Rogue, Neighbor, and Honeypot Access Points
Understand the threat posed by unauthorized access points on or near your site. Learn how to view the list of detected APs, and take action to address these threats.
What are Rogue, Neighbor, and Honeypot Access Points?
Rogue, neighbor, and honeypot access points (APs) are unauthorized devices operating on or near your network, often with the goal of fooling users into connecting to the "false" access point in order to steal data or monitor communications.
-
Rogue APs are any wireless APs installed on your wired network without authorization. Typically, this AP is connected to the LAN through an Ethernet cable. The intent of rogues can be malicious, such as to gain illicit access to the network, or benign, such as an employee setting up their own Wi-Fi hotspot to cover a perceived deadspot. Rogue clients are users who've connected to the rogue AP.
-
Neighbor APs are not connected to your network, but Juniper Mist detects them in the vicinity. Because these nearby APs typically have a strong signal, clients might connect to the neighbor AP, assuming that it's yours and is secure. Neighbor APs can also be a way for users in your facility to get around security restrictions on your network, such as streaming music or accessing blocked sites, or to avoid paying for services. Nonmalicious neighbor APs are SSIDs from another organization. In other words, legitimate SSIDs belonging to one organization will also be listed as neighbors for another organization.
-
Honeypots, also known as Evil Twins, are unauthorized APs that advertise your SSID, typically with the goal of capturing client login credentials. Here, a bad actor may copy or approximate your Wi-Fi hotspot, spoof your organization's login screen, and then collect the username and password of unsuspecting users as they try to login to "your" network. The bad actor can then use the credentials to log in to your actual network and wreak whatever havoc they have in mind. Non-malicious Honeypots are SSIDs from another organization that are broadcasting the same WLAN.
Dectection of Anomalous Devices
Juniper APs include a dedicated scanning radio to detect and potentially malicious APs and their clients. The dedicated scanning radios operate on 2.4, 5 and 6 GHz Wi-Fi bands. They provide data for real-time performance adjustments on the AP, as well as streaming telemetry that Juniper Mist uses for site-wide optimizations.
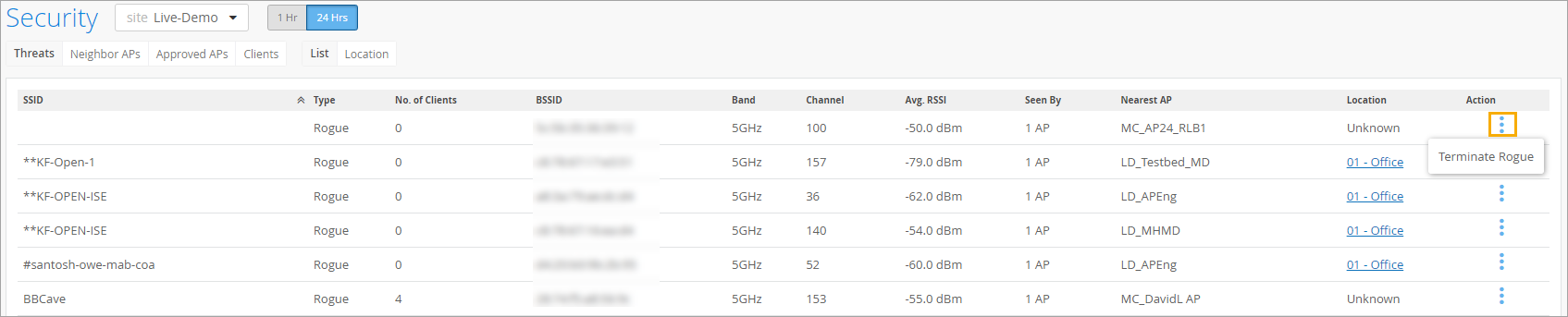
In the Juniper Mist portal, the Site > Wireless> Security page provides a list of all the anomalous APs that have been detected. You can drill down on any item to find the physical location, Ethernet connection, and rogue clients connected to the AP. Click on non-zero entries in No. of Clients column to open a Rogue Clients List pop-up for clients associated with that device.
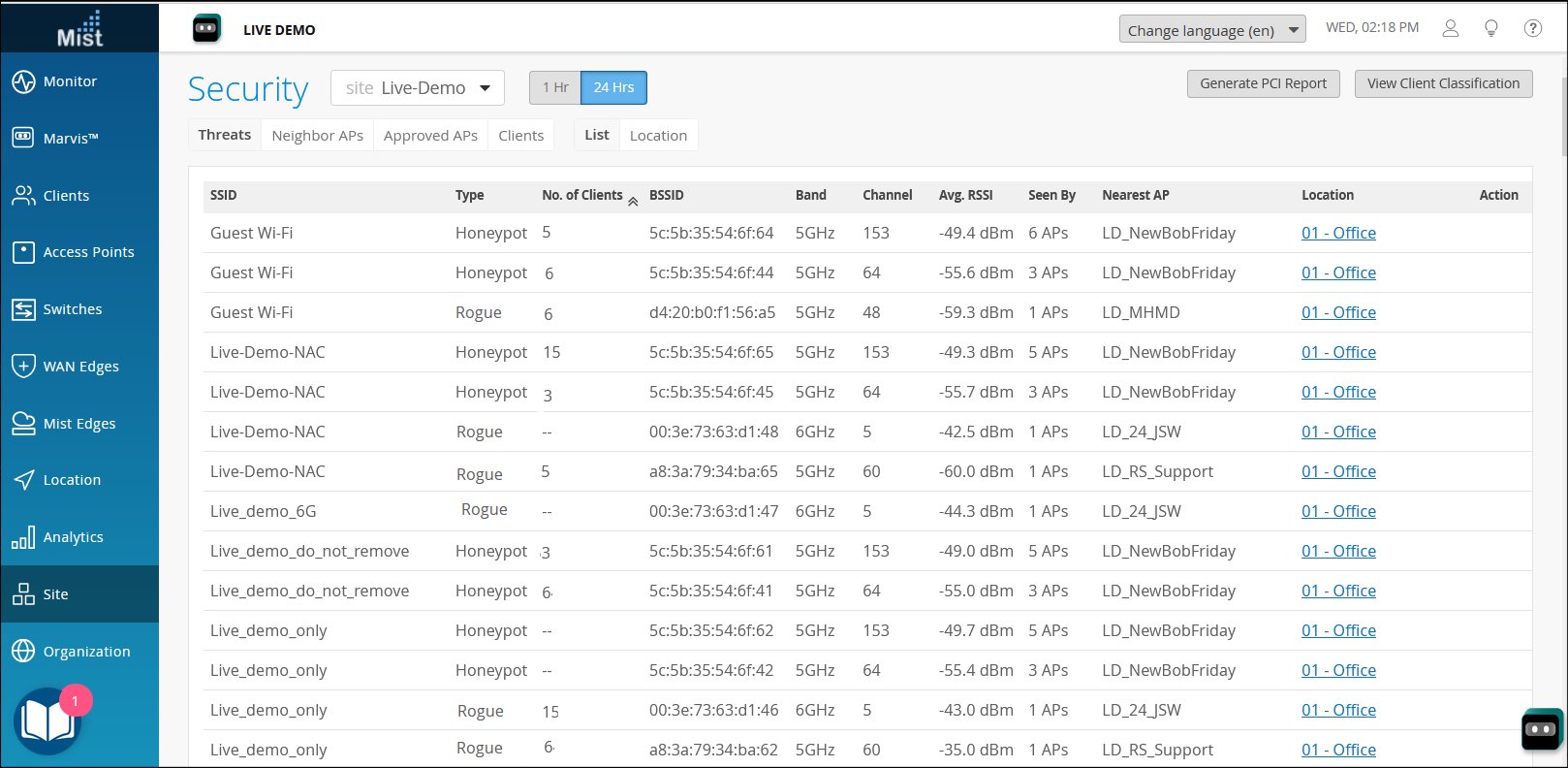
The Threats tab on the Security page shows a list of Rogue and Honeypot APs. You can see the lists of Neighbor APs, Approved APs, and Clients by clicking on the appropriate tab above the list.
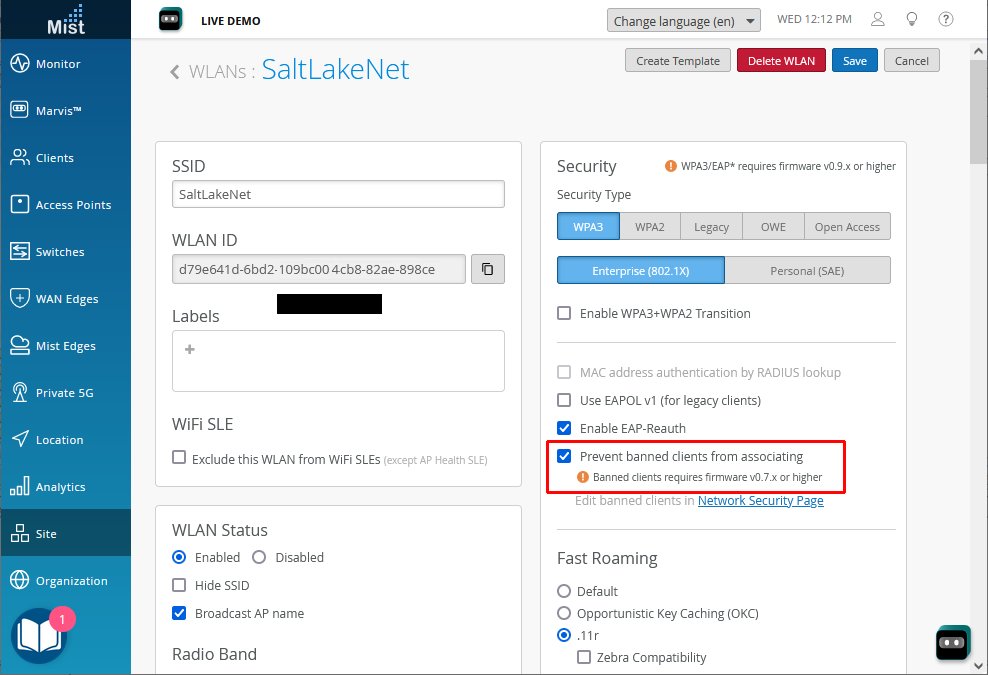
To see this information on this page, you must configure alerts for honeypot and rogue APs for the site or the entire organization.
Configure AP Threat Protection
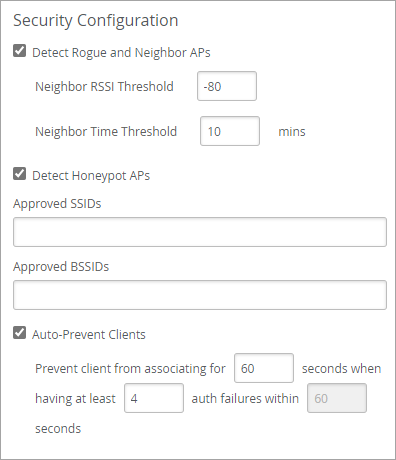
In your site settings, you can enable or disable detection of rogue, neighbor, and honeypot APs. You also can adjust the settings to prevent known APs from being misclassified as threats.
To configure AP threat protection:
Find and Remove Rogues
You can discover and remove rogue clients from your network on the Site > Wireless > Security page of the Juniper Mist™ portal.
The following animation shows how to find rogue APs and remove them. Basically, when you click the Terminate button, nearby Juniper APs will send deauthentication frames to the rogue clients, which are identified by their MAC addresses through their association with the rogue AP. The deauthentication frame is a notification, not a request, and the rogue client will be dropped.
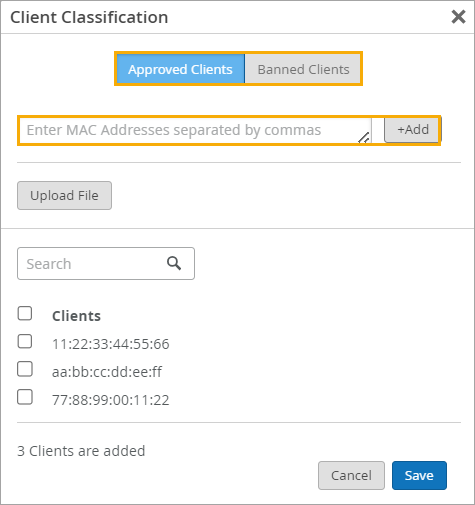
If you want to prevent these rogue clients from rejoining the network, you can classify them as banned, and they will not be re-authenticated by any AP in the site. Conversely, to allow certain terminated clients back on the network, you can classify them as approved, and the APs will not reject the authentication attempt. For help, see Classify, Approve, and Ban Designated Wireless Clients.
To find and remove rogue APs:
Classify, Approve, and Ban Designated Wireless Clients
To protect your network, use this feature to allow or ban access points based on their MAC addresses.
To simplify wireless security and control, you can identify wireless clients that you want to ban or approve.
With AP firmware version 0.9.x or later, clients can be banned or approved from a specific site or from the entire organization.
Classification limitations:
-
Firmware version 0.14.x and later—Up to 512 client classifications for a given SSID can be stored locally, on the relevant APs, (Any more than 512 are stored only on the cloud.)
-
Earlier firmware versions—Client classifications are stored on the Mist cloud. The AP must be connected to the cloud to reference and enforce the classification.