Use Case Overview: Threat Remediation of Infected Hosts with Forescout CounterACT
This use case provides a step-by-step Juniper Connected Security for enterprises to remediate threats of infected hosts using a third-party device, ForeScout CounterACT. ForeScout CounterACT is an agentless security appliance that dynamically identifies and evaluates network endpoints and applications the instant they connect to your network. CounterACT applies an agentless approach and integrates with Juniper Connected Security to block or quarantine infected hosts on Juniper Networks’ devices, third-party switches, and wireless access controllers with or without 802.1X protocol integration.
Without requiring management agents or previous device awareness, CounterACT uses active and passive techniques to discover and classify endpoints as they connect to the network, including:
BYOD (bring your own device), such as smartphones, laptops, tablets, and guest devices
Non-traditional devices, such as IoT devices, handhelds, and sensors
Unknown and rogue endpoints; such as unauthorized endpoints, switches, routers, and wireless access points

Using agentless visibility, CounterACT checks for device posture and compliance according to the security policies defined by the organization. Then, based on device classification and posture, CounterACT coordinates an automated host- or network-based response.
Customer Benefits
The elements in this use case provide the following benefits:
Multilayer Security
You gain layered security, policy enforcement, and control at the access, aggregation, core, and perimeter while greatly increasing your network security profile and reducing noncompliance risks and unauthorized access.
Agentless
No endpoint agents are required for device profiling, compliance, remediation, and access control. CounterACT detects and controls managed, unmanaged, and IoT devices which greatly simplifies deployment.
Open Interoperability
Elements in this use case are based on industry-standard protocols, enabling interoperability with other third-party solutions. CounterACT integrates with various switches, routers, VPNs, firewalls, and endpoint operating systems without requiring infrastructure changes or upgrades.
802.1X and Non-802.1X authentication
You can deploy CounterACT with Juniper Networks switches using 802.1X authentication or a robust non-802.1X approach. This use case provides a hybrid deployment approach, allowing you to select to authenticate traditional devices using 802.1X, or connect non-traditional devices using a non-802.1X approach.
Comprehensive Endpoint Visibility and Assessment
With great detail and speed, CounterACT detects the network to identify, evaluate, and monitor network endpoints and applications, as well as determine the device’s operating system, configuration, software, services, patch state, and presence of security agents. CounterACT automatically classifies a growing number of IoT endpoints as it quickly clarifies and assesses the status and security posture of devices on the network.
Use Case Building Blocks

There are four building blocks for this use case.
- Security Fabric Building Block
- ATP Cloud Realm (Management) Building Block
- Threat Intelligence Feed Building Block
- Enforcement Building Block
Security Fabric Building Block
Juniper Networks SRX Series firewalls provide security enforcement and deep inspection across all network layers and applications. In this particular Juniper Connected Security use case, a vSRX Series device is deployed as a perimeter firewall connected to ATP Cloud for anti-malware services.
ATP Cloud Realm (Management) Building Block
Juniper Networks ATP Cloud (integrated with SRX Series firewalls and registered with Policy Enforcer) identifies varying levels of risk, and provides a higher degree of accuracy in threat protection. Policy Enforcer orchestrates threat remediation workflows based on threats detected by Juniper’s ATP Cloud solution or custom threat feeds, and enforces these policies on firewalls, in particular SRX Series devices, and EX Series and QFX Series switches.
Threat Intelligence Feed Building Block
ATP Cloud feeds gather threat intelligence from multiple sources (including third-party feeds) and reports the gathered intelligence to Policy Enforcer. Then, Policy Enforcer uses the information gathered and reported by ATP Cloud to learn about the threats and rapidly respond to new threat conditions.
Policy Enforcer gathers third-party feeds, and based on the configured policy, the enforcement points can then respond to and take action to block and quarantine those threats.
Enforcement Building Block
On the SRX Series firewall using Security Director:
ATP policy is pushed to the SRX Series firewall from Security Director.
