|
Note: An ICMP flood can consist of any type of ICMP message. Therefore, JUNOS software monitors all ICMP message types, not just echo requests. |
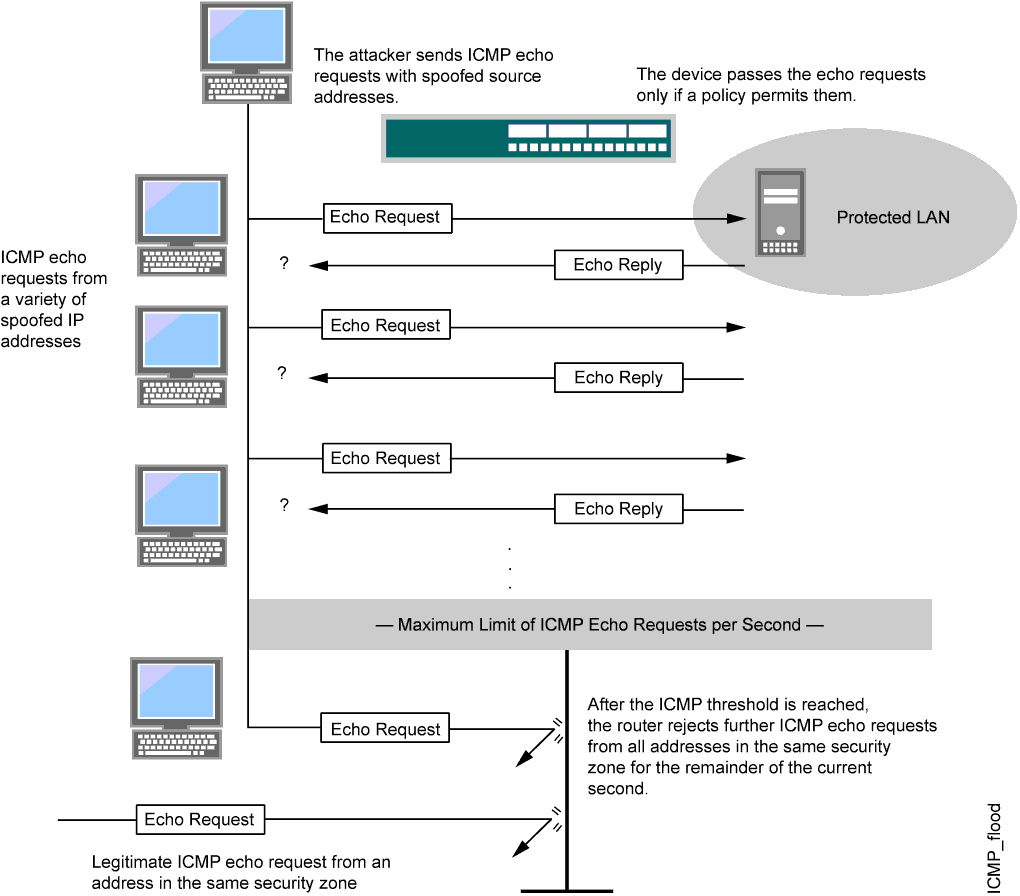
An ICMP flood typically occurs when ICMP echo requests overload its victim with so many requests that it expends all its resources responding until it can no longer process valid network traffic.
|
Before You Begin |
|---|
|
For background information, read Network DoS Attacks Overview. |
When enabling the ICMP flood protection feature, you can set a threshold that once exceeded invokes the ICMP flood attack protection feature. (The default threshold value is 1000 packets per second.) If the threshold is exceeded, JUNOS software ignores further ICMP echo requests for the remainder of that second plus the next second as well. See Figure 50.
 |
Note: An ICMP flood can consist of any type of ICMP message. Therefore, JUNOS software monitors all ICMP message types, not just echo requests. |
Figure 50: ICMP Flooding