ON THIS PAGE
Migrate to vSRX3.0
Learn how to migrate vSRX Virtual Firewall software architecture from vSRX2.0 to vSRX3.0 and understand about the license requirements when you upgrade your vSRX Virtual Firewall.
In Junos OS Release 18.4R1, we've introduced a new software architecture vSRX3.0 for vSRX Virtual Firewall virtual firewalls. We recommend that you migrate to vSRX3.0 for your vSRX Virtual Firewall VM. If you are using vSRX2.0, you can migrate to the new vSRX3.0 in few steps. Note that the command-line interface (CLI) remains the same and the configuration that works on vSRX2.0 also works in vSRX3.0.
In this document, we use the following terms for vSRX Virtual Firewall architectures:
- Latest vSRX Virtual Firewall architecture (vSRX3.0) as vSRX3.0
- Architecture prior to vSRX3.0 as vSRX2.0 or vSRX
Overview
- Introduction to vSRX3.0
- Supported Junos OS Releases
- Feature Support in vSRX2.0 and vSRX3.0
- License Requirements for vSRX3.0
Introduction to vSRX3.0
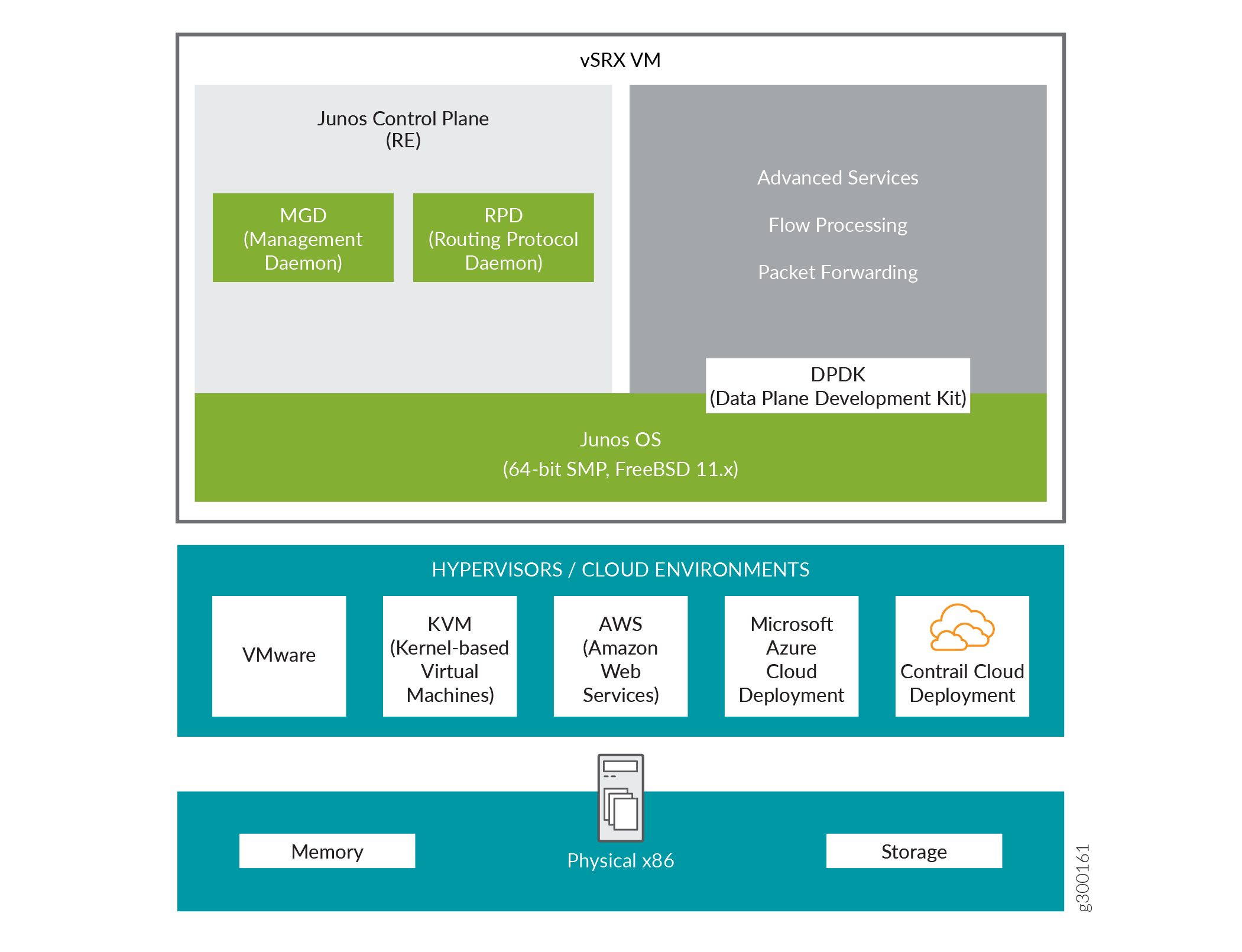
The new vSRX3.0 architecture is a streamlined virtual machine (VM) using FreeBSD 12.x / Junos OS as operating system. In vSRX3.0, the Routing Engine and the Packet Forwarding Engine run on FreeBSD 12.x or later version as single VM for improved performance and scalability. The vSRX3.0 uses DPDK to process the data packets in the data plane.
Benefits
Migrating to vSRX3.0 enables you to quickly introduce new services, deliver customized solutions, and scale security services dynamically due to:
-
Faster boot-time and enhanced responsiveness of the control plane during management operations
-
Increased operational benefits due to faster commits and CLI upgrades
-
Increased agility and smaller image size due to elimination of dual OS and nested virtualization
-
No special configuration required for enabling promiscuous mode on the management port and cluster control links
- Simplified and seamless deployments across different host environments
Figure 1 shows vSRX Virtual Firewall architecture.
Supported Junos OS Releases
Table 1 provides a list of supported Junos OS releases for vSRX2.0 and vSRX3.0.
| vSRX Virtual Firewall Architectures | Supported Junos OS Releases |
|---|---|
| vSRX2.0 |
15.1X49, 17.3 and later up to and including 22.4. Junos OS Release 22.4 is the last version available for vSRX2.0. We recommend using vSRX Virtual Firewall 3.0 going forward. |
| vSRX3.0 |
18.4 and later |
Feature Support in vSRX2.0 and vSRX3.0
Table 2 and Table 3 lists features supported in vSRX2.0 and vSRX3.0.
| Features | vSRX2.0 | vSRX3.0 |
|---|---|---|
|
2 vCPU / 4 GB RAM 5 vCPU / 8 GB RAM |
Yes | Yes |
|
9 vCPU / 16 GB RAM |
Yes | Yes (Junos OS Release 19.1R1 onwards) |
|
17 vCPU / 32 GB RAM |
Yes | Yes (Junos OS Release 19.1R1 onwards) |
|
Flexible flow session capacity scaling by an additional vRAM |
Yes (from Junos 19.1R1 onwards) | Yes (Junos OS Release 19.2R1 onwards) |
|
Multicore scaling support (Software RSS) |
No | Yes (Junos OS Release 19.3R1 onwards) |
|
Reserve additional vCPU cores for the Routing Engine |
Yes | Yes |
|
Virtio (virtio-net, vhost-net) |
Yes | Yes |
| Supported Hypervisors | ||
|
VMware ESXi 5.5, 6.0, and 6.5 |
Yes | Yes |
|
VMware ESXi 6.7 and 7.0 |
No | Yes (Junos OS Release 19.3R1 onwards) |
|
KVM on Ubuntu 16.04, Centos 7.1, Redhat 7.2 |
Yes | Yes |
|
Hyper-V |
Yes | Yes (Junos OS Release 19.1R1 onwards) |
| Multicore scaling support on Microsoft Hyper-V | No | Yes (Junos OS Release 19.1R1 onwards) |
|
Nutanix |
Yes | Yes (Junos OS Release 19.1R1 onwards) |
|
Contrail Networking 3.x |
Yes | Yes |
|
Contrail Networking 5.x |
No | Yes (Junos OS Release 19.3R1 onwards) |
|
AWS |
Yes | Yes |
|
Azure |
Yes | Yes (Junos OS Release 19.1R1 onwards) |
|
Google Cloud Platform (GCP) |
No | Yes (Junos OS Release 19.3R1 onwards) |
| Other Features | ||
|
Cloud-init |
Yes | Yes |
|
AWS ELB and ENA using C5 instances |
Yes | Yes (Junos OS Release 20.1R1 onwards) |
|
Powermode IPSec (PMI) |
Yes | Yes |
|
Chassis cluster |
Yes | Yes |
|
GTP TEID based session distribution using Software RSS |
No | Yes (Junos OS Release 19.3R1 onwards) |
|
On-device antivirus scan engine (Avira) |
No | Yes (Junos OS Release 19.4R1 onwards) |
|
LLDP |
Yes | Yes (Junos OS Release 21.1R1 onwards) |
|
Junos Telemetry Interface |
Yes | Yes (Junos OS Release 20.3R1 onwards) |
| System Requirements | ||
|
Hardware acceleration/enabled VMX CPU flag in the hypervisor |
Yes | No |
|
Disk space |
16 GB | 18 GB |
| vNICs | Supported On | vSRX2.0 | vSRX3.0 |
|---|---|---|---|
| VMXNET3 SA and HA | VMware | Yes | Yes |
| Virtio SA and HA | KVM | Yes | Yes |
| SR-IOV SA and HA over Intel 82599/X520 series | VMware and KVM | Yes | Yes |
| SR-IOV SA and HA over Intel X710/XL710/XXV710 series | VMware and KVM | Yes | Yes |
| SR-IOV SA over Intel E810 series | VMware and KVM | Yes | Yes |
| SR-IOV HA over Intel E810 series | VMware and KVM | No | No |
| SR-IOV SA and HA over Mellanox ConnectX-3 | VMware and KVM | No | No |
| SR-IOV SA and HA over Mellanox ConnectX-4/5/6 (MLX5 driver only) | VMware | Yes |
Yes (SA from Junos OS Release 21.2R1 onwards) (HA from Junos OS Release 21.2R2 onwards) |
| SR-IOV SA and HA over Mellanox ConnectX-4/5/6 (MLX5 driver only) | KVM | Yes |
Yes (Junos OS Release 21.2R1 onwards) |
| PCI passthrough over Intel 82599/X520 series | VMware and KVM | No | No |
| PCI passthrough over Intel X710/XL710 series | VMware and KVM | Yes | No |
License Requirements for vSRX3.0
Starting in Junos OS Release 21.1R1, we've transitioned to the Flex Software subscription licensing model for SRX Series and vSRX3.0. We now use Juniper Agile Licensing to support soft enforcement for virtual CPU (vCPU) usage on vSRX Virtual Firewall. Juniper Agile Licensing provides simplified and centralized license administration and deployment.
Junos OS Releases prior to 21.1 use licenses from a legacy Licensing Management System (LMS). If you apply the same license on vSRX3.0 with Junos OS 21.1 or later releases, the license expires after a grace period of 30 days. You must obtain a new license with Juniper Agile Licensing (JAL) portal (https://license.juniper.net/licensemanage/).
If you upgrade from vSRX2.0 (any Junos OS release) to vSRX3.0 (Junos OS Release 21.1 or higher), you must get a new license key. You can revoke the current license key and generate a new one for the higher Junos OS release. See Knowledge Base Article for details.
Figure 2 summarizes license requirements for different upgrade scenarios.
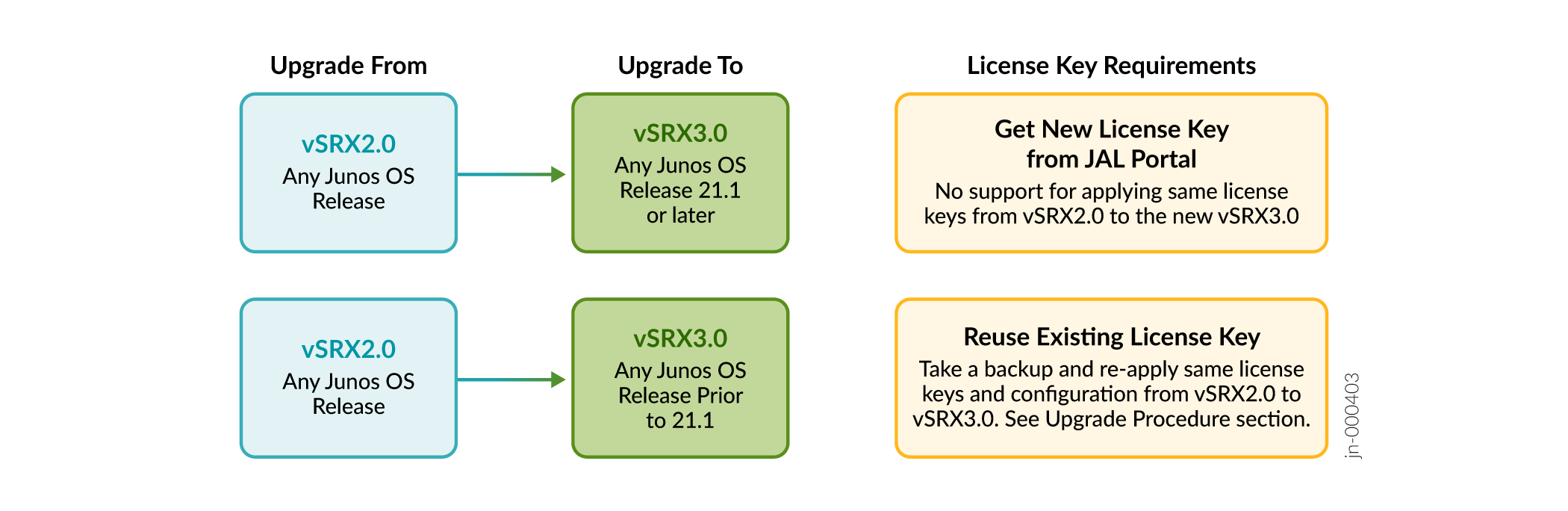
| Upgrade From | Upgrade To | Changes in License Keys |
|---|---|---|
|
vSRX2.0 with any Junos OS Release |
vSRX3.0 with Junos OS Releases 21.1 or later releases (21.1, 21.2, 21.3, 21.4, 22.1 and later releases) |
Get a new license with Juniper Agile Licensing (JAL) portal (https://license.juniper.net/licensemanage/). See Release Notes: Junos OS Release 21.1R1, Flex Software License for vSRX, and Licensing Guide for details. Ensure you specify the correct numbers of vCPUs in the license request. |
|
vSRX2.0 with any Junos OS Release |
vSRX3.0 with Junos OS Releases prior to 21.1 (18.4, 19.1, 19.2, 19.3, 19.4, 20.1, 20.2, 20.3, 20.4) |
Re-use the existing license key with following steps:
See Migration Procedure in this topic. |
We recommend you upgrade to vSRX3.0 with Junos OS Release 21.1R1 or higher versions to avoid licensing issue when you do vSRX Virtual Firewall image upgrades in the future.
Migration
- Check vSRX Virtual Firewall Version
- Pre-Migration Checklist
- Migration Procedure
- Post-Migration Tasks
Check vSRX Virtual Firewall Version
Check if your vSRX Virtual Firewall instance has vSRX2.0 or vSRX3.0 using the
show version command:
Example-1
user@host-01> show version Hostname: host-01 Model: vsrx
In the output, the field Model: vsrx with letters srx in lowercase represents vSRX2.0.
Example-2
user@host-01> show version Hostname: host-01 Model: vSRX Junos: 22.1R1.10
In the output, the field Model: vSRX with letters SRX in uppercase represents vSRX3.0.
Pre-Migration Checklist
Complete the following tasks before you migrate to vSRX3.0.
-
Check Junos OS version on your vSRX Virtual Firewall instance.
user@host-01> show version Hostname: host-01 Model: vsrx Junos: 19.4R3.1
The sample output indicates that your vSRX Virtual Firewall instance has Junos OS version 19.4R3 and with vSRX2.0.
-
Save the active configuration without any uncommitted changes.
user@host-01> show configuration | save /var/tmp/existingConfig.txt Wrote 273 lines of output to '/var/tmp/existingConfig.txt'
The system saves the active configuration at the specified file location. Copy the saved file into your local workspace for later use.
-
Check your license requirements as per Figure 2. You might need a new license key, or you can re-apply the existing one.
- If you require new license keys, obtain them from the Juniper Agile Licensing (JAL) portal (https://license.juniper.net/licensemanage/)
- If you can re-apply the existing license key, save a copy of license
file using the following steps:
-
Display license keys installed on your vSRX Virtual Firewall from the operational mode:
user@host-01> show system license keys DemolabJUNOS966777536 aeaqic beain4 vywmka bb3sxc zriaer ok4lgf aattzl rmyuac ipfoft cqaj34 vywmka frembw gaztem bsgiyd gmbzfv 4tkzcw hegbas tvnzux azlseb ew45df ojxgc3 ahfbho wz2j2i fojb6m z2jeif bwbml3 esqdkk dm4jxp j7o35h x6mvei fd3sjp uubu3r udfzu -
Copy license keys or save license keys to a file or URL with the following command:
user@host-01> request system license save filename | url
-
-
Backup any other files on the vSRX2.0 VM, which you might require on the new vSRX3.0 VM (such as IPsec VPN certificates and scripts) (if applicable).
-
Ensure you have your server/host OS ready and setup the required virtual networks and storage pool in the host OS.
-
Power-off your vSRX2.0 VM before you start deploying the new vSRX3.0 VM.
Migration Procedure
Use the following steps to migrate from vSRX2.0 to vSRX3.0:
- Navigate to the Juniper Networks Support page for the vSRX3.0 (https://support.juniper.net/support/downloads/?p=vsrx3) and select OS as vSRX3.0 and select the required
versions shown in Figure 3. Figure 3: vSRX3.0 Download
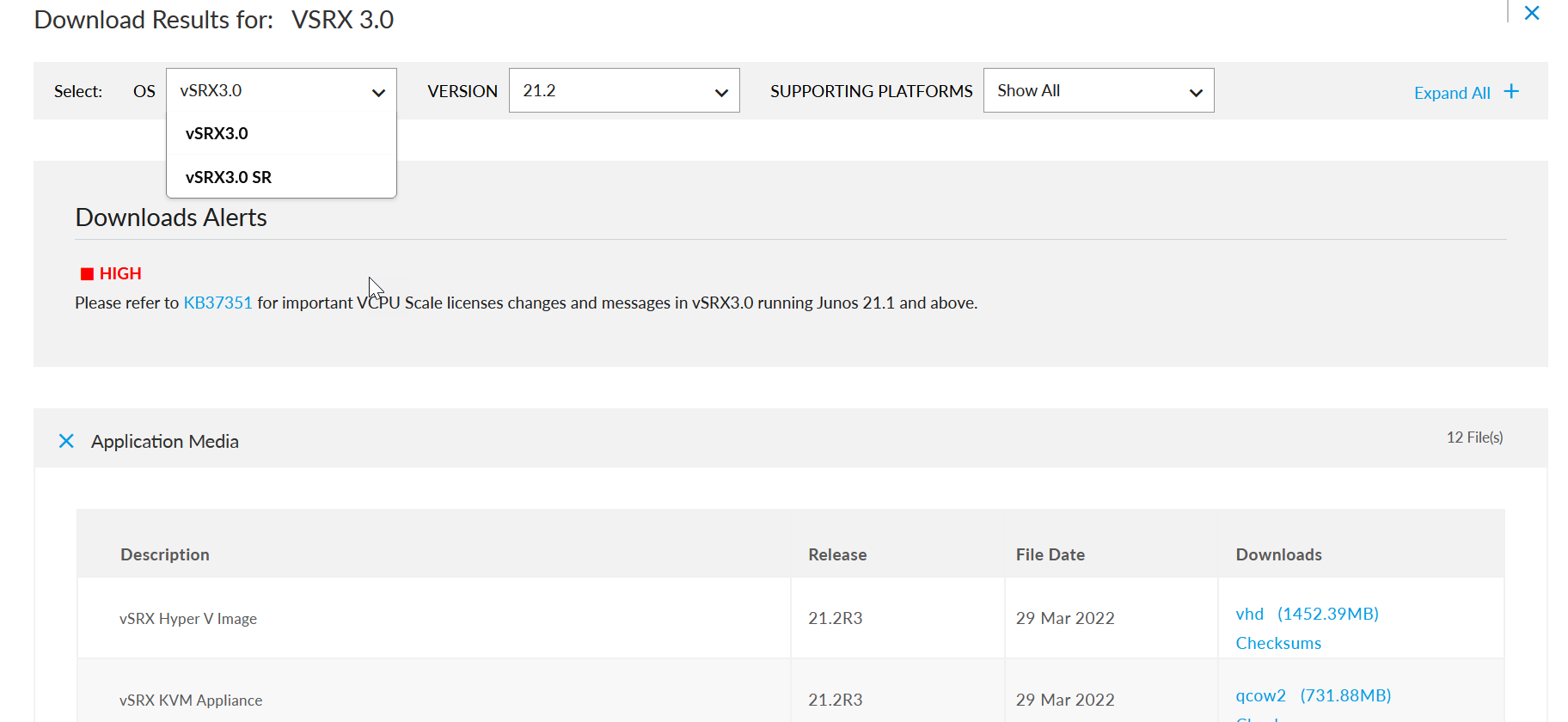
-
Enter your credentials and review/accept the End User License Agreement. You’ll be guided to the software image download page. Follow the instructions on the page and download the Junos OS image file.
Install the downloaded vSRX Virtual Firewall VM on your server.
When you download a vSRX3.0 image, the image file name includes vsrx3. Example:junos-install- vsrx3 -x86-64-21.2R3.8.tgz. See vSRX Deployment Guide for Private and Public Cloud Platforms for details on installation and launching of VM.-
Check Junos OS and vSRX Virtual Firewall version after a reboot using the
show versioncommand.user@host-01> show version Hostname: host-01 Model: vSRX Junos: 22.3R1.1
Post-Migration Tasks
Complete the following checks after you install new Junos OS with vSRX3.0.
-
Launch the new vSRX Virtual Firewall instance with vSRX3.0 on your server.
- Enable network access (for example by configuring an IP address on the fxp0 interface). This step enables you to transfer files to the new vSRX3.0 VM.
-
Apply the license keys (the existing keys or new keys as per Figure 2) on the newly launched vSRX Virtual Firewall instance.
user@host-01# request system license add terminal [Type ^D at a new line to end input, enter blank line between each license key] DemolabJUNOS966777536 aeaqic beain4 vywmka bb3sxc zriaer ok4lgf aattzl rmyuac ipfoft cqaj34 vywmka frembw gaztem bsgiyd gmbzfv 4tkzcw hegbas tvnzux azlseb ew45df ojxgc3 ahfbho wz2j2i fojb6m z2jeif bwbml3 esqdkk dm4jxp j7o35h x6mvei fd3sjp uubu3r udfzu DemolabJUNOS966777536: successfully added add license complete (no errors) -
If you are using a chassis cluster setup, enable chassis cluster on the new vSRX3.0 using the
set chassis cluster cluster-id X node [0|1]command and reboot VMs. -
Transfer any other files that you have taken a backup from vSRX2.0 VM such as IPsec VPN certificates and scripts (If applicable).
-
Copy the config file you saved earlier back to the /var/tmp folder.
- Run the load override /var/tmp/existingConfig.txt in
the configuration mode to replace the current configuration with the saved
configuration.
user@host-01# load override /var/tmp/existingConfig.txt load complete
- Commit the configuration.
user@host-01# commit
-
Ensure your device settings, network settings, and other configuration are available using the
show configurationcommand.
Changes in Application Layer Gateways (ALG) Default Behavior
In vSRX2.0, the following ALGs were disabled by default; however, when you migrate to vSRX3.0, these ALGs are enabled by default:
- H323
- MGCP
- RTSP
- SCCP
- SIP
If you've not enabled these ALGs in your vSRX2.0 configuration, you might want to disable them in the vSRX3.0 configuration to keep the same ALG behavior.
To disable an ALG:
[edit] set security alg <alg-name> disable
Use the show security alg status command to confirm which
ALGs are enabled/disabled.
Example:
user@host> show security alg status DNS : Enabled FTP : Enabled H323 : Disabled MGCP : Disabled MSRPC : Enabled PPTP : Enabled RSH : Disabled RTSP : Disabled SCCP : Disabled SIP : Disabled SQL : Disabled SUNRPC : Enabled TALK : Enabled TFTP : Enabled IKE-ESP : Disabled TWAMP : Disabled
What's Next?
Now that you have installed the new vSRX3.0, you can explore the new features and enhancements. See Release Notes.
