Set Up Secure Edge Connector with Juniper Secure Edge (Manual Provisioning)
Follow this workflow for help with every step of the workflow to manually provision Juniper® Secure Edge.
The Juniper Mist™ cloud works with Juniper® Secure Edge to perform traffic inspection from edge devices by using the Secure Edge connector feature. This feature allows the Juniper® Session Smart™ Routers, deployed as WAN edge device, to send a portion of traffic to Juniper Secure Edge for an inspection.
Secure Edge capabilities are all managed by Juniper Security Director Cloud, Juniper’s simple and seamless management experience delivered in a single user interface (UI).
For more information, see Juniper Secure Edge.
Configuration Overview
In this task, you send the Internet-bound traffic from the LAN side of a spoke or hub device to Secure Edge for an inspection before the traffic reaches Internet.
To perform traffic inspection by Secure Edge:
-
In Juniper Security Director Cloud, create and configure the service locations, IPsec profiles, sites, and policies for Secure Edge. These are the cloud-based resources that provide security services and connectivity for the WAN edge devices.
-
In Mist Cloud, create and configure the WAN edge devices (Session Smart Routers or SRX Series Firewalls), that connect to the LAN networks. These are the physical devices that provide routing, switching, and SD-WAN capabilities for the branches or campuses.
-
In Mist WAN-Edge, create and configure the Secure Edge tunnels that connect the WAN edge devices to the service locations. These are the IPsec tunnels that provide secure and reliable transport for the traffic that needs to be inspected by Secure Edge.
-
In Mist Cloud, assign the Secure Edge tunnels to the sites or device profiles that correspond to the WAN edge devices. This enables the traffic steering from the LAN networks to the Secure Edge cloud based on the defined data policies and other match criteria.
Topics in the following table present the overview information you need to use the cloud-based security of Secure Edge with the Juniper Mist™ cloud.
| Step | Task | Description |
| 1 | Access Juniper Security Director Cloud and Check Active Subscriptions | Access Juniper Security Director Cloud, go to your organization account, and check Secure Edge subscriptions. The subscription entitles you to configure Secure Edge services for your deployments. |
| 2 | Configure a Service Location in Juniper Security Director Cloud |
Create service locations. This is where the vSRX-based VPN gateways creates secure connections between different networks. |
| 3 | Generate Device Certificates in Juniper Security Director Cloud | Generate digital certificates for Juniper Secure Edge to establish secure communications between Secure Edge and user endpoints. |
| 4 | Create an IPsec Profile in Juniper Security Director Cloud | Create IPsec profiles to establish IPsec tunnels for communication between the WAN edge devices on your Juniper Mist cloud network with Secure Edge instance. |
| 5 | Create a Site in Juniper Security Director Cloud | Create a site that hosts a WAN edge device (Session Smart Router or SRX Series Firewall). The traffic from the device is forwarded to the Secure Edge instance through a secure tunnel for an inspection. |
| 6 | Deploy a Secure Edge Policy in Juniper Security Director Cloud | Configure policies that define the security rules and actions for the traffic originating from or destined to the site. |
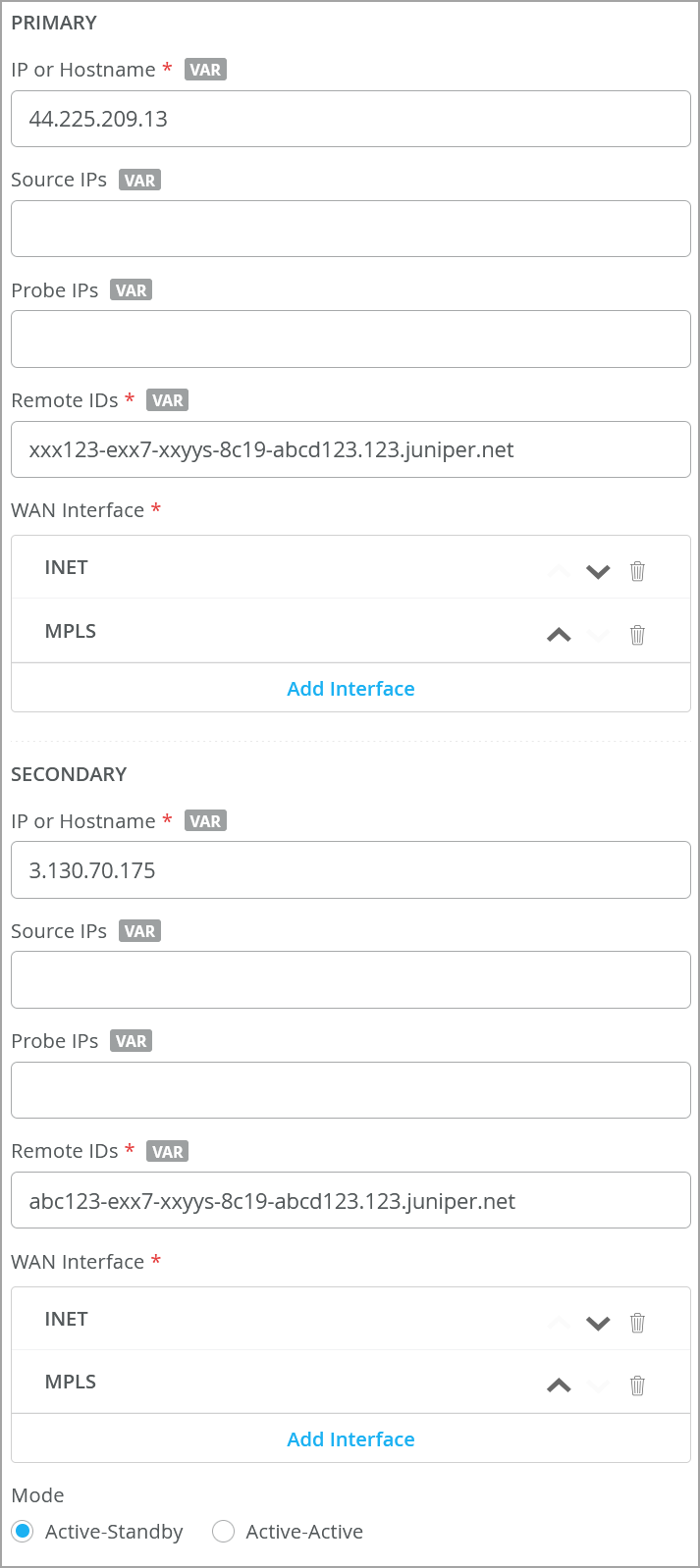
| 7 | Get IPsec Tunnel Configuration Parameters to Apply in Juniper Security Director Cloud | Note down the details such as service location IP or hostname, the IPsec profile name, and the pre-shared key. You need these details to set up IPsec tunnels from Juniper Mist side. |
| 8 | Create Secure Edge Connectors in the Juniper Mist Cloud Portal | Create Secure Edge connectors in the Juniper Mist cloud portal. This task completes the configuration on the Mist cloud side of the tunnels to establish an IPsec tunnel between WAN edge device managed by Mist and the Secure Edge instance. |
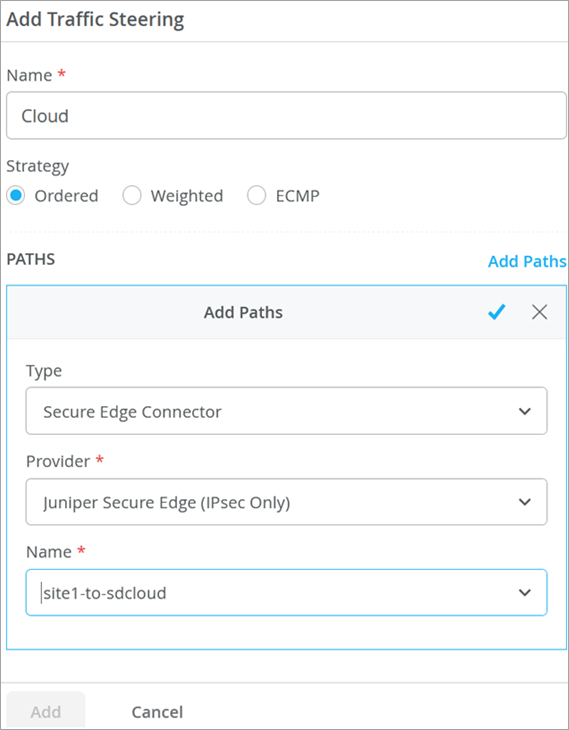
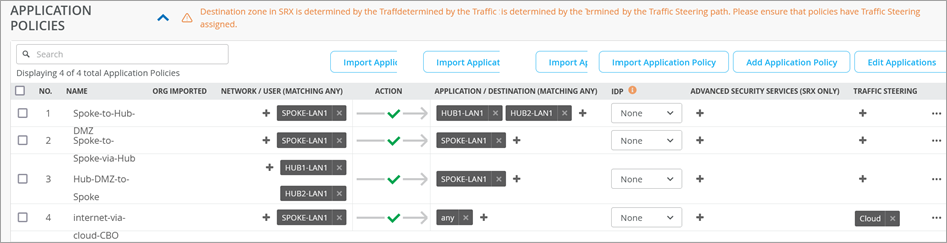
| 9 | Modify an Application Policy | Create a new or change an existing application policy to direct the traffic from WAN edge device to the Internet through Juniper Security Director Cloud instead of going through a hub for centralized access. |
| 10 | Verify the Configuration | Confirm if your configuration is working by checking the
established IPsec tunnels in:
|
Before You Begin
-
Read about the Juniper® Secure Edge subscription requirements. See Juniper Secure Edge Subscriptions Overview.
-
Ensure that you have completed the prerequisites to access the Juniper Security Director Cloud Portal . See Prerequisites.
- Create Your Secure Edge Tenant. See Create Your Secure Edge Tenant.
- We assume that you have adopted and configured the Session Smart Router or SRX Series Firewall deployed as WAN edge device in Juniper Mist Cloud.
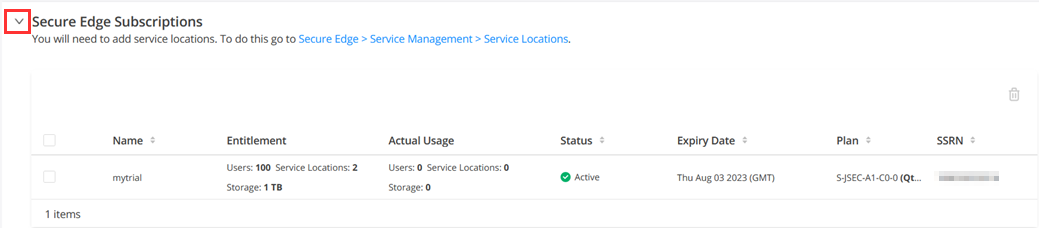
Access Juniper Security Director Cloud and Check Active Subscriptions
A tenant in Juniper Secure Edge is an organization account that you create to access the Juniper Security Director Cloud portal and manage your Secure Edge services. A tenant is associated with a unique e-mail address and a subscription plan. A tenant can have multiple service locations, which are vSRX based VPN gateways hosted in a public cloud for your organization.
A tenant can have one or more service locations, which are the connection points for end users. To create a tenant, you need to have an account on Juniper Security Director Cloud. See Create Your Secure Edge Tenant for details.
After you create your Secure Edge tenant in the Juniper Security Director Cloud portal, access the portal and check your subscriptions.
To access Juniper Security Director Cloud and check active subscriptions:
Configure Service Locations
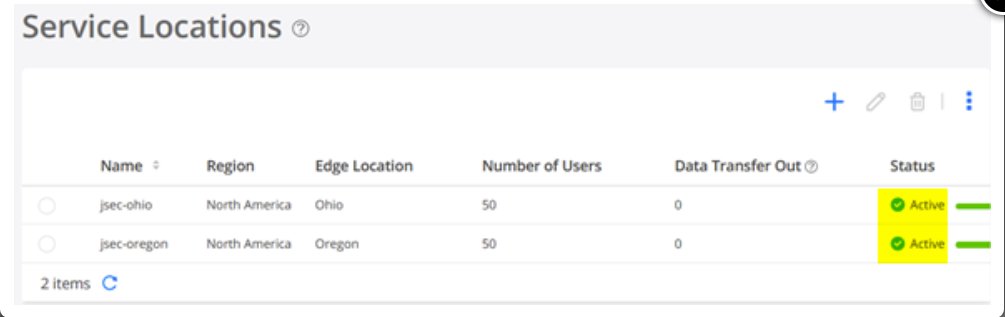
After ensuring that you have an active license to Juniper Security Director Cloud, you configure a service location. This step is your first main task in setting up a Secure Edge connector for Session Smart Routers.
A service location in Juniper Security Director Cloud is also known as POP (point of presence) and represents a Juniper® Secure Edge instance in a cloud location. The service location is the connection (access) point for both on-premises and roaming users.
Service locations are places where vSRX creates secure connections between different networks using a public cloud service. The public IP address (unique per tenant and service location) is used to:
-
Set up an IPsec tunnel between the branch device and the Juniper Security Director Cloud.
-
Centrally distribute the traffic when the destination is on the Internet.
To configure a service location in Juniper Security Director Cloud:
Generate Device Certificates in Juniper Security Director Cloud
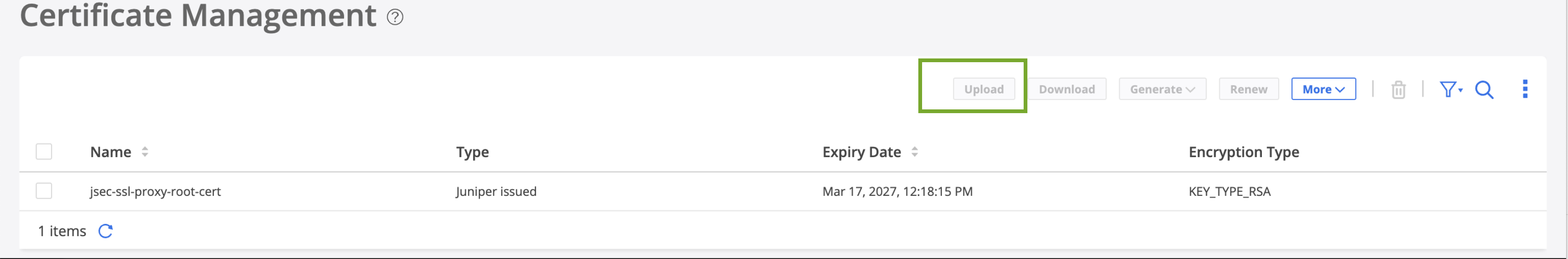
Now that you have configured service locations in Juniper Security Director Cloud, you generate device certificates to secure network traffic.
