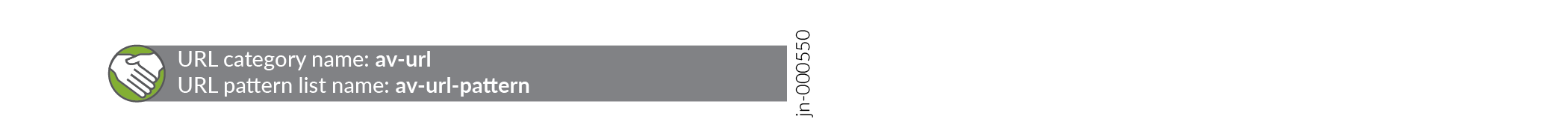Prevent Virus Attacks by Using J-Web Content Security Antivirus
Learn about Content Security antivirus protection and how to configure Content Security antivirus to prevent virus attacks on SRX Series Firewalls by using J-Web. The Content Security antivirus feature on the SRX Series Firewall scans network traffic to protect your network from virus attacks and to prevent virus spread.
Content Security Antivirus Overview
In today’s world, where cyber security threats are evolving and getting more sophisticated, protecting your network from virus attacks is extremely critical. The viruses, worms, and malware perform unwanted and malicious acts, such as damaging or deleting files, hacking personal data, affecting system performance, reformatting the hard disk, or using your computer to transmit viruses to other computers. The Content Security antivirus software acts like a first line of defense against such security threats and prevents the spread of viruses into your network. It protects your network from virus attacks, unwanted computer malwares, spywares, rootkits, worms, phishing attacks, spam attacks, trojan horses, and so on.
You must always ensure that the antivirus software and virus pattern database are up to date.
Starting in Junos OS 22.2R1:
-
In the J-Web GUI, UTM term is replaced with Content Security.
-
In Junos CLI commands, we continue to use the legacy term UTM for content security.
Juniper Networks offers the following Content Security antivirus solutions:
-
On-device antivirus protection
The on-device antivirus is an on-box solution. The on-device antivirus scan engine scans the data by accessing the virus pattern database that is locally stored on the device. It provides a full file-based antivirus scanning function that is available through a separately licensed subscription service.
Note:-
The on-device Express or Kaspersky scan engine is not supported from Junos OS Release 15.1X49-D10 onwards; however, it is still applicable for Junos OS Release 12.3X48.
-
Starting in Junos OS Release 18.4R1, SRX Series Firewalls support the Avira on-device antivirus scanning engine.
-
Avira on-device antivirus scanning engine is not supported on SRX300, SRX320, SRX340, SRX345, SRX380, and SRX550 HM devices.
-
-
Sophos antivirus protection
Sophos antivirus is an in-the-cloud antivirus solution. The virus pattern and malware database is located on external servers maintained by Sophos (Sophos Extensible List) servers. The Sophos antivirus scanner also uses a local internal cache to maintain query responses from the external list server. We offer the Sophos antivirus scanning as a less CPU-intensive alternative to the full file-based antivirus feature.
Benefits of Content Security Antivirus
-
The on-device antivirus solution:
-
Scans the application traffic locally without connecting to the Internet server to query whether the application traffic has virus.
-
Minimizes processing delays because the pattern database is locally stored and the scan engine is on-device.
-
-
The Sophos antivirus solution:
-
Avoids downloading and maintaining large pattern databases on the Juniper device because the virus pattern and malware database is located on external servers maintained by Sophos.
-
Improves lookup performance because the Sophos antivirus scanner uses a local internal cache to maintain query responses from the external list server.
-
Effectively prevents malicious content from reaching the endpoint client or server through the use of the Uniform Resource Identifier (URI) checking functionality.
