Application Identification on SRX Series Firewalls
Application Identification enables you to see the applications on your network and learn how they work, their behavioral characteristics, and their relative risk. Using several different identification mechanisms, App ID detects the applications on your network regardless of the port, protocol, and other evasive tactics used. For more information, see the following topics:
Understanding Application Identification Techniques
Historically, firewalls have used the IP address and port numbers as a way of enforcing policies. That strategy is based on the assumption that users connect to the network from fixed locations and access particular resources using specific port numbers.
Today, wireless networking and mobile devices require a different strategy. The way in which devices connect to the network changes rapidly. An individual can connect to the network using multiple devices simultaneously. It is no longer practical to identify a user, application, or device by a group of statically allocated IP addresses and port numbers.
This topic includes the following section:
- Junos OS Next-Generation Application Identification
- Benefits of Application Identification
- Application Signature Mapping
- Application Identification Match Sequence
Junos OS Next-Generation Application Identification
Next-generation application identification builds on the legacy application identification functionality and provides more effective detection capabilities for evasive applications such as Skype, BitTorrent, and Tor.
Junos OS application identification recognizes Web-based and other applications and protocols at different network layers using characteristics other than port number. Applications are identified by using a protocol bundle containing application signatures and parsing information. The identification is based on protocol parsing and decoding and session management.
The detection mechanism has its own data feed and constructs to identify applications.
The following features are supported in application identification:
-
Support for protocols and applications, including video streaming, peer-to-peer communication, social networking, and messaging
-
Identification of services within applications
-
Ability to distinguish actions launched within an application (such as login, browse, chat, and file transfer)
-
Support for all versions of protocols and application decoders and dynamic updates of decoders
-
Support for encrypted and compressed traffic and most complex tunneling protocols
-
Ability to identify all protocols from Layer 3 to Layer 7 and above Layer 7
Benefits of Application Identification
-
Provides granular control over applications, including video streaming, peer-to-peer communication, social networking, and messaging. It also identifies services, port usage, underlying technology, and behavioral characteristics within applications. This visibility enables you to block evasive applications inline at the firewall.
-
Identifies applications and allows, blocks, or limits applications— regardless of port or protocol, including applications known for using evasive techniques to avoid identification. This identification helps organizations control the types of traffic allowed to enter and exit the network.
Application Signature Mapping
Application signature mapping is a precise method of identifying the application that issued traffic on the network. Signature mapping operates at Layer 7 and inspects the actual content of the payload.
Applications are identified by using a downloadable protocol bundle. Application signatures and parsing information of the first few packets are compared to the content of the database. If the payload contains the same information as an entry in the database, the application of the traffic is identified as the application mapped to that database entry.
Juniper Networks provides a predefined application identification database that contains entries for a comprehensive set of known applications, such as FTP and DNS, and applications that operate over the HTTP protocol, such as Facebook, Kazaa, and many instant messaging programs. A signature subscription allows you to download the database from Juniper Networks and regularly update the content as new predefined signatures are added.
Application Identification Match Sequence
Figure 1 shows the sequence in which mapping techniques are applied and how the application is determined.
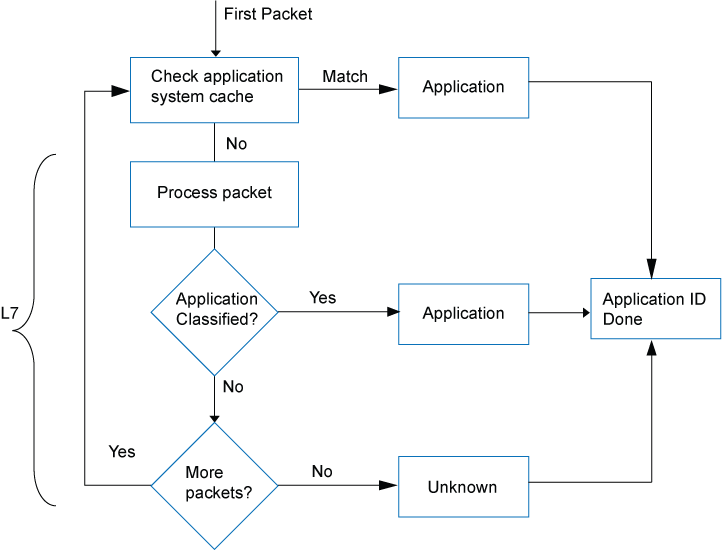
In application identification, every packet in the flow passes through the application identification engine for processing until the application is identified. Application bindings are saved in the application system cache (ASC) to expedite future identification process.
Application signatures identify an application based on protocol grammar analysis in the first few packets of a session. If the application identification engine has not yet identified the application, it passes the packets and waits for more data.
The application identification module matches applications for both client-to-server and server-to-client sessions.
Once the application is determined, AppSecure service modules can be configured to monitor and control traffic for tracking, prioritization, access control, detection, and prevention based on the application ID of the traffic.
-
Application Tracking (AppTrack)— Tracks and reports applications passing through the device.
-
Intrusion Detection and Prevention (IDP)— Applies appropriate attack objects to applications running on nonstandard ports. Application identification improves IDP performance by narrowing the scope of attack signatures for applications without decoders.
-
Application Firewall (AppFW)— Implements an application firewall using application-based rules.
-
Application Quality of Service (AppQoS)— Provides quality-of-service prioritization based on application awareness.
-
Advanced policy-based routing (APBR)— Classifies session based on applications and applies the configured rules to reroute the traffic.
-
Application Quality of Experience (AppQoE)— Monitors the performance of applications, and based on the score, selects the best possible link for that application traffic.
See Also
Understanding the Junos OS Application Identification Database
A predefined signature database is available on the Juniper Networks Security Engineering website. This database includes a library of application signatures. See Application Signatures for more details. These signature pages will give you visibility into the application category, group, risk-level, ports, and so on.
The predefined signature package provides identification criteria for known application signatures and is updated periodically.
Whenever new applications are added, the protocol bundle is updated and generated for all relevant platforms. It is packaged together with other application signature files. This package will be available for download through the security download website.
A subscription service allows you to regularly download the latest signatures for up-to-date coverage without having to create entries for your own use.
Application identification is enabled by default and is automatically turned on when you configure Intrusion Detection and Prevention (IDP), AppFW, AppQoS, or AppTrack.
Updates to the Junos OS predefined application signature package are authorized by a separately licensed subscription service. You must install the application identification application signature update license key on your device to download and install the signature database updates provided by Juniper Networks. When your license key expires, you can continue to use the locally stored application signature package contents but you cannot update the package.
See Also
Disabling and Reenabling Junos OS Application Identification
Application identification is enabled by default. You can disable application identification with the CLI.
To disable application identification:
user@host# set services application-identification no-application-identification
If you want to reenable application identification, delete the configuration statement that specifies disabling of application identification:
user@host# delete services application-identification no-application-identification
If you are finished configuring the device, commit the configuration.
To verify the configuration, enter the show services application-identification command.
See Also
Understanding the Application System Cache
Application system cache (ASC) saves the mapping between an application type and the corresponding destination IP address, destination port, protocol type, and service. Once an application is identified, its information is saved in the ASC so that only a matching entry is required to identify an application running on a particular system, thereby expediting the identification process.
By default, the ASC saves the mapping information for 3600 seconds. However, you can configure the cache timeout value by using the CLI.
You can use the [edit services application-identification
application-system-cache-timeout] command to change the timeout
value for the application system cache entries. The timeout value
can be configured from 0 through 1,000,000 seconds. The ASC session
might expire after 1000,000 seconds.
ASC entries expire after the configured ASC timeout. ASC entries are not refreshed even when there are cache hits (matching entry in ASC found) during the timeout period.
When you configure a new custom application signature or modify an existing custom signature, all the existing application system cache entries for predefined and custom applications will be cleared.
When you delete or disable a custom application signature, and the configuration commit fails, the application system cache (ASC) entry is not cleared completely; instead, a base application in the path of custom application will be reported in ASC.
See Also
Enabling or Disabling Application System Cache for Application Services
ASC is enabled by default; note the difference in security services lookup:
-
ASC lookup for security services is not enabled by default. That is—security services including security policies, application firewall (AppFW), application tracking (AppTrack), application quality of service (AppQoS), Juniper ATP Cloud, IDP, and Content Security do not use the ASC by default.
-
ASC lookup for miscellaneous services is enabled by default. That is—miscellaneous services including advanced policy-based routing (APBR) use the ASC for application identification by default.
The change in the default behavior of the ASC affects the legacy AppFW functionality. With the ASC disabled by default for the security services starting in Junos OS Release 18.2 onward, AppFW will not use the entries present in the ASC.
You can revert to the ASC behavior as in Junos OS releases before
Release 18.2 by using the set services application-identification
application-system-cache security-services command.
The security device might become susceptible to application evasion techniques if the ASC is enabled for security services. We recommend that you enable the ASC only when the performance of the device in its default configuration (disabled for security services) is not sufficient for your specific use case.
Use the following commands to enable or disable the ASC:
Enable the ASC for security services:
user@host#set services application-identification application-system-cache security-servicesDisable the ASC for miscellaneous services:
user@host#set services application-identification application-system-cache no-miscellaneous-servicesDisable the enabled ASC for security services:
user@host#delete services application-identification application-system-cache security-servicesEnable the disabled ASC for miscellaneous services:
user@host#delete services application-identification application-system-cache no-miscellaneous-services
You can use the show services application-identification
application-system-cache command to verify the status of the
ASC.
The following sample output provides the status of the ASC:
user@host>show services application-identification application-system-cache
Application System Cache Configurations:
application-cache: on
Cache lookup for security-services: off
Cache lookup for miscellaneous-services: on
cache-entry-timeout: 3600 seconds
In previous releases , application caching was enabled by default. You can manually disable it by
using the set services application-identification
no-application-system-cache command.
user@host# set services application-identification no-application-system-cache
See Also
Verifying Application System Cache Statistics
Purpose
Verify the application system cache (ASC) statistics.
The application system cache will display the cache for application identification applications.
Action
From CLI operation mode, enter the show services
application-identification application-system-cache command.
Sample Output
command-name
user@host> show services application-identification application-system-cache application-cache: on nested-application-cache: on cache-unknown-result: on cache-entry-timeout: 3600 seconds
Meaning
The output shows a summary of the ASC statistics information. Verify the following information:
IP address—Displays the destination address.
Port—Displays the destination port on the server.
Protocol—Displays the protocol type on the destination port.
Application—Displays the name of the application identified on the destination port.
When there are a large number of ASC entries (10,000 or more), and the
entries are to be listed in the output for the command show services
application-identification application-system-cache, a CLI session timeout
occurs for some firewalls.
See Also
Onbox Application Identification Statistics
Application Identification services provide statistical information per session. These statistics provide customers with an application usage profile. The Onbox Application Identification Statistics feature adds application-level statistics to the AppSecure suite. Application statistics allow an administrator to access cumulative statistics as well as statistics accumulated over user-defined intervals.
With this feature, the administrator can clear the statistics and configure the interval values while maintaining bytes and session count statistics. Because the statistics count occurs at session close event time, the byte and session counts are not updated until the session closes. Juniper Networks security devices support a history of eight intervals that an administrator can use to display application session and byte counts..
If application grouping is supported in your configuration of Junos OS, then the Onbox Application Identification Statistic feature supports onbox per-group matching statistics. The statistics are maintained for predefined groups only.
Reinstalling an application signature package will not clear the application statistics. If the application is disabled, there will not be any traffic for that application, but the application is still maintained in the statistics. It does not matter if you are reinstalling a predefined application, because applications are tracked according to application type. For predefined group statistics, reinstalling a security package will not clear the statistics. However, any changes to group memberships are updated. For example, junos:web might have 50 applications in the current release and 60 applications following an upgrade. Applications that are deleted and application groups that are renamed are handled in the same way as applications that are added.
The Application Identification module maintains a 64-bit session counters for each application on each Services Processing Unit (SPU). The counter increments when a session is identified as a particular application. Another set of 64-bit counters aggregates the total bytes per application on the SPU. Counters for unspecified applications are also maintained. Statistics from multiple SPUs for both sessions and bytes are aggregated on the Routing Engine and presented to the users.
