Address Books and Address Sets
An address book is a collection of addresses and address sets. Address books are like components or building blocks, that are referenced in other configurations such as security policies and security zones. You can add addresses to address books or use the predefined addresses available to each address book by default
An address book within a zone can consist of individual addresses or address sets. An address set is a set of one or more addresses defined within an address book. Using address sets, you can organize addresses in logical groups. Address sets are useful when you must refer to a group of addresses more than once in a security policy, in a security zone, or NAT configuration.
Understanding Address Books
An address book is a collection of addresses and address sets. Junos OS allows you to configure multiple address books. You can add addresses to address books or use the predefined addresses available to each address book by default.
Address book entries include addresses of hosts and subnets whose traffic is either allowed, blocked, encrypted, or user-authenticated. These addresses can be any combination of IPv4 addresses, IPv6 addresses, wildcard addresses, or Domain Name System (DNS) names.
- Predefined Addresses
- Network Prefixes in Address Books
- Wildcard Addresses in Address Books
- DNS Names in Address Books
Predefined Addresses
You can either create addresses or use any of the following predefined addresses that are available by default:
Any—This address matches any IP address. When this address is used as a source or destination address in a policy configuration, it matches the source and destination address of any packet.Any-ipv4—This address matches any IPv4 address.Any-ipv6—This address matches any IPv6 address.
Network Prefixes in Address Books
You can specify addresses as network prefixes in the prefix/length format. For example, 203.0.113.0/24 is an acceptable address book address because it translates to a network prefix. However, 203.0.113.4/24 is not acceptable for an address book because it exceeds the subnet length of 24 bits. Everything beyond the subnet length must be entered as 0 (zero). In special scenarios, you can enter a hostname because it can use the full 32-bit address length.
An IPv6 address prefix is a combination of an IPv6 prefix (address) and a prefix length. The prefix takes the form ipv6-prefix/prefix-length and represents a block of address space (or a network). The ipv6-prefix variable follows general IPv6 addressing rules. The /prefix-length variable is a decimal value that indicates the number of contiguous, higher-order bits of the address that make up the network portion of the address. For example, 2001:db8::/32 is a possible IPv6 prefix. For more information on text representation of IPv6 addresses and address prefixes, see RFC 4291, IP Version 6 Addressing Architecture.
Wildcard Addresses in Address Books
Besides IP addresses and domain names, you can specify a wildcard address in an address book. A wildcard address is represented as A.B.C.D/wildcard-mask. The wildcard mask determines which of the bits in the IP address A.B.C.D should be ignored. For example, the source IP address 192.168.0.11/255.255.0.255 in a security policy implies that the security policy match criteria can discard the third octet in the IP address (symbolically represented as 192.168.*.11). Therefore, packets with source IP addresses such as 192.168.1.11 and 192.168.22.11 conform to the match criteria. However, packets with source IP addresses such as 192.168.0.1 and 192.168.1.21 do not satisfy the match criteria.
The wildcard address usage is not restricted to full octets only. You can configure any wildcard address. For example, the wildcard address 192.168.7.1/255.255.7.255 implies that you need to ignore only the first 5 bits of the third octet of the wildcard address while making the policy match. If the wildcard address usage is restricted to full octets only, then wildcard masks with either 0 or 255 in each of the four octets only will be permitted.
DNS Names in Address Books
By default, you can resolve IPv4 and IPv6 addresses for a DNS. If IPv4 or IPv6 addresses are designated, you can resolve only those addresses by using the keywords ipv4-only and ipv6-only, respectively.
Consider the following when you configure the source address for DNS:
-
Only one source address can be configured as the source address for each DNS server name.
-
IPv6 source addresses are supported for IPv6 DNS servers, and only IPv4 addresses are supported for IPv4 servers. You cannot configure an IPv4 address for an IPv6 DNS server or an IPv6 address for an IPv4 DNS server.
To have all management traffic originate from a specific source address, configure the system name server and the source address. For example:
user@host# set system name-server 10.5.0.1 source-address 10.4.0.1
Before you can use domain names for address entries, you must configure the security device for DNS services. For information about DNS, see DNS Overview.
Understanding Global Address Books
An address book called “global” is always present on your system. Similar to other address books, the global address book can include any combination of IPv4 addresses, IPv6 addresses, wildcard addresses, or Domain Name System (DNS) names.
You can create addresses in the global address book or use the predefined addresses (any, any-ipv4, and any-ipv6). However, to use the addresses in the global address book, you do not need to attach the security zones to it. The global address book is available to all security zones that have no address books attached to them.
Global address books are used in the following cases:
NAT configurations–NAT rules can use address objects only from the global address book. They cannot use addresses from zone-based address books.
Global policies–Addresses used in a global policy must be defined in global address book. Global address book objects do not belong to any particular zone.
Understanding Address Sets
An address book can grow to contain large numbers of addresses and become difficult to manage. You can create groups of addresses called address sets to manage large address books. Using address sets, you can organize addresses in logical groups and use them to easily configure other features, such as policies and NAT rules.
The predefined address set, any, which contains both any-ipv4 and any-ipv6 addresses, is automatically
created for each security zone.
You can create address sets with existing users, or create empty address sets and later fill them with users. When creating address sets, you can combine IPv4 and IPv6 addresses, but the addresses must be in the same security zone.
You can also create an address set within an address set. This
allows you to apply policies more effectively. For example, if you
want to apply a policy to two address sets, set1 and set2, instead of using two statements, you can use just one
statement to apply the policy to a new address set, set3, that includes address sets set1 and set2.
When you add addresses to policies, sometimes the same subset of addresses can be present in multiple policies, making it difficult to manage how policies affect each address entry. Reference an address set entry in a policy like an individual address book entry to allow you to manage a small number of address sets, rather than manage a large number of individual address entries.
Configuring Addresses and Address Sets
You can define addresses and address sets in an address book and then use them when
configuring different features. You can also use predefined addresses any,
any-ipv4, and any-ipv6 that are available by default.
However, you cannot add the predefined address any to an address book.
After address books and sets are configured, they are used in configuring different features, such as security policies, security zones, and NAT.
Addresses and Address Sets
You can define IPv4 addresses, IPv6 addresses, wildcard addresses, or Domain Name System (DNS) names as address entries in an address book.
The following sample address book called book1 contains different types of
addresses and address sets. Once defined, you can leverage these addresses and address sets
when you configure security zones, policies, or NAT rules.
[edit security address-book book1] user@host# set address a1 203.0.113.1 user@host# set address a2 203.0.113.4/30 user@host# set address a4 2001:db8::/32 user@host# set address a5 2001:db8:1::1/127 user@host# set address example dns-name www.example.com user@host# set address-set set1 address a1 user@host# set address-set set1 address a2 user@host# set address-set set1 address a2 user@host# set address-set set2 address bbc
When defining addresses and address sets, follow these guidelines:
-
Address sets can only contain address names that belong to the same security zone.
-
Address names
any,any-ipv4andany-ipv6are reserved; you cannot use them to create any addresses. -
Addresses and address sets in the same zone must have distinct names.
-
Address names cannot be the same as address set names. For example, if you configure an address with the name
add1, do not create the address set with the nameadd1. -
When deleting an individual address book entry from the address book, you must remove the address (wherever it is referred) from all the address sets; otherwise, the system will cause a commit failure.
Address Books and Security Zones
A security zone is a logical group of interfaces with identical security requirements. You attach security zones to address books that contain entries for the addressable networks and end hosts (and, thus, users) belonging to the zone.
A zone can use two address books at a time—the global address book and the address book that the zone is attached to. When a security zone is not attached to any address book, it automatically uses the global address book. Thus, when a security zone is attached to an address book, the system looks up addresses from this attached address book; otherwise, the system looks up addresses from the default global address book. The global address book is available to all security zones by default; you do not need to attach zones to the global address book.
The following guidelines apply when attaching security zones to address books:
-
Addresses attached to a security zone conform to the security requirements of the zone.