-
Antivirus Workflow
- Scope
- Before You Begin
- Topology
- Video
- Sneak Peek – J-Web Content Security Antivirus Configuration Steps
Scope
Juniper Web (J-Web) Device Manager supports the Content Security antivirus solution on SRX Series Firewalls. In this example, you’ll use Sophos antivirus protection to do the following:
-
Scan HTTP and FTP traffic from a server (10.102.70.89) to your computer for virus attacks.
-
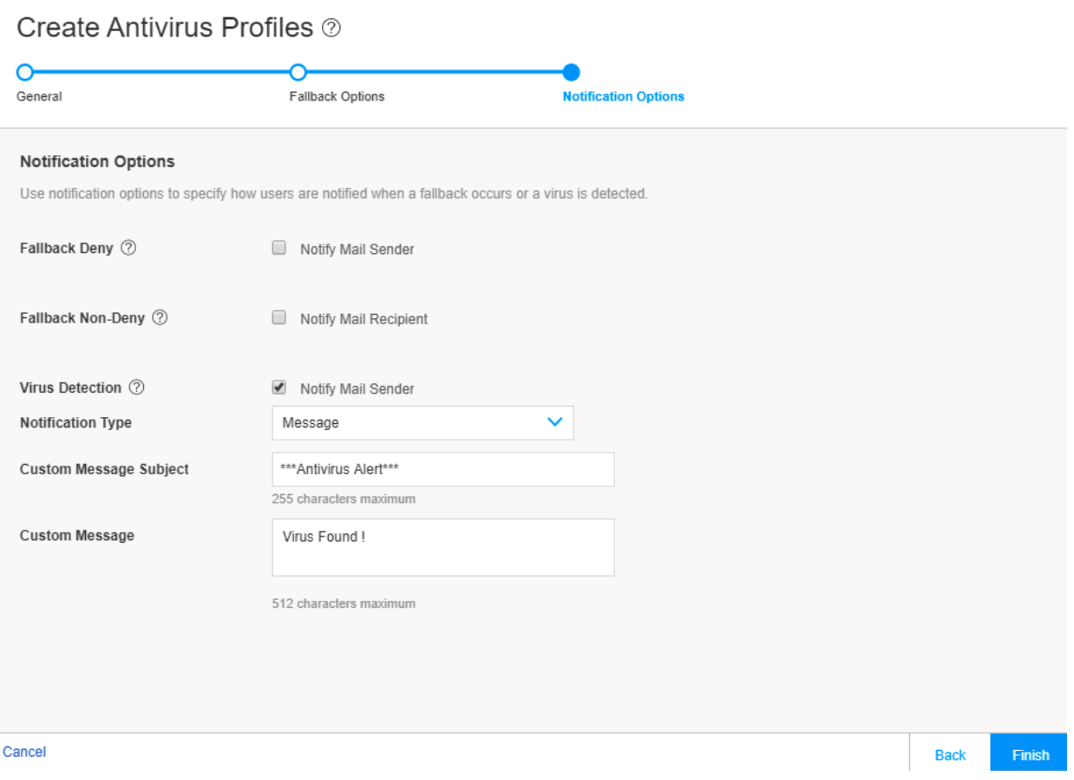
Define a custom message Virus Found! to be displayed when a virus is found while scanning the traffic.
-
Create Allowlist URLs (http://10.102.70.89) where AV scanning is skipped.
Note:Assumption is that you must be able to route to the example URLs.
Before You Begin
-
Install a Sophos antivirus license. See the Installation and Upgrade Guide, Licensing Administration Guide, and Licensing Guide.
-
Ensure that the SRX Series Firewall you use in this example runs Junos OS Release 22.2R1.
Note:Starting in Junos OS 22.2R1:
-
In the J-Web GUI, UTM term is replaced with Content Security.
-
In Junos CLI commands, we continue to use the legacy term UTM for content security.
-
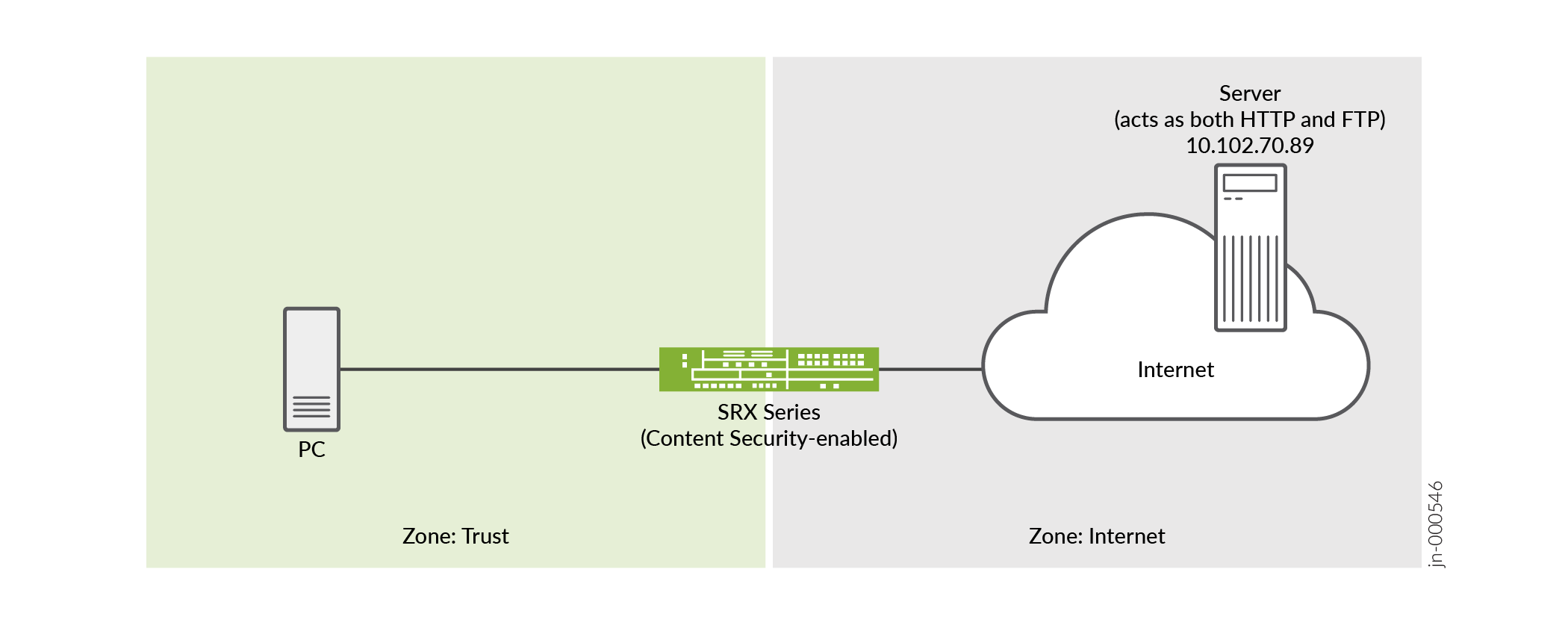
Topology
The topology used in this example comprises a PC connected to a Content Security-enabled SRX Series Firewall that has access to the Internet and a server. You'll use J-Web to scan the HTTP and FTP requests sent to the server with this simple setup. You’ll then use Sophos antivirus protection to prevent virus attacks from the Internet to your PC.
Video
See the following video to learn how to configure Content Security antivirus using J-Web.
Sneak Peek – J-Web Content Security Antivirus Configuration Steps
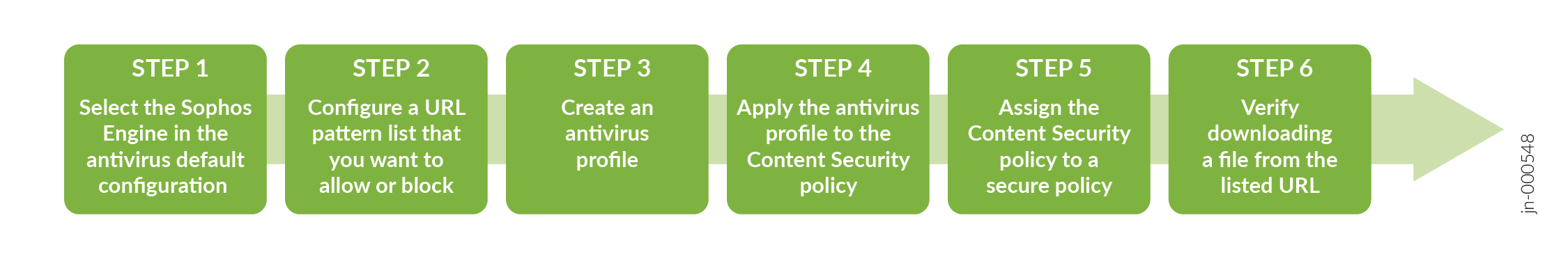
|
Step |
Action |
|---|---|
|
Step 1 |
Configure the Sophos engine in Default Configuration. Here, you first define the default engine as Sophos in Default Configuration. |
|
Step 2 |
Configure antivirus custom object. Here, you define the URL pattern list (allowlist) of URLs or addresses that will be bypassed by antivirus scanning. After you create the URL pattern list, you will create a custom URL category list and add the pattern list to it. |
|
Step 3 |
Configure an antivirus feature profile using the Sophos engine. After the default configuration, you define the parameters that will be used for virus scanning in the feature profile. Note:
You must configure DNS servers before creating the antivirus profiles. To configureDNS servers, go to Device Administration>Basic Settings>System Identity>DNS servers. |
|
Step 4 |
Create a Content Security policy for Sophos antivirus and apply the antivirus feature profile to the Content Security policy. Here, you use a Content Security policy to bind a set of protocols (for example, HTTP) to the Sophos Content Security feature profile. You can scan other protocols as well by creating different profiles or adding other protocols to the profile, such as imap-profile, pop3-profile, and smtp-profile. |
|
Step 5 |
Create a security policy for Sophos antivirus and assign the Content Security policy to the security policy. Here, you use the security firewall and feature profile settings to scan the traffic from the trust zone (trust) to the untrust zone (Internet). |
|
Step 6 |
Access a URL from the allowlist URL (http://10.102.70.89) and try to download a test virus file (eicar.txt) which is made available on the 10.102.70.89 server. |
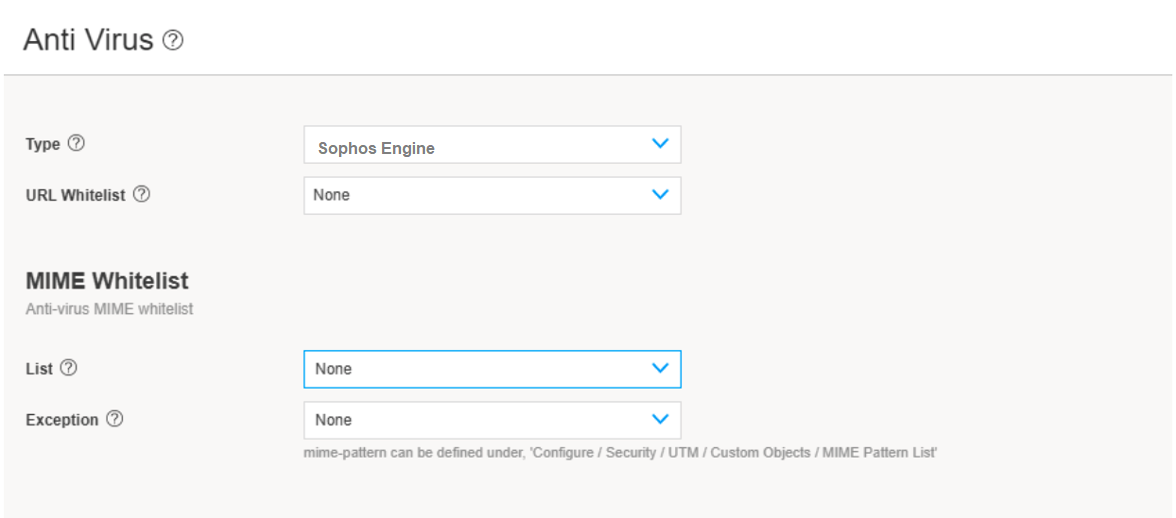
Step 1: Update Default Configuration for Antivirus
You are here (in the J-Web UI): Security Services>Content Security>Default Configuration.
