What is application visibility and control?
What is application visibility and control?
Application visibility and control functionality protects critical high-speed networks against application-level threats. These threats are both existing and emerging, and can penetrate and proliferate in the network.
Problems Application Visibility and Control Address
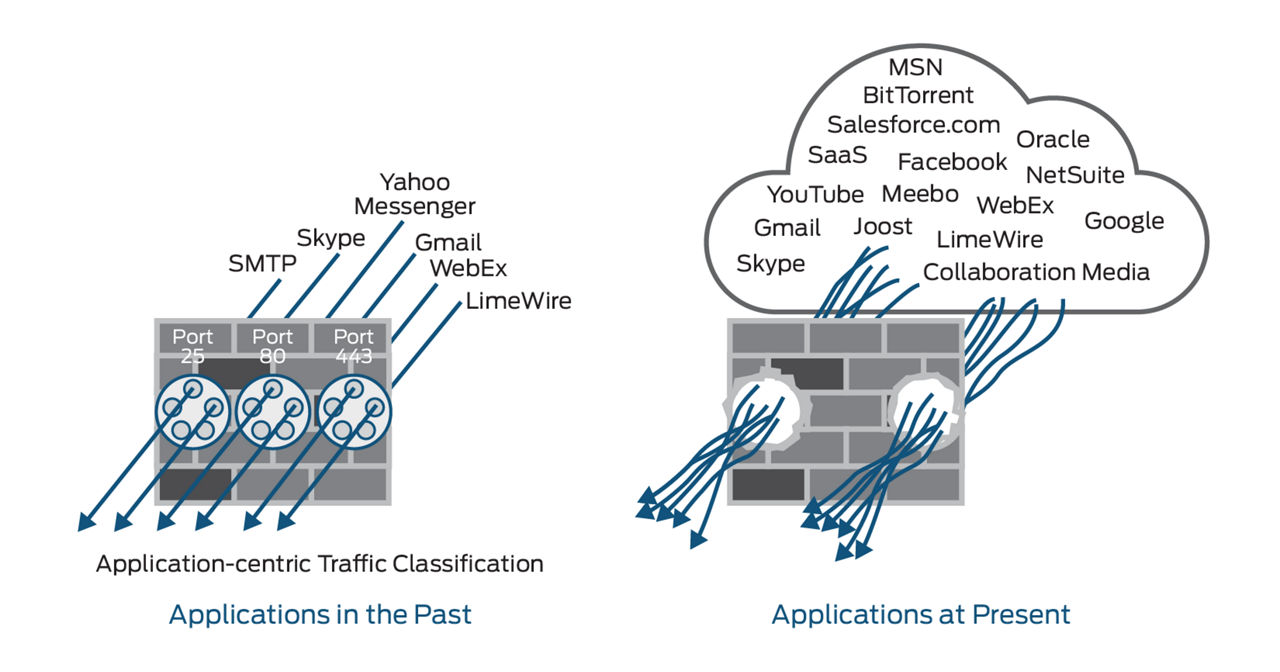
Web-based applications have changed the dynamics of security. Previously, specific applications were associated with specific protocols and ports, making policy enforcement at the host level relatively straightforward. Now, virtually all traffic is HTTP-based (ports 80/443), as shown below. Web applications that can be accessed from anywhere by employees, contractors, partners, and service providers through the firewall create access control challenges. Applications such as instant messaging, peer-to-peer file sharing, Webmail, social networking, and IP voice/video collaboration evade security mechanisms by changing communications ports and protocols, or by tunneling within other commonly used services (for example, HTTP or HTTPS). Organizations need control over the applications and traffic on their networks to protect their assets against attacks and manage bandwidth.
What Can You Do with Application Visibility and Control?
An effective security solution provides administrators with visibility and control over the applications traversing their networks. Application visibility and control is necessary in order to:
- Identify applications and allow, block, or limit applications – regardless of the port, protocol, decryption, or any other evasive tactic.
- Identify users, regardless of device or IP address, by using granular control of applications by specific users, groups of users, and machines. This helps organizations control the types of traffic allowed to enter and exit the network.
- Support inbound and outbound SSL decryption capabilities to identify and prevent threats and malware in encrypted network streams.
- Integrate with intrusion prevention systems (IPS) and apply appropriate attack objects to applications on nonstandard ports.
How Does Application Visibility and Control Work?
The application identification (App ID) classification engine and application signature pattern-matching engine operate at Layer 7 and inspect the actual content of the payload for identifying applications. App ID performs a deep packet inspection (DPI) of traffic on the network and on every packet in the flow that passes through the application identification engine until the application is identified. Application findings such as IP addresses, hostnames, and port ranges are saved in the application system cache (ASC) to expedite future identification.
Juniper Networks Implementation
The Juniper Networks AppSecure suite of application-aware security services for the SRX Series classifies traffic flows and brings visibility, enforcement, control, and protection to network security. AppSecure uses a sophisticated classification engine to accurately identify applications regardless of port or protocol, including applications known for using evasive techniques to avoid identification. It gives you the context to regain control of your network traffic, set and enforce policies based on accurate information, and deliver the performance and scale required to address your business needs.













