DHCP Snooping
Dynamic Host Configuration Protocol (DHCP) snooping enhances network security by verifying DHCP messages from untrusted devices that are connected to the router, switch, or firewall and prevents unauthorized DHCP servers from sending DHCPOFFER packets on untrusted ports.
DHCP Snooping Support
Dynamic Host Configuration Protocol (DHCP) is a network management protocol used in TCP/IP networks to dynamically assign IP addresses and other related configuration information to network devices.
How DHCP Snooping Works
Dynamic Host Configuration Protocol (DHCP) dynamically allocates IP addresses to devices, leasing addresses that can be reused when no longer needed. Hosts or end devices that require IP addresses through DHCP must communicate with a DHCP server across the LAN.
The following illustration shows the DHCP snooping process.
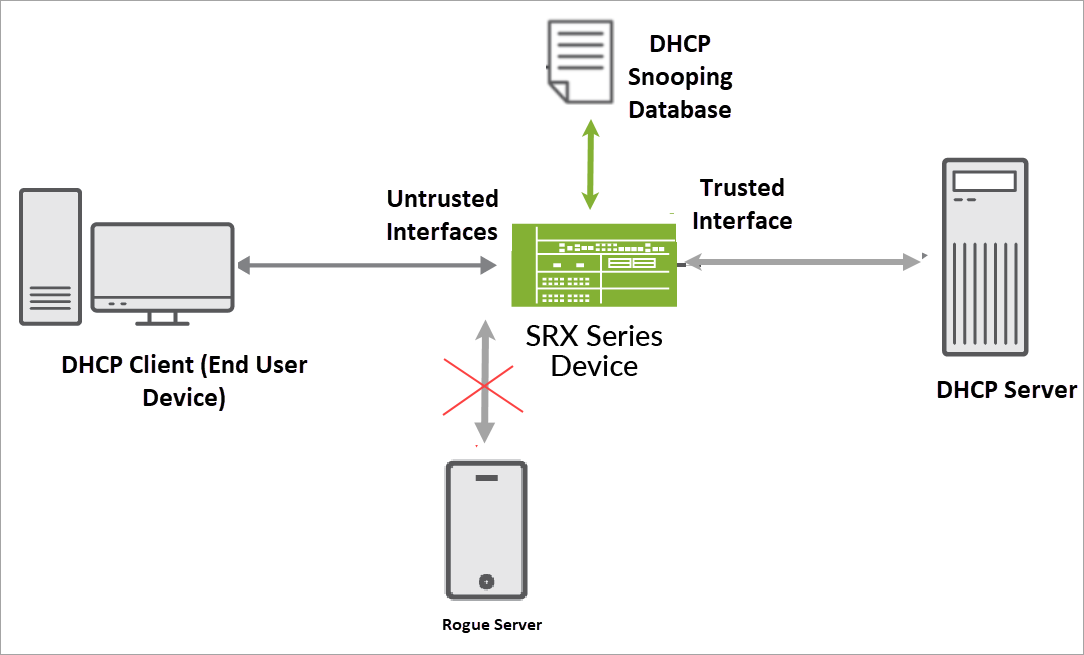
In the topology, an end user device connects to a Junos OS device (router, switch, or firewall). The Junos OS device connects to both the DHCP client and the DHCP server. The Junos OS device configured as a DHCP relay agent operates as the interface between DHCP clients and the DHCP server. This Junos OS device inspects DHCP packets. The DHCP server assigns IP addresses to clients.
The DHCP snooping feature on a Junos OS device performs the following actions:
- Validates DHCP messages received from untrusted sources and filters out invalid messages.
- Extracts the IP address leased to each client and builds a database. The DHCP snooping database (or binding table) includes information about the IP address, MAC address, and VLAN of each DHCP client.
- Uses the DHCP snooping binding table to validate subsequent requests from untrusted hosts. By verifying that DHCP requests are coming from trusted sources, the Juniper device can ensure that only valid DHCP requests are processed.
In this way, DHCP snooping acts as a guardian of network security by keeping track of valid IP addresses that a trusted DHCP server (a server connected to a trusted network port) assigns to downstream network devices.
DHCPv6 Relay Agent Snooping
The DHCPv6 relay agent enhances the DHCP relay agent by providing support in an IPv6 network. The DHCPv6 relay agent passes messages between the DHCPv6 client and the DHCPv6 server, similar to the way DHCP relay agent supports an IPv4 network. In a multi-relay topology that has multiple DHCPv6 relay agents between the client and the server, snooping enables the intervening relay agents to correctly process unicast traffic from the client and forward it to the server. Snooping in this topology involves these actions:
- The DHCPv6 relay agent snoops incoming unicast DHCPv6 packets using a filter with UDP port 547, which is the DHCPv6 UDP server port, on a per-forwarding table basis.
- The DHCPv6 relay agent then processes the packets intercepted by the filter and forwards the packets to the DHCPv6 server.
Benefits of DHCP Snooping
- DHCP snooping can provide an additional security layer by filtering IP addresses. The filtering process evaluates network traffic to allow communication from verified and valid IP addresses.
- DHCP snooping can prevent rogue DHCP activity in the network by filtering out DHCP packets that are arriving on the wrong ports, or with incorrect contents.
Example: Configuring DHCP Snooping Support for DHCP Relay Agent
This example shows how to configure DHCP snooping support for DHCP relay agent.
Requirements
Configure DHCP relay agent. See Extended DHCP Relay Agent Overview.
Overview
In this example, you configure DHCP snooping support for DHCP relay agent by completing the following operations:
Override the default DHCP snooping configuration and enable DHCP snooping support for the interfaces in group frankfurt.
Configure DHCP relay agent to forward snooped packets to only configured interfaces.
Configuration
Procedure
Step-by-Step Procedure
To configure DHCP relay support for DHCP snooping:
Specify that you want to configure DHCP relay agent.
[edit] user@host# edit forwarding-options dhcp-relay
Specify the named group of interfaces on which DHCP snooping is supported.
[edit forwarding-options dhcp-relay] user@host# edit group frankfurt
Specify the interfaces that you want to include in the group. DHCP relay agent considers these as the configured interfaces when determining whether to forward or drop traffic.
[edit forwarding-options dhcp-relay group frankfurt] user@host# set interface fe-1/0/1.3 upto fe-1/0/1.9
Specify that you want to override the default configuration for the group.
[edit forwarding-options dhcp-relay group frankfurt] user@host# edit overrides
Enable DHCP snooping support for the group.
[edit forwarding-options dhcp-relay group frankfurt overrides] user@host# set allow-snooped-clients
Return to the
[edit forwarding-options dhcp-relay]hierarchy level to configure the forwarding action and specify that DHCP relay agent forward snooped packets on only configured interfaces:[edit forwarding-options dhcp-relay group frankfurt overrides] user@host# up 2
Enable DHCP snooped packet forwarding for DHCP relay agent.
[edit forwarding-options dhcp-relay] user@host# edit forward-snooped-clients
Specify that snooped packets are forwarded on only configured interfaces (the interfaces in group
frankfurt).[edit forwarding-options dhcp-relay forward-snooped-clients] user@host# set configured-interfaces
Results
From configuration mode, confirm your configuration
by entering the show forwarding-options command. If the
output does not display the intended configuration, repeat the instructions
in this example to correct it. The following output also shows a range
of configured interfaces in group frankfurt.
[edit]
user@host# show forwarding-options
dhcp-relay {
forward-snooped-clients configured-interfaces;
group frankfurt {
overrides {
allow-snooped-clients;
}
interface fe-1/0/1.3 {
upto fe-1/0/1.9;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Enable DHCP Snooping
On a Junos OS device, the DHCP snooping feature is automatically enabled when you configure DHCP security, DHCP relay, DHCP server settings for a specific VLAN, or routing instance.
Note that on a Junos OS device, you cannot configure DHCP snooping as an independent feature.
Junos OS enables DHCP snooping on a switch, router, or firewall when you configure any one or all of the following features:
- DHCP relay or DHCP local server options at the following hierarchy levels:
- The
dhcp-relaystatement at the[edit forwarding-options]or[edit routing-instances routing-instance-name forwarding-options]hierarchy level. - The
dhcp-local-serverstatement at the[edit system services]or[edit routing-instances routing-instance-name system services]hierarchy level.Note:When you configure DHCP relay, use the
forward-onlystatement unless you need subscriber management or class-of-service (CoS). Theforward-onlyconfiguration forwards specified DHCP client packets, without creating a subscriber session.
- The
-
DHCP security on a specific VLAN activates DHCP snooping for that VLAN:
The dhcp-security statement at the
[edit vlans vlan-name forwarding-options]hierarchy level for switches. - The
dhcp-securitystatement at the[edit bridge-domains bridge-domain-name forwarding-options dhcp-security]hierarchy level for routers. -
You can configure the DHCP local server to forward or drop snooped packets for all interfaces, only configured interfaces, or only non-configured interfaces. See Configuring DHCP Snooped Packets Forwarding Support for DHCP Local Server for more details.
Forward DHCP Snooped Packets for DHCP Relay Agent
You can further refine the control over DHCP snooping behavior using the
forward-snooped-clients statement.
You can use the forward-snooped-clients statement to decide whether
the monitored traffic should be forwarded or dropped based on the interface
configuration.
- To assess the snooped traffic and later decide whether to forward or drop the
traffic, configure the
forward-snooped-clientsstatement at the[edit forwarding-options dhcp-relay] hierarchy level.You can set the
forward-snooped-clientsoption for the following scenarios:- All interfaces: Applies the action to all interfaces.
- Configured interfaces: Applies the action only to the interfaces configured as part of an interface group.
- Non-configured interfaces: Applies the action only to the interfaces that are not a part of an interface group.
- To forward or drop the snooped packets, configure
allow-snooped-clientsorno-allow-snooped-clients, respectively, with theforward-snooped-clientsoption.- When you configure
allow-snooped-clients, snooped packets are forwarded if a valid subscriber is associated with them. - When you configure
no-allow-snooped-clients, snooped packets are dropped even if a valid subscriber is associated with them.
- When you configure
To learn more about the action that the device takes on DHCP snooped packets based on
the combination of allow-snooped-clients or
no-allow-snooped-clients with
forward-snooped-clients, see Table 1 and Table 2.
Table 1 shows the action
that the device takes on the packets snooped by the DHCP relay agent when you
configure allow-snooped-clients with
forward-snooped-clients option.
|
Configuration Applies To |
Action on Configured Interfaces |
Action on Non-Configured Interfaces |
|---|---|---|
|
All interfaces |
Forwarded |
Forwarded |
|
Configured interfaces |
Forwarded |
Dropped |
|
Non-configured interfaces |
Snooped DHCP packets create subscriber entries in the DHCP snooping database. |
Forwarded |
|
No configuration |
Snooped DHCP packets create subscriber entries in the DHCP snooping database. |
Dropped |
Table 2 shows the action
that the device takes on the packets snooped by the DHCP relay agent when you
configure no-allow-snooped-clients with
forward-snooped-clients.
|
Configuration Applies To |
Action on Configured Interfaces |
Action on Non-Configured Interfaces |
|---|---|---|
|
All interfaces |
Dropped | Forwarded |
|
Configured interfaces |
Dropped | Dropped |
|
Non-configured interfaces |
Dropped | Forwarded |
|
No configuration |
Dropped | Dropped |
During DHCP relay agent snooping, the device relies on its global configuration to decide whether to forward or discard BOOTREPLY packets. Additionally, during a lease renewal, a BOOTPREQUEST packet might be unicast directly to the DHCP server, and this packet is also subject to snooping.
Table 3 shows the action
the device takes on the snooped BOOTREPLY packets.
| Configuration State | Action |
|---|---|
forward-snooped-clients not configured |
Snooped BOOTREPLY packets dropped if client is
not found |
forward-snooped-clients configured |
Snooped BOOTREPLY packets forwarded if client is
not found |
In both the default configuration and in configurations using the
forward-snooped-clients statement, the device forwards all DHCP
traffic on the hardware control plane to the routing plane of the routing instance
for interception of DHCP packets.
You can use the no-snoop option to disable the snooping filter for DHCP traffic.
When you configure the no-snoop option, DHCP traffic goes to the
hardware control plane but bypasses the routing plane, avoiding interception there.
DHCP Snooping Configuration
Sample Configuration of DHCP Snooped Packet Forwarding
We recommend that you read the DHCP User Guide and use a lab with DHCP traceoptions enabled to check and to understand the configuration.