In this step, you'll set up Sophos Engine as the default engine type.
To update the default antivirus profile:
Step 2: Configure Antivirus Custom Object
- Step 2a: Configure a URL Pattern List That You Want to Bypass
- Step 2b: Categorize the URLs That You Want to Allow
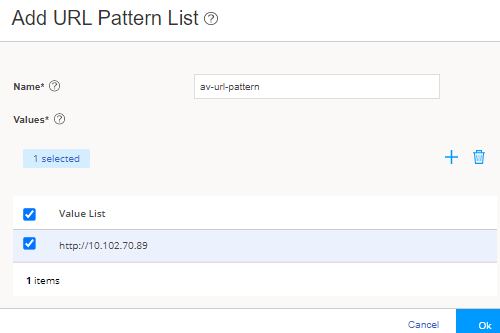
Step 2a: Configure a URL Pattern List That You Want to Bypass
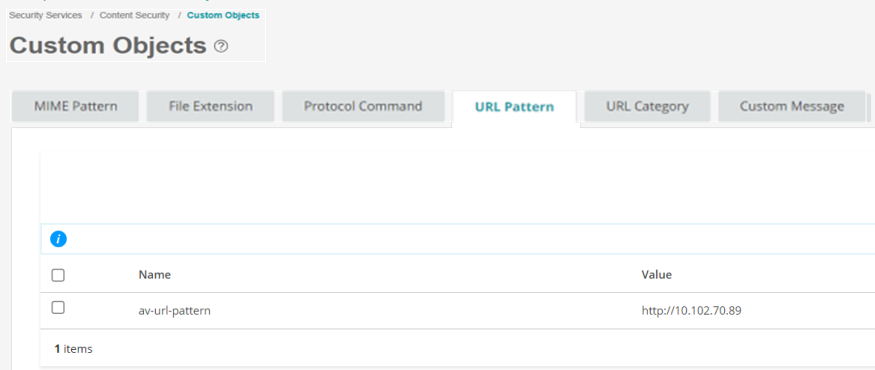
In this step, you define a URL pattern list (safelist) of URLs or addresses that will be bypassed by antivirus scanning.
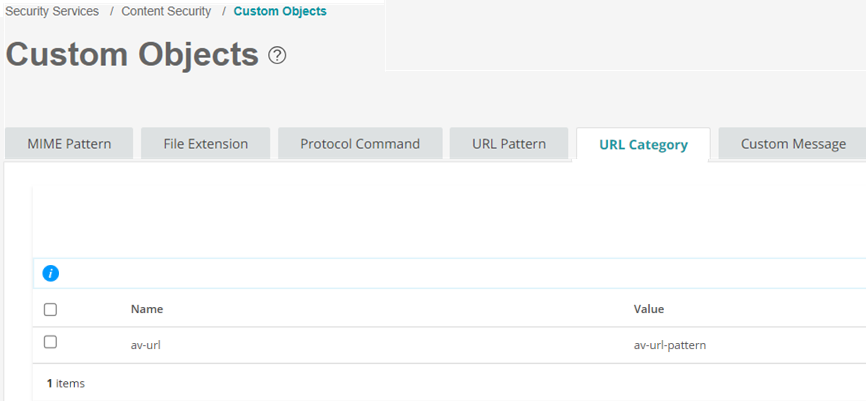
You are here (in the J-Web UI): Security Services>Content Security>Custom Objects.
To configure the safelist of URLs:
Good job! Here's the result of your configuration:
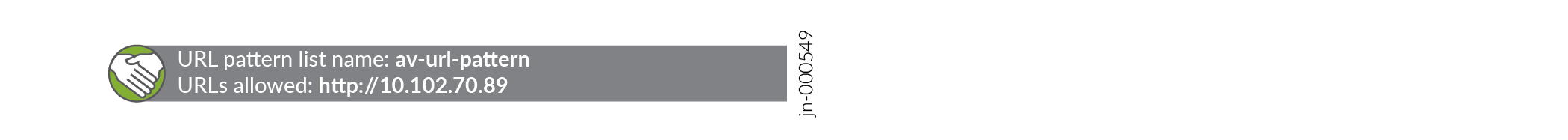
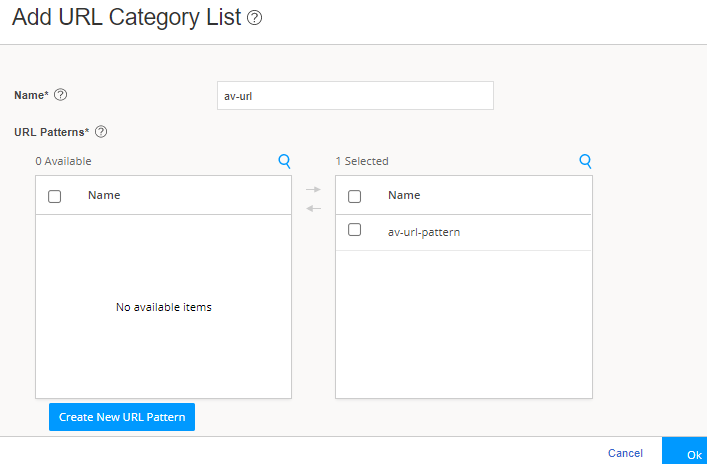
Step 2b: Categorize the URLs That You Want to Allow
You'll now assign the created URL pattern to a URL category list. The category list defines the action of mapping. For example, the Safelist category should be permitted.
You are here: Security Services>Content Security>Custom Objects.
To categorize URLs:
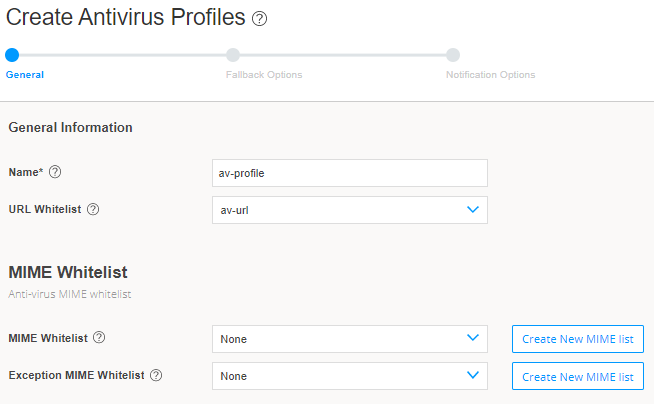
Step 3: Create Antivirus Profile
You are here: Security Services>Content Security>Antivirus Profiles.
In this step, you’ll create a new Content Security antivirus profile, refer the created URL objects (patterns and categories) to the profile, and specify the notification details.
To create the new antivirus profile:
Step 4: Apply the Antivirus Profile to a Content Security Policy
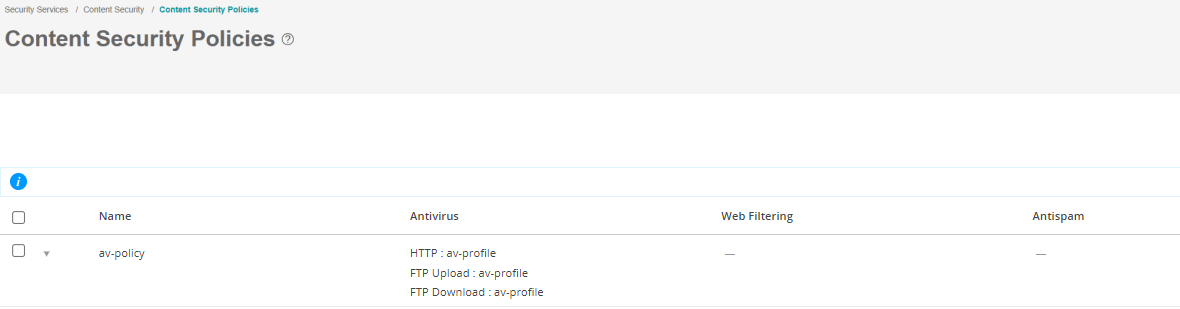
After you’ve created the antivirus feature profile, you configure a Content Security policy for an antivirus scanning protocol and attach this policy to the antivirus profile created in Step 3: Create Antivirus Profile. In this example, you’ll scan HTTP and FTP traffic for viruses.
You are here: Security Services>Content Security>Content Security Policies.
To create a Content Security policy:
Step 5: Assign the Content Security Policy to a Security Firewall Policy
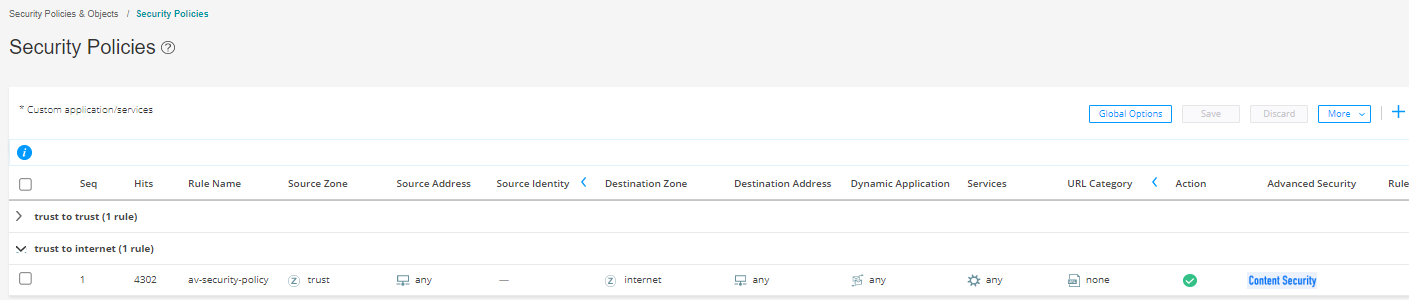
In this step, you create a firewall security policy that will cause traffic passing from the trust zone (trust) to the untrust zone (Internet) to be scanned by Sophos antivirus using the antivirus profile settings.
You haven’t yet assigned the Content Security configurations to the security policy from the trust zone to the Internet zone. Filtering actions are taken only after you assign the Content Security policy to security policy rules that act as the match criteria.
When the security policy rules are permitted, the SRX Series Firewall:
-
Intercepts an HTTP connection and extracts each URL (in the HTTP request) or IP address.
Note:For an HTTPS connection, antivirus is supported through SSL forward proxy.
-
Searches for URLs in the user-configured safelist under Antivirus (Security Services>Content Security>Default Configuration). Then, if the URL is in the user-configured safelist, the device permits the URL.
-
Allows or blocks the URL (if a category is not configured) based on the default action configured in the antivirus profile.
You are here: Security Policies & Objects>Security Policies.
