept set policy-options policy-statement INTERCONNECT-EXPORT term Advertise_Loopback from protocol direct set policy-options policy-statement INTERCONNECT-EXPORT term Advertise_Loopback from route-filter 192.168.255.1/32 exact set policy-options policy-statement INTERCONNECT-EXPORT term Advertise_Loopback then accept set policy-options policy-statement INTERCONNECT-EXPORT term Reject_All then reject set policy-options policy-statement INTERCONNECT-IMPORT term Tenant_Routes from route-filter 192.168.0.0/16 longer set policy-options policy-statement INTERCONNECT-IMPORT term Tenant_Routes then accept set policy-options policy-statement INTERCONNECT-IMPORT term DEFAULT then reject
스파인 1 구성
단계별 절차
JNPR_1 라우팅 인스턴스에서 EBGP 피어링을 구성합니다.
set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT type external set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT import Interconnect_JNPR_1-IMPORT set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT family inet unicast set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT authentication-key "$ABC123" set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT export Interconnect_JNPR_1-EXPORT set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT local-as 65113 set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT multipath multiple-as set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT bfd-liveness-detection minimum-interval 1000 set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT bfd-liveness-detection multiplier 3 set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT neighbor 192.168.191.1 peer-as 65200
JNPR_2 라우팅 인스턴스에서 EBGP 피어링을 구성합니다.
set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT type external set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT import Interconnect_JNPR_2-IMPORT set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT family inet unicast set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT authentication-key "$ABC123" set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT export Interconnect_JNPR_2-EXPORT set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT local-as 65213 set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT multipath multiple-as set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT bfd-liveness-detection minimum-interval 1000 set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT bfd-liveness-detection multiplier 3 set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT neighbor 192.168.192.1 peer-as 65200
SRX 디바이스와 상호 연결을 위한 가져오기 및 내보내기 정책을 구성합니다.
set policy-options policy-statement Interconnect_JNPR_1-EXPORT term Tenant_Routes from route-filter 192.168.0.0/16 orlonger set policy-options policy-statement Interconnect_JNPR_1-EXPORT term Tenant_Routes then accept set policy-options policy-statement Interconnect_JNPR_1-EXPORT term DEFAULT then reject set policy-options policy-statement Interconnect_JNPR_1-IMPORT term Tenant_Routes from route-filter 192.168.0.0/16 orlonger set policy-options policy-statement Interconnect_JNPR_1-IMPORT term Tenant_Routes then accept set policy-options policy-statement Interconnect_JNPR_1-IMPORT term DEFAULT then reject set policy-options policy-statement Interconnect_JNPR_2-EXPORT term Tenant_Routes from route-filter 192.168.0.0/16 orlonger set policy-options policy-statement Interconnect_JNPR_2-EXPORT term Tenant_Routes then accept set policy-options policy-statement Interconnect_JNPR_2-EXPORT term DEFAULT then reject set policy-options policy-statement Interconnect_JNPR_2-IMPORT term Tenant_Routes from route-filter 192.168.0.0/16 orlonger set policy-options policy-statement Interconnect_JNPR_2-IMPORT term Tenant_Routes then accept set policy-options policy-statement Interconnect_JNPR_2-IMPORT term DEFAULT then reject
스파인 2 구성
단계별 절차
-
JNPR_1 라우팅 인스턴스에서 EBGP 피어링을 구성합니다.
set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT type external set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT import Interconnect_JNPR_1-IMPORT set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT family inet unicast set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT authentication-key "$ABC123" set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT export Interconnect_JNPR_1-EXPORT set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT local-as 65112 set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT multipath multiple-as set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT bfd-liveness-detection minimum-interval 1000 set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT bfd-liveness-detection multiplier 3 set routing-instances JNPR_1_VRF protocols bgp group INTERCONNECT neighbor 192.168.191.1 peer-as 65200
-
JNPR_2 라우팅 인스턴스에서 EBGP 피어링을 구성합니다.
set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT type external set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT import Interconnect_JNPR_2-IMPORT set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT family inet unicast set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT authentication-key "$ABC123" set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT export Interconnect_JNPR_2-EXPORT set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT local-as 65212 set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT multipath multiple-as set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT bfd-liveness-detection minimum-interval 1000 set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT bfd-liveness-detection multiplier 3 set routing-instances JNPR_2_VRF protocols bgp group INTERCONNECT neighbor 192.168.192.1 peer-as 65200
-
SRX 디바이스와 상호 연결을 위한 가져오기 및 내보내기 정책을 구성합니다.