-
The address book that you attach to a security zone must contain all IP addresses that are reachable within that zone.
-
When you configure policies between two zones, you must define the addresses for each of the zone's address books.
-
Addresses in a user-defined address book have a higher lookup priority than addresses in the global address book. Thus, for a security zone that is attached to a user-defined address book, the system searches the user-defined address book first; if no address is found, then it searches the global address book.
Address Books and Security Policies
Addresses and address sets are used when specifying the match criteria for a policy. Before you can configure policies to permit, deny, or tunnel traffic to and from individual hosts and subnets, you must make entries for them in address books. You can define different types of addresses, such as IPv4 addresses, IPv6 addresses, wildcard addresses, and DNS names, as match criteria for security policies.
Policies contain both source and destination addresses. You can refer to an address or address set in a policy by the name you give to it in the address book attached to the zone specified in the policy.
-
When traffic is sent to a zone, the zone and address to which the traffic is sent are used as the destination zone and address-matching criteria in policies.
-
When traffic is sent from a zone, the zone and address from which the traffic is sent are used as the source zone and address-matching criteria in policies.
Addresses Available for Security Policies
When configuring the source and destination addresses for a policy rule, you can type a question mark in the CLI to list all the available addresses that you can choose from.
You can use the same address name for different addresses that are in different address books. However, the CLI lists only one of these addresses—the address that has the highest lookup priority.
For example, suppose you configure addresses in two address books—global
and book1. Then, display the addresses that you can configure as source
or destination addresses in a policy (see Table 1).
|
Addresses Configured |
Addresses Displayed in the CLI |
|---|---|
[edit security address-book] set global address a1 203.0.113.0/24; set global address a2 198.51.100.0/24; set global address a3 192.0.2.0/24; set book1 address a1 203.0.113.128/25; |
[edit security policies from-zone trust to-zone untrust] user@host# set policy p1 match set match source-address ? Possible completions: [ Open a set of values a1 The address in address book book1 a2 The address in address book global a3 The address in address book global any Any IPv4 or IPv6 address any-ipv4 Any IPv4 address any-ipv6 Any IPv6 address |
The addresses displayed in this example illustrate:
-
Addresses in a user-defined address book have a higher lookup priority than addresses in the global address book.
-
Addresses in a global address book have a higher priority than the predefined addresses
any,any-ipv4, andany-ipv6. -
When the same address name is configured for two or more different addresses, only the highest priority address, based on the address lookup, is available. In this example, the CLI displays address
a1frombook1(203.0.113.128/25) because that address has a higher lookup priority than the global addressa1(203.0.113.0/24).
Applying Policies to Address Sets
When you specify an address set in policies, Junos OS applies the policies automatically to each address set member, so you do not have to create them one by one for each address. Also, if an address set is referenced in a policy, the address set cannot be removed without removing its reference in the policy. It can, however, be edited.
Consider that for each address set, the system creates individual rules for its members. It creates an internal rule for each member in the group as well as for each service configured for each user. If you configure address books without taking this into account, you can exceed the number of available policy resources, especially if both the source and destination addresses are address groups and the specified service is a service group.
Figure 1 shows how policies are applied to address sets.

Using Addresses and Address Sets in NAT Configuration
Once you define addresses in address books, you can specify them in the source,
destination, or static NAT rules. It is simpler to specify meaningful address names
instead of IP prefixes as source and destination addresses in the NAT rule
configuration. For example, instead of specifying 10.208.16.0/22 as source address,
you can specify an address called local that includes address
10.208.16.0/22.
You can also specify address sets in NAT rules, allowing you to add multiple addresses within an address set and therefore manage a small number of address sets, rather than manage a large number of individual address entries. When you specify an address set in a NAT rule, Junos OS applies the rule automatically to each address set member, so you do not have to specify each address one by one.
The following address and address set types are not supported in NAT rules—wildcard addresses, DNS names, and a combination of IPv4 and IPv6 addresses.
When configuring address books with NAT, follow these guidelines:
-
In a NAT rule, you can specify addresses from a global address book only. User-defined address books are not supported with NAT.
-
You can configure an address set as a source address name in a source NAT rule. However, you cannot configure an address set as a destination address name in a destination NAT rule.
The following sample NAT statements show the address and address set types that are supported with source and destination NAT rules:
[edit security nat source rule-set src-nat rule src-rule1] set match source-address 2001:db8:1::/64 set match source-address-name add1 set match source-address-name add-set1 set match destination-address 2001:db8::/64 set match destination-address-name add2 set match destination-address-name add-set2
[edit security nat destination rule-set dst-nat rule dst-rule1] set match source-address 2001:db8::/64 set match source-address-name add2 set match source-address-name add-set2 set match destination-address-name add1
-
In a static NAT rule, you cannot configure an address set as a source or destination address name. The following sample NAT statements show the types of address that are supported with static NAT rules:
[edit security nat static rule-set stat] set rule stat-rule1 match destination-address 203.0.113.0/24 set rule stat-rule2 match destination-address-name add1
Example: Configuring Address Books and Address Sets
This example shows how to configure addresses and address sets in address books. It also shows how to attach address books to security zones.
Requirements
Before you begin:
-
Configure the Juniper Networks security devices for network communication.
-
Configure network interfaces on server and member devices. See the Interfaces User Guide for Security Devices.
-
Configure Domain Name System (DNS) services. For information about DNS, see DNS Overview.
Overview
In this example, you configure an address book with addresses
and address sets (see Figure 2) to simplify configuring
your company’s network. You create an address book called Eng-dept and add addresses of members from the Engineering
department. You create another address book called Web and
add a DNS name to it. Then you attach a security zone trust to the Eng-dept address book and security zone untrust to the Web address book. You also create address sets to group software
and hardware addresses in the Engineering department. You plan to
use these addresses as source address and destination addresses in
your future policy configurations.
In addition, you add an address to the global address book, to be available to any security zone that has no address book attached to it.
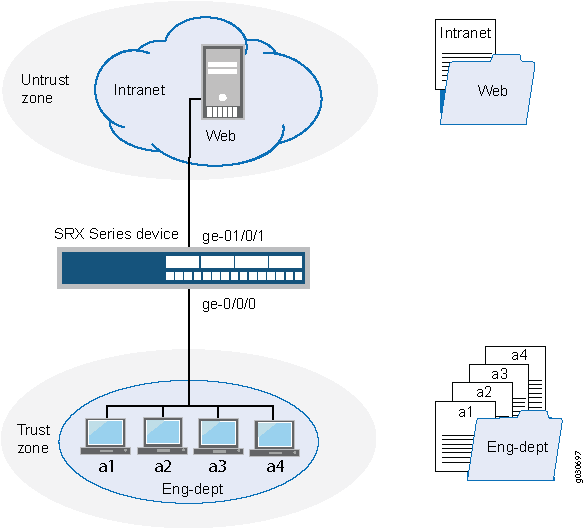
Topology
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set interfaces ge-0/0/0 unit 0 family inet address 203.0.113.5
set interfaces ge-0/0/1 unit 0 family inet address 203.0.113.6
set security zones security-zone trust interfaces ge-0/0/0
set security zones security-zone untrust interfaces ge-0/0/1
set security address-book Eng-dept address a1 203.0.113.1
set security address-book Eng-dept address a2 203.0.113.2
set security address-book Eng-dept address a3 203.0.113.3
set security address-book Eng-dept address a4 203.0.113.4
set security address-book Eng-dept address-set sw-eng address a1
set security address-book Eng-dept address-set sw-eng address a2
set security address-book Eng-dept address-set hw-eng address a3
set security address-book Eng-dept address-set hw-eng address a4
set security address-book Eng-dept attach zone trust
set security address-book Web address Intranet dns-name www-int.device1.example.com
set security address-book Web attach zone untrust
set security address-book global address g1 198.51.100.2
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User guide.
To configure addresses and address sets:
-
Configure Ethernet interfaces and assign IPv4 addresses to them.
[edit] user@host# set interfaces ge-0/0/0 unit 0 family inet address 203.0.113.5 user@host# set interfaces ge-0/0/1 unit 0 family inet address 203.0.113.6 -
Create security zones and assign interfaces to them.
[edit] user@host# set security zones security-zone trust interfaces ge-0/0/0 user@host# set security zones security-zone untrust interfaces ge-0/0/1 -
Create an address book and define addresses in it.
[edit security address-book Eng-dept ] user@host# set address a1 203.0.113.1 user@host# set address a2 203.0.113.2 user@host# set address a3 203.0.113.3 user@host# set address a4 203.0.113.4 -
Create address sets.
[edit security address-book Eng-dept] user@host# set address-set sw-eng address a1 user@host# set address-set sw-eng address a2 user@host# set address-set hw-eng address a3 user@host# set address-set hw-eng address a4 -
Attach the address book to a security zone.
[edit security address-book Eng-dept] user@host# set attach zone trust -
Create another address book and attach it to a security zone.
[edit security address-book Web ] user@host# set address Intranet dns-name www-int.device1.example.com user@host# set attach zone untrust -
Define an address in the global address book.
[edit] user@host# set security address-book global address g1 198.51.100.2
Results
From configuration mode, confirm your configuration
by entering the show security zones and show security
address-book commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example
to correct it.
[edit]
user@host# show security zones
security-zone trust {
interfaces {
ge-0/0/0.0;
}
}
security-zone untrust {
interfaces {
ge-0/0/1.0;
}
}
[edit]
user@host# show security address-book
Eng-dept {
address a1 203.0.113.1/32;
address a2 203.0.113.2/32;
address a3 203.0.113.3/32;
address a4 203.0.113.4/32;
address-set sw-eng {
address a1;
address a2;
}
address-set hw-eng {
address a3;
address a4;
}
attach {
zone trust;
}
}
Web {
address Intranet {
dns-name www-int.device1.example.com;
}
attach {
zone untrust;
}
}
global {
address g1 198.51.100.2/32;
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
Verifying Address Book Configuration
Purpose
Display information about configured address books and addresses.
Action
From configuration mode, enter the show security
address-book command.
user@host#
show security address-book
Eng-dept {
address a1 203.0.113.1/32;
address a2 203.0.113.2/32;
address a3 203.0.113.3/32;
address a4 203.0.113.4/32;
address-set sw-eng {
address a1;
address a2;
}
address-set hw-eng {
address a3;
address a4;
}
attach {
zone trust;
}
}
Web {
address Intranet {
dns-name www-int.device1.example.com;
}
attach {
zone untrust;
}
}
global {
address g1 198.51.100.2/32;
}
Excluding Addresses from Policies
Junos OS allows users to add any number of source and destination addresses to a policy. If you need to exclude certain addresses from a policy, you can configure them as negated addresses. When an address is configured as a negated address, it is excluded from a policy. You cannot, however, exclude the following IP addresses from a policy:
Wildcard
IPv6
any
any-ipv4
any-ipv6
0.0.0.0
When a range of addresses or a single address is negated, it can be divided into multiple addresses. These negated addresses are shown as a prefix or a length that requires more memory for storage on a Packet Forwarding Engine.
Each platform has a limited number of policies with negated addresses. A policy can contain 10 source or destination addresses. The capacity of the policy depends on the maximum number of policies that the platform supports.
Before you configure a negated source address, destination address, or both, perform the following tasks:
Create a source, destination, or both address book.
Create address names and assign source and destination addresses to the address names.
Create address sets to group source, destination, or both address names.
Attach source and destination address books to security zones. For example, attach the source address book to the from-zone trust and the destination address book to the to-zone untrust.
Specify the match source, destination, or both address names.
Execute source-address-excluded, destination-address excluded, or both commands. A source, destination, or both addresses added in the source, destination, or both address books will be excluded from the policy.
The global address book does not need to be attached to any security zone.
Example: Excluding Addresses from Policies
This example shows how to configure negated source and destination addresses. It also shows how to configure address books and address sets.
Requirements
This example uses the following hardware and software components:
An SRX Firewall
A PC
Any supported Junos OS Release
Before you begin, configure address books and address sets. See Example: Configuring Address Books and Address Sets.
Overview
In this example, you create source and destination address books, SOUR-ADDR and DES-ADDR, and add source and destination addresses to it. You create source and destination address sets, as1 and as2, and group source and destination addresses to them. Then you attach source address book to the security zone trust and the destination address book to the security zone untrust.
You create security zones from-zone trust and to-zone untrust. You specify the policy name to p1 and then you set the name of the match source address to as1 and the match destination address to as2. You specify the commands source -address-excluded and destination -address-excluded to exclude source and destination addresses configured in the policy p1. Finally, you set the policy p1 to permit traffic from-zone trust to to-zone untrust.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security address-book SOU-ADDR address ad1 255.255.255.255/32 set security address-book SOU-ADDR address ad2 203.0.113.130/25 set security address-book SOU-ADDR address ad3 range-address 192.0.2.6 to 192.0.2.116 set security address-book SOU-ADDR address ad4 192.0.2.128/25 set security address-book SOU-ADDR address-set as1 address ad1 set security address-book SOU-ADDR address-set as1 address ad2 set security address-book SOU-ADDR address-set as1 address ad3 set security address-book SOU-ADDR address-set as1 address ad4 set security address-book SOU-ADDR attach zone trust set security address-book DES-ADDR address ad8 198.51.100.1/24 set security address-book DES-ADDR address ad9 range-address 192.0.2.117 to 192.0.2.199 set security address-book DES-ADDR address ad10 198.51.100.0/24 set security address-book DES-ADDR address ad11 range-address 192.0.2.199 to 192.0.2.250 set security address-book DES-ADDR address-set as2 address ad8 set security address-book DES-ADDR address-set as2 address ad9 set security address-book DES-ADDR address-set as2 address ad10 set security address-book DES-ADDR address-set as2 address ad11 set security address-book DES-ADDR attach zone untrust set security policies from-zone trust to-zone untrust policy p1 match source-address as1 set security policies from-zone trust to-zone untrust policy p1 match source-address-excluded set security policies from-zone trust to-zone untrust policy p1 match destination-address as2 set security policies from-zone trust to-zone untrust policy p1 match destination-address-excluded set security policies from-zone trust to-zone untrust policy p1 match application any set security policies from-zone trust to-zone untrust policy p1 then permit
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User guide.
To configure negated addresses:
Create a source address book and address names. Add the source addresses to the address book.
[edit security address book ] user@host#set SOU-ADDR address ad1 255.255.255.255/32 user@host#set SOU-ADDR address ad2 203.0.113.130/25 user@host#set SOU-ADDR ad3 range-address 192.0.2.6 to 192.0.2.116 user@host#set SOU-ADDR address ad4 192.0.2.128/25
Create an address set to group source address names.
[edit security address book ] user@host# set SOU-ADDR address-set as1 address ad1 user@host# set SOU-ADDR address-set as1 address ad2 user@host# set SOU-ADDR address-set as1 address ad3 user@host# set SOU-ADDR address-set as1 address ad4
Attach the source address book to the security from zone.
[edit security address book ] user@host# set SOU-ADDR attach zone trust
Create a destination address book and address names. Add the destination addresses to the address book.
[edit security address book ] user@host#set DES-ADDR address ad8 198.51.100.1/24 user@host#set DES-ADDR address ad9 range-address 192.0.2.117 to 192.0.2.199 user@host#set DES-ADDR address ad10 198.51.100.0/24 user@host#set DES-ADDR address ad11 range-address 192.0.2.199 to 192.0.2.250
Create another address set to group destination address names.
[edit security address book ] user@host# set DES-ADDR address-set as1 address ad8 user@host# set DES-ADDR address-set as1 address ad9 user@host# set DES-ADDR address-set as1 address ad10 user@host# set DES-ADDR address-set as1 address ad11
Attach the destination address book to the security to zone.
[edit security address book ] user@host# set DES-ADDR attach zone untrust
Specify the policy name and source address.
[edit security policies] user@host# set from-zone trust to-zone untrust policy p1 match source-address as1
Exclude source addresses from the policy.
[edit security policies] user@host# set from-zone trust to-zone untrust policy p1 match source-address-excluded
Specify the destination address.
[edit security policies] user@host# set from-zone trust to-zone untrust policy p1 match destination-address as2
Exclude destination addresses from the policy.
[edit security policies] user@host# set from-zone trust to-zone untrust policy p1 match destination-address-excluded
Configure the security policy application.
[edit security policies] user@host# set from-zone trust to-zone untrust policy p1 match application any
Permit the traffic from-zone trust to to-zone untrust.
[edit security policies] user@host# set from-zone trust to-zone untrust policy p1 then permit
Results
From configuration mode, confirm your configuration
by entering the show security policies command. If the
output does not display the intended configuration, repeat the configuration
instructions in this example to correct it.
[edit]
user@host# show security policies
from-zone trust to-zone untrust {
policy p1 {
match {
source-address as1;
destination-address as2;
source-address-excluded;
destination-address-excluded;
application any;
}
then {
permit;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
Verifying the Policy Configuration
Purpose
Verify that the policy configuration is correct.
Action
From operational mode, enter the show security
policies policy-name p1 command.
user@host>show security policies policy-name p1 node0: -------------------------------------------------------------------------- From zone: trust, To zone: untrust Policy: p1, State: enabled, Index: 4, Scope Policy: 0, Sequence number: 1 Source addresses(excluded): as1 Destination addresses(excluded): as2 Applications: any Action: permit
This output summarizes the policy configuration.
Verifying the Policy Configuration Detail
Purpose
Verify that the policy and the negated source and destination address configurations are correct.
Action
From operational mode, enter the show security
policies policy-name p1 detail command.
user@host>show security policies policy-name p1 detail
Policy: p1, action-type: permit, State: enabled, Index: 4, Scope Policy: 0
Policy Type: Configured
Sequence number: 1
From zone: trust, To zone: untrust
Source addresses(excluded):
ad1(SOU-ADDR): 255.255.255.255/32
ad2(SOU-ADDR): 203.0.113.130/25
ad3(SOU-ADDR): 192.0.2.6 ~ 192.0.2.116
ad4(SOU-ADDR): 192.0.2.128/25
Destination addresses(excluded):
ad8(DES-ADDR): 198.51.100.1/24
ad9(DES-ADDR): 192.0.2.117 ~ 192.0.2.199
ad10(DES-ADDR): 198.51.100.0/24
ad11(DES-ADDR): 192.0.2.199 to 192.0.2.250
Application: any
IP protocol: 0, ALG: 0, Inactivity timeout: 0
Source port range: [0-0]
Destination port range: [0-0]
Per policy TCP Options: SYN check: No, SEQ check: No
This output summarizes the policy configuration and shows the names of negated source and destination addresses excluded from the policy.
Platform-Specific Policies, Address Books and Address Sets Behavior
- Platform-Specific DNS Names in Address Books Behavior
- Platform-Specific Addresses and Address Sets Behavior
Platform-Specific DNS Names in Address Books Behavior
Use Address books and Feature Explorer to confirm platform and release support for specific features.
Use the following table to review platform-specific behavior for your platform:
|
Platform |
Difference |
|---|---|
|
SRX Firewalls and vSRX3.0 |
|
Platform-Specific Addresses and Address Sets Behavior
|
Platform |
Difference Address Objects Per Security Policy |
|
|---|---|---|
|
SRX Firewalls |
There is a limit to the number of address objects that a policy can reference; the maximum number of address objects per policy is different for different platforms as shown in table below. See Best Practices for Defining Policies on SRX Firewalls for details on the maximum number of policies per context for SRX Firewalls. |
|
|
SRX5400 devices support a maximum of 16,000 address objects per policy and a maximum of 80,000 policies per context. |
||