To create security policy rules for the Content Security policy:
Step 6: Verify That Content Security Antivirus Is Working
Purpose
Verify that your configured Content Security antivirus is preventing virus attacks from the Internet server and allowing traffic from the Allowlist server.
Action
-
Open a browser, enter www.eicar.org, and click the download button to download a file using standard HTTP protocol.
Sorry! The SRX Series Firewall has blocked downloading the file and sent you a custom block message ***Antivirus Alert***- Virus Found!.
-
Open a browser, enter https://www.juniper.net, and click the download icon to download a PDF of Junos OS Day One+.
Good job! The file is successfully downloaded to your system.
-
Using the PC, send a HTTP request to http://10.102.70.89.
Good job! You can access the http://10.102.70.89 server.
-
Using the PC, send a FTP request to the 10.102.70.89 server to download the eicar.txt file. The eicar.txt file is a test virus file which is made available on the 10.102.70.89 server.
Sorry! The SRX Series Firewall has blocked downloading the file and sent you a custom block message ***Antivirus Alert***- Virus Found!.
Here is an example output when you try to download the eicar.txt file and the SRX Series Firewall sends a virus alert:
[centos-01 ~]$ ftp 10.102.70.89 Connected to 10.102.70.89 (10.102.70.89). 220 XX FTP server (Version 6.00LS) ready. Name (10.102.70.89:lab): root 331 Password required for root. Password: 230 User root logged in. Remote system type is UNIX. Using binary mode to transfer files. ftp> get eicar.txt local: eicar.txt remote: eicar.txt 227 Entering Passive Mode (10,102,70,89,197,55) 150 Opening BINARY mode data connection for 'eicar.txt' (70 bytes). netin: Connection reset by peer 426 10.102.70.89:21->10.0.1.1:36240 ***Antivirus Alert***- Virus Found!
Here is an example of the anti-virus statistics output when you find a threat:
[edit] root@srx> show security utm anti-virus statistics UTM Anti Virus statistics: Intelligent-prescreening passed: 0 MIME-whitelist passed: 0 URL-whitelist passed: 1 Session abort: 0 Scan Request: Total Clean Threat-found Fallback 2 0 1 0 Fallback: Log-and-Permit Block Permit Engine not ready: 0 0 0 Out of resources: 0 0 0 Timeout: 0 0 0 Maximum content size: 0 0 0 Too many requests: 0 0 0 Decompress error: 0 0 0 Others: 0 0 0
What’s Next?
|
If you want to |
Then |
|---|---|
|
Monitor Content Security antivirus details and statistics |
In J-Web, go to Monitor>Security Services>Content Security>Anti Virus. |
|
Generate and view reports on URLs allowed and blocked |
To generate and view reports:
|
|
Learn more about Content Security features |
Sample Configuration Output
In this section, we present samples of configurations that block virus attacks from the websites defined in this example.
You configure the following Content Security configurations at the [edit
security utm] hierarchy level.
Creating custom objects at the [edit security utm] hierarchy
level:
custom-objects {
url-pattern {
av-url-pattern {
value http://10.102.70.89 ;
}
}
custom-url-category {
av-url {
value av-url-pattern;
}
}
}
Creating the antivirus profile at the [edit security utm] hierarchy
level:
default-configuration {
anti-virus {
type sophos-engine;
}
}
feature-profile {
anti-virus {
profile UTM-LB-AV {
notification-options {
virus-detection {
type message;
notify-mail-sender;
custom-message “Virus-Found!”;
custom-message-subject “***Antivirus Alert***”;
}
}
}
}
}
Creating the Content Security policy:
utm-policy av-policy {
anti-virus {
http-profile av-profile;
ftp {
upload-profile av-profile;
download-profile av-profile;
}
}
}
Creating rules for a security policy at the [edit security policies]
hierarchy level.:
from-zone trust to-zone internet {
policy av-security-policy {
match {
source-address any;
destination-address any;
application any;
}
then {
permit {
application-services {
utm-policy av-policy;
}
}
}
}
}