Individual SPUs have interval timers to roll over statistics
per interval time. To configure the interval
for statistics collection, use the set services application-identification
statistics interval time command. Whenever
the Routing Engine queries for the required interval, the corresponding
statistics are fetched from each SPU, aggregated in the Routing Engine
and presented to the user.
Use the clear services application-identification statistics to clear all application statistics such as cumulative, interval,
applications, and application groups.
Use the clear services application-identification counter command to reset the counters manually. Counters reset automatically
when a device is upgraded or rebooted, when flowd restarts, or when
there is a change in the interval timer.
Use the set services application-identification application-system-cache-timeout
value to specify the timeout value in seconds for the application
system cache entries.
The default time interval for application identification statistics collection time is 1440 minutes.
Configuring IMAP Cache Size
Internet Message Access Protocol (IMAP) is an Internet standard protocol used by e-mail clients for e-mail storage and retrieval services. IMAP cache is used for protocol parsing and context generation. It stores parsing related information of an email.
You can configure to limit the maximum number of entries in the IMAP cache and specify the timeout value for the entries in the cache using following commands:
set services application-identification imap-cache imap-cache-size size
set services application-identification imap-cache imap-cache-timeout time in seconds
Example:
[edit]
user@host# set services application-identification imap-cache imap-cache-size 50000
In this example, the IMAP cache size is configured to store 50,000 entries.
[edit]
user@host# set services application-identification imap-cache-timeout 600
In this example, time out period is configured to 600 seconds during which a cache entry remains in IMAP cache.
See Also
Understanding Jumbo Frames Support for Junos OS Application Identification Services
Application identification support the larger jumbo frame size
of 9192 bytes. Although jumbo frames are enabled by default, you can
adjust the maximum transmission unit (MTU) size by using the [set interfaces] command. CPU overhead can be reduced while
processing jumbo frames.
See Also
Application Identification Inspection Limit
To configure the application identification inspection limits:
-
Inspection Limit for TCP and UDP Sessions
You can set the byte limit and the packet limit for application identification (AppID) in a UDP or in a TCP session. AppID concludes the classification based on the configured inspection limit. On exceeding the limit, AppID terminates the application classification.
If AppID does not conclude the final classification within the configured limits, and a pre-matched application is available, AppID concludes the application as the pre-matched application. Otherwise, the application is concluded as junos:UNKNOWN provided the global AppID cache is enabled. The global AppID cache is enabled by default.
To configure the byte limit and the packet limit, use the following configuration statements from the
[edit]hierarchy:-
user@host#set services application-identification inspection-limit tcp byte-limit byte-limit-number packet-limit packet-limit-number -
user@host#set services application-identification inspection-limit udp byte-limit byte-limit-number packet-limit packet-limit-number
Table 1 provides the range and default value for configuring the byte limit and the packet limit for TCP and UDP sessions.
Table 1: Maximum Byte Limit and Packet Byte Limit for TCP and UDP Sessions Session
Limit
Range
Default Value
TCP
Byte limit
0 through 4294967295
6000
Packet limit
0 through 4294967295
Zero
UDP
Byte limit
0 through 4294967295
Zero
Packet limit
0 through 4294967295
10
The byte limit excludes the IP header and the TCP/UDP header lengths.
If you set the both the
byte-limitand thepacket-limitoptions, AppID inspects the session until both the limits are reached.You can disable the TCP or UDP inspection limit by configuring the corresponding
byte-limitand thepacket-limitvalues to zero. -
-
Global Offload Byte Limit (Other Sessions)
You can set the byte limit for the AppID to conclude the classification and identify the application in a session. On exceeding the limit, AppID terminates the application classification and takes one of the following decisions:
-
If a pre-matched application is available, AppID concludes the application classification as the pre-matched application in following cases:
-
When AppID does not conclude the final classification within the configured byte limit
-
When the session is not offloaded due to tunnelling behavior of some applications
-
-
If a pre-matched application is not available, AppID concludes the application as junos:UNKNOWN, provided the global AppID cache is enabled. The global AppID cache is enabled by default. See Enabling or Disabling Application System Cache for Application Services.
To configure the byte limit, use the following configuration statement from the
[edit]hierarchy:set services application-identification global-offload-byte-limit byte-limit-number
The default value for the
global-offload-byte-limitoption is 10000.You can disable the global offload byte limit by configuring the
global-offload-byte-limitvalue to zero.The byte limit excludes the IP header and the TCP/UDP header lengths.
-
- Enable Performance Mode Option
- Application Identification Support for Applications Hosted on Content Delivery Network (CDN)
- Maximum Memory Limit for DPI
Enable Performance Mode Option
The maximum packet threshold for DPI performance mode option set services
application-identification enable-performance-mode max-packet-threshold
value is deprecated—rather than immediately
removed—to provide backward compatibility and an opportunity to bring your
configuration into compliance with the new configuration. This option was used for
setting the maximum packet threshold for the DPI performance mode.
If your configuration includes enabled performance mode option with
max-packet-threshold in older Junos OS releases, the AppID
concludes the application classification on reaching the lowest value configured in
the TCP or UDP inspection limit or global offload byte limit, or in the maximum
packet threshold for DPI performance mode option.
Application Identification Support for Applications Hosted on Content Delivery Network (CDN)
You can enable application identification (AppID) to classify a web application that is hosted on a content delivery network (CDN) such as AWS, Akamai, Azure, Fastly, and Cloudflare and so on accurately. Use the following configuration statement to enable CDN application classification:
[edit]user@host#user@hots# set service application-identification enable-cdn-application-detection
When you apply the configuration, AppID identifies and classifies actual applications that are hosted on the CDN.
Maximum Memory Limit for DPI
You can configure the maximum memory limit for deep packet inspection (DPI) by using the following configuration statement:
user@host# set services application-identification max-memory memory-value
You can set 1 through 200000 MB as memory value.
Once the JDPI memory consumption reaches to 90% of the configured value, then DPI stops processing new sessions.
Improving the Application Traffic Throughput
The application traffic throughput can be improved by setting the deep packet inspection (DPI) in performance mode with default packet inspection limit as two packets, including both client-to-server and server-to-client directions. By default, performance mode is disabled on security devices.
To improve the application traffic throughput:
Use the show services application-identification status command to display detailed information about application identification
status.
show services application-identification status (DPI Performance Mode Enabled)
user@host> show services application-identification status pic: 2/1 Application Identification Status Enabled Sessions under app detection 0 Engine Version 4.18.2-24.006 (build date Jul 30 2014) Max TCP session packet memory 30000 Force packet plugin Disabled Force stream plugin Disabled DPI Performance mode: Enabled Statistics collection interval 1 (in minutes) Application System Cache Status Enabled Negative cache status Disabled Max Number of entries in cache 262144 Cache timeout 3600 (in seconds) Protocol Bundle Download Server https://signatures.juniper.net/cgi-bin/index.cgi AutoUpdate Disabled Slot 1: Application package version 2399 Status Active Version 1.40.0-26.006 (build date May 1 2014) Sessions 0 Slot 2 Application package version 0 Status Free Version Sessions 0
The DPI Performance mode field displays whether the DPI performance mode is enabled or not. This field is displayed in the CLI command output only if the performance mode is enabled.
If you want to set DPI to default accuracy mode and disable the performance mode, delete the configuration statement that specifies enabling of the performance mode:
To disable the performance mode:
Delete the performance mode.
[edit]user@host# delete services application-identification enable-performance-modeCommit the configuration.
[edit]user@host# commit
See Also
Packet Capture of Unknown Application Traffic Overview
You can use the packet capture of unknown applications feature to gather more details about an unknown application on your security device. Unknown application traffic is the traffic that does not match an application signature.
Once you’ve configured packet capture options on your security device, the unknown application traffic is gathered and stored on the device in a packet capture file (.pcap). You can use the packet capture of an unknown application to define a new custom application signature. You can use this custom application signature in a security policy to manage the application traffic more efficiently.
You can send the .pcap file to Juniper Networks for analysis in cases where the traffic is incorrectly classified, or to request creation of an application signature.
Benefits of Packet Capture of Unknown Application Traffic
You can use the packet capture of unknown application traffic to:
Gather more insight about an unknown application
Analyze unknown application traffic for potential threats
Assist in creation of security policy rules
Enable custom application signature creation
Implementing security policies that block all unknown application traffic could cause issues with network-based applications. Before applying these types of policies, be sure to validate that this approach does not cause issues in your environment. You must carefully analyze the unknown application traffic, and define the security policy accordingly.