You use a Transport Layer Security/Secure Sockets Layer (TLS/SSL) certificate to establish secure communications between Secure Edge and WAN edge devices. All the client browsers on your network must trust the certificates signed by the Juniper Networks and SRX Series Firewalls to use an SSL proxy.
In Juniper Security Director Cloud, you have the following choices for generating certificates:
-
Create a new certificate signing request (CSR), and your own certificate authority (CA) can use the CSR to generate a new certificate.
-
Select the option to have Juniper Networks create a certificate.
This topic describes how to generate a TLS/SSL certificate. How you import and use the certificate depends on your company's client-management requirements and is beyond the scope of this topic.
To generate device certificates in Juniper Security Director Cloud:
Create an IPsec Profile in Juniper Security Director Cloud
After you generate the certificates to establish secure communications between Secure Edge and WAN edge devices, you're ready to create IPsec profiles.
IPsec profiles define the parameters with which an IPsec tunnel is established when the WAN edge devices on your Juniper Mist™ cloud network start communicating with your Secure Edge instance.
To create an IPsec profile in Juniper Security Director Cloud:
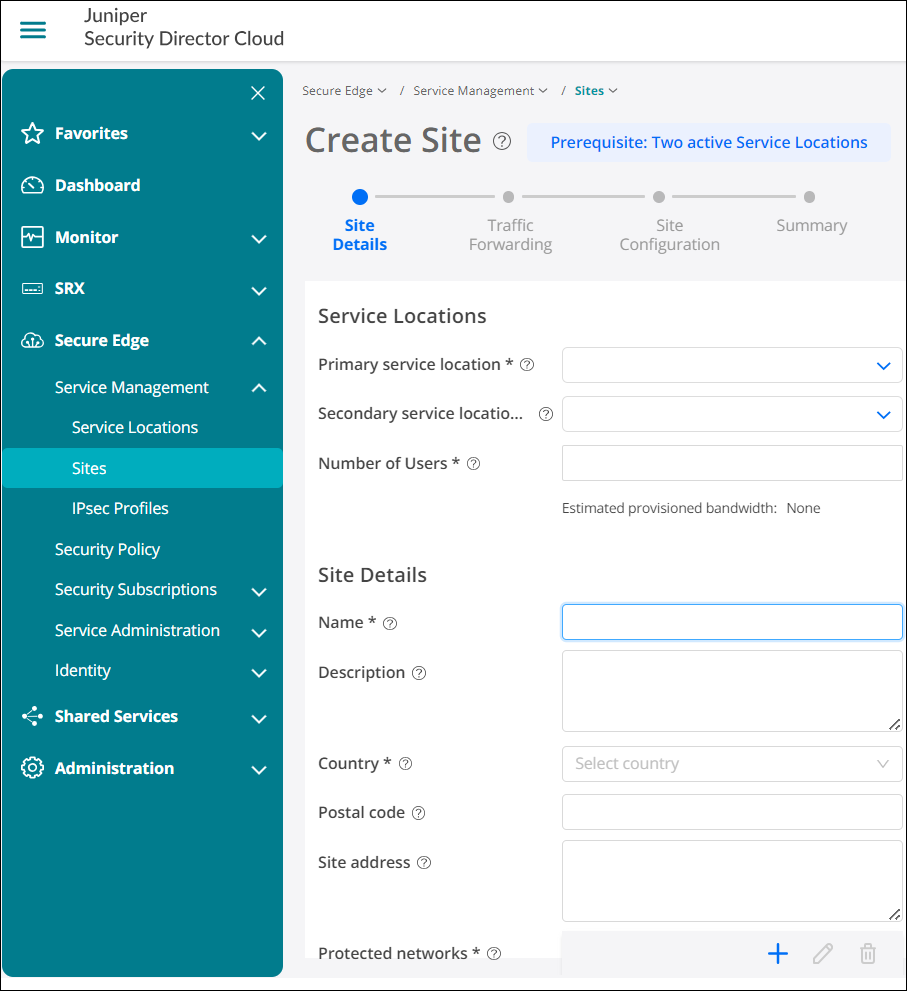
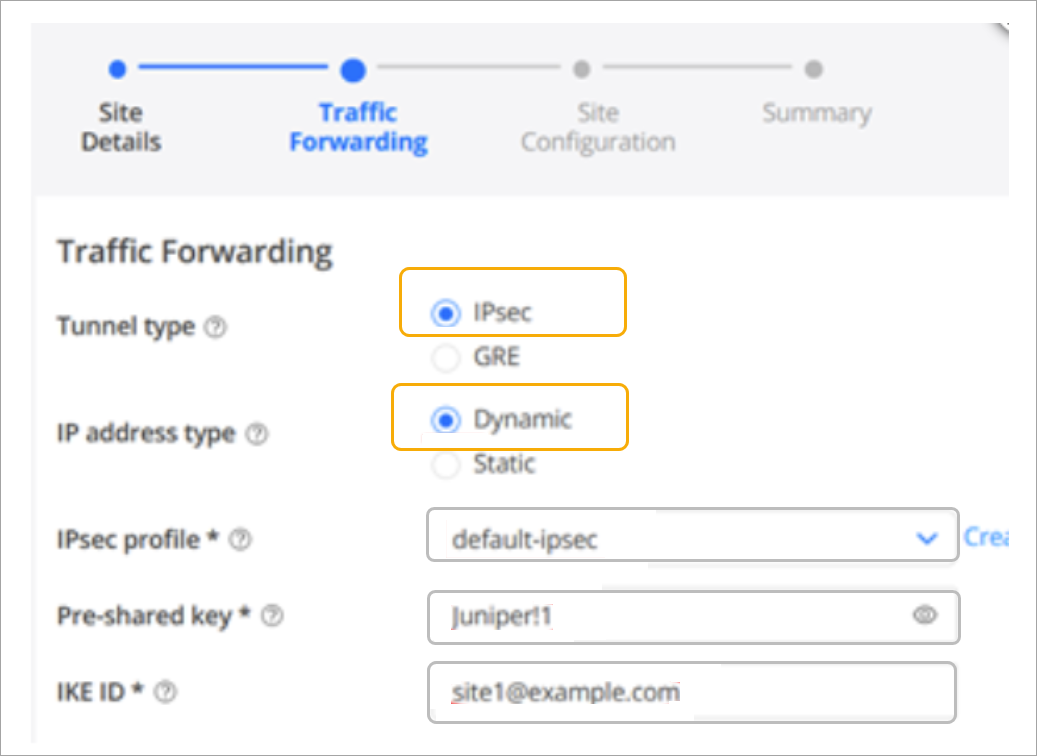
Create a Site in Juniper Secure Edge Cloud
You have now created IPsec profiles. These profiles define the parameters for the IPsec tunnel between WAN edge devices on your Juniper Mist™ cloud network and your Secure Edge instance.
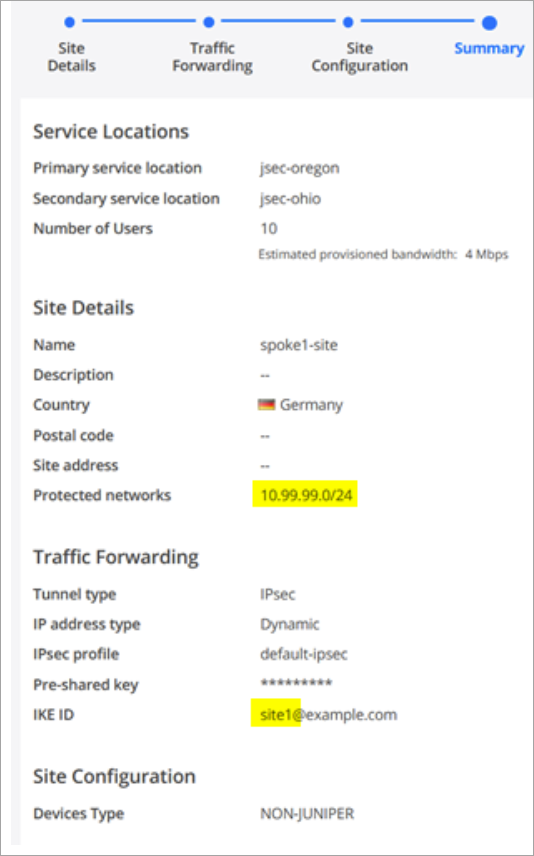
At this point, you need to create a site in Juniper Security Director Cloud. A site represents a location that hosts a WAN edge device. The traffic from the WAN edge device is forwarded to the Secure Edge instance through a secure tunnel, and then inspected and enforced by the Secure Edge cloud services.
You can configure to forward some or all of the Internet-bound traffic from customer sites to the Juniper Secure Edge cloud through generic routing encapsulation (GRE) or IPsec tunnels from the WAN edge devices at the site.
Overlapping branch addresses are not supported to the same POP within Secure Edge when using a stateful firewall at branch locations. Reverse path traffic to these overlapping IPs will be routed using equal-cost multipath (ECMP) across all connections. Traffic is routed using ECMP rather than per-session routing to the interface from which traffic originated. Consider reverse path traffic through ECMP when you configure the protected networks for a site.