set policy-options policy-statement Interconnect_JNPR_1-EXPORT term Tenant_Routes from route-filter 192.168.0.0/16 orlonger set policy-options policy-statement Interconnect_JNPR_1-EXPORT term Tenant_Routes then accept set policy-options policy-statement Interconnect_JNPR_1-EXPORT term DEFAULT then reject set policy-options policy-statement Interconnect_JNPR_1-IMPORT term Tenant_Routes from route-filter 192.168.0.0/16 orlonger set policy-options policy-statement Interconnect_JNPR_1-IMPORT term Tenant_Routes then accept set policy-options policy-statement Interconnect_JNPR_1-IMPORT term DEFAULT then reject set policy-options policy-statement Interconnect_JNPR_2-EXPORT term Tenant_Routes from route-filter 192.168.0.0/16 orlonger set policy-options policy-statement Interconnect_JNPR_2-EXPORT term Tenant_Routes then accept set policy-options policy-statement Interconnect_JNPR_2-EXPORT term DEFAULT then reject set policy-options policy-statement Interconnect_JNPR_2-IMPORT term Tenant_Routes from route-filter 192.168.0.0/16 orlonger set policy-options policy-statement Interconnect_JNPR_2-IMPORT term Tenant_Routes then accept set policy-options policy-statement Interconnect_JNPR_2-IMPORT term DEFAULT then reject
SRX 시리즈 방화벽 보안 정책 구성
단계별 절차
JNPR_1용 영역 1에서 보안 정책을 구성합니다.
set security policies from-zone JNPR_1-Zone to-zone JNPR_2-Zone policy Allow_All match source-address any set security policies from-zone JNPR_1-Zone to-zone JNPR_2-Zone policy Allow_All match destination-address any set security policies from-zone JNPR_1-Zone to-zone JNPR_2-Zone policy Allow_All match application any set security policies from-zone JNPR_1-Zone to-zone JNPR_2-Zone policy Allow_All then permit
JNPR_2용 영역 1에서 보안 정책을 구성합니다.
set security policies from-zone JNPR_2-Zone to-zone JNPR_1-Zone policy Allow_All match source-address any set security policies from-zone JNPR_2-Zone to-zone JNPR_1-Zone policy Allow_All match destination-address any set security policies from-zone JNPR_2-Zone to-zone JNPR_1-Zone policy Allow_All match application any set security policies from-zone JNPR_2-Zone to-zone JNPR_1-Zone policy Allow_All then permit
SRX 섀시 클러스터에서 BGP 확인
단계별 절차
스파인 스위치와의 모든 BGP 피어링 세션이 설정되었는지 확인합니다.
user@srx> show bgp summary Groups: 1 Peers: 4 Down peers: 0 Table Tot Paths Act Paths Suppressed History Damp State Pending inet.0 26 14 0 0 0 0 Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped... 192.168.191.2 65112 113 106 0 73 47:34 Establ inet.0: 4/7/7/0 192.168.191.3 65113 110 107 0 41 47:35 Establ inet.0: 4/7/7/0 192.168.192.2 65212 111 106 0 71 47:35 Establ inet.0: 3/6/6/0 192.168.192.3 65213 109 106 0 34 47:35 Establ inet.0: 3/6/6/0SRX 시리즈 방화벽이 JNPR_1 테넌트로부터 BGP 경로를 수신했는지 확인합니다.
user@srx> show route receive-protocol bgp 192.168.191.2 inet.0: 18 destinations, 35 routes (18 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path 192.168.191.0/28 192.168.191.2 65112 I 192.168.191.1/32 192.168.191.2 65112 I 192.168.201.0/24 192.168.191.2 65112 I * 192.168.202.42/32 192.168.191.2 65112 I 192.168.202.0/24 192.168.191.2 65112 I * 192.168.251.12/32 192.168.191.2 65112 I 192.168.251.13/32 192.168.191.2 65112 65100 I
user@srx> show route receive-protocol bgp 192.168.191.3 inet.0: 18 destinations, 35 routes (18 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path 192.168.191.0/28 192.168.191.3 65113 I 192.168.191.1/32 192.168.191.3 65113 I * 192.168.201.0/24 192.168.191.3 65113 I 192.168.202.42/32 192.168.191.3 65113 I * 192.168.202.0/24 192.168.191.3 65113 I 192.168.251.12/32 192.168.191.3 65113 65100 I * 192.168.251.13/32 192.168.191.3 65113 I
SRX 시리즈 방화벽이 JNPR_2 테넌트에서 BGP 경로를 수신했는지 확인합니다.
user@srx> show route receive-protocol bgp 192.168.192.2 inet.0: 18 destinations, 35 routes (18 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path 192.168.192.0/28 192.168.192.2 65212 I 192.168.192.1/32 192.168.192.2 65212 I 192.168.211.0/24 192.168.192.2 65212 I 192.168.212.0/24 192.168.192.2 65212 I * 192.168.252.12/32 192.168.192.2 65212 I 192.168.252.13/32 192.168.192.2 65212 65100 I
user@srx> show route receive-protocol bgp 192.168.192.3 inet.0: 18 destinations, 35 routes (18 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path 192.168.192.0/28 192.168.192.3 65213 I 192.168.192.1/32 192.168.192.3 65213 I * 192.168.211.0/24 192.168.192.3 65213 I * 192.168.212.0/24 192.168.192.3 65213 I 192.168.252.12/32 192.168.192.3 65213 65100 I * 192.168.252.13/32 192.168.192.3 65213 I
SRX 섀시 클러스터가 스파인 디바이스에 요약 경로를 보급하는지 확인합니다.
