Application Detection
Network Insights uses inspectors to detect applications, sessions, and protocols.
JSA Network Insights 7.5.0 includes protocol parsing improvements and can now analyze the payload to identify approximately 300 more applications than earlier versions of the product.
To see the complete list of applications that JSA Network Insights 7.5.0 can identify, view these files after you upgrade.
-
/opt/ibm/xforce/metadata/protocols.hdr (column headers)
-
/opt/ibm/xforce/metadata/protocols.csv (values)
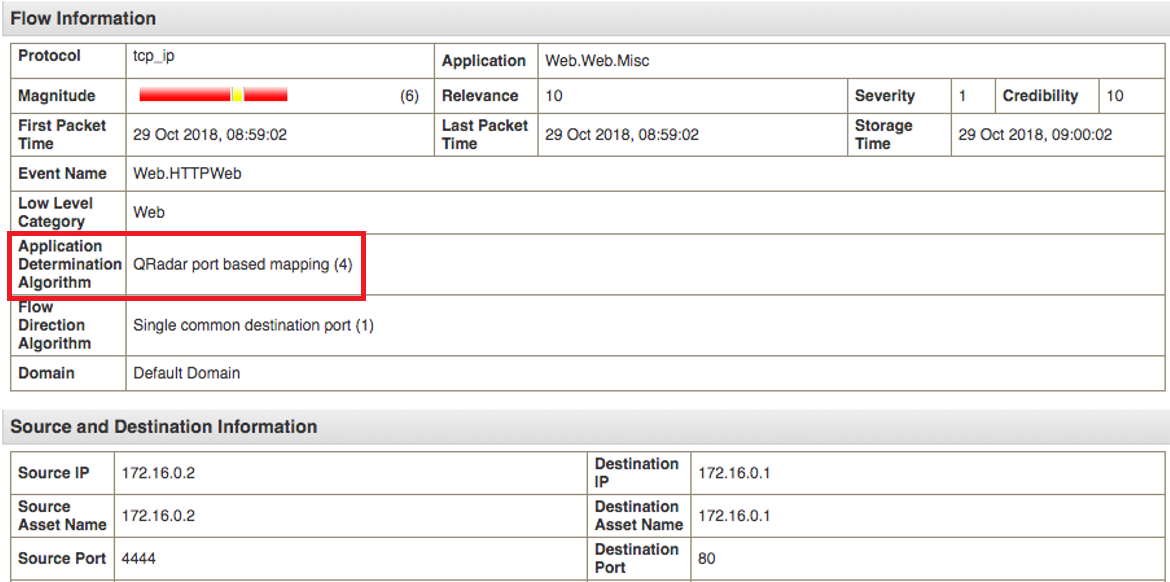
Application determination algorithms
Network Insights relies on its own set of inspectors and application detection methods. Network Insights, the Flow Processor algorithms are used only when Network Insights cannot identify a specific protocol.
The application determination algorithms are shown in the following table.
|
Numeric value |
Algorithm name |
Description |
|---|---|---|
|
2 |
Application signatures |
A payload-based algorithm that looks at the way that the payload is structured. This algorithm uses information from the signatures.xml file. |
|
3 |
State-based decoding |
A payload-based algorithm that uses complex internal logic. |
|
4 |
JSA port-based mapping |
A port-based algorithm that uses a pre-defined list of application mappings. This algorithm uses information from the /opt/qradar/conf/appid_map.conf file. |
|
5 |
User port-based mapping |
A port-based algorithm that uses a customizable list of application mappings. Use this algorithm to add new port-based mappings or reclassify existing mappings that come with JSA. This algorithm uses information from the /opt/qradar/conf/user_application_mapping.conf file. |
|
6 |
ICMP protocol mapping |
A protocol-based algorithm that looks at the protocol type and code. |
|
7 |
Flow exporter |
An algorithm that relies on the Flow Exporter to determine the application. For example, the QFlow process inherently trusts application IDs that come from Network Insights. |
|
8 |
QNI Application Signatures |
This algorithm is used by Network Insights. |
|
10 |
X-Force Web Application Classification |
This algorithm is used by Network Insights. |
|
11 |
QNI port heuristics |
This algorithm is used by Network Insights. It indicates that the application is identified by using port-based heuristics, and represents a low degree of confidence. |
|
12 |
QNI initial data |
This algorithm is used by Network Insights. It indicates that the application is identified by using the initial data in the flow session, and represents a medium degree of confidence. |
|
13 |
QNI parsers |
This algorithm is used by Network Insights. It indicates that the application is identified by parsing the available data, and represents the highest degree of confidence. |
You can see which type of application detection algorithm that is used in the Application Determination Algorithm field on the Flow Information window.