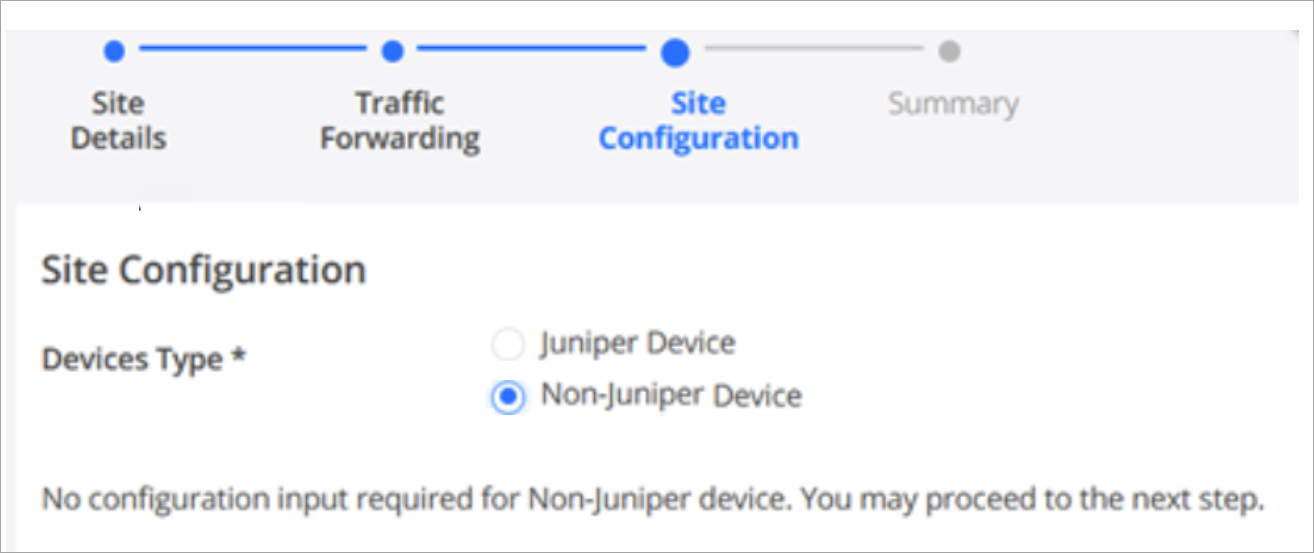
To create a site in Juniper Security Director Cloud:
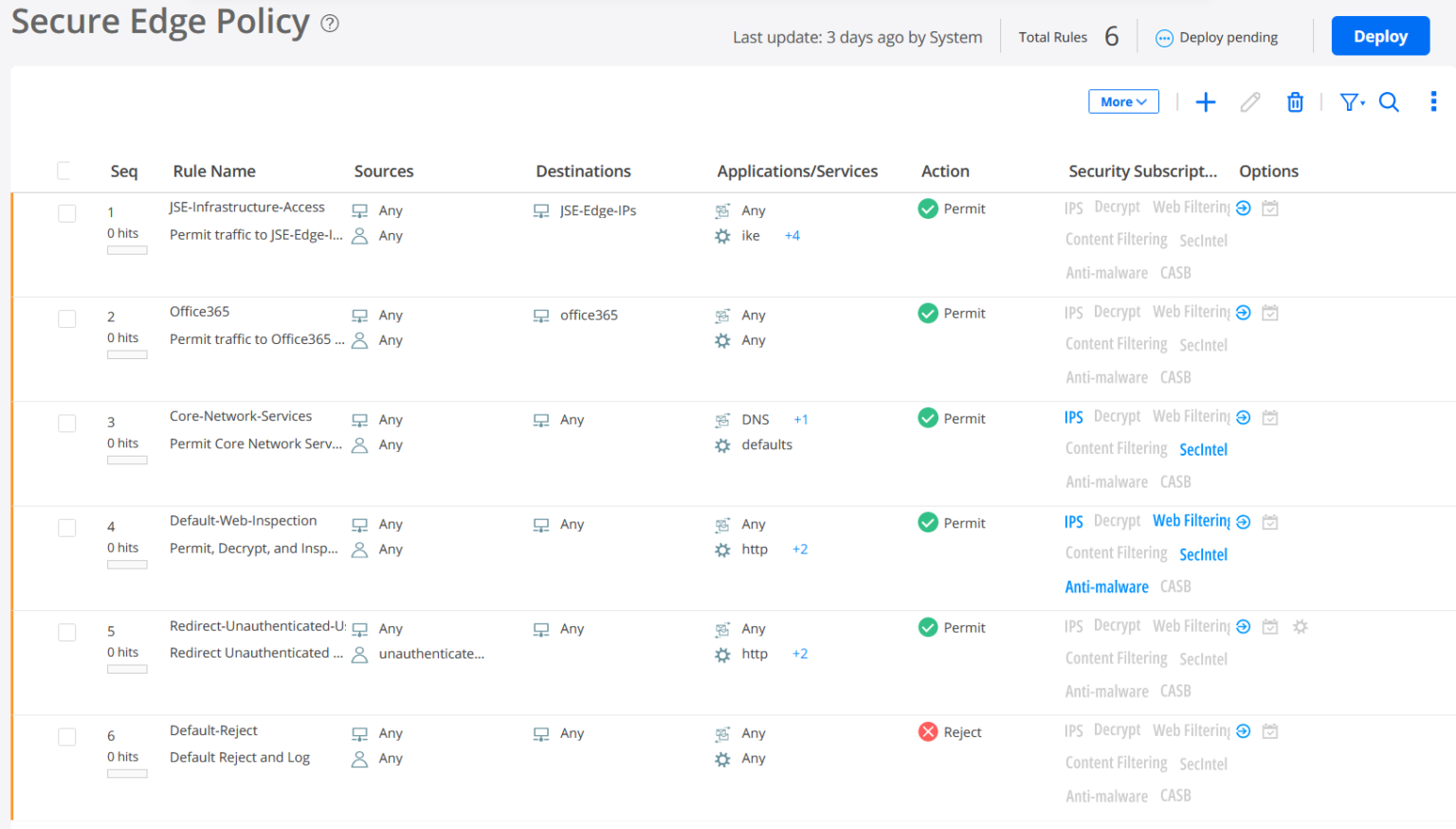
Deploy a Secure Edge Policy in Juniper Security Director Cloud
Now that you have created sites in Juniper Security Director Cloud, its time to deploy one or more Juniper® Secure Edge policies.
