Configuration of SRX Series Devices and EX Series Switches
As discussed in Use Case # 1: Configuring Juniper Connected Security, Juniper Connected Security can be deployed in three ways, as shown in Figure 1:
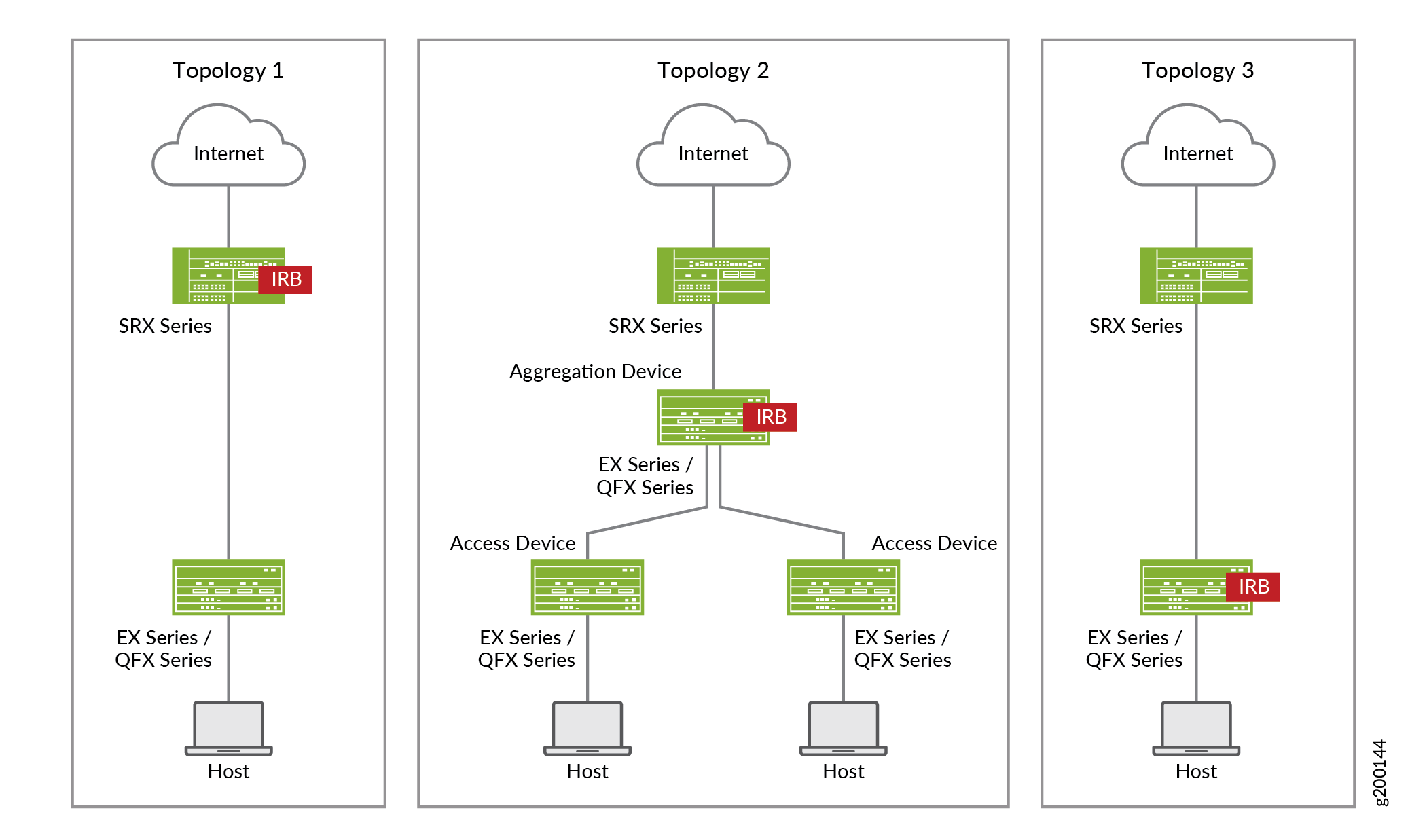
Table 1 provides more detail on these deployment options.
Topology 1 |
Topology 2 |
Topology 3 |
|---|---|---|
EX Series or QFX Series device as Layer 2 switch |
EX Series or QFX Series device (access switch) as Layer 2 switch EX Series or QFX Series device (aggregation switch) as Layer 3 switch |
EX Series or QFX Series device as Layer 2/Layer 3 switch |
SRX Series device as firewall in Layer 3 mode |
SRX Series device as firewall in Layer 3 mode |
SRX Series device as firewall in Layer 3 mode |
IRB / VLAN tagging on SRX Series device |
IRB / VLAN tagging on EX Series or QFX Series device (aggregation switch) |
IRB / VLAN tagging on EX Series or QFX Series switch |
Configuration files for each topology are provided below.
These configurations are captured from a lab environment, and are provided for reference only. Actual configurations may vary based on the specific requirements of your environment.
Configuration Files for Topology #1
SRX Series Firewall Configuration
set version 15.1X49-D80.4 set system host-name SRX1500-WF set system time-zone America/New_York set system root-authentication encrypted-password "$ABC123" set system name-server 8.8.8.8 set system services ssh max-sessions-per-connection 32 set system services telnet set system services xnm-clear-text set system services netconf ssh set system services dhcp-local-server group wan-dhcp interface irb.12 set system syslog user * any emergency set system syslog host 192.168.10.4 structured-data set system syslog file messages any any set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system syslog file default-log-messages any info set system syslog file default-log-messages match "(requested 'commit' operation)|(requested 'commit synchronize' operation)|(copying configuration to juniper.save)|(commit complete)|ifAdminStatus|(FRU power)|(FRU removal)|(FRU insertion)|(link UP)|transitioned|Transferred|transfer-file|(license add)|(license delete)|(package -X update)|(package -X delete)|(FRU Online)|(FRU Offline)|(plugged in)|(unplugged)|GRES" set system syslog file default-log-messages structured-data set system max-configurations-on-flash 5 set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set system ntp server 203.0.113.1 set services application-identification set services ssl initiation profile aamw-ssl trusted-ca aamw-secintel-ca set services ssl initiation profile aamw-ssl trusted-ca aamw-cloud-ca set services ssl initiation profile aamw-ssl client-certificate aamw-srx-cert set services ssl initiation profile aamw-ssl actions crl disable set services security-intelligence url https://10.13.107.164:443/api/v1/manifest.xml set services security-intelligence authentication auth-token ABC123 set services security-intelligence profile TPP_CC category CC set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 1 set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 2 set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 3 set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 4 set services security-intelligence profile TPP_CC rule Rule-1 then action permit set services security-intelligence profile TPP_CC rule Rule-1 then log set services security-intelligence profile TPP_CC rule Rule-2 match threat-level 5 set services security-intelligence profile TPP_CC rule Rule-2 match threat-level 6 set services security-intelligence profile TPP_CC rule Rule-2 match threat-level 7 set services security-intelligence profile TPP_CC rule Rule-2 then action permit set services security-intelligence profile TPP_CC rule Rule-2 then log set services security-intelligence profile TPP_CC rule Rule-3 match threat-level 8 set services security-intelligence profile TPP_CC rule Rule-3 match threat-level 9 set services security-intelligence profile TPP_CC rule Rule-3 match threat-level 10 set services security-intelligence profile TPP_CC rule Rule-3 then action block drop set services security-intelligence profile TPP_CC rule Rule-3 then log set services security-intelligence profile TPP_Infected-Hosts category Infected-Hosts set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 1 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 2 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 3 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 4 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 5 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 6 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 then action permit set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 then log set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 7 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 8 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 9 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 10 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 then action block drop set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 then log set services security-intelligence policy TPP CC TPP_CC set services security-intelligence policy TPP Infected-Hosts TPP_Infected-Hosts set services advanced-anti-malware connection url https://srxapi.us-west-2.sky.junipersecurity.net set services advanced-anti-malware connection authentication tls-profile aamw-ssl set services advanced-anti-malware policy TPP http inspection-profile default_profile set services advanced-anti-malware policy TPP http action block set services advanced-anti-malware policy TPP http notification log set services advanced-anti-malware policy TPP verdict-threshold 8 set services advanced-anti-malware policy TPP fallback-options action permit set services advanced-anti-malware policy TPP fallback-options notification log set services advanced-anti-malware policy TPP default-notification log set services advanced-anti-malware policy TPP whitelist-notification log set services advanced-anti-malware policy TPP blacklist-notification log set security log mode stream set security log format sd-syslog set security log source-address 192.168.10.1 set security log stream TRAFFIC category all set security log stream TRAFFIC host 192.168.10.4 set security log stream TRAFFIC host port 514 set security pki ca-profile All-Trusted-CA-Def_1 ca-identity All-Trusted-CA-Def_1 set security pki ca-profile All-Trusted-CA-Def_2 ca-identity All-Trusted-CA-Def_2 set security pki ca-profile All-Trusted-CA-Def_3 ca-identity All-Trusted-CA-Def_3 set security pki ca-profile All-Trusted-CA-Def_4 ca-identity All-Trusted-CA-Def_4 set security pki ca-profile All-Trusted-CA-Def_5 ca-identity All-Trusted-CA-Def_5 set security pki ca-profile All-Trusted-CA-Def_6 ca-identity All-Trusted-CA-Def_6 set security pki ca-profile All-Trusted-CA-Def_7 ca-identity All-Trusted-CA-Def_7 set security pki ca-profile All-Trusted-CA-Def_8 ca-identity All-Trusted-CA-Def_8 set security pki ca-profile All-Trusted-CA-Def_9 ca-identity All-Trusted-CA-Def_9 set security pki ca-profile All-Trusted-CA-Def_10 ca-identity All-Trusted-CA-Def_10 set security pki ca-profile All-Trusted-CA-Def_11 ca-identity All-Trusted-CA-Def_11 set security pki ca-profile All-Trusted-CA-Def_12 ca-identity All-Trusted-CA-Def_12 set security pki ca-profile All-Trusted-CA-Def_13 ca-identity All-Trusted-CA-Def_13 set security pki ca-profile All-Trusted-CA-Def_14 ca-identity All-Trusted-CA-Def_14 set security pki ca-profile All-Trusted-CA-Def_15 ca-identity All-Trusted-CA-Def_15 set security pki ca-profile All-Trusted-CA-Def_16 ca-identity All-Trusted-CA-Def_16 set security pki ca-profile All-Trusted-CA-Def_17 ca-identity All-Trusted-CA-Def_17 set security pki ca-profile All-Trusted-CA-Def_18 ca-identity All-Trusted-CA-Def_18 set security pki ca-profile All-Trusted-CA-Def_19 ca-identity All-Trusted-CA-Def_19 set security pki ca-profile All-Trusted-CA-Def_20 ca-identity All-Trusted-CA-Def_20 set security pki ca-profile All-Trusted-CA-Def_21 ca-identity All-Trusted-CA-Def_21 set security pki ca-profile All-Trusted-CA-Def_22 ca-identity All-Trusted-CA-Def_22 set security pki ca-profile All-Trusted-CA-Def_23 ca-identity All-Trusted-CA-Def_23 set security pki ca-profile All-Trusted-CA-Def_24 ca-identity All-Trusted-CA-Def_24 set security pki ca-profile All-Trusted-CA-Def_25 ca-identity All-Trusted-CA-Def_25 set security pki ca-profile All-Trusted-CA-Def_26 ca-identity All-Trusted-CA-Def_26 set security pki ca-profile All-Trusted-CA-Def_27 ca-identity All-Trusted-CA-Def_27 set security pki ca-profile All-Trusted-CA-Def_28 ca-identity All-Trusted-CA-Def_28 set security pki ca-profile All-Trusted-CA-Def_29 ca-identity All-Trusted-CA-Def_29 set security pki ca-profile All-Trusted-CA-Def_30 ca-identity All-Trusted-CA-Def_30 set security pki ca-profile All-Trusted-CA-Def_31 ca-identity All-Trusted-CA-Def_31 set security pki ca-profile All-Trusted-CA-Def_32 ca-identity All-Trusted-CA-Def_32 set security pki ca-profile All-Trusted-CA-Def_33 ca-identity All-Trusted-CA-Def_33 set security pki ca-profile All-Trusted-CA-Def_34 ca-identity All-Trusted-CA-Def_34 set security pki ca-profile All-Trusted-CA-Def_35 ca-identity All-Trusted-CA-Def_35 set security pki ca-profile All-Trusted-CA-Def_36 ca-identity All-Trusted-CA-Def_36 set security pki ca-profile All-Trusted-CA-Def_37 ca-identity All-Trusted-CA-Def_37 set security pki ca-profile All-Trusted-CA-Def_38 ca-identity All-Trusted-CA-Def_38 set security pki ca-profile All-Trusted-CA-Def_39 ca-identity All-Trusted-CA-Def_39 set security pki ca-profile All-Trusted-CA-Def_40 ca-identity All-Trusted-CA-Def_40 set security pki ca-profile All-Trusted-CA-Def_41 ca-identity All-Trusted-CA-Def_41 set security pki ca-profile All-Trusted-CA-Def_42 ca-identity All-Trusted-CA-Def_42 set security pki ca-profile All-Trusted-CA-Def_43 ca-identity All-Trusted-CA-Def_43 set security pki ca-profile All-Trusted-CA-Def_44 ca-identity All-Trusted-CA-Def_44 set security pki ca-profile All-Trusted-CA-Def_45 ca-identity All-Trusted-CA-Def_45 set security pki ca-profile All-Trusted-CA-Def_46 ca-identity All-Trusted-CA-Def_46 set security pki ca-profile All-Trusted-CA-Def_47 ca-identity All-Trusted-CA-Def_47 set security pki ca-profile All-Trusted-CA-Def_48 ca-identity All-Trusted-CA-Def_48 set security pki ca-profile All-Trusted-CA-Def_49 ca-identity All-Trusted-CA-Def_49 set security pki ca-profile All-Trusted-CA-Def_50 ca-identity All-Trusted-CA-Def_50 set security pki ca-profile All-Trusted-CA-Def_51 ca-identity All-Trusted-CA-Def_51 set security pki ca-profile All-Trusted-CA-Def_52 ca-identity All-Trusted-CA-Def_52 set security pki ca-profile All-Trusted-CA-Def_53 ca-identity All-Trusted-CA-Def_53 set security pki ca-profile All-Trusted-CA-Def_54 ca-identity All-Trusted-CA-Def_54 set security pki ca-profile All-Trusted-CA-Def_55 ca-identity All-Trusted-CA-Def_55 set security pki ca-profile All-Trusted-CA-Def_56 ca-identity All-Trusted-CA-Def_56 set security pki ca-profile All-Trusted-CA-Def_57 ca-identity All-Trusted-CA-Def_57 set security pki ca-profile All-Trusted-CA-Def_58 ca-identity All-Trusted-CA-Def_58 set security pki ca-profile All-Trusted-CA-Def_59 ca-identity All-Trusted-CA-Def_59 set security pki ca-profile All-Trusted-CA-Def_60 ca-identity All-Trusted-CA-Def_60 set security pki ca-profile All-Trusted-CA-Def_61 ca-identity All-Trusted-CA-Def_61 set security pki ca-profile All-Trusted-CA-Def_62 ca-identity All-Trusted-CA-Def_62 set security pki ca-profile All-Trusted-CA-Def_63 ca-identity All-Trusted-CA-Def_63 set security pki ca-profile All-Trusted-CA-Def_64 ca-identity All-Trusted-CA-Def_64 set security pki ca-profile All-Trusted-CA-Def_65 ca-identity All-Trusted-CA-Def_65 set security pki ca-profile All-Trusted-CA-Def_66 ca-identity All-Trusted-CA-Def_66 set security pki ca-profile All-Trusted-CA-Def_67 ca-identity All-Trusted-CA-Def_67 set security pki ca-profile All-Trusted-CA-Def_68 ca-identity All-Trusted-CA-Def_68 set security pki ca-profile All-Trusted-CA-Def_69 ca-identity All-Trusted-CA-Def_69 set security pki ca-profile All-Trusted-CA-Def_70 ca-identity All-Trusted-CA-Def_70 set security pki ca-profile All-Trusted-CA-Def_71 ca-identity All-Trusted-CA-Def_71 set security pki ca-profile All-Trusted-CA-Def_72 ca-identity All-Trusted-CA-Def_72 set security pki ca-profile All-Trusted-CA-Def_73 ca-identity All-Trusted-CA-Def_73 set security pki ca-profile All-Trusted-CA-Def_74 ca-identity All-Trusted-CA-Def_74 set security pki ca-profile All-Trusted-CA-Def_75 ca-identity All-Trusted-CA-Def_75 set security pki ca-profile All-Trusted-CA-Def_76 ca-identity All-Trusted-CA-Def_76 set security pki ca-profile All-Trusted-CA-Def_77 ca-identity All-Trusted-CA-Def_77 set security pki ca-profile All-Trusted-CA-Def_78 ca-identity All-Trusted-CA-Def_78 set security pki ca-profile All-Trusted-CA-Def_79 ca-identity All-Trusted-CA-Def_79 set security pki ca-profile All-Trusted-CA-Def_80 ca-identity All-Trusted-CA-Def_80 set security pki ca-profile All-Trusted-CA-Def_81 ca-identity All-Trusted-CA-Def_81 set security pki ca-profile All-Trusted-CA-Def_82 ca-identity All-Trusted-CA-Def_82 set security pki ca-profile All-Trusted-CA-Def_83 ca-identity All-Trusted-CA-Def_83 set security pki ca-profile All-Trusted-CA-Def_84 ca-identity All-Trusted-CA-Def_84 set security pki ca-profile All-Trusted-CA-Def_85 ca-identity All-Trusted-CA-Def_85 set security pki ca-profile All-Trusted-CA-Def_86 ca-identity All-Trusted-CA-Def_86 set security pki ca-profile All-Trusted-CA-Def_87 ca-identity All-Trusted-CA-Def_87 set security pki ca-profile All-Trusted-CA-Def_88 ca-identity All-Trusted-CA-Def_88 set security pki ca-profile All-Trusted-CA-Def_89 ca-identity All-Trusted-CA-Def_89 set security pki ca-profile All-Trusted-CA-Def_90 ca-identity All-Trusted-CA-Def_90 set security pki ca-profile All-Trusted-CA-Def_91 ca-identity All-Trusted-CA-Def_91 set security pki ca-profile All-Trusted-CA-Def_92 ca-identity All-Trusted-CA-Def_92 set security pki ca-profile All-Trusted-CA-Def_93 ca-identity All-Trusted-CA-Def_93 set security pki ca-profile All-Trusted-CA-Def_94 ca-identity All-Trusted-CA-Def_94 set security pki ca-profile All-Trusted-CA-Def_95 ca-identity All-Trusted-CA-Def_95 set security pki ca-profile All-Trusted-CA-Def_96 ca-identity All-Trusted-CA-Def_96 set security pki ca-profile All-Trusted-CA-Def_97 ca-identity All-Trusted-CA-Def_97 set security pki ca-profile All-Trusted-CA-Def_98 ca-identity All-Trusted-CA-Def_98 set security pki ca-profile All-Trusted-CA-Def_99 ca-identity All-Trusted-CA-Def_99 set security pki ca-profile All-Trusted-CA-Def_100 ca-identity All-Trusted-CA-Def_100 set security pki ca-profile All-Trusted-CA-Def_101 ca-identity All-Trusted-CA-Def_101 set security pki ca-profile All-Trusted-CA-Def_102 ca-identity All-Trusted-CA-Def_102 set security pki ca-profile All-Trusted-CA-Def_103 ca-identity All-Trusted-CA-Def_103 set security pki ca-profile All-Trusted-CA-Def_104 ca-identity All-Trusted-CA-Def_104 set security pki ca-profile All-Trusted-CA-Def_105 ca-identity All-Trusted-CA-Def_105 set security pki ca-profile All-Trusted-CA-Def_106 ca-identity All-Trusted-CA-Def_106 set security pki ca-profile All-Trusted-CA-Def_107 ca-identity All-Trusted-CA-Def_107 set security pki ca-profile All-Trusted-CA-Def_108 ca-identity All-Trusted-CA-Def_108 set security pki ca-profile All-Trusted-CA-Def_109 ca-identity All-Trusted-CA-Def_109 set security pki ca-profile All-Trusted-CA-Def_110 ca-identity All-Trusted-CA-Def_110 set security pki ca-profile All-Trusted-CA-Def_111 ca-identity All-Trusted-CA-Def_111 set security pki ca-profile All-Trusted-CA-Def_112 ca-identity All-Trusted-CA-Def_112 set security pki ca-profile All-Trusted-CA-Def_114 ca-identity All-Trusted-CA-Def_114 set security pki ca-profile All-Trusted-CA-Def_115 ca-identity All-Trusted-CA-Def_115 set security pki ca-profile All-Trusted-CA-Def_116 ca-identity All-Trusted-CA-Def_116 set security pki ca-profile All-Trusted-CA-Def_117 ca-identity All-Trusted-CA-Def_117 set security pki ca-profile All-Trusted-CA-Def_118 ca-identity All-Trusted-CA-Def_118 set security pki ca-profile All-Trusted-CA-Def_119 ca-identity All-Trusted-CA-Def_119 set security pki ca-profile All-Trusted-CA-Def_120 ca-identity All-Trusted-CA-Def_120 set security pki ca-profile All-Trusted-CA-Def_121 ca-identity All-Trusted-CA-Def_121 set security pki ca-profile All-Trusted-CA-Def_122 ca-identity All-Trusted-CA-Def_122 set security pki ca-profile All-Trusted-CA-Def_123 ca-identity All-Trusted-CA-Def_123 set security pki ca-profile All-Trusted-CA-Def_124 ca-identity All-Trusted-CA-Def_124 set security pki ca-profile All-Trusted-CA-Def_125 ca-identity All-Trusted-CA-Def_125 set security pki ca-profile All-Trusted-CA-Def_126 ca-identity All-Trusted-CA-Def_126 set security pki ca-profile All-Trusted-CA-Def_127 ca-identity All-Trusted-CA-Def_127 set security pki ca-profile All-Trusted-CA-Def_128 ca-identity All-Trusted-CA-Def_128 set security pki ca-profile All-Trusted-CA-Def_129 ca-identity All-Trusted-CA-Def_129 set security pki ca-profile All-Trusted-CA-Def_130 ca-identity All-Trusted-CA-Def_130 set security pki ca-profile All-Trusted-CA-Def_131 ca-identity All-Trusted-CA-Def_131 set security pki ca-profile All-Trusted-CA-Def_132 ca-identity All-Trusted-CA-Def_132 set security pki ca-profile All-Trusted-CA-Def_133 ca-identity All-Trusted-CA-Def_133 set security pki ca-profile All-Trusted-CA-Def_134 ca-identity All-Trusted-CA-Def_134 set security pki ca-profile All-Trusted-CA-Def_135 ca-identity All-Trusted-CA-Def_135 set security pki ca-profile All-Trusted-CA-Def_136 ca-identity All-Trusted-CA-Def_136 set security pki ca-profile All-Trusted-CA-Def_137 ca-identity All-Trusted-CA-Def_137 set security pki ca-profile All-Trusted-CA-Def_138 ca-identity All-Trusted-CA-Def_138 set security pki ca-profile All-Trusted-CA-Def_139 ca-identity All-Trusted-CA-Def_139 set security pki ca-profile All-Trusted-CA-Def_140 ca-identity All-Trusted-CA-Def_140 set security pki ca-profile All-Trusted-CA-Def_141 ca-identity All-Trusted-CA-Def_141 set security pki ca-profile All-Trusted-CA-Def_142 ca-identity All-Trusted-CA-Def_142 set security pki ca-profile All-Trusted-CA-Def_143 ca-identity All-Trusted-CA-Def_143 set security pki ca-profile All-Trusted-CA-Def_144 ca-identity All-Trusted-CA-Def_144 set security pki ca-profile All-Trusted-CA-Def_145 ca-identity All-Trusted-CA-Def_145 set security pki ca-profile All-Trusted-CA-Def_146 ca-identity All-Trusted-CA-Def_146 set security pki ca-profile All-Trusted-CA-Def_147 ca-identity All-Trusted-CA-Def_147 set security pki ca-profile All-Trusted-CA-Def_148 ca-identity All-Trusted-CA-Def_148 set security pki ca-profile All-Trusted-CA-Def_149 ca-identity All-Trusted-CA-Def_149 set security pki ca-profile All-Trusted-CA-Def_150 ca-identity All-Trusted-CA-Def_150 set security pki ca-profile All-Trusted-CA-Def_151 ca-identity All-Trusted-CA-Def_151 set security pki ca-profile All-Trusted-CA-Def_152 ca-identity All-Trusted-CA-Def_152 set security pki ca-profile All-Trusted-CA-Def_153 ca-identity All-Trusted-CA-Def_153 set security pki ca-profile All-Trusted-CA-Def_154 ca-identity All-Trusted-CA-Def_154 set security pki ca-profile All-Trusted-CA-Def_155 ca-identity All-Trusted-CA-Def_155 set security pki ca-profile ssl-inspect-ca ca-identity ssl-inspect-ca set security pki ca-profile ssl-ca ca-identity ssl-ca set security pki ca-profile aamw-ca ca-identity deviceCA set security pki ca-profile aamw-ca enrollment url http://ca.junipersecurity.net:8080/ejbca/publicweb/apply/scep/SRX/pkiclient.exe set security pki ca-profile aamw-ca revocation-check disable set security pki ca-profile aamw-ca revocation-check crl url http://va.junipersecurity.net/ca/deviceCA.crl set security pki ca-profile aamw-secintel-ca ca-identity JUNIPER set security pki ca-profile aamw-secintel-ca revocation-check crl url http://va.junipersecurity.net/ca/current.crl set security pki ca-profile aamw-cloud-ca ca-identity JUNIPER_CLOUD set security pki ca-profile aamw-cloud-ca revocation-check crl url http://va.junipersecurity.net/ca/cloudCA.crl set security pki ca-profile-group All-Trusted-CA-Def cert-base-count 155 set security address-book global address JSD_192.168.10.1/24 192.168.10.0/24 set security address-book global address JSD_192.168.11.1/24 192.168.11.0/24 set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.10.1/24 set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.11.1/24 set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match destination-address any set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match application any set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 then permit application-services security-intelligence-policy TPP set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 then permit application-services advanced-anti-malware-policy TPP set security policies from-zone trust to-zone untrust policy t-u match source-address any set security policies from-zone trust to-zone untrust policy t-u match destination-address any set security policies from-zone trust to-zone untrust policy t-u match application any set security policies from-zone trust to-zone untrust policy t-u then permit set security policies global policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.10.1/24 set security policies global policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.11.1/24 set security policies global policy PolicyEnforcer-Rule1-1 match destination-address any set security policies global policy PolicyEnforcer-Rule1-1 match application any set security policies global policy PolicyEnforcer-Rule1-1 then permit application-services security-intelligence-policy TPP set security policies global policy PolicyEnforcer-Rule1-1 then permit application-services advanced-anti-malware-policy TPP set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces irb.12 set security zones security-zone trust interfaces irb.14 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces irb.13 set interfaces ge-0/0/0 unit 0 family ethernet-switching interface-mode trunk set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members VLAN12 set interfaces ge-0/0/1 unit 0 family ethernet-switching interface-mode trunk set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members VLAN14 set interfaces ge-0/0/2 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/2 unit 0 family ethernet-switching vlan members VLAN13 set interfaces fxp0 unit 0 family inet address 10.13.107.186/23 set interfaces irb unit 12 family inet address 192.168.10.1/24 set interfaces irb unit 13 family inet address 192.168.231.1/24 set interfaces irb unit 14 family inet address 192.168.11.1/24 set snmp trap-group space targets 10.13.107.162 set routing-options static route 172.28.0.0/16 next-hop 10.13.106.1 set routing-options static route 10.13.0.0/16 next-hop 10.13.106.1 set routing-options static route 0.0.0.0/0 next-hop 192.168.231.10 set routing-options static route 172.29.0.0/16 next-hop 10.13.106.1 set routing-options static route 172.30.76.0/23 next-hop 10.13.106.1 set routing-options static route 10.163.69.44/30 next-hop 10.13.106.1 set protocols l2-learning global-mode switching set access address-assignment pool wan-1 family inet network 192.168.10.1/24 set access address-assignment pool wan-1 family inet range wan-1-range low 192.168.10.10 set access address-assignment pool wan-1 family inet range wan-1-range high 192.168.10.20 set access address-assignment pool wan-1 family inet dhcp-attributes maximum-lease-time 86400 set access address-assignment pool wan-1 family inet dhcp-attributes name-server 8.8.8.8 set access address-assignment pool wan-1 family inet dhcp-attributes router 192.168.10.1 set vlans VLAN12 vlan-id 12 set vlans VLAN12 l3-interface irb.12 set vlans VLAN13 vlan-id 13 set vlans VLAN13 l3-interface irb.13 set vlans VLAN14 vlan-id 14 set vlans VLAN14 l3-interface irb.14
EX4300 Access Switch Configuration
set version 15.1R5.5 set system host-name EX4300-1 set system auto-snapshot set system time-zone America/New_York set system root-authentication encrypted-password "$ABC123" set system services ftp set system services ssh max-sessions-per-connection 32 set system services telnet set system services netconf ssh set system syslog user * any emergency set system syslog file messages any notice set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system syslog file default-log-messages any any set system syslog file default-log-messages match "(requested 'commit' operation)|(requested 'commit synchronize' operation)|(copying configuration to juniper.save)|(commit complete)|ifAdminStatus|(FRU power)|(FRU removal)|(FRU insertion)|(link UP)|transitioned|Transferred|transfer-file|(license add)|(license delete)|(package -X update)|(package -X delete)|(FRU Online)|(FRU Offline)|(plugged in)|(unplugged)|CFMD_CCM_DEFECT| LFMD_3AH | RPD_MPLS_PATH_BFD|(Master Unchanged, Members Changed)|(Master Changed, Members Changed)|(Master Detected, Members Changed)|(vc add)|(vc delete)|(Master detected)|(Master changed)|(Backup detected)|(Backup changed)|(interface vcp-)" set system syslog file default-log-messages structured-data set system ntp server 203.0.113.1 set interfaces ge-0/0/1 unit 0 family ethernet-switching interface-mode trunk set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members VLAN99 set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members VLAN14 set interfaces ge-0/0/12 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/12 unit 0 family ethernet-switching vlan members VLAN14 set interfaces me0 unit 0 family inet address 10.13.107.181/23 set snmp trap-group space targets 10.13.107.162 set routing-options static route 0.0.0.0/0 next-hop 10.13.106.1 set protocols l2-learning global-mac-table-aging-time 120 set protocols lldp interface all set protocols lldp-med interface all set protocols igmp-snooping vlan default set vlans VLAN14 vlan-id 14 set vlans VLAN99 vlan-id 99
EX2200 Switch Configuration
In this topology, the EX2200 switch acts as a simple default gateway to the Internet. It does not play any role in the Juniper Connected Security solution.
set version 15.1R5.5 set system host-name EX2200-INTERNET set system root-authentication encrypted-password "$ABC123" set system services ftp set system services ssh set system services telnet set system syslog user * any emergency set system syslog file messages any notice set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set interfaces ge-0/0/13 unit 0 family ethernet-switching port-mode access set interfaces ge-0/0/13 unit 0 family ethernet-switching vlan members VLAN13 set interfaces ge-0/0/47 description "to DMZ ge/0/015" set interfaces ge-0/0/47 unit 0 family inet address 198.51.100.2/30 set interfaces me0 unit 0 family inet address 10.13.107.188/23 set interfaces vlan unit 13 family inet address 192.168.231.10/24 set routing-options static route 0.0.0.0/0 next-hop 198.51.100.1 set routing-options static route 10.13.0.0/16 next-hop 10.13.106.1 set routing-options static route 172.28.0.0/16 next-hop 10.13.106.1 set routing-options static route 192.168.0.0/16 next-hop 192.168.231.1 set protocols igmp-snooping vlan all set protocols lldp interface all set protocols lldp-med interface all set vlans VLAN13 vlan-id 13 set vlans VLAN13 l3-interface vlan.13
Configuration Files for Topology #2
- SRX Series Firewall Configuration
- EX4300-1 Access Switch Configuration
- EX4300-2 Access Switch Configuration
- EX2200 Aggregation Switch Configuration
- EX2200 Internet Gateway Switch Configuration
SRX Series Firewall Configuration
set version 15.1X49-D80.4 set system host-name SRX1500-1 set system time-zone America/New_York set system root-authentication encrypted-password "$ABC123" set system name-server 8.8.8.8 set system services ssh max-sessions-per-connection 32 set system services telnet set system services xnm-clear-text set system services netconf ssh set system syslog user * any emergency set system syslog host 192.168.10.4 structured-data set system syslog file messages any any set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system syslog file default-log-messages any info set system syslog file default-log-messages match "(requested 'commit' operation)|(requested 'commit synchronize' operation)|(copying configuration to juniper.save)|(commit complete)|ifAdminStatus|(FRU power)|(FRU removal)|(FRU insertion)|(link UP)|transitioned|Transferred|transfer-file|(license add)|(license delete)|(package -X update)|(package -X delete)|(FRU Online)|(FRU Offline)|(plugged in)|(unplugged)|GRES" set system syslog file default-log-messages structured-data set system max-configurations-on-flash 5 set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set system ntp server 203.0.113.1 set services application-identification set services ssl initiation profile aamw-ssl actions crl disable set services security-intelligence url https://10.13.107.164:443/api/v1/manifest.xml set services security-intelligence authentication auth-token ABC123 set services security-intelligence profile TPP_CC category CC set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 1 set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 2 set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 3 set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 4 set services security-intelligence profile TPP_CC rule Rule-1 then action permit set services security-intelligence profile TPP_CC rule Rule-1 then log set services security-intelligence profile TPP_CC rule Rule-2 match threat-level 5 set services security-intelligence profile TPP_CC rule Rule-2 match threat-level 6 set services security-intelligence profile TPP_CC rule Rule-2 match threat-level 7 set services security-intelligence profile TPP_CC rule Rule-2 then action permit set services security-intelligence profile TPP_CC rule Rule-2 then log set services security-intelligence profile TPP_CC rule Rule-3 match threat-level 8 set services security-intelligence profile TPP_CC rule Rule-3 match threat-level 9 set services security-intelligence profile TPP_CC rule Rule-3 match threat-level 10 set services security-intelligence profile TPP_CC rule Rule-3 then action block drop set services security-intelligence profile TPP_CC rule Rule-3 then log set services security-intelligence profile TPP_Infected-Hosts category Infected-Hosts set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 1 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 2 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 3 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 4 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 5 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 6 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 then action permit set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 then log set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 7 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 8 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 9 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 10 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 then action block drop set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 then log set services security-intelligence policy TPP CC TPP_CC set services security-intelligence policy TPP Infected-Hosts TPP_Infected-Hosts set services advanced-anti-malware connection url https://srxapi.us-west-2.sky.junipersecurity.net set services advanced-anti-malware connection authentication tls-profile aamw-ssl set services advanced-anti-malware policy TPP http inspection-profile default_profile set services advanced-anti-malware policy TPP http action block set services advanced-anti-malware policy TPP http notification log set services advanced-anti-malware policy TPP verdict-threshold 8 set services advanced-anti-malware policy TPP fallback-options action permit set services advanced-anti-malware policy TPP fallback-options notification log set services advanced-anti-malware policy TPP default-notification log set services advanced-anti-malware policy TPP whitelist-notification log set services advanced-anti-malware policy TPP blacklist-notification log set security log mode stream set security log format sd-syslog set security log source-address 192.168.1.254 set security log stream TRAFFIC category all set security log stream TRAFFIC host 192.168.10.4 set security log stream TRAFFIC host port 514 set security pki ca-profile All-Trusted-CA-Def_1 ca-identity All-Trusted-CA-Def_1 set security pki ca-profile All-Trusted-CA-Def_2 ca-identity All-Trusted-CA-Def_2 set security pki ca-profile All-Trusted-CA-Def_3 ca-identity All-Trusted-CA-Def_3 set security pki ca-profile All-Trusted-CA-Def_4 ca-identity All-Trusted-CA-Def_4 set security pki ca-profile All-Trusted-CA-Def_5 ca-identity All-Trusted-CA-Def_5 set security pki ca-profile All-Trusted-CA-Def_6 ca-identity All-Trusted-CA-Def_6 set security pki ca-profile All-Trusted-CA-Def_7 ca-identity All-Trusted-CA-Def_7 set security pki ca-profile All-Trusted-CA-Def_8 ca-identity All-Trusted-CA-Def_8 set security pki ca-profile All-Trusted-CA-Def_9 ca-identity All-Trusted-CA-Def_9 set security pki ca-profile All-Trusted-CA-Def_10 ca-identity All-Trusted-CA-Def_10 set security pki ca-profile All-Trusted-CA-Def_11 ca-identity All-Trusted-CA-Def_11 set security pki ca-profile All-Trusted-CA-Def_12 ca-identity All-Trusted-CA-Def_12 set security pki ca-profile All-Trusted-CA-Def_13 ca-identity All-Trusted-CA-Def_13 set security pki ca-profile All-Trusted-CA-Def_14 ca-identity All-Trusted-CA-Def_14 set security pki ca-profile All-Trusted-CA-Def_15 ca-identity All-Trusted-CA-Def_15 set security pki ca-profile All-Trusted-CA-Def_16 ca-identity All-Trusted-CA-Def_16 set security pki ca-profile All-Trusted-CA-Def_17 ca-identity All-Trusted-CA-Def_17 set security pki ca-profile All-Trusted-CA-Def_18 ca-identity All-Trusted-CA-Def_18 set security pki ca-profile All-Trusted-CA-Def_19 ca-identity All-Trusted-CA-Def_19 set security pki ca-profile All-Trusted-CA-Def_20 ca-identity All-Trusted-CA-Def_20 set security pki ca-profile All-Trusted-CA-Def_21 ca-identity All-Trusted-CA-Def_21 set security pki ca-profile All-Trusted-CA-Def_22 ca-identity All-Trusted-CA-Def_22 set security pki ca-profile All-Trusted-CA-Def_23 ca-identity All-Trusted-CA-Def_23 set security pki ca-profile All-Trusted-CA-Def_24 ca-identity All-Trusted-CA-Def_24 set security pki ca-profile All-Trusted-CA-Def_25 ca-identity All-Trusted-CA-Def_25 set security pki ca-profile All-Trusted-CA-Def_26 ca-identity All-Trusted-CA-Def_26 set security pki ca-profile All-Trusted-CA-Def_27 ca-identity All-Trusted-CA-Def_27 set security pki ca-profile All-Trusted-CA-Def_28 ca-identity All-Trusted-CA-Def_28 set security pki ca-profile All-Trusted-CA-Def_29 ca-identity All-Trusted-CA-Def_29 set security pki ca-profile All-Trusted-CA-Def_30 ca-identity All-Trusted-CA-Def_30 set security pki ca-profile All-Trusted-CA-Def_31 ca-identity All-Trusted-CA-Def_31 set security pki ca-profile All-Trusted-CA-Def_32 ca-identity All-Trusted-CA-Def_32 set security pki ca-profile All-Trusted-CA-Def_33 ca-identity All-Trusted-CA-Def_33 set security pki ca-profile All-Trusted-CA-Def_34 ca-identity All-Trusted-CA-Def_34 set security pki ca-profile All-Trusted-CA-Def_35 ca-identity All-Trusted-CA-Def_35 set security pki ca-profile All-Trusted-CA-Def_36 ca-identity All-Trusted-CA-Def_36 set security pki ca-profile All-Trusted-CA-Def_37 ca-identity All-Trusted-CA-Def_37 set security pki ca-profile All-Trusted-CA-Def_38 ca-identity All-Trusted-CA-Def_38 set security pki ca-profile All-Trusted-CA-Def_39 ca-identity All-Trusted-CA-Def_39 set security pki ca-profile All-Trusted-CA-Def_40 ca-identity All-Trusted-CA-Def_40 set security pki ca-profile All-Trusted-CA-Def_41 ca-identity All-Trusted-CA-Def_41 set security pki ca-profile All-Trusted-CA-Def_42 ca-identity All-Trusted-CA-Def_42 set security pki ca-profile All-Trusted-CA-Def_43 ca-identity All-Trusted-CA-Def_43 set security pki ca-profile All-Trusted-CA-Def_44 ca-identity All-Trusted-CA-Def_44 set security pki ca-profile All-Trusted-CA-Def_45 ca-identity All-Trusted-CA-Def_45 set security pki ca-profile All-Trusted-CA-Def_46 ca-identity All-Trusted-CA-Def_46 set security pki ca-profile All-Trusted-CA-Def_47 ca-identity All-Trusted-CA-Def_47 set security pki ca-profile All-Trusted-CA-Def_48 ca-identity All-Trusted-CA-Def_48 set security pki ca-profile All-Trusted-CA-Def_49 ca-identity All-Trusted-CA-Def_49 set security pki ca-profile All-Trusted-CA-Def_50 ca-identity All-Trusted-CA-Def_50 set security pki ca-profile All-Trusted-CA-Def_51 ca-identity All-Trusted-CA-Def_51 set security pki ca-profile All-Trusted-CA-Def_52 ca-identity All-Trusted-CA-Def_52 set security pki ca-profile All-Trusted-CA-Def_53 ca-identity All-Trusted-CA-Def_53 set security pki ca-profile All-Trusted-CA-Def_54 ca-identity All-Trusted-CA-Def_54 set security pki ca-profile All-Trusted-CA-Def_55 ca-identity All-Trusted-CA-Def_55 set security pki ca-profile All-Trusted-CA-Def_56 ca-identity All-Trusted-CA-Def_56 set security pki ca-profile All-Trusted-CA-Def_57 ca-identity All-Trusted-CA-Def_57 set security pki ca-profile All-Trusted-CA-Def_58 ca-identity All-Trusted-CA-Def_58 set security pki ca-profile All-Trusted-CA-Def_59 ca-identity All-Trusted-CA-Def_59 set security pki ca-profile All-Trusted-CA-Def_60 ca-identity All-Trusted-CA-Def_60 set security pki ca-profile All-Trusted-CA-Def_61 ca-identity All-Trusted-CA-Def_61 set security pki ca-profile All-Trusted-CA-Def_62 ca-identity All-Trusted-CA-Def_62 set security pki ca-profile All-Trusted-CA-Def_63 ca-identity All-Trusted-CA-Def_63 set security pki ca-profile All-Trusted-CA-Def_64 ca-identity All-Trusted-CA-Def_64 set security pki ca-profile All-Trusted-CA-Def_65 ca-identity All-Trusted-CA-Def_65 set security pki ca-profile All-Trusted-CA-Def_66 ca-identity All-Trusted-CA-Def_66 set security pki ca-profile All-Trusted-CA-Def_67 ca-identity All-Trusted-CA-Def_67 set security pki ca-profile All-Trusted-CA-Def_68 ca-identity All-Trusted-CA-Def_68 set security pki ca-profile All-Trusted-CA-Def_69 ca-identity All-Trusted-CA-Def_69 set security pki ca-profile All-Trusted-CA-Def_70 ca-identity All-Trusted-CA-Def_70 set security pki ca-profile All-Trusted-CA-Def_71 ca-identity All-Trusted-CA-Def_71 set security pki ca-profile All-Trusted-CA-Def_72 ca-identity All-Trusted-CA-Def_72 set security pki ca-profile All-Trusted-CA-Def_73 ca-identity All-Trusted-CA-Def_73 set security pki ca-profile All-Trusted-CA-Def_74 ca-identity All-Trusted-CA-Def_74 set security pki ca-profile All-Trusted-CA-Def_75 ca-identity All-Trusted-CA-Def_75 set security pki ca-profile All-Trusted-CA-Def_76 ca-identity All-Trusted-CA-Def_76 set security pki ca-profile All-Trusted-CA-Def_77 ca-identity All-Trusted-CA-Def_77 set security pki ca-profile All-Trusted-CA-Def_78 ca-identity All-Trusted-CA-Def_78 set security pki ca-profile All-Trusted-CA-Def_79 ca-identity All-Trusted-CA-Def_79 set security pki ca-profile All-Trusted-CA-Def_80 ca-identity All-Trusted-CA-Def_80 set security pki ca-profile All-Trusted-CA-Def_81 ca-identity All-Trusted-CA-Def_81 set security pki ca-profile All-Trusted-CA-Def_82 ca-identity All-Trusted-CA-Def_82 set security pki ca-profile All-Trusted-CA-Def_83 ca-identity All-Trusted-CA-Def_83 set security pki ca-profile All-Trusted-CA-Def_84 ca-identity All-Trusted-CA-Def_84 set security pki ca-profile All-Trusted-CA-Def_85 ca-identity All-Trusted-CA-Def_85 set security pki ca-profile All-Trusted-CA-Def_86 ca-identity All-Trusted-CA-Def_86 set security pki ca-profile All-Trusted-CA-Def_87 ca-identity All-Trusted-CA-Def_87 set security pki ca-profile All-Trusted-CA-Def_88 ca-identity All-Trusted-CA-Def_88 set security pki ca-profile All-Trusted-CA-Def_89 ca-identity All-Trusted-CA-Def_89 set security pki ca-profile All-Trusted-CA-Def_90 ca-identity All-Trusted-CA-Def_90 set security pki ca-profile All-Trusted-CA-Def_91 ca-identity All-Trusted-CA-Def_91 set security pki ca-profile All-Trusted-CA-Def_92 ca-identity All-Trusted-CA-Def_92 set security pki ca-profile All-Trusted-CA-Def_93 ca-identity All-Trusted-CA-Def_93 set security pki ca-profile All-Trusted-CA-Def_94 ca-identity All-Trusted-CA-Def_94 set security pki ca-profile All-Trusted-CA-Def_95 ca-identity All-Trusted-CA-Def_95 set security pki ca-profile All-Trusted-CA-Def_96 ca-identity All-Trusted-CA-Def_96 set security pki ca-profile All-Trusted-CA-Def_97 ca-identity All-Trusted-CA-Def_97 set security pki ca-profile All-Trusted-CA-Def_98 ca-identity All-Trusted-CA-Def_98 set security pki ca-profile All-Trusted-CA-Def_99 ca-identity All-Trusted-CA-Def_99 set security pki ca-profile All-Trusted-CA-Def_100 ca-identity All-Trusted-CA-Def_100 set security pki ca-profile All-Trusted-CA-Def_101 ca-identity All-Trusted-CA-Def_101 set security pki ca-profile All-Trusted-CA-Def_102 ca-identity All-Trusted-CA-Def_102 set security pki ca-profile All-Trusted-CA-Def_103 ca-identity All-Trusted-CA-Def_103 set security pki ca-profile All-Trusted-CA-Def_104 ca-identity All-Trusted-CA-Def_104 set security pki ca-profile All-Trusted-CA-Def_105 ca-identity All-Trusted-CA-Def_105 set security pki ca-profile All-Trusted-CA-Def_106 ca-identity All-Trusted-CA-Def_106 set security pki ca-profile All-Trusted-CA-Def_107 ca-identity All-Trusted-CA-Def_107 set security pki ca-profile All-Trusted-CA-Def_108 ca-identity All-Trusted-CA-Def_108 set security pki ca-profile All-Trusted-CA-Def_109 ca-identity All-Trusted-CA-Def_109 set security pki ca-profile All-Trusted-CA-Def_110 ca-identity All-Trusted-CA-Def_110 set security pki ca-profile All-Trusted-CA-Def_111 ca-identity All-Trusted-CA-Def_111 set security pki ca-profile All-Trusted-CA-Def_112 ca-identity All-Trusted-CA-Def_112 set security pki ca-profile All-Trusted-CA-Def_114 ca-identity All-Trusted-CA-Def_114 set security pki ca-profile All-Trusted-CA-Def_115 ca-identity All-Trusted-CA-Def_115 set security pki ca-profile All-Trusted-CA-Def_116 ca-identity All-Trusted-CA-Def_116 set security pki ca-profile All-Trusted-CA-Def_117 ca-identity All-Trusted-CA-Def_117 set security pki ca-profile All-Trusted-CA-Def_118 ca-identity All-Trusted-CA-Def_118 set security pki ca-profile All-Trusted-CA-Def_119 ca-identity All-Trusted-CA-Def_119 set security pki ca-profile All-Trusted-CA-Def_120 ca-identity All-Trusted-CA-Def_120 set security pki ca-profile All-Trusted-CA-Def_121 ca-identity All-Trusted-CA-Def_121 set security pki ca-profile All-Trusted-CA-Def_122 ca-identity All-Trusted-CA-Def_122 set security pki ca-profile All-Trusted-CA-Def_123 ca-identity All-Trusted-CA-Def_123 set security pki ca-profile All-Trusted-CA-Def_124 ca-identity All-Trusted-CA-Def_124 set security pki ca-profile All-Trusted-CA-Def_125 ca-identity All-Trusted-CA-Def_125 set security pki ca-profile All-Trusted-CA-Def_126 ca-identity All-Trusted-CA-Def_126 set security pki ca-profile All-Trusted-CA-Def_127 ca-identity All-Trusted-CA-Def_127 set security pki ca-profile All-Trusted-CA-Def_128 ca-identity All-Trusted-CA-Def_128 set security pki ca-profile All-Trusted-CA-Def_129 ca-identity All-Trusted-CA-Def_129 set security pki ca-profile All-Trusted-CA-Def_130 ca-identity All-Trusted-CA-Def_130 set security pki ca-profile All-Trusted-CA-Def_131 ca-identity All-Trusted-CA-Def_131 set security pki ca-profile All-Trusted-CA-Def_132 ca-identity All-Trusted-CA-Def_132 set security pki ca-profile All-Trusted-CA-Def_133 ca-identity All-Trusted-CA-Def_133 set security pki ca-profile All-Trusted-CA-Def_134 ca-identity All-Trusted-CA-Def_134 set security pki ca-profile All-Trusted-CA-Def_135 ca-identity All-Trusted-CA-Def_135 set security pki ca-profile All-Trusted-CA-Def_136 ca-identity All-Trusted-CA-Def_136 set security pki ca-profile All-Trusted-CA-Def_137 ca-identity All-Trusted-CA-Def_137 set security pki ca-profile All-Trusted-CA-Def_138 ca-identity All-Trusted-CA-Def_138 set security pki ca-profile All-Trusted-CA-Def_139 ca-identity All-Trusted-CA-Def_139 set security pki ca-profile All-Trusted-CA-Def_140 ca-identity All-Trusted-CA-Def_140 set security pki ca-profile All-Trusted-CA-Def_141 ca-identity All-Trusted-CA-Def_141 set security pki ca-profile All-Trusted-CA-Def_142 ca-identity All-Trusted-CA-Def_142 set security pki ca-profile All-Trusted-CA-Def_143 ca-identity All-Trusted-CA-Def_143 set security pki ca-profile All-Trusted-CA-Def_144 ca-identity All-Trusted-CA-Def_144 set security pki ca-profile All-Trusted-CA-Def_145 ca-identity All-Trusted-CA-Def_145 set security pki ca-profile All-Trusted-CA-Def_146 ca-identity All-Trusted-CA-Def_146 set security pki ca-profile All-Trusted-CA-Def_147 ca-identity All-Trusted-CA-Def_147 set security pki ca-profile All-Trusted-CA-Def_148 ca-identity All-Trusted-CA-Def_148 set security pki ca-profile All-Trusted-CA-Def_149 ca-identity All-Trusted-CA-Def_149 set security pki ca-profile All-Trusted-CA-Def_150 ca-identity All-Trusted-CA-Def_150 set security pki ca-profile All-Trusted-CA-Def_151 ca-identity All-Trusted-CA-Def_151 set security pki ca-profile All-Trusted-CA-Def_152 ca-identity All-Trusted-CA-Def_152 set security pki ca-profile All-Trusted-CA-Def_153 ca-identity All-Trusted-CA-Def_153 set security pki ca-profile All-Trusted-CA-Def_154 ca-identity All-Trusted-CA-Def_154 set security pki ca-profile All-Trusted-CA-Def_155 ca-identity All-Trusted-CA-Def_155 set security pki ca-profile ssl-inspect-ca ca-identity ssl-inspect-ca set security pki ca-profile ssl-ca ca-identity ssl-ca set security pki ca-profile aamw-ca ca-identity deviceCA set security pki ca-profile aamw-ca enrollment url http://ca.junipersecurity.net:8080/ejbca/publicweb/apply/scep/SRX/pkiclient.exe set security pki ca-profile aamw-ca revocation-check disable set security pki ca-profile aamw-ca revocation-check crl url http://va.junipersecurity.net/ca/deviceCA.crl set security pki ca-profile aamw-secintel-ca ca-identity JUNIPER set security pki ca-profile aamw-secintel-ca revocation-check crl url http://va.junipersecurity.net/ca/current.crl set security pki ca-profile aamw-cloud-ca ca-identity JUNIPER_CLOUD set security pki ca-profile aamw-cloud-ca revocation-check crl url http://va.junipersecurity.net/ca/cloudCA.crl set security pki ca-profile-group All-Trusted-CA-Def cert-base-count 155 set security address-book global address JSD_192.168.10.1/24 192.168.10.0/24 set security address-book global address JSD_192.168.11.1/24 192.168.11.0/24 set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.10.1/24 set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.11.1/24 set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match destination-address any set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match application any set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 then permit application-services security-intelligence-policy TPP set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 then permit application-services advanced-anti-malware-policy TPP set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 then log session-init set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 then count set security policies from-zone trust to-zone untrust policy t-u match source-address any set security policies from-zone trust to-zone untrust policy t-u match destination-address any set security policies from-zone trust to-zone untrust policy t-u match application any set security policies from-zone trust to-zone untrust policy t-u then permit set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.10.1/24 set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.11.1/24 set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 match destination-address any set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 match application any set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 then permit application-services security-intelligence-policy TPP set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 then permit application-services advanced-anti-malware-policy TPP set security policies from-zone untrust to-zone trust policy u-t match source-address any set security policies from-zone untrust to-zone trust policy u-t match destination-address any set security policies from-zone untrust to-zone trust policy u-t match application any set security policies from-zone untrust to-zone trust policy u-t then permit set security policies global policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.10.1/24 set security policies global policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.11.1/24 set security policies global policy PolicyEnforcer-Rule1-1 match destination-address any set security policies global policy PolicyEnforcer-Rule1-1 match application any set security policies global policy PolicyEnforcer-Rule1-1 then permit application-services security-intelligence-policy TPP set security policies global policy PolicyEnforcer-Rule1-1 then permit application-services advanced-anti-malware-policy TPP set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/0.12 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces ge-0/0/2.13 set interfaces ge-0/0/0 vlan-tagging set interfaces ge-0/0/0 unit 12 vlan-id 12 set interfaces ge-0/0/0 unit 12 family inet address 192.168.1.254/24 set interfaces ge-0/0/2 vlan-tagging set interfaces ge-0/0/2 unit 13 vlan-id 13 set interfaces ge-0/0/2 unit 13 family inet address 192.168.231.1/24 set interfaces fxp0 description MGMT set interfaces fxp0 unit 0 family inet address 10.13.107.186/23 set snmp trap-group space targets 10.13.107.162 set routing-options static route 172.28.0.0/16 next-hop 10.13.106.1 set routing-options static route 10.13.0.0/16 next-hop 10.13.106.1 set routing-options static route 0.0.0.0/0 next-hop 192.168.231.10 set routing-options static route 192.168.10.0/24 next-hop 192.168.1.1 set routing-options static route 192.168.11.0/24 next-hop 192.168.1.1 set routing-options static route 192.168.99.0/24 next-hop 192.168.1.1 set routing-options static route 172.29.64.0/20 next-hop 10.13.106.1 set routing-options static route 172.29.80.0/20 next-hop 10.13.106.1
EX4300-1 Access Switch Configuration
set version 15.1R5.5 set system host-name EX4300-1 set system auto-snapshot set system time-zone America/New_York set system root-authentication encrypted-password "$ABC123" set system services ftp set system services ssh max-sessions-per-connection 32 set system services telnet set system services netconf ssh set system syslog user * any emergency set system syslog file messages any notice set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system syslog file default-log-messages any any set system syslog file default-log-messages match "(requested 'commit' operation)|(requested 'commit synchronize' operation)|(copying configuration to juniper.save)|(commit complete)|ifAdminStatus|(FRU power)|(FRU removal)|(FRU insertion)|(link UP)|transitioned|Transferred|transfer-file|(license add)|(license delete)|(package -X update)|(package -X delete)|(FRU Online)|(FRU Offline)|(plugged in)|(unplugged)|CFMD_CCM_DEFECT| LFMD_3AH | RPD_MPLS_PATH_BFD|(Master Unchanged, Members Changed)|(Master Changed, Members Changed)|(Master Detected, Members Changed)|(vc add)|(vc delete)|(Master detected)|(Master changed)|(Backup detected)|(Backup changed)|(interface vcp-)" set system syslog file default-log-messages structured-data set system ntp server 203.0.113.1 set interfaces ge-0/0/1 unit 0 family ethernet-switching interface-mode trunk set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members VLAN11 set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members VLAN99 set interfaces ge-0/0/12 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/12 unit 0 family ethernet-switching vlan members VLAN11 set interfaces me0 unit 0 family inet address 10.13.107.181/23 set snmp trap-group space targets 10.13.107.162 set routing-options static route 0.0.0.0/0 next-hop 10.13.106.1 set protocols l2-learning global-mac-table-aging-time 120 set protocols lldp interface all set protocols lldp-med interface all set protocols igmp-snooping vlan default set vlans VLAN11 vlan-id 11 set vlans VLAN99 vlan-id 99
EX4300-2 Access Switch Configuration
set version 15.1R5.5 set system host-name EX4300-2 set system auto-snapshot set system time-zone America/New_York set system root-authentication encrypted-password "$ABC123" set system services ftp set system services ssh max-sessions-per-connection 32 set system services telnet set system services netconf ssh set system syslog user * any emergency set system syslog file messages any notice set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system syslog file default-log-messages any any set system syslog file default-log-messages match "(requested 'commit' operation)|(requested 'commit synchronize' operation)|(copying configuration to juniper.save)|(commit complete)|ifAdminStatus|(FRU power)|(FRU removal)|(FRU insertion)|(link UP)|transitioned|Transferred|transfer-file|(license add)|(license delete)|(package -X update)|(package -X delete)|(FRU Online)|(FRU Offline)|(plugged in)|(unplugged)|CFMD_CCM_DEFECT| LFMD_3AH | RPD_MPLS_PATH_BFD|(Master Unchanged, Members Changed)|(Master Changed, Members Changed)|(Master Detected, Members Changed)|(vc add)|(vc delete)|(Master detected)|(Master changed)|(Backup detected)|(Backup changed)|(interface vcp-)" set system syslog file default-log-messages structured-data set system ntp server 203.0.113.1 set interfaces ge-0/0/0 unit 0 family ethernet-switching interface-mode trunk set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members VLAN10 set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members VLAN99 set interfaces xe-0/2/0 unit 0 family ethernet-switching interface-mode access set interfaces xe-0/2/0 unit 0 family ethernet-switching vlan members VLAN10 set interfaces me0 unit 0 family inet address 10.13.107.180/23 set snmp trap-group space targets 10.13.107.162 set routing-options static route 0.0.0.0/0 next-hop 10.13.106.1 set protocols l2-learning global-mac-table-aging-time 120 set protocols lldp interface all set protocols lldp-med interface all set protocols igmp-snooping vlan default set vlans VLAN10 vlan-id 10 set vlans VLAN99 vlan-id 99
EX2200 Aggregation Switch Configuration
set version 15.1R5.5 set system host-name EX2200-LAN set system arp aging-timer 2 set system root-authentication encrypted-password "$ABC123" set system services ftp set system services ssh max-sessions-per-connection 32 set system services netconf ssh set system syslog user * any emergency set system syslog file messages any notice set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system syslog file default-log-messages any any set system syslog file default-log-messages match "(requested 'commit' operation)|(requested 'commit synchronize' operation)|(copying configuration to juniper.save)|(commit complete)|ifAdminStatus|(FRU power)|(FRU removal)|(FRU insertion)|(link UP)|transitioned|Transferred|transfer-file|(license add)|(license delete)|(package -X update)|(package -X delete)|(FRU Online)|(FRU Offline)|(plugged in)|(unplugged)|cm_device|(Master Unchanged, Members Changed)|(Master Changed, Members Changed)|(Master Detected, Members Changed)|(vc add)|(vc delete)|(Master detected)|(Master changed)|(Backup detected)|(Backup changed)|(interface vcp-)" set system syslog file default-log-messages structured-data set interfaces ge-0/0/0 unit 0 family ethernet-switching port-mode trunk set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members VLAN10 set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members VLAN99 set interfaces ge-0/0/1 unit 0 family ethernet-switching port-mode trunk set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members VLAN11 set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members VLAN99 set interfaces ge-0/0/12 unit 0 family ethernet-switching port-mode trunk set interfaces ge-0/0/12 unit 0 family ethernet-switching vlan members VLAN12 set interfaces ge-0/0/13 unit 0 family ethernet-switching port-mode trunk set interfaces ge-0/0/13 unit 0 family ethernet-switching vlan members VLAN12 set interfaces me0 unit 0 family inet address 10.13.107.182/23 set interfaces vlan unit 10 family inet address 192.168.10.1/24 set interfaces vlan unit 11 family inet address 192.168.11.1/24 set interfaces vlan unit 12 family inet address 192.168.1.1/24 set interfaces vlan unit 99 family inet address 192.168.99.1/24 set snmp trap-group space targets 10.13.107.162 set routing-options static route 10.13.0.0/16 next-hop 10.13.106.1 set routing-options static route 172.28.0.0/16 next-hop 10.13.106.1 set routing-options static route 0.0.0.0/0 next-hop 192.168.1.254 set routing-options static route 172.29.64.0/20 next-hop 10.13.106.1 set routing-options static route 172.29.80.0/20 next-hop 10.13.106.1 set protocols igmp-snooping vlan all set protocols lldp interface all set protocols lldp-med interface all set vlans VLAN10 vlan-id 10 set vlans VLAN10 l3-interface vlan.10 set vlans VLAN11 vlan-id 11 set vlans VLAN11 l3-interface vlan.11 set vlans VLAN12 vlan-id 12 set vlans VLAN12 l3-interface vlan.12 set vlans VLAN99 vlan-id 99 set vlans VLAN99 l3-interface vlan.99
EX2200 Internet Gateway Switch Configuration
In this topology, the EX2200 switch acts as a simple default gateway to the Internet. It does not play any role in the Juniper Connected Security solution.
set version 15.1R5.5 set system host-name EX2200-INTERNET set system root-authentication encrypted-password "$ABC123" set system services ftp set system services ssh set system services telnet set system syslog user * any emergency set system syslog file messages any notice set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set interfaces ge-0/0/12 unit 0 family ethernet-switching port-mode trunk set interfaces ge-0/0/12 unit 0 family ethernet-switching vlan members VLAN13 set interfaces ge-0/0/13 unit 0 family ethernet-switching port-mode trunk set interfaces ge-0/0/13 unit 0 family ethernet-switching vlan members VLAN13 set interfaces ge-0/0/47 description "to DMZ ge/0/015" set interfaces ge-0/0/47 unit 0 family inet address 198.51.100.2/30 set interfaces me0 unit 0 family inet address 10.13.107.188/23 set interfaces vlan unit 13 family inet address 192.168.231.10/24 set routing-options static route 0.0.0.0/0 next-hop 198.51.100.1 set routing-options static route 10.13.0.0/16 next-hop 10.13.106.1 set routing-options static route 172.28.0.0/16 next-hop 10.13.106.1 set routing-options static route 192.168.0.0/16 next-hop 192.168.231.1 set protocols igmp-snooping vlan all set protocols lldp interface all set protocols lldp-med interface all set vlans VLAN13 vlan-id 13 set vlans VLAN13 l3-interface vlan.13
Configuration Files for Topology #3
- SRX Series Firewall Configuration
- EX4300 Access Switch Configuration
- EX2200 Internet Gateway Switch Configuration
SRX Series Firewall Configuration
set version 15.1X49-D80.4 set system host-name SRX1500-1 set system time-zone America/New_York set system root-authentication encrypted-password "$ABC123" set system name-server 8.8.8.8 set system services ssh max-sessions-per-connection 32 set system services telnet set system services xnm-clear-text set system services netconf ssh set system syslog user * any emergency set system syslog host 192.168.10.4 structured-data set system syslog file messages any any set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system syslog file default-log-messages any info set system syslog file default-log-messages match "(requested 'commit' operation)|(requested 'commit synchronize' operation)|(copying configuration to juniper.save)|(commit complete)|ifAdminStatus|(FRU power)|(FRU removal)|(FRU insertion)|(link UP)|transitioned|Transferred|transfer-file|(license add)|(license delete)|(package -X update)|(package -X delete)|(FRU Online)|(FRU Offline)|(plugged in)|(unplugged)|GRES" set system syslog file default-log-messages structured-data set system max-configurations-on-flash 5 set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval set system ntp server 203.0.113.1 set services application-identification set services ssl initiation profile aamw-ssl trusted-ca aamw-secintel-ca set services ssl initiation profile aamw-ssl trusted-ca aamw-cloud-ca set services ssl initiation profile aamw-ssl client-certificate aamw-srx-cert set services ssl initiation profile aamw-ssl actions crl disable set services security-intelligence url https://10.13.107.164:443/api/v1/manifest.xml set services security-intelligence authentication auth-token ABC123 set services security-intelligence profile TPP_CC category CC set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 1 set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 2 set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 3 set services security-intelligence profile TPP_CC rule Rule-1 match threat-level 4 set services security-intelligence profile TPP_CC rule Rule-1 then action permit set services security-intelligence profile TPP_CC rule Rule-1 then log set services security-intelligence profile TPP_CC rule Rule-2 match threat-level 5 set services security-intelligence profile TPP_CC rule Rule-2 match threat-level 6 set services security-intelligence profile TPP_CC rule Rule-2 match threat-level 7 set services security-intelligence profile TPP_CC rule Rule-2 then action permit set services security-intelligence profile TPP_CC rule Rule-2 then log set services security-intelligence profile TPP_CC rule Rule-3 match threat-level 8 set services security-intelligence profile TPP_CC rule Rule-3 match threat-level 9 set services security-intelligence profile TPP_CC rule Rule-3 match threat-level 10 set services security-intelligence profile TPP_CC rule Rule-3 then action block drop set services security-intelligence profile TPP_CC rule Rule-3 then log set services security-intelligence profile TPP_Infected-Hosts category Infected-Hosts set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 1 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 2 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 3 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 4 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 5 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 match threat-level 6 set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 then action permit set services security-intelligence profile TPP_Infected-Hosts rule Rule-1 then log set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 7 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 8 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 9 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 match threat-level 10 set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 then action block drop set services security-intelligence profile TPP_Infected-Hosts rule Rule-2 then log set services security-intelligence policy TPP CC TPP_CC set services security-intelligence policy TPP Infected-Hosts TPP_Infected-Hosts set services advanced-anti-malware connection url https://srxapi.us-west-2.sky.junipersecurity.net set services advanced-anti-malware connection authentication tls-profile aamw-ssl set services advanced-anti-malware policy TPP http inspection-profile default_profile set services advanced-anti-malware policy TPP http action block set services advanced-anti-malware policy TPP http notification log set services advanced-anti-malware policy TPP verdict-threshold 8 set services advanced-anti-malware policy TPP fallback-options action permit set services advanced-anti-malware policy TPP fallback-options notification log set services advanced-anti-malware policy TPP default-notification log set services advanced-anti-malware policy TPP whitelist-notification log set services advanced-anti-malware policy TPP blacklist-notification log set security log mode stream set security log format sd-syslog set security log source-address 192.168.1.254 set security log stream TRAFFIC category all set security log stream TRAFFIC host 192.168.10.4 set security log stream TRAFFIC host port 514 set security pki ca-profile All-Trusted-CA-Def_1 ca-identity All-Trusted-CA-Def_1 set security pki ca-profile All-Trusted-CA-Def_2 ca-identity All-Trusted-CA-Def_2 set security pki ca-profile All-Trusted-CA-Def_3 ca-identity All-Trusted-CA-Def_3 set security pki ca-profile All-Trusted-CA-Def_4 ca-identity