SRX Series firewall pulls the infected host feed from Policy Enforcer. Policy Enforcer automatically orchestrates threat remediation workflows based on threats detected by Juniper’s ATP Cloud solution or custom threat feeds, and enforces these policies on the SRX Series firewall and EX Series/QFX Series switch. Infected hosts are tracked and stop the progress of threats.
On the EX Series and QFX Series switches:
EX Series and QFX Series switches deliver layered policy enforcement and control at the access, aggregation, core, and perimeter. In the Juniper Connected Security, clients and endpoints are connected to EX Series and QFX Series switches with endpoint protection software. This multilayer approach mitigates risk and noncompliance at multiple levels while increasing the security profile of the network.
Policy Enforcer identifies an infected host by its IP and MAC address, allowing tracking and continued blocking of the host even if it moves to another switch or access point on the network.
Commits a MAC F/W filter on the switch for enforcement.
ForeScout CounterACT is an agentless security appliance that dynamically identifies (discovers) and evaluates network endpoints and applications the instant they connect to your network. In the Juniper Connected Security, using standard protocols such as SNMP, CLI, and IETF Network Configuration (NETCONF) protocol, CounterACT classifies and assesses device compliance posture, then applies automated policy actions at the EX Series and QFX Series switches. CounterACT also provides continuous device monitoring of HTTP and DHCP requests. Additionally, CounterACT leverages RADIUS CoA to enforce automated actions on an 802.1X environment.
Workflow for Endpoint Visibility and Access Control
When CounterACT detects a device that is either unknown, rogue, or noncompliant, it coordinates an instant response through its integration with EX Series switches and wireless controllers.
Table 1 summarizes these responses.
Connection Type |
Connection State |
Juniper Connected Security Message |
Counter ACT Action |
Wired |
Non-Dot1x |
Block |
Apply VACL |
Quarantine |
Quarantine VLAN |
||
Dot1x |
Block |
802.1x Authorize—Deny |
|
Quarantine |
802.1x Authorize—Specify VLAN |
||
Wireless |
Non-Dot1x |
Block |
WLAN Block |
Quarantine |
WLAN Role |
||
Dot1x |
Block |
802.1x Authorize—Deny |
|
Quarantine |
802.1x Authorize—Attribute Value |
CounterACT responds to these threats by pushing NETCONF files to Juniper Networks EX and QFX switches. Figure 3 shows the flow chart of the response process.