user@srx> show route advertising-protocol bgp 192.168.191.2 inet.0: 18 destinations, 35 routes (18 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 192.168.0.0/16 Self I * 192.168.255.1/32 Self I
user@srx> show route advertising-protocol bgp 192.168.191.3 inet.0: 18 destinations, 35 routes (18 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 192.168.0.0/16 Self I * 192.168.255.1/32 Self I
user@srx> show route advertising-protocol bgp 192.168.192.2 inet.0: 18 destinations, 35 routes (18 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 192.168.0.0/16 Self I * 192.168.255.1/32 Self I
user@srx> show route advertising-protocol bgp 192.168.192.3 inet.0: 18 destinations, 35 routes (18 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 192.168.0.0/16 Self I * 192.168.255.1/32 Self I
SRX 섀시 클러스터를 통해 테넌트 간 트래픽을 확인합니다.
이 예에서 Endpoint12는 VLAN 212 및 테넌트 JNPR_2의 일부입니다. Endpoint12는 그림 4와 같이 VLAN 201 및 테넌트 JNPR_1의 일부인 Endpoint2를 ping합니다. 테넌트 간 트래픽이므로 이 트래픽은 SRX 섀시 클러스터의 활성 멤버를 통과합니다. SRX-Node0은 SRX 섀시 클러스터의 액티브 멤버이고 SRX-Node1은 패시브 멤버입니다.
그림 4: SRX 클러스터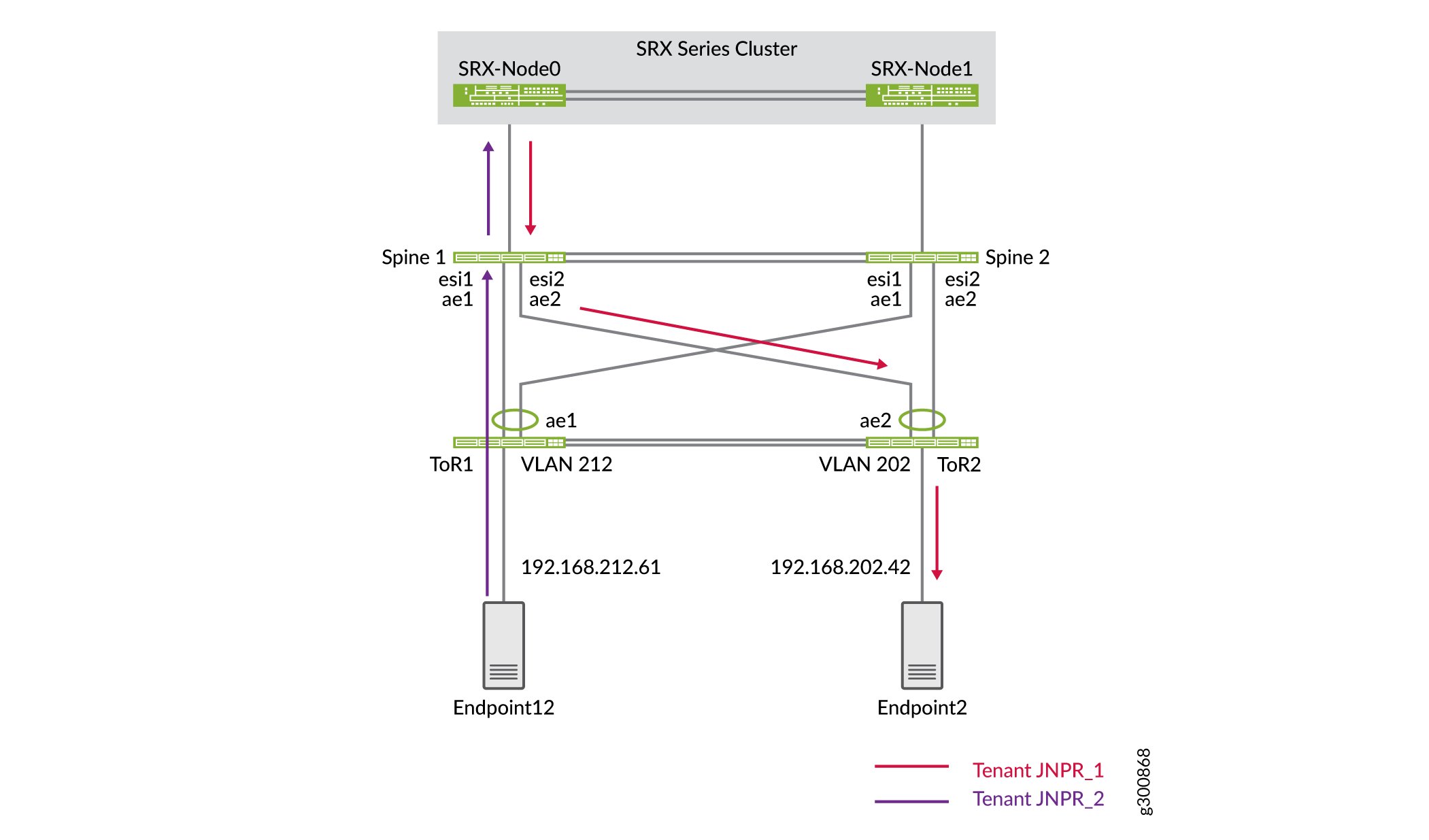 를 통한 테넌트 간 트래픽
를 통한 테넌트 간 트래픽
SRX 시리즈 방화벽의 플로우 테이블에 SRX 섀시 클러스터를 통과하는 이 트래픽이 표시되는지 확인합니다.
user@srx> show security flow session destination-prefix 192.168.202.42 node0: -------------------------------------------------------------------------- Session ID: 15548, Policy name: Allow_All/7, State: Active, Timeout: 2, Valid In: 192.168.212.61/623 --> 192.168.202.42/8204;icmp, Conn Tag: 0x0, If: reth1.992, Pkts: 1, Bytes: 84, Out: 192.168.202.42/8204 --> 192.168.212.61/623;icmp, Conn Tag: 0x0, If: reth1.991, Pkts: 1, Bytes: 84, Session ID: 15551, Policy name: Allow_All/7, State: Active, Timeout: 2, Valid In: 192.168.212.61/624 --> 192.168.202.42/8204;icmp, Conn Tag: 0x0, If: reth1.992, Pkts: 1, Bytes: 84, Out: 192.168.202.42/8204 --> 192.168.212.61/624;icmp, Conn Tag: 0x0, If: reth1.991, Pkts: 1, Bytes: 84, Session ID: 15555, Policy name: Allow_All/7, State: Active, Timeout: 4, Valid In: 192.168.212.61/625 --> 192.168.202.42/8204;icmp, Conn Tag: 0x0, If: reth1.992, Pkts: 1, Bytes: 84, Out: 192.168.202.42/8204 --> 192.168.212.61/625;icmp, Conn Tag: 0x0, If: reth1.991, Pkts: 1, Bytes: 84, Total sessions: 3
데이터센터에 대한 고급 보안을 구성하고 테넌트 간 트래픽이 SRX 섀시 클러스터를 통해 라우팅됨을 확인했습니다.
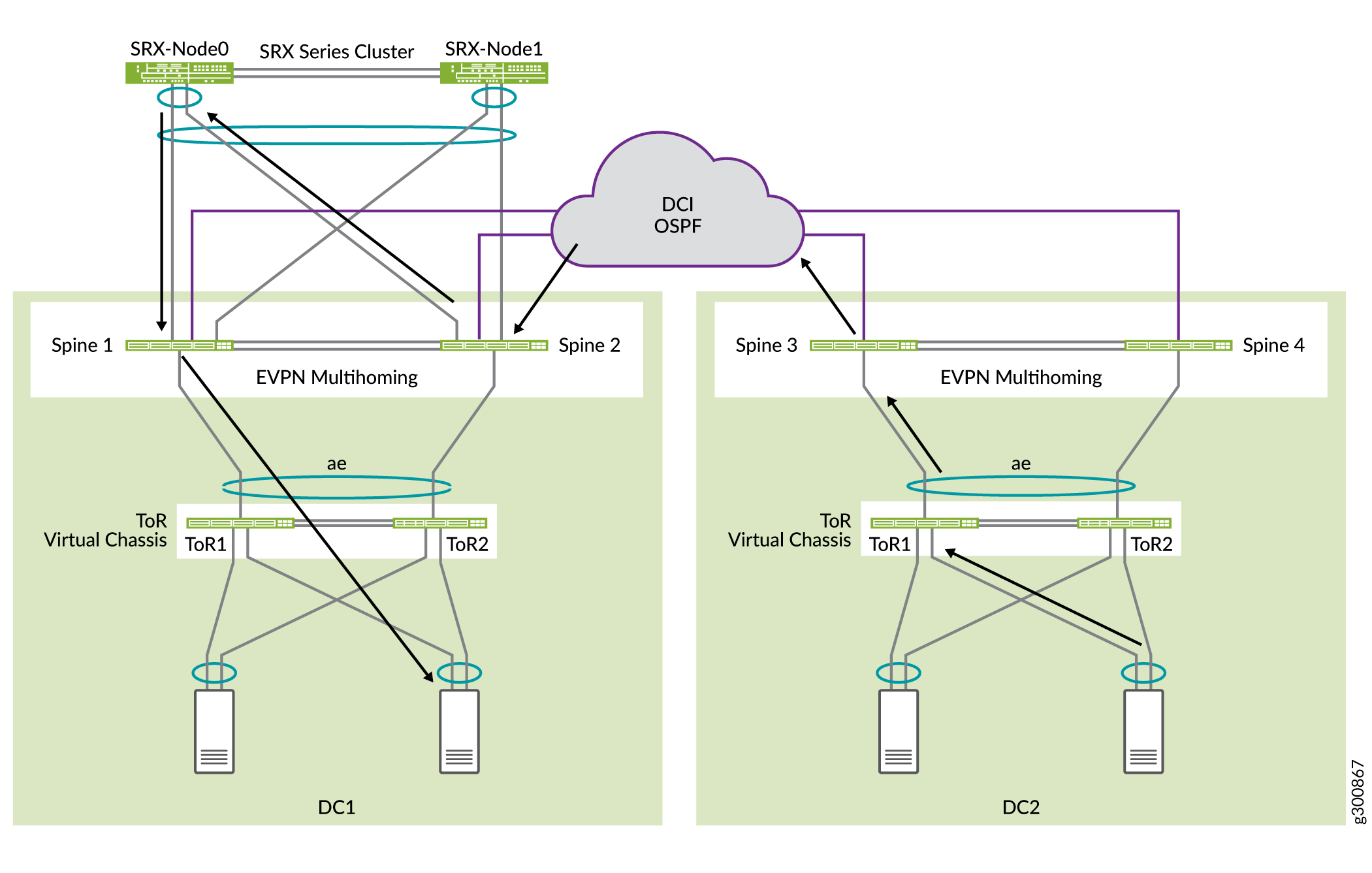
Data Center Interconnect(DCI) 구성
요구 사항
EVPN 멀티호밍으로 축소된 스파인을 구성하고 테넌트 간 트래픽에 대한 고급 보안을 구성하는 방법에서 구성한 디바이스입니다.
개요
두 데이터센터에 대해 축소된 스파인 아키텍처를 구성하고 DC1에 고급 보안을 추가했으므로 이제 DCI(Data Center Interconnect)를 사용하여 DC1과 DC2를 연결할 차례입니다.
위상수학
이 예에서는 데이터센터 간에 레이어 2를 확장할 필요가 없습니다. 데이터센터 간 통신은 그림 5와 같이 DC1의 SRX 섀시 클러스터를 통해 라우팅됩니다. 스파인 스위치는 각각 WAN 라우팅 인스턴스를 가지며 데이터센터 간에 WAN에 연결됩니다. 스파인 스위치는 레이어 3 경로를 WAN 라우터로 전달합니다(이 그림에 나와 있지 않음).
SRX 섀시 클러스터는 192.168.0.0/16 서브넷을 보급합니다. DC2 스파인 스위치 스파인 3 및 스파인 4는 두 개의 서브넷 192.168.221.0/24 및 192.168.222.0/24를 보급합니다.
각 SRX 시리즈 방화벽은 JNPR_1, JNPR_2 및 WAN 라우팅 인스턴스에 해당하는 3개의 영역으로 구성됩니다. JNPR_1와 JNPR_2 사이의 모든 테넌트 간 트래픽은 SRX 섀시 클러스터를 통해 라우팅됩니다. DC1과 DC2 사이의 모든 트래픽은 WAN 라우팅 인스턴스를 사용하여 SRX 섀시 클러스터를 통해 라우팅됩니다. 각 SRX 시리즈 방화벽에는 각 라우팅 인스턴스에서 스파인 1 및 스파인 2를 포함하는 개별 EBGP 피어링이 있습니다. 그림 6 에는 DC1의 스파인 스위치와 SRX 섀시 클러스터 간의 EBGP 피어링이 나와 있습니다.
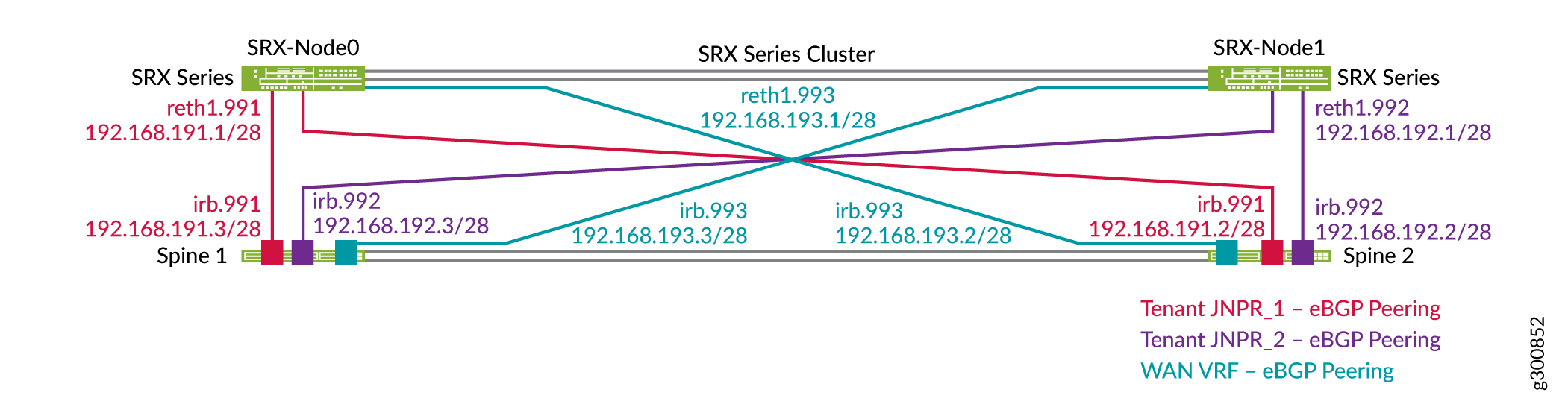
구성
SRX 디바이스 구성
단계별 절차
각 SRX 시리즈 방화벽은 JNPR_1, JNPR_2 및 WAN의 세 가지 라우팅 인스턴스에 해당하는 세 개의 영역으로 분할되어야 합니다. 테넌트 간 트래픽에 대한 고급 보안 구성에서 JNPR_1 영역과 JNPR_2 영역을 이미 생성했습니다.
WAN 인터커넥트를 위해 Reth1에 새 하위 인터페이스를 추가합니다.
set interfaces reth1 unit 993 description "DC1 Spine Interconnect for WAN VRF" set interfaces reth1 unit 993 vlan-id 993 set interfaces reth1 unit 993 family inet address 192.168.193.1/28
WAN 보안 영역을 구성합니다.
set security zones security-zone WAN-Zone host-inbound-traffic system-services ping set security zones security-zone WAN-Zone host-inbound-traffic protocols bgp set security zones security-zone WAN-Zone interfaces reth1.993
WAN 보안 영역용 EBGP를 구성합니다.
set protocols bgp group INTERCONNECT neighbor 192.168.193.2 peer-as 65312 set protocols bgp group INTERCONNECT neighbor 192.168.193.3 peer-as 65313
보안 정책을 구성합니다. 단순화를 위해 이 예제의 보안 정책은 개방형입니다. 설치 시 필요에 따라 보안 정책을 수정합니다.
set security address-book global address 192.168.221.0/24 192.168.221.0/24 set security address-book global address 192.168.222.0/24 192.168.222.0/24
set security policies from-zone WAN-Zone to-zone JNPR_1-Zone policy ALLOW_ALL match source-address 192.168.221.0/24 set security policies from-zone WAN-Zone to-zone JNPR_1-Zone policy ALLOW_ALL match source-address 192.168.222.0/24 set security policies from-zone WAN-Zone to-zone JNPR_1-Zone policy ALLOW_ALL match destination-address any set security policies from-zone WAN-Zone to-zone JNPR_1-Zone policy ALLOW_ALL match application any set security policies from-zone WAN-Zone to-zone JNPR_1-Zone policy ALLOW_ALL then permit
set security policies from-zone WAN-Zone to-zone JNPR_2-Zone policy ALLOW_ALL match source-address 192.168.221.0/24 set security policies from-zone WAN-Zone to-zone JNPR_2-Zone policy ALLOW_ALL match source-address 192.168.222.0/24 set security policies from-zone WAN-Zone to-zone JNPR_2-Zone policy ALLOW_ALL match destination-address any set security policies from-zone WAN-Zone to-zone JNPR_2-Zone policy ALLOW_ALL match application any set security policies from-zone WAN-Zone to-zone JNPR_2-Zone policy ALLOW_ALL then permit
set security policies from-zone JNPR_1-Zone to-zone WAN-Zone policy ALLOW_ALL match source-address any set security policies from-zone JNPR_1-Zone to-zone WAN-Zone policy ALLOW_ALL match destination-address 192.168.222.0/24 set security policies from-zone JNPR_1-Zone to-zone WAN-Zone policy ALLOW_ALL match destination-address 192.168.221.0/24 set security policies from-zone JNPR_1-Zone to-zone WAN-Zone policy ALLOW_ALL match application any set security policies from-zone JNPR_1-Zone to-zone WAN-Zone policy ALLOW_ALL then permit
set security policies from-zone JNPR_2-Zone to-zone WAN-Zone policy ALLOW_ALL match source-address any set security policies from-zone JNPR_2-Zone to-zone WAN-Zone policy ALLOW_ALL match destination-address 192.168.222.0/24 set security policies from-zone JNPR_2-Zone to-zone WAN-Zone policy ALLOW_ALL match destination-address 192.168.221.0/24 set security policies from-zone JNPR_2-Zone to-zone WAN-Zone policy ALLOW_ALL match application any set security policies from-zone JNPR_2-Zone to-zone WAN-Zone policy ALLOW_ALL then permit
스파인 스위치 구성
단계별 절차
-
스파인 1에서 라우팅 인스턴스 및 irb 인터페이스를 구성합니다.
set interfaces irb unit 993 family inet address 192.168.193.3/28 set routing-instances WAN_VRF description "VRF for tenant WAN" set routing-instances WAN_VRF instance-type vrf set routing-instances WAN_VRF interface et-0/0/48.0 set routing-instances WAN_VRF interface irb.993 set routing-instances WAN_VRF interface lo0.103 set routing-instances WAN_VRF route-distinguisher 192.168.253.13:103 set routing-instances WAN_VRF vrf-target target:3:65001 set routing-instances WAN_VRF vrf-table-label set routing-instances WAN_VRF routing-options auto-export set routing-instances WAN_VRF routing-options multipath set routing-instances WAN_VRF protocols bgp group INTERCONNECT type external set routing-instances WAN_VRF protocols bgp group INTERCONNECT import Interconnect_WAN-IMPORT set routing-instances WAN_VRF protocols bgp group INTERCONNECT family inet unicast set routing-instances WAN_VRF protocols bgp group INTERCONNECT authentication-key "$ABC123" set routing-instances WAN_VRF protocols bgp group INTERCONNECT export Interconnect_WAN-EXPORT set routing-instances WAN_VRF protocols bgp group INTERCONNECT local-as 65313 set routing-instances WAN_VRF protocols bgp group INTERCONNECT multipath multiple-as set routing-instances WAN_VRF protocols bgp group INTERCONNECT bfd-liveness-detection minimum-interval 1000 set routing-instances WAN_VRF protocols bgp group INTERCONNECT bfd-liveness-detection multiplier 3 set routing-instances WAN_VRF protocols bgp group INTERCONNECT neighbor 192.168.193.1 peer-as 65200 set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY type external set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY description "Connection to EBGP WAN_UNDERLAY" set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY family inet unicast set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY authentication-key "$ABC123" set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY local-as 65313 set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY multipath multiple-as set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY bfd-liveness-detection minimum-interval 350 set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY bfd-liveness-detection multiplier 3 set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY neighbor 192.168.100.2 peer-as 65300
스파인 2에서 라우팅 인스턴스를 구성합니다.
set interfaces irb unit 993 family inet address 192.168.193.2/28 set routing-instances WAN_VRF description "VRF for tenant WAN" set routing-instances WAN_VRF instance-type vrf set routing-instances WAN_VRF interface et-0/0/48.0 set routing-instances WAN_VRF interface irb.993 set routing-instances WAN_VRF interface lo0.103 set routing-instances WAN_VRF route-distinguisher 192.168.253.12:103 set routing-instances WAN_VRF vrf-target target:3:65001 set routing-instances WAN_VRF vrf-table-label set routing-instances WAN_VRF routing-options auto-export set routing-instances WAN_VRF routing-options multipath set routing-instances WAN_VRF protocols bgp group INTERCONNECT type external set routing-instances WAN_VRF protocols bgp group INTERCONNECT import Interconnect_WAN-IMPORT set routing-instances WAN_VRF protocols bgp group INTERCONNECT family inet unicast set routing-instances WAN_VRF protocols bgp group INTERCONNECT authentication-key "$ABC123" set routing-instances WAN_VRF protocols bgp group INTERCONNECT export Interconnect_WAN-EXPORT set routing-instances WAN_VRF protocols bgp group INTERCONNECT local-as 65312 set routing-instances WAN_VRF protocols bgp group INTERCONNECT multipath multiple-as set routing-instances WAN_VRF protocols bgp group INTERCONNECT bfd-liveness-detection minimum-interval 1000 set routing-instances WAN_VRF protocols bgp group INTERCONNECT bfd-liveness-detection multiplier 3 set routing-instances WAN_VRF protocols bgp group INTERCONNECT neighbor 192.168.193.1 peer-as 65200 set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY type external set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY description "Connection to EBGP WAN_UNDERLAY" set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY family inet unicast set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY authentication-key "$ABC123" set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY local-as 65312 set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY multipath multiple-as set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY bfd-liveness-detection minimum-interval 350 set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY bfd-liveness-detection multiplier 3 set routing-instances WAN_VRF protocols bgp group WAN_UNDERLAY neighbor 192.168.100.0 peer-as 65300
스파인 3에서 EBGP를 구성합니다.
set protocols bgp group WAN_UNDERLAY type external set protocols bgp group WAN_UNDERLAY description "Connection to EBGP WAN_UNDERLAY" set protocols bgp group WAN_UNDERLAY family inet unicast set protocols bgp group WAN_UNDERLAY authentication-key "$ABC123" set protocols bgp group WAN_UNDERLAY export WAN_EXPORT set protocols bgp group WAN_UNDERLAY local-as 65322 set protocols bgp group WAN_UNDERLAY multipath multiple-as set protocols bgp group WAN_UNDERLAY bfd-liveness-detection minimum-interval 350 set protocols bgp group WAN_UNDERLAY bfd-liveness-detection multiplier 3 set protocols bgp group WAN_UNDERLAY neighbor 192.168.100.10 peer-as 65300 set policy-options policy-statement WAN_EXPORT term DIRECT_ROUTES from protocol direct set policy-options policy-statement WAN_EXPORT term DIRECT_ROUTES from route-filter 192.168.221.0/24 exact set policy-options policy-statement WAN_EXPORT term DIRECT_ROUTES from route-filter 192.168.222.0/24 exact set policy-options policy-statement WAN_EXPORT term DIRECT_ROUTES then accept
스파인 4에서 EBGP를 구성합니다.