All-Trusted-CA-Def_4 set security pki ca-profile All-Trusted-CA-Def_5 ca-identity All-Trusted-CA-Def_5 set security pki ca-profile All-Trusted-CA-Def_6 ca-identity All-Trusted-CA-Def_6 set security pki ca-profile All-Trusted-CA-Def_7 ca-identity All-Trusted-CA-Def_7 set security pki ca-profile All-Trusted-CA-Def_8 ca-identity All-Trusted-CA-Def_8 set security pki ca-profile All-Trusted-CA-Def_9 ca-identity All-Trusted-CA-Def_9 set security pki ca-profile All-Trusted-CA-Def_10 ca-identity All-Trusted-CA-Def_10 set security pki ca-profile All-Trusted-CA-Def_11 ca-identity All-Trusted-CA-Def_11 set security pki ca-profile All-Trusted-CA-Def_12 ca-identity All-Trusted-CA-Def_12 set security pki ca-profile All-Trusted-CA-Def_13 ca-identity All-Trusted-CA-Def_13 set security pki ca-profile All-Trusted-CA-Def_14 ca-identity All-Trusted-CA-Def_14 set security pki ca-profile All-Trusted-CA-Def_15 ca-identity All-Trusted-CA-Def_15 set security pki ca-profile All-Trusted-CA-Def_16 ca-identity All-Trusted-CA-Def_16 set security pki ca-profile All-Trusted-CA-Def_17 ca-identity All-Trusted-CA-Def_17 set security pki ca-profile All-Trusted-CA-Def_18 ca-identity All-Trusted-CA-Def_18 set security pki ca-profile All-Trusted-CA-Def_19 ca-identity All-Trusted-CA-Def_19 set security pki ca-profile All-Trusted-CA-Def_20 ca-identity All-Trusted-CA-Def_20 set security pki ca-profile All-Trusted-CA-Def_21 ca-identity All-Trusted-CA-Def_21 set security pki ca-profile All-Trusted-CA-Def_22 ca-identity All-Trusted-CA-Def_22 set security pki ca-profile All-Trusted-CA-Def_23 ca-identity All-Trusted-CA-Def_23 set security pki ca-profile All-Trusted-CA-Def_24 ca-identity All-Trusted-CA-Def_24 set security pki ca-profile All-Trusted-CA-Def_25 ca-identity All-Trusted-CA-Def_25 set security pki ca-profile All-Trusted-CA-Def_26 ca-identity All-Trusted-CA-Def_26 set security pki ca-profile All-Trusted-CA-Def_27 ca-identity All-Trusted-CA-Def_27 set security pki ca-profile All-Trusted-CA-Def_28 ca-identity All-Trusted-CA-Def_28 set security pki ca-profile All-Trusted-CA-Def_29 ca-identity All-Trusted-CA-Def_29 set security pki ca-profile All-Trusted-CA-Def_30 ca-identity All-Trusted-CA-Def_30 set security pki ca-profile All-Trusted-CA-Def_31 ca-identity All-Trusted-CA-Def_31 set security pki ca-profile All-Trusted-CA-Def_32 ca-identity All-Trusted-CA-Def_32 set security pki ca-profile All-Trusted-CA-Def_33 ca-identity All-Trusted-CA-Def_33 set security pki ca-profile All-Trusted-CA-Def_34 ca-identity All-Trusted-CA-Def_34 set security pki ca-profile All-Trusted-CA-Def_35 ca-identity All-Trusted-CA-Def_35 set security pki ca-profile All-Trusted-CA-Def_36 ca-identity All-Trusted-CA-Def_36 set security pki ca-profile All-Trusted-CA-Def_37 ca-identity All-Trusted-CA-Def_37 set security pki ca-profile All-Trusted-CA-Def_38 ca-identity All-Trusted-CA-Def_38 set security pki ca-profile All-Trusted-CA-Def_39 ca-identity All-Trusted-CA-Def_39 set security pki ca-profile All-Trusted-CA-Def_40 ca-identity All-Trusted-CA-Def_40 set security pki ca-profile All-Trusted-CA-Def_41 ca-identity All-Trusted-CA-Def_41 set security pki ca-profile All-Trusted-CA-Def_42 ca-identity All-Trusted-CA-Def_42 set security pki ca-profile All-Trusted-CA-Def_43 ca-identity All-Trusted-CA-Def_43 set security pki ca-profile All-Trusted-CA-Def_44 ca-identity All-Trusted-CA-Def_44 set security pki ca-profile All-Trusted-CA-Def_45 ca-identity All-Trusted-CA-Def_45 set security pki ca-profile All-Trusted-CA-Def_46 ca-identity All-Trusted-CA-Def_46 set security pki ca-profile All-Trusted-CA-Def_47 ca-identity All-Trusted-CA-Def_47 set security pki ca-profile All-Trusted-CA-Def_48 ca-identity All-Trusted-CA-Def_48 set security pki ca-profile All-Trusted-CA-Def_49 ca-identity All-Trusted-CA-Def_49 set security pki ca-profile All-Trusted-CA-Def_50 ca-identity All-Trusted-CA-Def_50 set security pki ca-profile All-Trusted-CA-Def_51 ca-identity All-Trusted-CA-Def_51 set security pki ca-profile All-Trusted-CA-Def_52 ca-identity All-Trusted-CA-Def_52 set security pki ca-profile All-Trusted-CA-Def_53 ca-identity All-Trusted-CA-Def_53 set security pki ca-profile All-Trusted-CA-Def_54 ca-identity All-Trusted-CA-Def_54 set security pki ca-profile All-Trusted-CA-Def_55 ca-identity All-Trusted-CA-Def_55 set security pki ca-profile All-Trusted-CA-Def_56 ca-identity All-Trusted-CA-Def_56 set security pki ca-profile All-Trusted-CA-Def_57 ca-identity All-Trusted-CA-Def_57 set security pki ca-profile All-Trusted-CA-Def_58 ca-identity All-Trusted-CA-Def_58 set security pki ca-profile All-Trusted-CA-Def_59 ca-identity All-Trusted-CA-Def_59 set security pki ca-profile All-Trusted-CA-Def_60 ca-identity All-Trusted-CA-Def_60 set security pki ca-profile All-Trusted-CA-Def_61 ca-identity All-Trusted-CA-Def_61 set security pki ca-profile All-Trusted-CA-Def_62 ca-identity All-Trusted-CA-Def_62 set security pki ca-profile All-Trusted-CA-Def_63 ca-identity All-Trusted-CA-Def_63 set security pki ca-profile All-Trusted-CA-Def_64 ca-identity All-Trusted-CA-Def_64 set security pki ca-profile All-Trusted-CA-Def_65 ca-identity All-Trusted-CA-Def_65 set security pki ca-profile All-Trusted-CA-Def_66 ca-identity All-Trusted-CA-Def_66 set security pki ca-profile All-Trusted-CA-Def_67 ca-identity All-Trusted-CA-Def_67 set security pki ca-profile All-Trusted-CA-Def_68 ca-identity All-Trusted-CA-Def_68 set security pki ca-profile All-Trusted-CA-Def_69 ca-identity All-Trusted-CA-Def_69 set security pki ca-profile All-Trusted-CA-Def_70 ca-identity All-Trusted-CA-Def_70 set security pki ca-profile All-Trusted-CA-Def_71 ca-identity All-Trusted-CA-Def_71 set security pki ca-profile All-Trusted-CA-Def_72 ca-identity All-Trusted-CA-Def_72 set security pki ca-profile All-Trusted-CA-Def_73 ca-identity All-Trusted-CA-Def_73 set security pki ca-profile All-Trusted-CA-Def_74 ca-identity All-Trusted-CA-Def_74 set security pki ca-profile All-Trusted-CA-Def_75 ca-identity All-Trusted-CA-Def_75 set security pki ca-profile All-Trusted-CA-Def_76 ca-identity All-Trusted-CA-Def_76 set security pki ca-profile All-Trusted-CA-Def_77 ca-identity All-Trusted-CA-Def_77 set security pki ca-profile All-Trusted-CA-Def_78 ca-identity All-Trusted-CA-Def_78 set security pki ca-profile All-Trusted-CA-Def_79 ca-identity All-Trusted-CA-Def_79 set security pki ca-profile All-Trusted-CA-Def_80 ca-identity All-Trusted-CA-Def_80 set security pki ca-profile All-Trusted-CA-Def_81 ca-identity All-Trusted-CA-Def_81 set security pki ca-profile All-Trusted-CA-Def_82 ca-identity All-Trusted-CA-Def_82 set security pki ca-profile All-Trusted-CA-Def_83 ca-identity All-Trusted-CA-Def_83 set security pki ca-profile All-Trusted-CA-Def_84 ca-identity All-Trusted-CA-Def_84 set security pki ca-profile All-Trusted-CA-Def_85 ca-identity All-Trusted-CA-Def_85 set security pki ca-profile All-Trusted-CA-Def_86 ca-identity All-Trusted-CA-Def_86 set security pki ca-profile All-Trusted-CA-Def_87 ca-identity All-Trusted-CA-Def_87 set security pki ca-profile All-Trusted-CA-Def_88 ca-identity All-Trusted-CA-Def_88 set security pki ca-profile All-Trusted-CA-Def_89 ca-identity All-Trusted-CA-Def_89 set security pki ca-profile All-Trusted-CA-Def_90 ca-identity All-Trusted-CA-Def_90 set security pki ca-profile All-Trusted-CA-Def_91 ca-identity All-Trusted-CA-Def_91 set security pki ca-profile All-Trusted-CA-Def_92 ca-identity All-Trusted-CA-Def_92 set security pki ca-profile All-Trusted-CA-Def_93 ca-identity All-Trusted-CA-Def_93 set security pki ca-profile All-Trusted-CA-Def_94 ca-identity All-Trusted-CA-Def_94 set security pki ca-profile All-Trusted-CA-Def_95 ca-identity All-Trusted-CA-Def_95 set security pki ca-profile All-Trusted-CA-Def_96 ca-identity All-Trusted-CA-Def_96 set security pki ca-profile All-Trusted-CA-Def_97 ca-identity All-Trusted-CA-Def_97 set security pki ca-profile All-Trusted-CA-Def_98 ca-identity All-Trusted-CA-Def_98 set security pki ca-profile All-Trusted-CA-Def_99 ca-identity All-Trusted-CA-Def_99 set security pki ca-profile All-Trusted-CA-Def_100 ca-identity All-Trusted-CA-Def_100 set security pki ca-profile All-Trusted-CA-Def_101 ca-identity All-Trusted-CA-Def_101 set security pki ca-profile All-Trusted-CA-Def_102 ca-identity All-Trusted-CA-Def_102 set security pki ca-profile All-Trusted-CA-Def_103 ca-identity All-Trusted-CA-Def_103 set security pki ca-profile All-Trusted-CA-Def_104 ca-identity All-Trusted-CA-Def_104 set security pki ca-profile All-Trusted-CA-Def_105 ca-identity All-Trusted-CA-Def_105 set security pki ca-profile All-Trusted-CA-Def_106 ca-identity All-Trusted-CA-Def_106 set security pki ca-profile All-Trusted-CA-Def_107 ca-identity All-Trusted-CA-Def_107 set security pki ca-profile All-Trusted-CA-Def_108 ca-identity All-Trusted-CA-Def_108 set security pki ca-profile All-Trusted-CA-Def_109 ca-identity All-Trusted-CA-Def_109 set security pki ca-profile All-Trusted-CA-Def_110 ca-identity All-Trusted-CA-Def_110 set security pki ca-profile All-Trusted-CA-Def_111 ca-identity All-Trusted-CA-Def_111 set security pki ca-profile All-Trusted-CA-Def_112 ca-identity All-Trusted-CA-Def_112 set security pki ca-profile All-Trusted-CA-Def_114 ca-identity All-Trusted-CA-Def_114 set security pki ca-profile All-Trusted-CA-Def_115 ca-identity All-Trusted-CA-Def_115 set security pki ca-profile All-Trusted-CA-Def_116 ca-identity All-Trusted-CA-Def_116 set security pki ca-profile All-Trusted-CA-Def_117 ca-identity All-Trusted-CA-Def_117 set security pki ca-profile All-Trusted-CA-Def_118 ca-identity All-Trusted-CA-Def_118 set security pki ca-profile All-Trusted-CA-Def_119 ca-identity All-Trusted-CA-Def_119 set security pki ca-profile All-Trusted-CA-Def_120 ca-identity All-Trusted-CA-Def_120 set security pki ca-profile All-Trusted-CA-Def_121 ca-identity All-Trusted-CA-Def_121 set security pki ca-profile All-Trusted-CA-Def_122 ca-identity All-Trusted-CA-Def_122 set security pki ca-profile All-Trusted-CA-Def_123 ca-identity All-Trusted-CA-Def_123 set security pki ca-profile All-Trusted-CA-Def_124 ca-identity All-Trusted-CA-Def_124 set security pki ca-profile All-Trusted-CA-Def_125 ca-identity All-Trusted-CA-Def_125 set security pki ca-profile All-Trusted-CA-Def_126 ca-identity All-Trusted-CA-Def_126 set security pki ca-profile All-Trusted-CA-Def_127 ca-identity All-Trusted-CA-Def_127 set security pki ca-profile All-Trusted-CA-Def_128 ca-identity All-Trusted-CA-Def_128 set security pki ca-profile All-Trusted-CA-Def_129 ca-identity All-Trusted-CA-Def_129 set security pki ca-profile All-Trusted-CA-Def_130 ca-identity All-Trusted-CA-Def_130 set security pki ca-profile All-Trusted-CA-Def_131 ca-identity All-Trusted-CA-Def_131 set security pki ca-profile All-Trusted-CA-Def_132 ca-identity All-Trusted-CA-Def_132 set security pki ca-profile All-Trusted-CA-Def_133 ca-identity All-Trusted-CA-Def_133 set security pki ca-profile All-Trusted-CA-Def_134 ca-identity All-Trusted-CA-Def_134 set security pki ca-profile All-Trusted-CA-Def_135 ca-identity All-Trusted-CA-Def_135 set security pki ca-profile All-Trusted-CA-Def_136 ca-identity All-Trusted-CA-Def_136 set security pki ca-profile All-Trusted-CA-Def_137 ca-identity All-Trusted-CA-Def_137 set security pki ca-profile All-Trusted-CA-Def_138 ca-identity All-Trusted-CA-Def_138 set security pki ca-profile All-Trusted-CA-Def_139 ca-identity All-Trusted-CA-Def_139 set security pki ca-profile All-Trusted-CA-Def_140 ca-identity All-Trusted-CA-Def_140 set security pki ca-profile All-Trusted-CA-Def_141 ca-identity All-Trusted-CA-Def_141 set security pki ca-profile All-Trusted-CA-Def_142 ca-identity All-Trusted-CA-Def_142 set security pki ca-profile All-Trusted-CA-Def_143 ca-identity All-Trusted-CA-Def_143 set security pki ca-profile All-Trusted-CA-Def_144 ca-identity All-Trusted-CA-Def_144 set security pki ca-profile All-Trusted-CA-Def_145 ca-identity All-Trusted-CA-Def_145 set security pki ca-profile All-Trusted-CA-Def_146 ca-identity All-Trusted-CA-Def_146 set security pki ca-profile All-Trusted-CA-Def_147 ca-identity All-Trusted-CA-Def_147 set security pki ca-profile All-Trusted-CA-Def_148 ca-identity All-Trusted-CA-Def_148 set security pki ca-profile All-Trusted-CA-Def_149 ca-identity All-Trusted-CA-Def_149 set security pki ca-profile All-Trusted-CA-Def_150 ca-identity All-Trusted-CA-Def_150 set security pki ca-profile All-Trusted-CA-Def_151 ca-identity All-Trusted-CA-Def_151 set security pki ca-profile All-Trusted-CA-Def_152 ca-identity All-Trusted-CA-Def_152 set security pki ca-profile All-Trusted-CA-Def_153 ca-identity All-Trusted-CA-Def_153 set security pki ca-profile All-Trusted-CA-Def_154 ca-identity All-Trusted-CA-Def_154 set security pki ca-profile All-Trusted-CA-Def_155 ca-identity All-Trusted-CA-Def_155 set security pki ca-profile ssl-inspect-ca ca-identity ssl-inspect-ca set security pki ca-profile ssl-ca ca-identity ssl-ca set security pki ca-profile aamw-ca ca-identity deviceCA set security pki ca-profile aamw-ca enrollment url http://ca.junipersecurity.net:8080/ejbca/publicweb/apply/scep/SRX/pkiclient.exe set security pki ca-profile aamw-ca revocation-check disable set security pki ca-profile aamw-ca revocation-check crl url http://va.junipersecurity.net/ca/deviceCA.crl set security pki ca-profile aamw-secintel-ca ca-identity JUNIPER set security pki ca-profile aamw-secintel-ca revocation-check crl url http://va.junipersecurity.net/ca/current.crl set security pki ca-profile aamw-cloud-ca ca-identity JUNIPER_CLOUD set security pki ca-profile aamw-cloud-ca revocation-check crl url http://va.junipersecurity.net/ca/cloudCA.crl set security pki ca-profile-group All-Trusted-CA-Def cert-base-count 155 set security address-book global address JSD_192.168.10.1/24 192.168.10.0/24 set security address-book global address JSD_192.168.11.1/24 192.168.11.0/24 set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.10.1/24 set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.11.1/24 set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match destination-address any set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 match application any set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 then permit application-services security-intelligence-policy TPP set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 then permit application-services advanced-anti-malware-policy TPP set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 then log session-init set security policies from-zone trust to-zone untrust policy PolicyEnforcer-Rule1-1 then count set security policies from-zone trust to-zone untrust policy t-u match source-address any set security policies from-zone trust to-zone untrust policy t-u match destination-address any set security policies from-zone trust to-zone untrust policy t-u match application any set security policies from-zone trust to-zone untrust policy t-u then permit set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.10.1/24 set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.11.1/24 set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 match destination-address any set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 match application any set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 then permit application-services security-intelligence-policy TPP set security policies from-zone untrust to-zone trust policy PolicyEnforcer-Rule1-1 then permit application-services advanced-anti-malware-policy TPP set security policies from-zone untrust to-zone trust policy u-t match source-address any set security policies from-zone untrust to-zone trust policy u-t match destination-address any set security policies from-zone untrust to-zone trust policy u-t match application any set security policies from-zone untrust to-zone trust policy u-t then permit set security policies global policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.10.1/24 set security policies global policy PolicyEnforcer-Rule1-1 match source-address JSD_192.168.11.1/24 set security policies global policy PolicyEnforcer-Rule1-1 match destination-address any set security policies global policy PolicyEnforcer-Rule1-1 match application any set security policies global policy PolicyEnforcer-Rule1-1 then permit application-services security-intelligence-policy TPP set security policies global policy PolicyEnforcer-Rule1-1 then permit application-services advanced-anti-malware-policy TPP set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/0.12 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces ge-0/0/2.13 set interfaces ge-0/0/0 vlan-tagging set interfaces ge-0/0/0 unit 12 vlan-id 12 set interfaces ge-0/0/0 unit 12 family inet address 192.168.1.254/24 set interfaces ge-0/0/2 vlan-tagging set interfaces ge-0/0/2 unit 13 vlan-id 13 set interfaces ge-0/0/2 unit 13 family inet address 192.168.231.1/24 set interfaces fxp0 description MGMT set interfaces fxp0 unit 0 family inet address 10.13.107.186/23 set snmp trap-group space targets 10.13.107.162 set routing-options static route 172.28.0.0/16 next-hop 10.13.106.1 set routing-options static route 10.13.0.0/16 next-hop 10.13.106.1 set routing-options static route 0.0.0.0/0 next-hop 192.168.231.10 set routing-options static route 172.29.64.0/20 next-hop 10.13.106.1 set routing-options static route 172.29.80.0/20 next-hop 10.13.106.1 set routing-options static route 192.168.10.0/24 next-hop 192.168.1.1 set routing-options static route 192.168.11.0/24 next-hop 192.168.1.3
EX4300 Access Switch Configuration
set version 15.1R5.5 set system host-name EX4300-1 set system auto-snapshot set system time-zone America/New_York set system root-authentication encrypted-password "$ABC123" set system services ftp set system services ssh max-sessions-per-connection 32 set system services telnet set system services netconf ssh set system syslog user * any emergency set system syslog file messages any notice set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system syslog file default-log-messages any any set system syslog file default-log-messages match "(requested 'commit' operation)|(requested 'commit synchronize' operation)|(copying configuration to juniper.save)|(commit complete)|ifAdminStatus|(FRU power)|(FRU removal)|(FRU insertion)|(link UP)|transitioned|Transferred|transfer-file|(license add)|(license delete)|(package -X update)|(package -X delete)|(FRU Online)|(FRU Offline)|(plugged in)|(unplugged)|CFMD_CCM_DEFECT| LFMD_3AH | RPD_MPLS_PATH_BFD|(Master Unchanged, Members Changed)|(Master Changed, Members Changed)|(Master Detected, Members Changed)|(vc add)|(vc delete)|(Master detected)|(Master changed)|(Backup detected)|(Backup changed)|(interface vcp-)" set system syslog file default-log-messages structured-data set system ntp server 203.0.113.1 set interfaces ge-0/0/1 unit 0 family ethernet-switching interface-mode trunk set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members VLAN99 set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members VLAN12 set interfaces ge-0/0/12 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/12 unit 0 family ethernet-switching vlan members VLAN11 set interfaces irb unit 11 family inet address 192.168.11.1/24 set interfaces irb unit 12 family inet address 192.168.1.3/24 set interfaces me0 unit 0 family inet address 10.13.107.181/23 set snmp trap-group space targets 10.13.107.162 set routing-options static route 10.13.0.0/16 next-hop 10.13.106.1 set routing-options static route 172.28.0.0/16 next-hop 10.13.106.1 set routing-options static route 172.29.64.0/20 next-hop 10.13.106.1 set routing-options static route 172.29.80.0/20 next-hop 10.13.106.1 set routing-options static route 0.0.0.0/0 next-hop 192.168.1.254 set protocols l2-learning global-mac-table-aging-time 120 set protocols lldp interface all set protocols lldp-med interface all set protocols igmp-snooping vlan default set vlans VLAN11 vlan-id 11 set vlans VLAN11 l3-interface irb.11 set vlans VLAN12 vlan-id 12 set vlans VLAN12 l3-interface irb.12 set vlans VLAN99 vlan-id 99 set vlans VLAN99 l3-interface irb.99
EX2200 Internet Gateway Switch Configuration
In this topology, the EX2200 switch acts as a simple default gateway to the Internet. It does not play any role in the Juniper Connected Security solution.
set version 15.1R5.5 set system host-name EX2200-INTERNET set system root-authentication encrypted-password "$ABC123" set system services ftp set system services ssh set system services telnet set system syslog user * any emergency set system syslog file messages any notice set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set interfaces ge-0/0/12 unit 0 family ethernet-switching port-mode trunk set interfaces ge-0/0/12 unit 0 family ethernet-switching vlan members VLAN13 set interfaces ge-0/0/13 unit 0 family ethernet-switching port-mode trunk set interfaces ge-0/0/13 unit 0 family ethernet-switching vlan members VLAN13 set interfaces ge-0/0/47 description "to DMZ ge/0/015" set interfaces ge-0/0/47 unit 0 family inet address 198.51.100.2/30 set interfaces me0 unit 0 family inet address 10.13.107.188/23 set interfaces vlan unit 13 family inet address 192.168.231.10/24 set routing-options static route 0.0.0.0/0 next-hop 198.51.100.1 set routing-options static route 10.13.0.0/16 next-hop 10.13.106.1 set routing-options static route 172.28.0.0/16 next-hop 10.13.106.1 set routing-options static route 192.168.0.0/16 next-hop 192.168.231.1 set protocols igmp-snooping vlan all set protocols lldp interface all set protocols lldp-med interface all set vlans VLAN13 vlan-id 13 set vlans VLAN13 l3-interface vlan.13