Secure Edge policies specify how the network routes traffic. By default, when you create a new tenant, the Security Director Cloud creates a Secure Edge policy rule set with predefined rules.
Even if you do not change the default rule set, you must use the Deploy option to load the rules in your service locations.
To deploy a Secure Edge policy in Juniper Security Director Cloud:
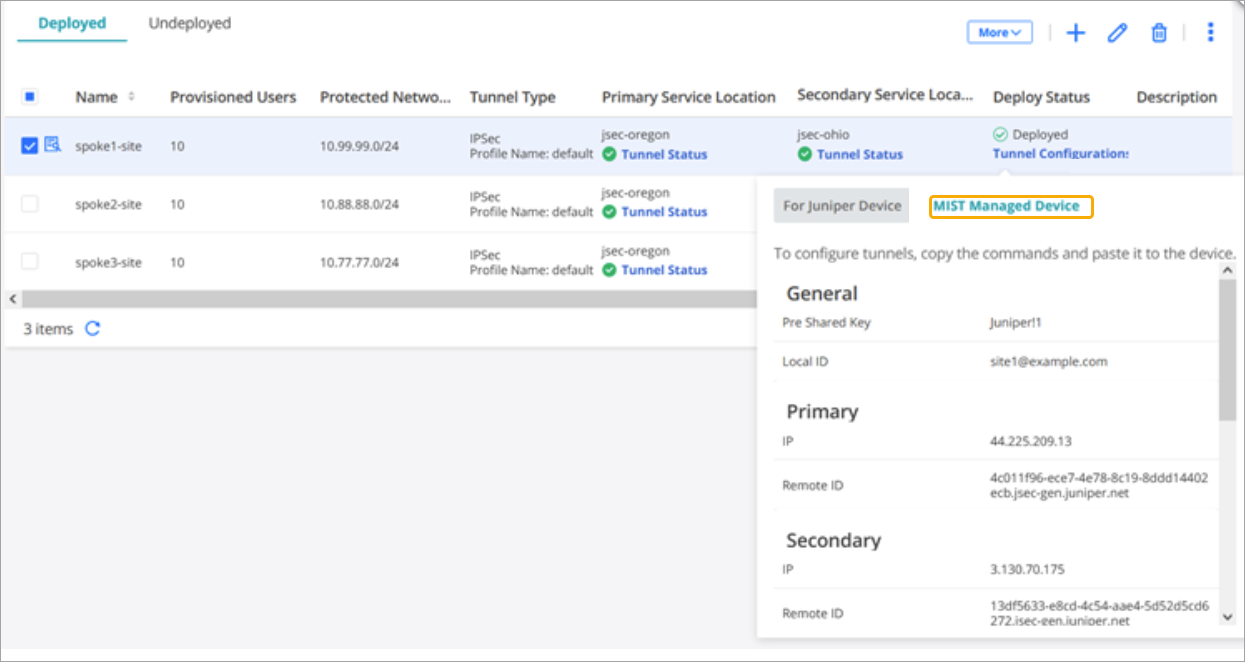
Get IPsec Tunnel Configuration Parameters to Apply in Juniper Security Director Cloud
In the preceding tasks, you completed several actions to set up an IPsec tunnels in Juniper Secure Edge and have deployed the Secure Edge policy in Juniper Security Director Cloud. The final step in Security Director Cloud is to collect configuration data for each site. You'll need these details to complete the secure edge connector configuration (Create Secure Edge Connectors in the Juniper Mist Portal) in the Juniper Mist™ cloud to set up an IPsec tunnel. In this step, you'll note down the details of the sites you created.
An automated configuration push to synchronize between Juniper Security Director Cloud and Juniper Mist cloud option not available.
To get IPsec tunnel configuration parameters to apply in Juniper Security Director Cloud:
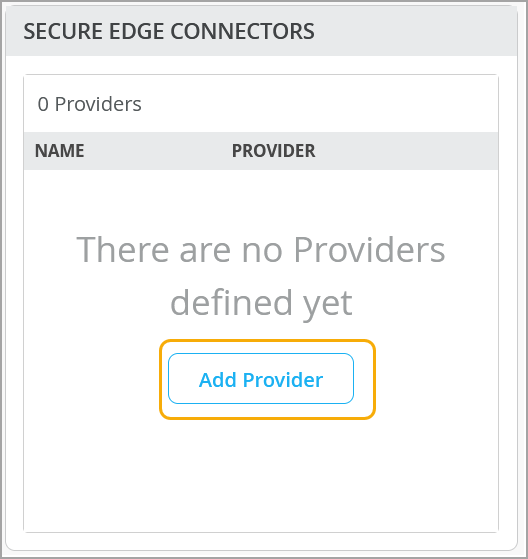
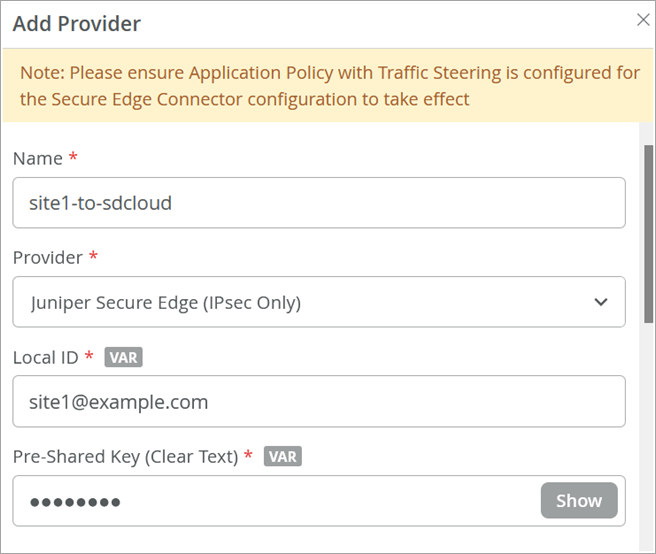
Create Secure Edge Connectors in the Juniper Mist Portal
You are about halfway to your ultimate goal of setting up a Secure Edge connector for the Session Smart Routers or SRX Series Firewalls in Juniper Mist™.
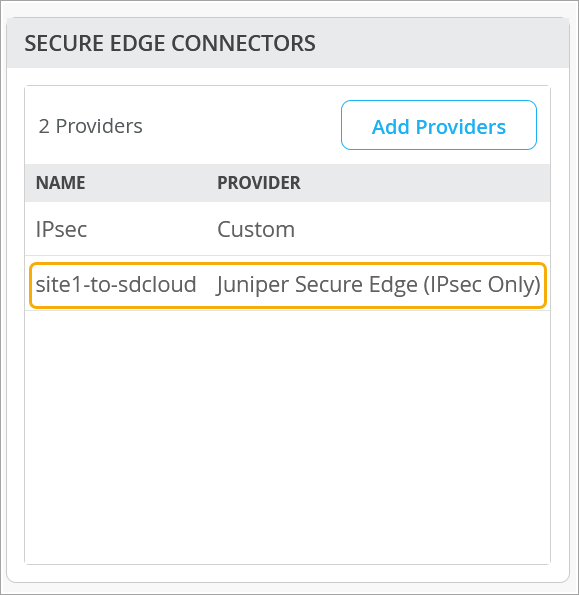
You create Secure Edge connectors in the Juniper Mist portal. This task completes the configuration on the Mist cloud side of the tunnels to establish an IPsec tunnel between WAN edge devices managed by Mist and Security Director Cloud. Before you create the connectors, ensure that your site has a deployed WAN edge device.
To create Secure Edge connectors in the Juniper Mist portal:
Modify an Application Policy
After you create Secure Edge connectors in the Juniper Mist™ cloud portal, next step is to modify application policies on the branch device. For example, you can allow traffic from a spoke device to a hub device. You can also allow traffic from a spoke device to another spoke device in the VPN tunnel. After that, you can send traffic from spokes to the Internet through Juniper Security Director Cloud instead of sending traffic from spokes to a hub for central breakout.
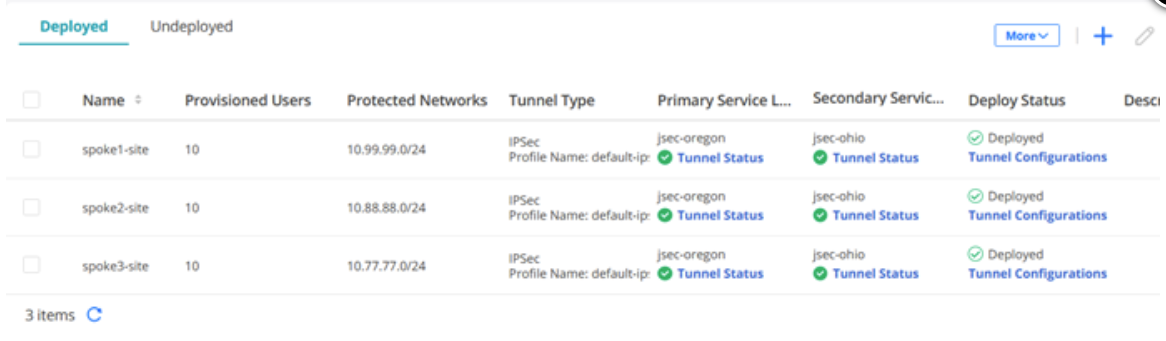
Use the following steps to confirm if the configuration is working:
Verify the Configuration
To verify the configuration: