DHCPv6 Relay Agent
The DHCPv6 relay agent enhances the DHCP relay agent by providing support in an IPv6 network. The DHCPv6 relay agent passes messages between the DHCPv6 client and the DHCPv6 server, similar to the way DHCP relay agent supports an IPv4 network. DHCPv6 relay agents eliminate the necessity of having a DHCPv6 server on each physical network. For more information about inserting DHCPv6 Interface-ID (Option 18), Remote-ID (Option 37) or Client MAC Address (Option 79) in DHCPv6 packets, and verifying the DHCPv6 configuration, read this topic.
DHCPv6 Relay Agent Overview
When a DHCPv6 client logs in, the DHCPv6 relay agent uses the AAA service framework to interact with the RADIUS server to provide authentication and accounting. The RADIUS server, which is configured independently of DHCP, authenticates the client and supplies the IPv6 prefix and client configuration parameters, such as session timeout and the maximum number of clients allowed per interface.
The PTX Series Packet Transport Routers do not support authentication for DHCPv6 relay agents.
The following DHCPv6 functionalities are not supported on ACX Series routers:
Subscriber authentication for DHCPv6 relay agents
DHCP snooping
DHCPv6 client
Liveness detection
Dynamic profiles
Option 37 support for remote ID insertion
Bidirectional Forwarding Detection (BFD) for DHCPv6 relay
The DHCPv6 relay agent is compatible with the DHCP local server and the DHCP relay agent, and can be enabled on the same interface as either the DHCP local server or DHCP relay agent.
To configure the DHCPv6 relay agent on the router (or switch),
you include the dhcpv6 statement at the [edit forwarding-options
dhcp-relay] hierarchy level.
You can also include the dhcpv6 statement
at the following hierarchy levels:
[edit logical-systems logical-system-name forwarding-options dhcp-relay][edit logical-systems logical-system-name routing-instances routing-instance-name forwarding-options dhcp-relay][edit routing-instances routing-instance-name forwarding-options dhcp-relay]
See DHCPv6 Monitoring and Management for commands specific to viewing and clearing DHCPv6 bindings and statistics.
Configuring DHCPv6 Relay Agent
The DHCPv6 relay agent operates as the interface to relay messages between DHCPv6 clients and the DHCPv6 server on different IP networks.
The example describes how to configure the DHCPv6 relay agent on the SRX Series Firewall. SRX Series Firewall acting as DHCPv6 relay agent is responsible for forwarding the requests and responses between the DHCPv6 clients and the server which are part of different routing instances.
Requirements
The example DHCPv6 relay agent configuration has been tested on the following hardware and software components:
-
SRX Series Firewalls with Junos OS 22.3R1 or later.
Overview
You can configure DHCPv6 relay agent to provide additional security when exchanging DHCPv6 messages between a DHCPv6 server and DHCPv6 clients that reside in different virtual routing instances. This type of configuration is for DHCPv6 relay connection between a DHCPv6 server and a DHCPv6 client, when the DHCPv6 server resides in a network that is isolated from the client network.
Topology
To exchange DHCPv6 messages between different routing instances, you must enable both the server-facing interface and the client-facing interface of the DHCPv6 relay agent to recognize and forward DHCPv6 packets.
The following Figure 1 shows DHCPv6 performance as DHCPv6 local server, DHCPv6 client, and DHCPv6 relay agent
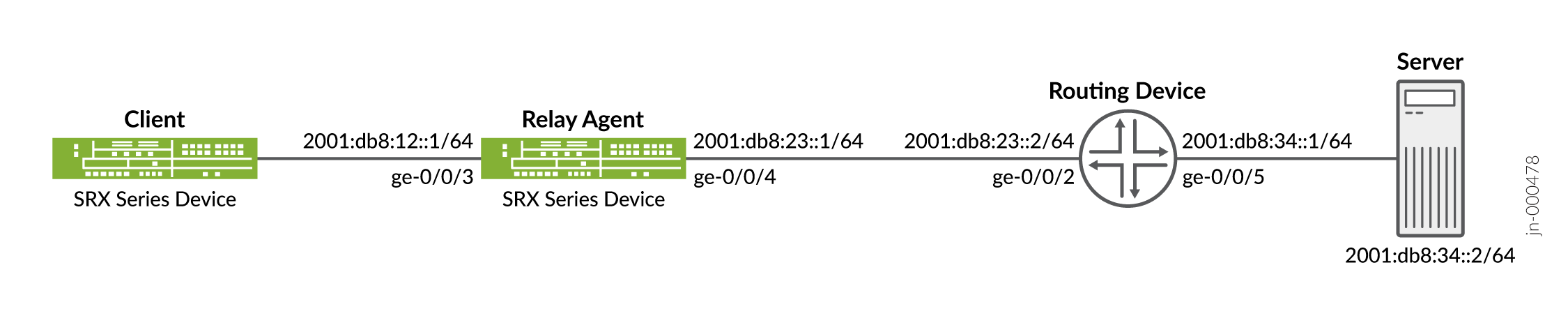
The following list provides an overview of the tasks required to create the DHCPv6 message exchange between the different routing instances:
-
Configure the client-facing side of the DHCPv6 relay agent.
-
Configure the server-facing side of the DHCPv6 relay agent.
-
Configure the Security Zone to Allow the DHCPv6 protocol.
Table1: DHCPv6 Relay Parameters:
Parameters
Client-Side-Details
Server-Side-Details
interface
ge-0/0/3.0
ge-0/0/4.0
routing interface
trust-vr
untrust-vr
ip address
2001:db8:12::1/64
2001:db8:23::1/64
Note:In order to make this setup work, the DHCPv6 server connecting route and relay agent interface route must be in both routing-instances. For example, in the above topology, the server route 2001:db8:34::/64 needs to be shared with the dhcp-relay VR, and the dhcp-relay interface route 2001:db8:12::/64 exact needs to be shared with the default routing instance.
Also, a dummy dhcp-relay config must be added in the routing instance with the DHCPv6 server. If this is not configured, dhcp-relay will not be able to receive packets from the DHCPv6 server.
Configuration
CLI Quick Configuration
The following procedures describe the configuration tasks for creating the
DHCPv6 message exchange between the DHCPv6 server and clients in different
routing instances. To quickly configure this example, copy the following
commands, paste them into a text file, remove any line breaks, change any
details necessary to match your network configuration, copy and paste the
commands into the CLI at the [edit] hierarchy level, and
then enter commit from configuration mode.
Quick configuration for Client-Facing Support:
set routing-instances trust-vr instance-type virtual-router set routing-instances trust-vr interface ge-0/0/3.0 set interfaces ge-0/0/3 unit 0 family inet6 address 2001:db8:12::1/64
Quick configuration for Server-Facing Support:
set routing-instances untrust-vr instance-type virtual-router set routing-instances untrust-vr interface ge-0/0/4.0 set routing-instances untrust-vr forwarding-options dhcp-relay dhcpv6 forward-only-replies set interfaces ge-0/0/4 unit 0 family inet6 address 2001:db8:23::1/64
Quick configuration for DHCPv6 Relay Support:
set routing-instances untrust-vr forwarding-options dhcp-relay dhcpv6 server-group dummy-config set routing-instances untrust-vr routing-options instance-import import_relay_route_to_server_vr set routing-instances untrust-vr routing-options static route 2001:db8:34::/64 next-hop 2001:db8:23::2 set routing-instances trust-vr forwarding-options dhcp-relay dhcpv6 server-group server-1 2001:db8:34::2 set routing-instances trust-vr forwarding-options dhcp-relay dhcpv6 active-server-group server-1 set routing-instances trust-vr forwarding-options dhcp-relay dhcpv6 group relay-in-vr interface ge-0/0/3.0 set routing-instances trust-vr routing-options instance-import export_dhcp_server_route set policy-options policy-statement export_dhcp_server_route term 1 from instance untrust-vr set policy-options policy-statement export_dhcp_server_route term 1 from route-filter 2001:db8:34::/64 exact set policy-options policy-statement export_dhcp_server_route term 1 then accept set policy-options policy-statement export_dhcp_server_route term 2 then reject set policy-options policy-statement import_relay_route_to_server_vr term 1 from instance trust-vr set policy-options policy-statement import_relay_route_to_server_vr term 1 from route-filter 2001:db8:12::/64 exact set policy-options policy-statement import_relay_route_to_server_vr term 1 then accept set policy-options policy-statement import_relay_route_to_server_vr term 2 then reject set routing-options static route 2001:db8:34::2/64 next-table untrust-vr.inet.0
Quick configuration for Security Zone to Allow the DHCPv6 Protocol:
set security policies default-policy permit-all set security zones security-zone untrust interfaces ge-0/0/4.0 host-inbound-traffic system-services all set security zones security-zone untrust interfaces ge-0/0/4.0 host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/3.0 host-inbound-traffic system-services all set security zones security-zone trust interfaces ge-0/0/3.0 host-inbound-traffic protocols all
Procedure
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure support on the client-facing side of the DHCPv6 relay agent:
-
Set a routing instance type as virtual router.
[edit] user@host# set routing-instances trust-vr instance-type virtual-router
-
Set an interface to the virtual router
[edit] user@host# set routing-instances trust-vr interface ge-0/0/3.0
-
Set the IP address to the interface.
[edit] user@host# set interfaces ge-0/0/3 unit 0 family inet6 address 2001:db8:12::1/64
Procedure
Step-by-Step Procedure
To configure support on the server-facing side of the DHCPv6 relay agent:
-
Set a virtual router.
[edit] user@host# set routing-instances untrust-vr instance-type virtual-router
-
Set an interface to the virtual router.
[edit] user@host# set routing-instances untrust-vr interface ge-0/0/4.0
-
Set the forward-only-replies option.
[edit] user@host# set routing-instances untrust-vr forwarding-options dhcp-relay dhcpv6 forward-only-replies
-
Set the IP address to the interface.
[edit] user@host# set interfaces ge-0/0/4 unit 0 family inet6 address 2001:db8:23::1/64
Procedure
Step-by-Step Procedure
To configure the DHCPv6 local server to support:
-
Set the configuration in dhcp-relay for untrust-vr routing instance
[edit ] user@host# set routing-instances untrust-vr forwarding-options dhcp-relay dhcpv6 server-group dummy-config user@host# set routing-instances untrust-vr routing-options instance-import import_relay_route_to_server_vr user@host# set routing-instances untrust-vr routing-options static route 2001:db8:34::/64 next-hop 2001:db8:23::2
-
Set the configuration in dhcp-relay for trust-vr routing instance
[edit ] user@host# set routing-instances trust-vr forwarding-options dhcp-relay dhcpv6 server-group server-1 2001:db8:34::2 user@host# set routing-instances trust-vr forwarding-options dhcp-relay dhcpv6 active-server-group server-1 user@host# set routing-instances trust-vr forwarding-options dhcp-relay dhcpv6 group relay-in-vr interface ge-0/0/3.0 user@host# set routing-instances trust-vr routing-options instance-import export_dhcp_server_route
-
Set the configuration to share routes between routing instances.
[edit ] user@host# set policy-options policy-statement export_dhcp_server_route term 1 from instance untrust-vr user@host# set policy-options policy-statement export_dhcp_server_route term 1 from route-filter 2001:db8:34::/64 exact user@host# set policy-options policy-statement export_dhcp_server_route term 1 then accept user@host# set policy-options policy-statement export_dhcp_server_route term 2 then reject user@host# set policy-options policy-statement import_relay_route_to_server_vr term 1 from instance trust-vr user@host# set policy-options policy-statement import_relay_route_to_server_vr term 1 from route-filter 2001:db8:12::/64 exact user@host# set policy-options policy-statement import_relay_route_to_server_vr term 1 then accept user@host# set policy-options policy-statement import_relay_route_to_server_vr term 2 then reject user@host# set routing-options static route 2001:db8:34::2/64 next-table untrust-vr.inet.0
Note:You can enable an SRX Series Firewall to function as a DHCPv6 local server. The DHCPv6 local server provides an IP address and other configuration information in response to a client request.
Procedure
Step-by-Step Procedure
To configure the security zone to allow the DHCPv6 Protocol:
-
Set the default security policy to permit all traffic.
[edit ] user@host# set security policies default-policy permit-all
-
Set all system services and protocols on interface ge-0/0/4.0.
[edit ] user@host# set security zones security-zone untrust interfaces ge-0/0/4.0 host-inbound-traffic system-services all user@host# set security zones security-zone untrust interfaces ge-0/0/4.0 host-inbound-traffic protocols all
-
Set all system services and protocols on interface ge-0/0/3.0.
[edit ] user@host# set security zones security-zone trust interfaces ge-0/0/3.0 host-inbound-traffic system-services all user@host# set security zones security-zone trust interfaces ge-0/0/3.0 host-inbound-traffic protocols all
Results
-
Result for Client-facing Support:
From configuration mode, confirm your configuration by entering the
show routing-instances command. If the output does not
display the intended configuration, repeat the configuration instructions in
this example to correct it.
[edit]
user@host# show routing-instances
trust-vr {
instance-type virtual-router;
interface ge-0/0/3.0;
}
-
Result for Server-Facing Support:
From configuration mode, confirm your configuration by entering the
show routing-instancescommand. If the output does not display the intended configuration, repeat the configuration instructions in this example to correct it.
[edit]
user@host# show routing-instances
untrust-vr {
instance-type virtual-router;
interface ge-0/0/4.0;
forwarding-options {
dhcp-relay {
forward-only-replies;
}
}
}
-
Result for DHCPv6 Local Server Support:
From configuration mode, confirm your configuration by entering the
show routing-instances,show policy-optionsandshow routing-optionscommands. If the output does not display the intended configuration, repeat the configuration instructions in this example to correct it.
[edit]
user@host# show routing-instances
trust-vr {
routing-options {
instance-import export_dhcp_server_route;
}
forwarding-options {
dhcp-relay {
server-group {
server-1 {
2001:db8:34::2;
}
}
active-server-group server-1;
group relay-in-vr {
interface ge-0/0/3.0;
}
}
}
}
untrust-vr {
routing-options {
static {
route 2001:db8:34::/64 next-hop 2001:db8:23::2;
}
instance-import import_relay_route_to_server_vr;
}
forwarding-options {
dhcp-relay {
server-group {
dummy-config;
}
}
}
}
[edit]
user@host# show policy-options
policy-statement export_dhcp_server_route {
term 1 {
from {
instance untrust-vr;
route-filter 2001:db8:34::/64 exact;
}
then accept;
}
term 2 {
then reject;
}
}
policy-statement import_relay_route_to_server_vr {
term 1 {
from {
instance trust-vr;
route-filter 2001:db8:12::/64 exact;
}
then accept;
}
term 2 {
then reject;
}
}
[edit]
user@host# show routing-options
static {
route 2001:db8:34::2/64 next-table untrust-vr.inet.0;
}
-
Result for Security Zone to Allow the DHCPv6 Protocol:
From configuration mode, confirm your configuration by entering the
show security policiesandshow security zonescommands. If the output does not display the intended configuration, repeat the configuration instructions in this example to correct it.
[edit]
user@host# show security policies
default-policy {
permit-all;
}
[edit]
user@host# show security zones
security-zone HOST {
interfaces {
all;
}
}
security-zone untrust {
interfaces {
ge-0/0/4.0 {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
}
}
}
security-zone trust {
interfaces {
ge-0/0/3.0 {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
}
}
}
If you are done configuring the device, enter commit from
configuration mode.
Inserting DHCPv6 Interface-ID Option (Option 18) In DHCPv6 Packets
You can configure DHCPv6 relay agent to insert the DHCPv6 Interface-ID (option 18) in the packets that the relay sends to a DHCPv6 server. You can configure the option 18 support at either the DHCPv6 global or group level.
When you configure option 18 support, you can optionally include the following additional information:
Prefix—Specify the
prefixoption to add a prefix to the interface identifier. The prefix can be any combination of hostname, logical system name, and routing instance name.Interface description—Specify the
use-interface-descriptionoption to include the textual interface description instead of the interface identifier. You can include either the device interface description or the logical interface description.Option 82 Agent Circuit ID suboption (suboption 1)—Specify the
use-option-82option to include the DHCPv4 Option 82 Agent Circuit ID suboption (suboption 1). This configuration is useful in a dual-stack environment, which has both DHCPv4 and DHCPv6 subscribers that reside over the same underlying logical interface. The router checks for the option 82 suboption 1 value and inserts it into the outgoing packets. If no DHCPv4 binding exists or if the binding does not have an option 82 suboption 1 value, the router sends the packets without adding an option 18.
If you specify one of the optional configurations, and the specified information does not exist (for example, there is no interface description), DHCPv6 relay ignores the optional configuration and inserts the default interface identifier in the packets.
To insert the DHCPv6 Interface-ID option (option 18) in DHCPv6 packets:
See Also
Inserting DHCPv6 Remote-ID Option (Option 37) In DHCPv6 Packets
Starting in Junos OS Release 14.1, you can configure DHCPv6 relay agent to insert DHCPv6 Remote-ID (option 37) in the packets that the relay sends to a DHCPv6 server. You can configure option 37 support at either the DHCPv6 global or group level.
When you configure option 37 support, you can optionally include the following information:
Prefix—Specify the
prefixoption to add a prefix to the interface identifier. The prefix can be any combination of hostname, logical system name, and routing instance name.Interface description—Specify the
use-interface-descriptionoption to include the textual interface description instead of the interface identifier. You can include either the device interface description or the logical interface description.Option 82 Agent Remote-ID suboption (suboption 2)—Specify the
use-option-82option to use the value of the DHCPv4 option 82 Remote-ID suboption (suboption 2). This configuration is useful in a dual-stack environment, which has both DHCPv4 and DHCPv6 subscribers that reside over the same underlying logical interface. The router checks for the option 82 suboption 2 value and inserts it into the outgoing packets.
If you specify one of the optional configurations, and the specified information does not exist (for example, there is no interface description), DHCPv6 relay ignores the optional configuration and inserts the default interface identifier in the packets.
To insert the DHCPv6 Remote-ID option (option 37) in DHCPv6 packets:
See Also
Inserting the DHCPv6 Client MAC Address Option (Option 79) In DHCPv6 Packets
The incremental deployment of IPv6 to existing IPv4 networks can result in a dual-stack network environment in which devices act as both DHCPv4 and DHCPv6 clients. In dual-stack scenarios, operators need to be able to associate DHCPv4 and DHCPv6 messages with the same client interface, based on an identifier that is common to the interface.
You can configure a DHCPv6 relay agent to insert the DHCPv6 client MAC address in the packets that the relay sends to a DHCPv6 server. The client MAC address is used to associate DHCPv4 and DHCPv6 messages with the same client interface.
In addition to associating DHCPv4 and DHCPv6 messages from a dual-stack client, having the client MAC address in DHCPv6 packets provides additional information for event debugging and logging related to the client at the relay agent and the server.
When DHCPv6 option 79 is enabled, the DHCPv6 relay agent reads the source MAC address of DHCPv6 Solicit and DHCPv6 Request messages that it receives from a client. The relay agent encapsulates the Solicit and Request messages within a DHCPv6 Relay-Forward message, and inserts the client MAC address as option 79 in the Relay-Forward header before relaying the message to the server.
If the DHCPv6 packet already has a Relay-Forward header, the DHCPv6 relay agent adds the client MAC address if the packet meets the following conditions: the packet has only one Relay-Forward header, the Relay-Forward header was added by an LDRA, and the Relay-Forward header does not already include option 79 information.
You can also configure DHCPv6 option 79 for a lightweight DHCPv6 relay agent (LDRA). An LDRA resides on the same IPv6 link as the DHCPv6 client and relay agent or server and acts as a layer 2 relay agent, without performing the routing function necessary to forward messages to a server or relay agent that resides on a different IPv6 link.
[edit] user@host# set forwarding-options dhcp-relay dhcpv6 relay-agent-option-79
To configure DHCPv6 option 79 for an LDRA (layer 2):
[edit] user@host# set vlans vlan-name forwarding-options dhcp-security dhcpv6-options option-79
See Also
Verifying and Managing DHCPv6 Relay Configuration
Purpose
View or clear address bindings or statistics for extended DHCPv6 relay agent clients:
Action
To display the address bindings for extended DHCPv6 relay agent clients:
user@host> show dhcpv6 relay binding
To display extended DHCPv6 relay agent statistics:
user@host> show dhcpv6 relay statistics
To clear the binding state of DHCPv6 relay agent clients:
user@host> clear dhcpv6 relay binding
To clear all extended DHCPv6 relay agent statistics:
user@host> clear dhcpv6 relay statistics
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