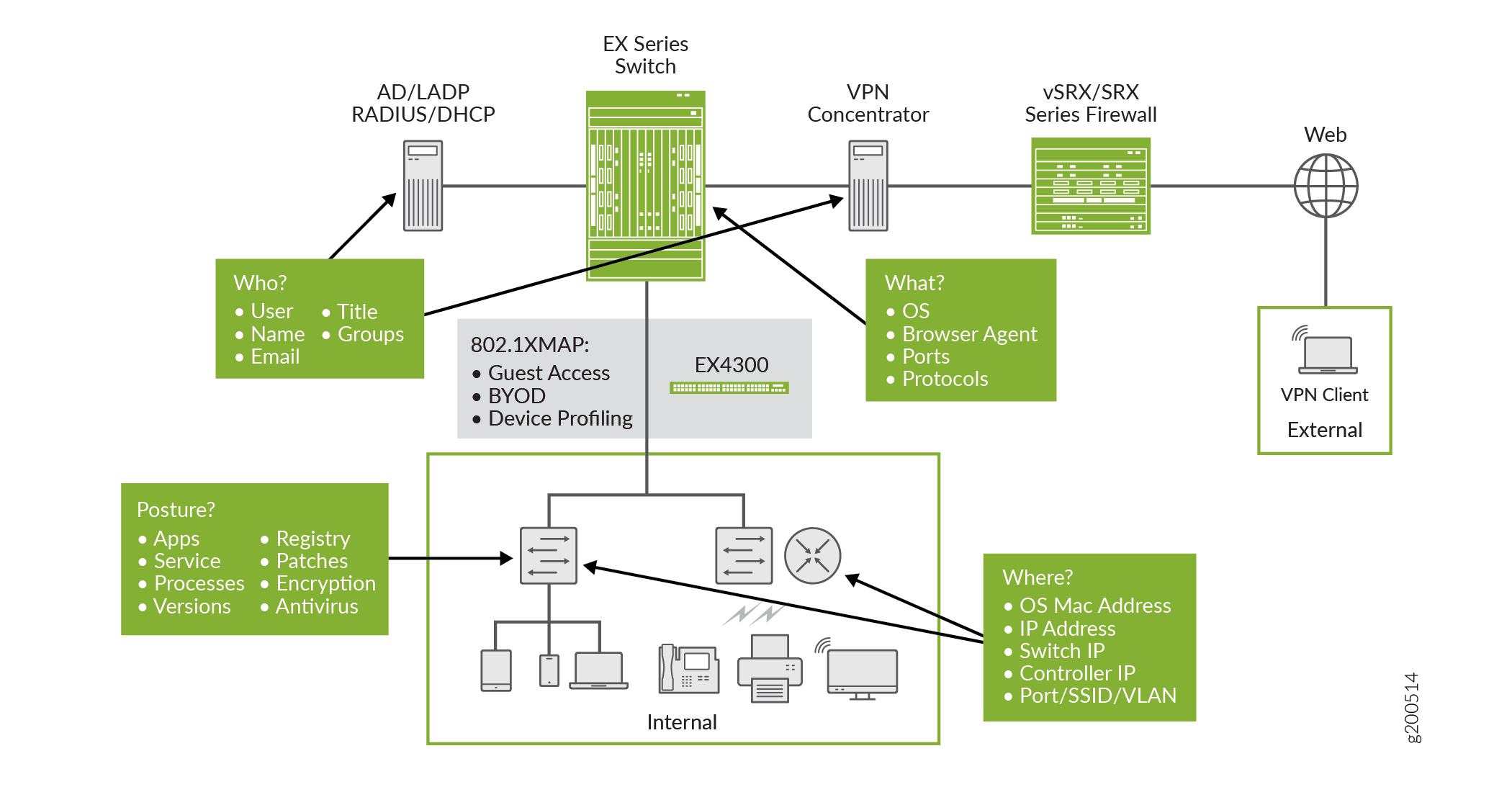
Based on endpoint classification, ownership, and posture, CounterACT pushes NETCONF configuration files to the switch to take one of the following actions:
Block the switch port and deny all network access.
Assign the device to a quarantine VLAN with restricted source access.
Apply an ACL to the interface to restrict access.
Downgrade infected host privileges through RADIUS CoA.
Device Detection and Profiling
The Juniper Networks and ForeScout CounterACT joint solution performs the following for device detection and profiling:
Identifies the type of connected device, such as printer, IP phone, tablet, Windows, iOS device, and so on.
Assigns network access based on the user identity or role, device type, location, ownership, and security compliance status.
Eliminates the need for enterprises to manually maintain a list of known device MAC IP addresses and device-type mappings.
Enables dynamic provisioning of ports based on the connected device type.
Agentless Endpoint Compliance
The Juniper Networks and ForeScout CounterACT joint solution delivers the following for agentless endpoint compliance:
Performs granular compliance checks on items such as antivirus software, OS patches, personal firewall, Peer-to-Peer Instant Messaging (P2P-IM), disk encryption, and so on, with the option to remediate any non-compliant issues.
Enforces compliance on corporate Windows, MAC, and Linux endpoints without installing agents.
Applies host and network actions, such as notifying users and administrators, moving to a remediation VLAN, pushing a restrictive ACL, and so on.
Guest Access and BYOD
Juniper Networks and ForeScout CounterACT joint solution provides the following for guest access and BYOD:
Delivers consistent wired and wireless experience to all personally owned devices.
Redirects users to a webpage through a captive portal to provide instructions on how to authenticate or register.
Presents users with an acceptable user policy (AUP) that they must agree to in order to obtain restricted guest access.
Enables guest users to log in using pre-allocated guest access credentials or can easily self-enroll.
Enables employees with non-corporate devices to be required to authenticate and auto-configure their endpoints. Once their devices have been auto-configured, these employee-owned devices are continuously monitored on the corporate network to ensure security policy compliance.