Configure Packet Capture For Unknown Application Traffic
Before You Begin
To enable automatic packet capture of unknown application traffic, you must:
-
Install an active application identification feature license on your firewall. See Managing Junos OS Licenses.
-
Download and install the Junos OS application signature package. See Download and Install Junos OS Application Signature Package.
-
Ensure you have Junos OS Release 20.2R1 or later version on your firewall.
Overview
In this example, you’ll learn how to configure automated packet capture of unknown applications on your security device by completing the following steps:
-
Set packet capture options at global level or at a security policy level.
-
Configure packet capture mode
-
(Optional) Configure packet capture file options
-
Access the generated packet capture file (.pcap file)
Configuration
To learn about packet capture configuration options, see packet-capture before you begin.
- Packet Capture for Unknown Applications Globally
- Packet Capture for Unknown Applications At a Security Policy Level
- Selecting Packet Capture Mode
- Define Packet Capture Options (Optional)
- Accessing Packet Capture Files (.pcaps)
Packet Capture for Unknown Applications Globally
Step-by-Step Procedure
-
To enable packet capture at a global level, use the following command:
user@host#set services application-identification packet-capture global
When you enable packet capture at the global level, your security device generates a packet capture for all sessions that contain unknown application traffic.
Packet Capture for Unknown Applications At a Security Policy Level
Step-by-Step Procedure
-
Configure packet capture at a security policy level, use the following procedure. In this example, you’ll enable packet capture of unknown application traffic at the security policy P1.
[edit]user@host#set security policies from-zone untrust to-zone trust policy P1 match source-address anyuser@host#set security policies from-zone untrust to-zone trust policy P1 match destination-address anyuser@host#set security policies from-zone untrust to-zone trust policy P1 match application anyuser@host#set security policies from-zone untrust to-zone trust policy P1 match dynamic-application junos:UNKNOWNuser@host#set security policies from-zone untrust to-zone trust policy P1 then permit application-services packet-captureTo enable packet capture of unknown application traffic at the security policy level, you must include
junos:UNKNOWNas the dynamic-application match conditions.When you configure the security policy (P1), the system captures the packet details for the application traffic that matches the security policy match criteria.
Selecting Packet Capture Mode
You can capture the packets for the unknown application traffic in either of the following modes:
-
ASC mode—Captures packets for unknown applications when the application is classified as junos:UNKNOWN and has a matching entry in the application system cache (ASC). This mode is enabled by default.
-
Aggressive mode—Captures all traffic before AppID has finished classification. In this mode, the system captures all application traffic regardless of an available ASC entry. Packet capture begins from the first packet of the first session. Note that aggressive mode is significantly more resource-intensive and should be used with caution.
To enable aggressive mode, use the following command:
[edit]user@host#set services application-identification packet-capture aggressive-modeWe do not recommend using aggressive mode unless you need to capture the first occurrence of a flow. As noted above, the default behavior of the device relies on the ASC.
Define Packet Capture Options (Optional)
Step-by-Step Procedure
Optionally, you can set the following packet capture parameters. Otherwise, the default options described in packet-capture are used for this feature. In this example, you define packet capture options such as maximum packet limit, maximum byte limit, and number of packet capture (.pcap) files.
-
Set the maximum number of UDP packets per session.
[edit]user@host#set services application-identification packet-capture max-packets 10 -
Set the maximum number of TCP bytes per session.
[edit]user@host#set services application-identification packet-capture max-bytes 2048 -
Set the maximum number of packet capture (.pcap) files to be created before the oldest one is overwritten and rotated out.
[edit]user@host#set services application-identification packet-capture max-files 30
Results
From configuration mode, confirm your configuration
by entering the show services application-identification packet-capture command and show security policies hierarchy level. If
the output does not display the intended configuration, follow the
configuration instructions in this example to correct it.
The following configuration shows an example of unknown application packet capture at the global level with optional configurations:
[edit services application-identification]user@host# show packet-capture{ global; max-packets 10; max-bytes 2048; max-files 30; }
The following configuration shows an example of unknown application packet capture at a security policy level with optional configurations:
[edit services application-identification]user@host# show packet-capture{ max-packets 10; max-bytes 2048; max-files 30; }
[edit security policies]
user@host# show
from-zone untrust to-zone trust {
policy P1 {
match {
source-address any;
destination-address any;
application any;
dynamic-application [ junos:UNKNOWN ];
}
then {
permit {
application-services {
packet-capture;
}
}
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Accessing Packet Capture Files (.pcaps)
After you complete the configuration and commit it, you can view the packet capture (.pcap) file. The system generates a unique packet capture file for each destination IP address, destination port, and protocol.
Step-by-Step Procedure
To view the packet capture file:
-
Navigate to the directory where .pcap files are stored on the device.
user@host> start shell % % cd /var/log/pcap
-
Locate the .pcap file.
The .pcap file is saved in destination-IP-address. destination-port.protocol. pcap format. Example: 142.250.31.156_443_17.pcap.
user@host:/var/log/pcap # ls -lah total 1544 drwxr-xr-x 2 root wheel 3.0K Jul 27 15:04 . drwxrwxr-x 9 root wheel 3.0K Jul 24 16:23 .. -rw-r----- 1 root wheel 5.0K Jul 24 20:16 142.250.31.156_443_17.pcap -rw-r----- 1 root wheel 16K Jul 27 15:03 142.250.64.97_443_17.pcap -rw-r----- 1 root wheel 9.0K Jul 27 14:26 162.223.228.170_443_17.pcap -rw-r----- 1 root wheel 2.1K Jul 26 17:06 17.133.234.32_16385_17.pcap -rw-r----- 1 root wheel 11K Jul 24 16:20 172.217.0.226_443_17.pcap -rw-r----- 1 root wheel 16K Jul 27 14:21 172.217.9.234_443_17.pcap -rw-r----- 1 root wheel 31K Jul 27 14:25 172.217.9.238_443_17.pcap -rw-r----- 1 root wheel 17K Jul 24 19:21 52.114.132.87_3478_17.pcap
You can download the .pcap file by using SFTP or SCP and view it with Wireshark or your favorite network analyzer.
Figure 2 shows a sample .pcap file generated for the unknown application traffic.
Figure 2: Sample Packet Capture File Note:
Note:In situations where packet loss is occurring, the device may not be able to capture all relevant details of the flow. In this case, the .pcap file will only reflect what the device was able to ingest and process.
The security device saves the packet capture details for all traffic that matches the three match criteria (destination IP address, destination port, and protocol) in the same file regardless of global or policy-level configuration. The system maintains the cache with the destination IP address, destination port, and the protocol and does not accept the repeated capturing of the same traffic which exceeds the defined limit. You can set the packet capture file options as in packet-capture.
Verification
Viewing Packet Capture Details
Purpose
View the packet capture details to confirm that your configuration is working.
Action
Use the show services application-identification
packet-capture counters command.
user@host> show services application-identification packet-capture counters pic: 0/0 Counter type Value Total sessions captured 47 Total packets captured 282 Active sessions being captured 1 Sessions ignored because of memory allocation failures 0 Packets ignored because of memory allocation failures 0 Ipc messages ignored because of storage limit 0 Sessions ignored because of buffer-packets limit 0 Packets ignored because of buffer-packets limit 0 Inconclusive sessions captured 4 Inconclusive sessions ignored 0 Cache entries timed out 0
Meaning
From this sample output, you can get details such as the number of sessions being captured, and the number of sessions already captured. For more details about the packet capture counters, see show services application-identification packet-capture counters.
Packet Capture of Unknown Applications Details per Session
Your security device stores the packet capture of unknown applications details per session. The packet capture (.pcap) file now includes the session ID in the file name. That is—destination-IP-address_destination-port_protocol_session-id. pcap in /var/log/pcap location.
By storing the packet capture per session, the .pcap file size is reduced as it saves details per session only.
In addition, we’ve enhanced packet capture of unknown application functionality to capture unknown SNI details
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
set
services application-identification enable-performance-mode max-packet-threshold
value is deprecated. set services application-identification
no-application-system-cache command.