set protocols bgp group WAN_UNDERLAY type external set protocols bgp group WAN_UNDERLAY description "Connection to EBGP WAN_UNDERLAY" set protocols bgp group WAN_UNDERLAY family inet unicast set protocols bgp group WAN_UNDERLAY authentication-key "$ABC123" set protocols bgp group WAN_UNDERLAY export WAN_EXPORT set protocols bgp group WAN_UNDERLAY local-as 65323 set protocols bgp group WAN_UNDERLAY multipath multiple-as set protocols bgp group WAN_UNDERLAY bfd-liveness-detection minimum-interval 350 set protocols bgp group WAN_UNDERLAY bfd-liveness-detection multiplier 3 set protocols bgp group WAN_UNDERLAY neighbor 192.168.100.16 peer-as 65300 set policy-options policy-statement WAN_EXPORT term DIRECT_ROUTES from protocol direct set policy-options policy-statement WAN_EXPORT term DIRECT_ROUTES from route-filter 192.168.221.0/24 exact set policy-options policy-statement WAN_EXPORT term DIRECT_ROUTES from route-filter 192.168.222.0/24 exact set policy-options policy-statement WAN_EXPORT term DIRECT_ROUTES then accept
DCI 경로 확인
단계별 절차
SRX 섀시 클러스터에서 경로를 확인합니다. SRX는 서로 다른 서브넷에 대한 모든 특정 경로를 학습해야 합니다.
user@srx> show route inet.0: 31 destinations, 37 routes (31 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both 192.168.201.0/24 *[BGP/170] 00:59:11, localpref 100 AS path: 65113 I, validation-state: unverified > to 192.168.191.3 via reth1.991 192.168.201.10/32 *[BGP/170] 00:00:07, localpref 100 AS path: 65113 I, validation-state: unverified > to 192.168.191.3 via reth1.991 192.168.201.81/32 *[BGP/170] 00:00:07, localpref 100 AS path: 65113 I, validation-state: unverified > to 192.168.191.3 via reth1.991 192.168.202.0/24 *[BGP/170] 00:59:11, localpref 100 AS path: 65113 I, validation-state: unverified > to 192.168.191.3 via reth1.991 192.168.202.61/32 *[BGP/170] 00:59:11, localpref 100 AS path: 65113 I, validation-state: unverified > to 192.168.191.3 via reth1.991 192.168.202.62/32 *[BGP/170] 00:59:11, localpref 100 AS path: 65113 I, validation-state: unverified > to 192.168.191.3 via reth1.991 192.168.203.0/24 *[BGP/170] 00:59:11, localpref 100 AS path: 65113 I, validation-state: unverified > to 192.168.191.3 via reth1.991 192.168.203.61/32 *[BGP/170] 00:15:09, localpref 100 AS path: 65113 I, validation-state: unverified > to 192.168.191.3 via reth1.991 192.168.211.0/24 *[BGP/170] 00:34:09, localpref 100 AS path: 65213 I, validation-state: unverified > to 192.168.192.3 via reth1.992 192.168.212.0/24 *[BGP/170] 00:34:09, localpref 100 AS path: 65213 I, validation-state: unverified > to 192.168.192.3 via reth1.992 192.168.221.0/24 *[BGP/170] 00:25:07, localpref 100 AS path: 65313 65300 65322 I, validation-state: unverified > to 192.168.193.3 via reth1.993 192.168.222.0/24 *[BGP/170] 00:25:07, localpref 100 AS path: 65313 65300 65322 I, validation-state: unverified > to 192.168.193.3 via reth1.993스파인 1 및 스파인 2에서 경로를 확인합니다. SRX 클러스터는 모든 VRF의 스파인 디바이스에 192.168.0.0/16 요약 경로를 보급합니다. 모든 VRF 간 트래픽 및 DCI 트래픽은 SRX 섀시 클러스터를 통과합니다.
user@spine1> show route 192.168.0.0 JNPR_1_VRF.inet.0: 19 destinations, 23 routes (19 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both 192.168.0.0/16 *[BGP/170] 01:05:15, localpref 100 AS path: 65200 I, validation-state: unverified > to 192.168.191.1 via irb.991 JNPR_2_VRF.inet.0: 13 destinations, 16 routes (13 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both 192.168.0.0/16 *[BGP/170] 00:40:12, localpref 100 AS path: 65200 I, validation-state: unverified > to 192.168.192.1 via irb.992 WAN_VRF.inet.0: 12 destinations, 12 routes (12 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both 192.168.0.0/16 *[BGP/170] 01:04:59, localpref 100 AS path: 65200 I, validation-state: unverified > to 192.168.193.1 via irb.993스파인 3 및 스파인 4에서 경로를 확인합니다. DC2 스파인 디바이스는 DC1 스파인 디바이스의 WAN VRF에서 집계 경로를 수신합니다. 두 데이터센터 간의 모든 트래픽은 SRX 섀시 클러스터를 통해 라우팅됩니다.
user@spine3> show route 192.168.0.0 inet.0: 24 destinations, 26 routes (21 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both 192.168.0.0/16 [BGP ] 00:11:47 AS path: 65300 65313 65200 I, validation-state: unverified > to 192.168.100.10 via et-0/0/30.0컬랩스드 스파인(collapsed spine) 데이터센터 네트워크를 DCI와 연결했습니다.
