Configure Policy Enforcer for Security Director Insights Mitigation
Security Director Insights performs mitigation using Juniper® Advanced Threat Prevention Cloud (Juniper ATP Cloud) or Policy Enforcer. This topic explains how to configure Policy Enforcer for mitigation. Policy Enforcer is integrated within the Security Director Insights virtual machine (VM). You can mitigate the IP addresses with either the Security Director Insights integrated Policy Enforcer or the legacy standalone Policy Enforcer. If you are using the integrated Policy Enforcer for mitigation, use the IP address of the Security Director Insights VM wherever Policy Enforcer details need to be entered.
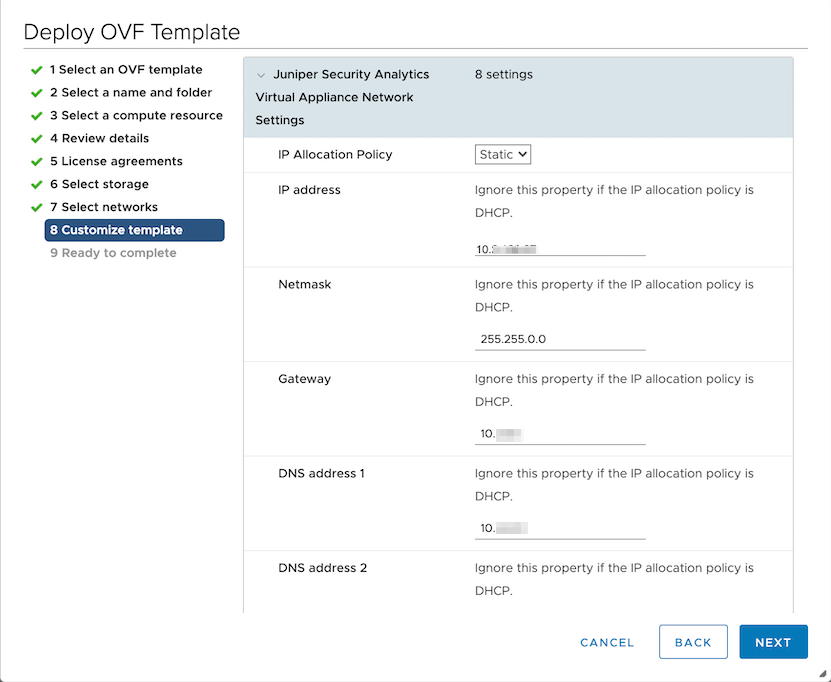
Add Security Director Insights Nodes
To add the Security Director Insights node:
Configure Security Director Insights as Integrated Policy Enforcer
To configure the integrated Policy Enforcer:
Create Custom Feeds for Mitigation
To mitigate incidents through Policy Enforcer, you must create custom feeds for blocklist and infected host.
To create the Policy Enforcer custom feeds:
You will see two new custom feeds listed on the Custom Feeds page: one for blocklist and one for infected host.
Configure Security Director Insights Mitigation Using Policy Enforcer
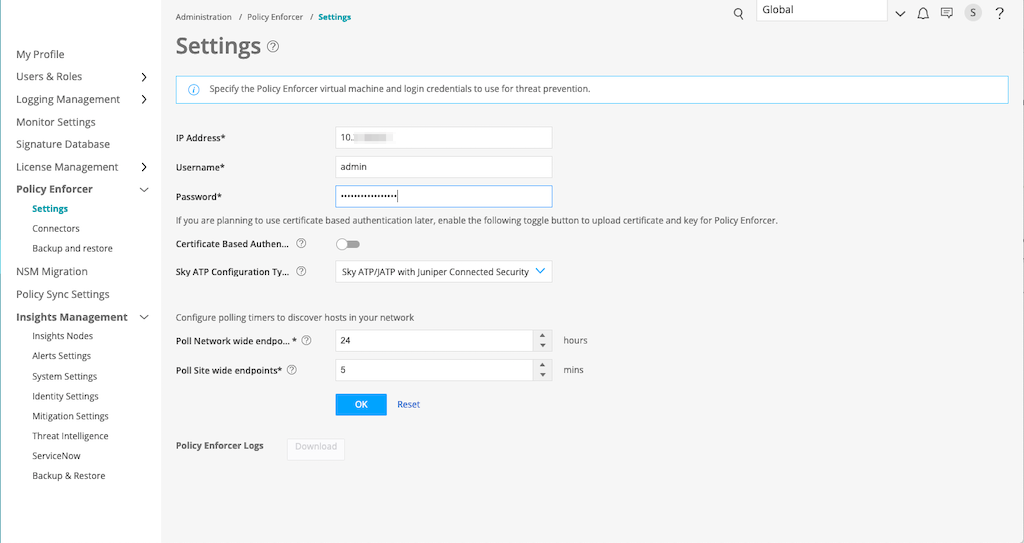
To configure mitigation settings using Policy Enforcer:
|
Setting |
Guideline |
|---|---|
|
Policy Enforcer Hostname |
The Policy Enforcer virtual machine IP address automatically appears. This is the IP address that you configure in the Policy Enforcer > Settings page. |
|
Policy Enforcer SSH User Name |
The SSH username automatically appears. This is the same username that you configure in the Policy Enforcer > Settings page. |
|
Policy Enforcer SSH Password |
Enter the Policy Enforcer SSH password. This is the same password that you enter in the Policy Enforcer > Settings page. |
|
API User Name |
If you have the credentials for the Policy Enforcer Controller APIs, enter the existing API username. Else, enter a name and Security Director Insights will create a new username. |
|
API Password |
If you have the credentials for the Policy Enforcer Controller APIs, enter the existing API password. Else, enter a password and Security Director Insights will create a new password. |
|
Blocklist Feed Name |
Enter the blocklist custom feed name that you created in the Configure > Threat Prevention > Feed Sources > Custom Feeds page. |
|
Infected-Host Feed Name |
Enter the infected host custom feed name that you created in the Configure > Threat Prevention > Feed Sources > Custom Feeds page. |
Security Director Insights supports mitigation using Juniper ATP Cloud and Policy Enforcer. Only one plugin can be active at a given time. Before you enable Policy Enforcer mitigation settings, ensure to disable the Juniper ATP Cloud plugin if it is enabled.
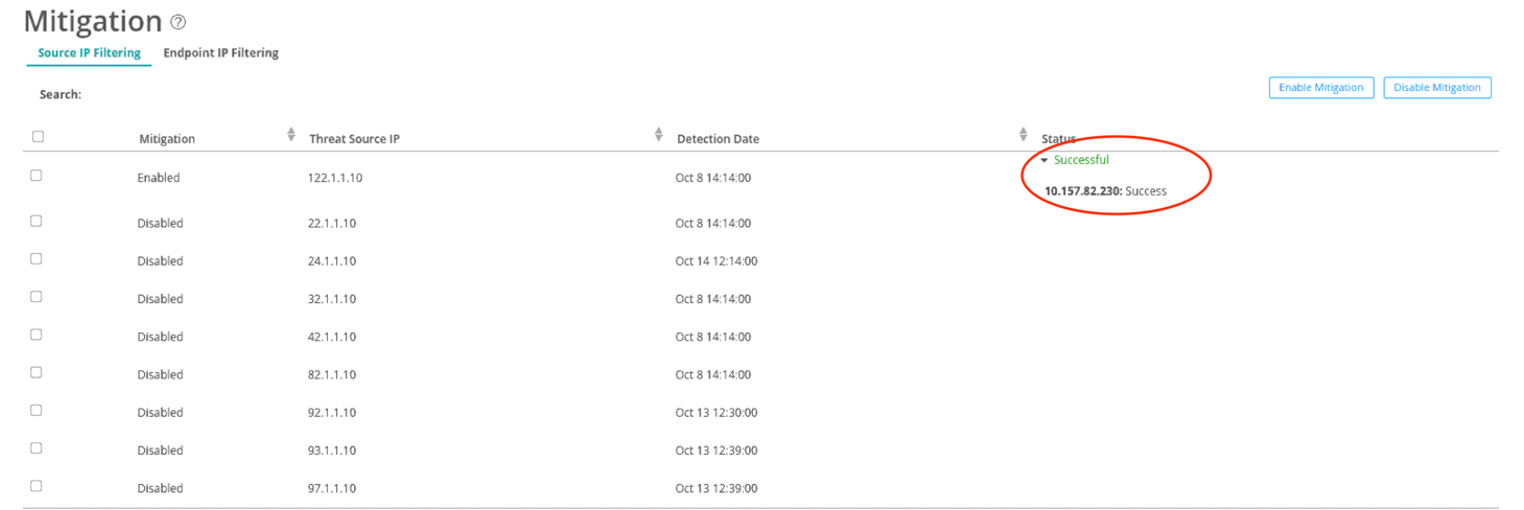
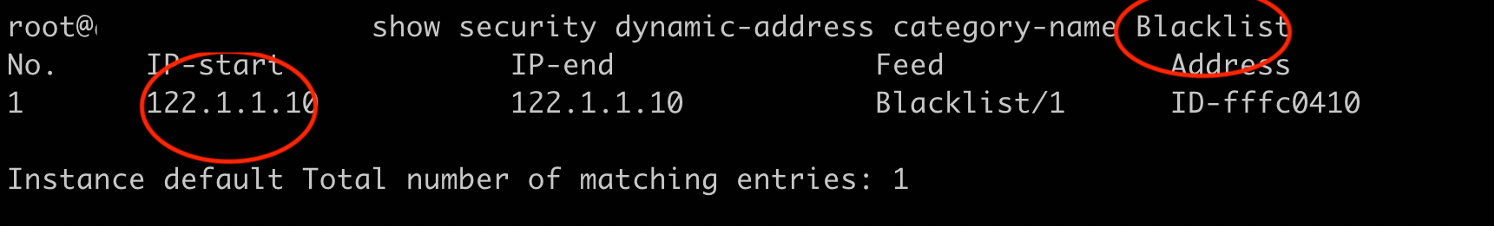
Monitor Mitigation Through Policy Enforcer
The following example shows how to mitigate incidents through Policy Enforcer.
To monitor the mitigation: