- play_arrow Overview
- play_arrow Onboarding
- play_arrow Additional Features and Services
- play_arrow Troubleshooting
How to Configure a Switch Proxy Server
This chapter provides information about configuring the Switch Proxy server for a Juniper Mist™ Edge appliance.
Mist Edge Switch Proxy Overview
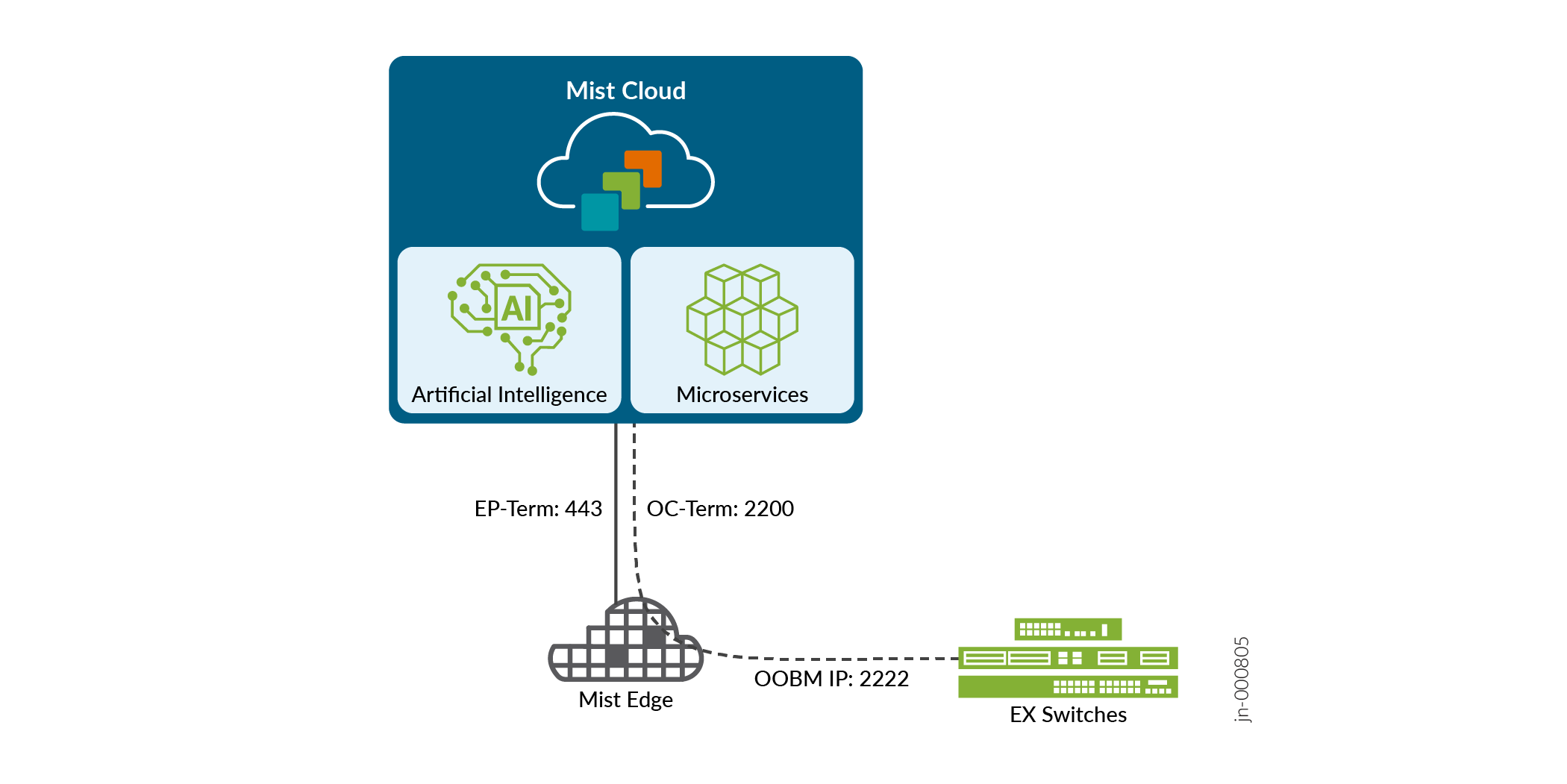
The switch proxy service in Juniper Mist™ Edge enables you to proxy all the data packets received from the Juniper EX series switches to the Juniper Mist™ cloud. You can benefit from this service when switches are behind an HTTP proxy or a firewall with port 2200 blocked. If a firewall exists between the Juniper Mist Edge device and the switch, you need to allow outbound access on TCP port 2222 (configurable) to the management port of the switch.
The following image illustrates the connectivity between a Juniper Mist Edge device, Juniper EX series switches, and the Juniper Mist cloud.
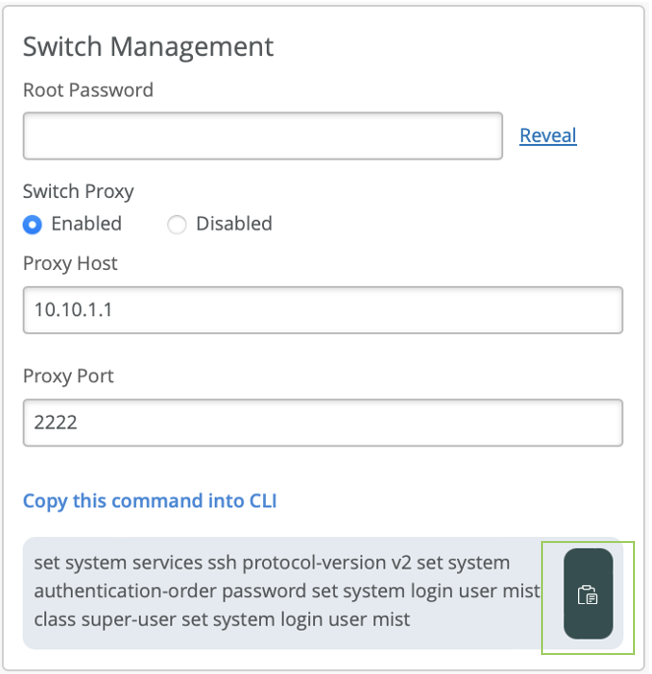
Configure a Switch Proxy
This topic describes how to enable the switch proxy service on Juniper Mist™ Edge and configure EX series switches to allow the cloud connection through Juniper Mist Edge.
Claim and configure Juniper Mist Edge. See Deploy Juniper Mist Edge at the Organization Level.
Configure the Juniper Mist Edge out-of-band management (OOBM) interface with a static IP address.
Juniper Networks EX Series switches must connect to a DNS server. Juniper Networks also recommends that you connect the switches to a network time protocol (NTP) server. The switch must connect to the Juniper Mist™ cloud architecture over the Internet. If a firewall exists between the cloud and the switch, you need to allow outbound access on TCP port 2200 to the management port of the switch.
You can configure a switch proxy at the organization level or the site level. In a site-level switch proxy configuration, you can configure each site to proxy to a different Juniper Mist Edge device. However, for an organization-level configuration, you can configure only one Juniper Mist Edge device to use the switch proxy service.
The process includes two main steps:
Configure the switch proxy service at the site or organization level to instantiate and run the mxocproxy service on the given Juniper Mist Edge device.
Copy the switch configuration blob from the dashboard and paste it into the switch console.
To configure the Juniper Mist Edge devices to run the switch proxy and EX switches to communicate to the switch proxy device using Juniper Mist Edge: