自动发现 VPN
了解自动发现 VPN 以及如何在 SRX 系列防火墙中对其进行配置。
自动发现 VPN (ADVPN) 在分支之间动态建立 VPN 隧道,以避免通过中枢路由流量。
使用 功能资源管理器 确认平台和版本对特定功能的支持。
查看该 ADVPN 行为中的特定平台组播 部分,了解与您的平台相关的注意事项。
了解自动发现 VPN
自动发现 VPN (ADVPN) 是一种允许中央中枢动态通知分支两个分支之间流量的更好路径的技术。当两个分支都确认来自中枢的信息时,它们会建立一个捷径隧道并更改路由拓扑,以便主机到达另一端,而无需通过中枢发送流量。
ADVPN 协议
ADVPN 使用 IKEv2 协议的扩展在两个对等方之间交换消息,从而允许分支在彼此之间建立快捷方式隧道。支持 ADVPN 扩展的设备在初始 IKE 交换期间在 IKEv2 通知有效负载中发送ADVPN_SUPPORTED通知,包括其功能信息和 ADVPN 版本号。支持 ADVPN 的设备可以充当 快捷方式建议程序 或快捷方式伙伴,但不能同时充当两者。
建立快捷方式
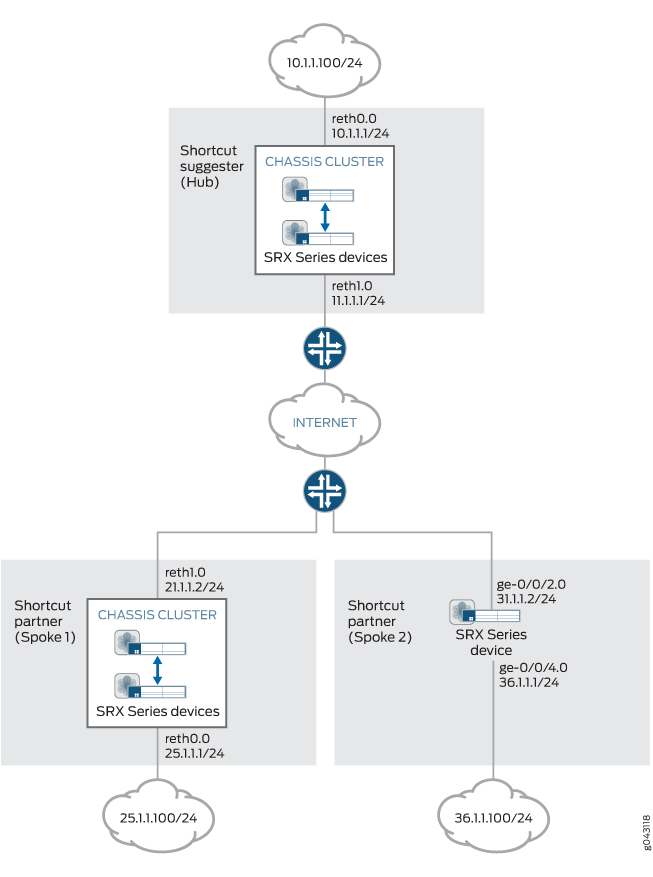
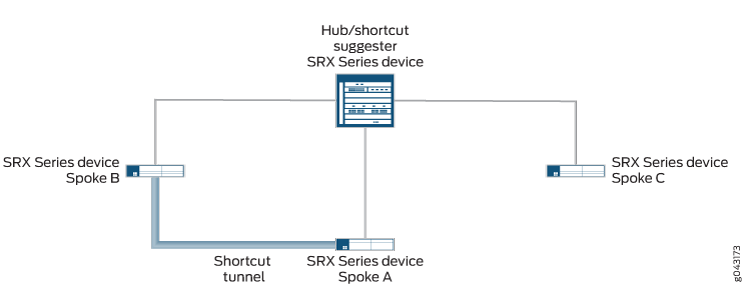
当 IPsec VPN 网关注意到流量正在与其一个对等方一起退出隧道,而与另一个对等方一起进入隧道时,它可以充当 快捷方式建议程序 。 图 1 显示从分支 1 到分支 3 通过中枢的流量。
在设备上配置 ADVPN 时,将在中心和分支之间交换 ADVPN 快捷方式功能信息。只要分支 1 和分支 3 之前已向中心播发 ADVPN 快捷方式伙伴功能,中心就可以建议分支 1 和分支 3 在彼此之间建立快捷方式。
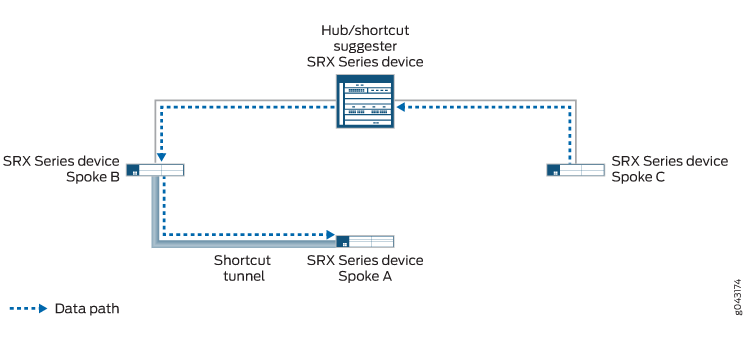
快捷方式建议器将其已建立的 IKEv2 SA 与对等方一起使用,开始与两个对等方之一进行快捷方式交换。如果对等方接受快捷方式交换,则快捷方式建议器将开始与其他对等方进行快捷方式交换。快捷方式交换包括允许对等方(称为 快捷方式伙伴)相互建立 IKE 和 IPsec SA 的信息。只有在两个对等方都接受快捷方式交换后,才会开始在快捷方式伙伴之间创建快捷方式。
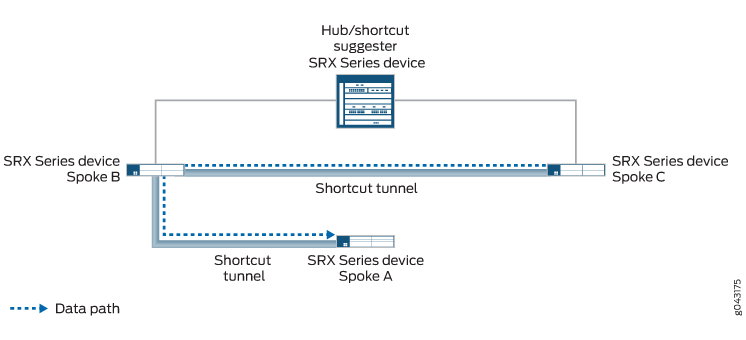
图 2 显示通过分支 1 和分支 3 之间的快捷方式的流量。从分支 1 到分支 3 的流量不需要遍历中枢。
快捷方式发起方和响应方角色
快捷方式建议器选择其中一个快捷方式伙伴作为快捷方式的发起者;另一个伙伴充当响应者。如果其中一个合作伙伴位于 NAT 设备后面,则会选择 NAT 设备后面的合作伙伴作为启动器。如果 NAT 设备后面没有一个伙伴,建议器会随机选择其中一个伙伴作为发起方;另一个伙伴充当响应者。如果两个合作伙伴都在 NAT 设备后面,则无法在它们之间创建快捷方式;建议器不会向任何对等方发送快捷方式交换。
快捷方式建议器首先开始与响应程序进行快捷方式交换。如果响应方接受快捷方式建议,则建议方会通知发起方。
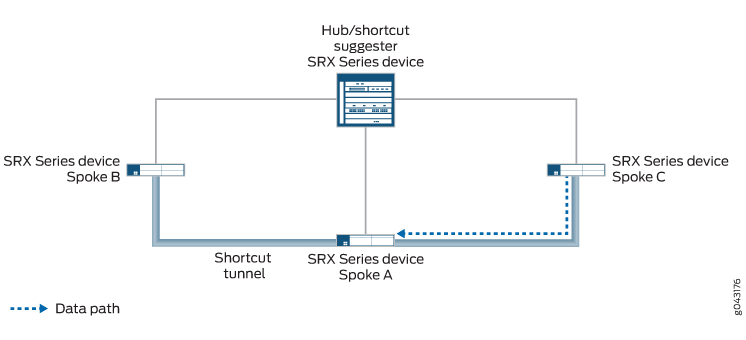
使用快捷方式建议程序通知中包含的信息,快捷方式发起方与响应方建立 IKEv2 交换,并在两个伙伴之间建立新的 IPsec SA。在每个伙伴上,到其伙伴后面网络的路由现在指向快捷方式,而不是伙伴和建议器之间的隧道。来自其中一个伙伴后面的流量,发往另一个快捷伙伴后面的网络,流经该快捷方式。
如果合作伙伴拒绝快捷方式建议,则合作伙伴会通知建议者拒绝的原因。在这种情况下,伙伴之间的流量将继续流经快捷方式建议器。
快捷方式属性
快捷方式从快捷方式建议器接收其某些属性,而其他属性则继承自建议器合作伙伴 VPN 隧道配置。 表 1 显示快捷方式的参数。
|
属性 |
接收/继承自 |
|---|---|
|
ADVPN |
配置 |
|
防重放 |
配置 |
|
身份验证算法 |
配置 |
|
失效对等体检测 |
配置 |
|
DF 位 |
配置 |
|
加密算法 |
配置 |
|
建立隧道 |
建议器 |
|
外部接口 |
配置 |
|
网关策略 |
配置 |
|
通用 IKE ID |
配置 |
|
IKE 版本 |
配置 |
|
安装间隔 |
配置 |
|
本地地址 |
配置 |
|
本地标识 |
建议器 |
|
NAT 遍历 |
配置 |
|
完全向前保密 |
配置 |
|
协议 |
配置 |
|
代理编号 |
不适用 |
|
远程地址 |
建议器 |
|
远程身份 |
建议器 |
|
响应不良 SPI |
配置 |
|
流量选择器 |
不适用 |
快捷终止
默认情况下,快捷方式无限期持续。如果流量在指定时间内低于指定速率,快捷方式合作伙伴将终止快捷方式。默认情况下,如果流量在 300 秒内低于每秒 5 个数据包,快捷方式将被终止;空闲时间和空闲阈值可以为合作伙伴配置。您可以使用或clear security ipsec security-association命令手动clear security ike security-association删除任一快捷方式伙伴上的快捷方式,以清除相应的 IKE 或 IPsec SA。任一快捷方式伙伴都可以随时通过向另一个快捷方式伙伴发送 IKEv2 删除有效负载来终止快捷方式。
快捷方式终止时,将删除相应的 IKE SA 和所有子 IPsec SA。快捷方式终止后,两个快捷方式伙伴上的相应路由都将被删除,两个对等方之间的流量将再次流经建议器。快捷方式终止信息从合作伙伴发送到建议器。
快捷方式的生存期与快捷方式建议器和快捷方式伙伴之间的隧道无关。快捷方式不会仅仅因为建议器和伙伴之间的隧道终止而终止。
使用 PIM 的组播支持
SRX 系列防火墙支持 ADVPN 基础架构中点对多点 (P2MP) 模式下的协议无关组播 (PIM)。您可以使用 P2MP 模式在防火墙的安全隧道接口 st0 上启用 PIM。ADVPN 中使用 PIM 对多播流量的支持类似于 AutoVPN 中提供的支持。ADVPN 在配置多播支持时遵循与 AutoVPN 相同的注意事项。有关了解在 P2MP 基础结构上使用 PIM 的组播支持的更多详细信息,请参阅 了解 AutoVPN。要在 st0 P2MP 接口上启用 PIM,请执行以下操作:
-
在多节点高可用性环境中,P2MP 组播是使用节点本地隧道实现的。st0 接口上的路由协议不支持同步状态隧道。请参阅 多节点高可用性中的 IPsec VPN 支持。
其中一个 SRX 系列防火墙是快捷方式建议器,其余防火墙是快捷方式合作伙伴。通常,组播发送方位于快捷方式建议器后面,而组播接收方位于快捷方式伙伴后面。对于组播支持,建议器和伙伴设备上的安全隧道接口 st0 配置为 PIM P2MP 模式。在上述每台设备上,st0 P2MP 接口跟踪每个邻接方的所有 PIM 联接,以确保组播转发或复制仅发生在处于联接状态的邻接方。
SRX 系列防火墙支持通过 st0 P2MP 接口在 PIM 稀疏模式下的 IP 组播流量。建议器充当第一跳路由器 (FHR) 或集合点 (RP)。合作伙伴可以充当 P2MP 网络中的最后一跳路由器 (LHR)。网络中的设备将组播数据包复制到加入组播组的邻接方。
有关如何在 P2MP 基础结构上配置 PIM 的详细信息,请参阅 在 P2MP 基础结构上配置组播支持。
ADVPN 配置限制
配置 ADVPN 时,请注意以下限制:
-
ADVPN 仅支持站点到站点通信。仅在 AutoVPN 中心上允许配置 ADVPN 建议器。
-
不能同时配置建议者和合作伙伴角色。在网关上启用 ADVPN 后,无法在网关上同时禁用建议者和合作伙伴角色。
-
您无法在同时位于 NAT 设备后面的伙伴之间创建快捷方式。仅当其中一个伙伴位于 NAT 设备后面或 NAT 设备后面没有伙伴时,建议程序才能启动快捷方式交换。
- 要将 IPv6 地址用于 ADVPN,请执行以下操作:
-
您必须在所有中心辐射设备上配置 st0 接口,使其支持 P2MP。
-
您必须运行动态路由协议 (DRP)(如 OSPFv3),以更新通过静态隧道的快捷隧道的路由首选项。
-
请注意,您无法使用基于 IPv6 P2MP st0 接口的 ADVPN 配置 VPN 监视器功能。
-
-
您可以使用支持 IPv6 地址或 IPv4 地址的 DRP 运行 ADVPN 服务,但不能同时使用两者。
-
对于合作伙伴上的配置更改,例如启用、禁用或角色更改,iked:
拆解并重新协商静态 IKE SA 和 IPsec SA,以交换新功能。
清除快捷方式 IKE SA 和 IPsec SA 以及存在的建议信息。
-
对于非 ADVPN 配置更改,例如:
静态隧道配置更改导致同时清除静态 IKE SA 和 IPsec SA,iked 会拆除快捷方式 IKE SA 和 IPsec SA。iked 清理建议信息。快捷方式隧道不会再次重新协商,直到它收到来自建议器的快捷方式建议。
静态隧道配置更改仅导致清除静态隧道 IPsec SA,IKED 会拆除快捷方式 IKE SA 和 IPsec SA。iked 清理建议信息。快捷方式隧道不会再次重新协商,直到它收到来自建议器的快捷方式建议。
我们不支持将 ADVPN 与 kmd 和 iked 进程进行以下配置:
-
IKEv1
-
基于策略的 VPN
-
IKEv2 配置有效负载
-
流量选择器
-
点对点安全隧道接口
-
种子预共享密钥
-
共享预共享密钥 - 不支持 kmd 进程
了解使用快捷方式隧道进行流量路由
隧道抖动或灾难性变化都可能导致静态隧道和快捷方式隧道出现故障。发生这种情况时,到特定目标的流量可能会通过意外的快捷方式隧道路由,而不是通过预期的静态隧道。
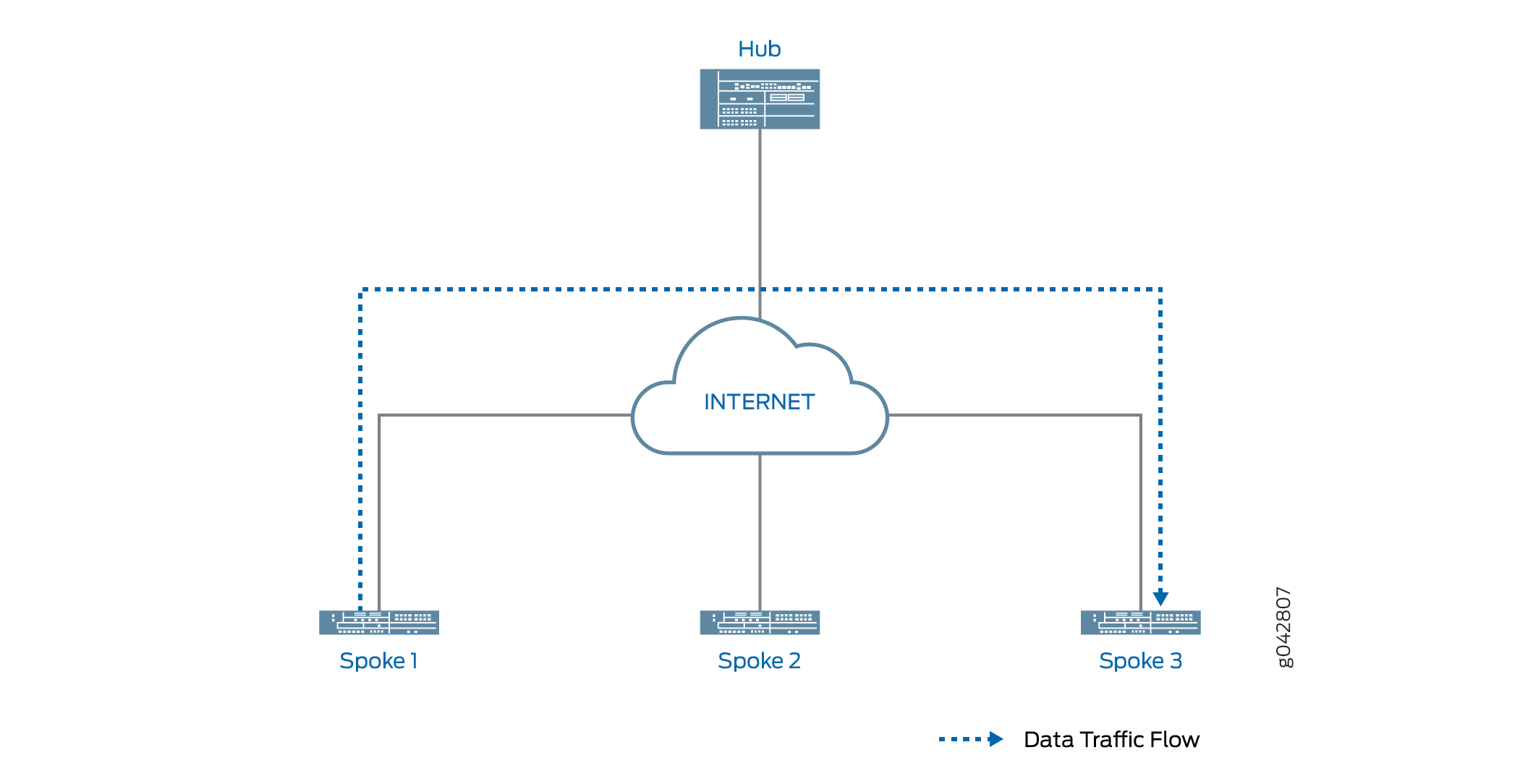
在 中 图 3,中心和每个分支之间存在静态隧道。OSPF 邻接关系在中心和分支之间建立。分支 A 还具有与分支 B 的快捷方式隧道,并且在分支之间建立了 OSPF 邻接关系。中心(快捷方式建议器)识别出,如果中心和分支 A 之间的连接中断,则可以通过分支 B 和分支 A 之间的快捷方式隧道访问分支 A 的网络。
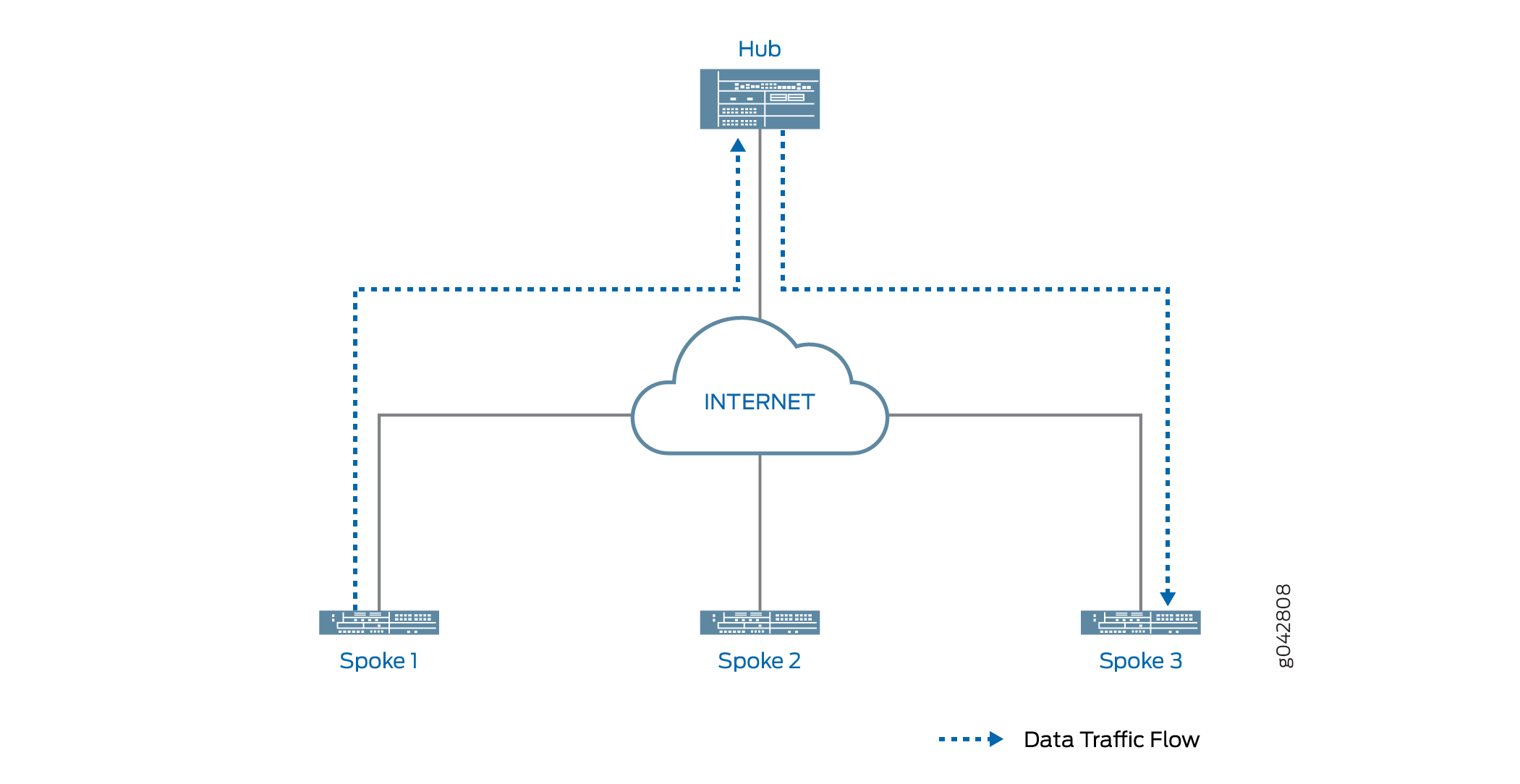
在 中 图 4,中心辐射和分支 A 之间的静态隧道已关闭。如果有从分支 C 到分支 A 的新流量,分支 C 会将流量转发到中心,因为它没有与分支 A 的快捷方式隧道。中心没有与分支 A 的活动静态隧道,但它识别到分支 A 和分支 B 之间存在快捷方式隧道,因此它将流量从分支 C 转发到分支 B。
只要分支 B 和分支 C 都支持自动发现 VPN (ADVPN) 合作伙伴功能,中心就可以建议分支在彼此之间建立直接快捷方式。即使两个分支之间没有直接流量,也会发生这种情况。从分支 C 到分支 A 的流量先通过分支 C 和分支 B 之间的快捷隧道,然后通过分支 B 和分支 A 之间的快捷隧道(请参阅 图 5)。
重新建立中心和分支 A 之间的静态隧道时,该隧道将播发至所有分支。分支 C 了解到到达分支 A 有更好的路线;它不是通过分支 B 传递流量,而是将分支 A 的流量转发到中心。集线器建议在分支 C 和分支 A 之间建立快捷方式隧道。在分支 C 和分支 A 之间建立快捷隧道后,流量将流经快捷隧道(请参阅 图 6)。分支 C 和分支 A 之间的流量不再通过分支 B,分支 B 和分支 C 之间的快捷方式隧道最终会消失。
您可以使用 connection-limit [edit security ike gateway gateway-name advpn partner] 层次结构级别的选项来设置可以使用特定网关与不同快捷方式伙伴创建的快捷方式隧道的最大数量。最大数量(也是默认值)取决于平台。
另请参阅
示例:通过自动发现 VPN 动态隧道提高网络资源利用率
如果要部署 AutoVPN 网络,则可以通过配置自动发现 VPN (ADVPN) 来提高网络资源利用率。在 AutoVPN 网络中,VPN 流量流经中枢,即使流量从一个辐条传输到另一个辐条。ADVPN 允许在分支之间动态建立 VPN 隧道,从而提高网络资源利用率。使用此示例配置 ADVPN,以便在 AutoVPN 网络中启用动态分支到分支 VPN 隧道。
要求
此示例使用以下硬件和软件组件:
三个支持 SRX 系列防火墙作为 AutoVPN 中心和辐射。
支持 ADVPN 的 Junos OS 12.3X48-D10 或更高版本。
在中心辐射中注册的数字证书,允许设备相互进行身份验证。
准备工作:
提交本地证书请求时,获取证书颁发机构 (CA) 的地址及其所需的信息(例如质询密码)。
在每个设备中注册数字证书。
请参阅 注册证书。
此示例使用 OSPF 动态路由协议以及静态路由配置通过 VPN 隧道转发数据包。您应该熟悉用于通过 VPN 隧道转发数据包的 OSPF 动态路由协议。
概述
此示例显示了 ADVPN 的 AutoVPN 中心和两个分支的配置。分支与中心建立 IPsec VPN 连接,使它们能够相互通信以及访问中心上的资源。虽然流量最初通过中心从一个分支传递到另一个分支,但 ADVPN 允许分支在彼此之间建立直接的安全关联。集线器充当快捷方式建议器。在中心,ADVPN 配置禁用该 partner 角色。在辐射上,ADVPN 配置禁用该 suggester 角色。
在 AutoVPN 中心和分支上配置的某些第 1 阶段和第 2 阶段 IKE 隧道选项必须具有相同的值。 表 2 显示了此示例中使用的值。
选项 |
value |
|---|---|
IKE 提案: |
|
身份验证方法 |
rsa-signatures |
Diffie-Hellman (DH) 组 |
group5 |
身份验证算法 |
sha1 |
加密算法 |
aes-256-cbc |
IKE 策略: |
|
证书 |
本地证书 |
IKE 网关: |
|
版本 |
仅 v2 |
IPsec 提议: |
|
协议 |
esp |
身份验证算法 |
HMAC-SHA1-96 |
加密算法 |
aes-256-cbc |
IPsec 策略: |
|
完全向前保密 (PFS) 组 |
group5 |
中心辐射上的 IKE 网关配置包括标识 VPN 对等方的远程和本地值。 表 3 显示了此示例中中心辐射的 IKE 网关配置。
选项 |
枢纽 |
辐条 |
|---|---|---|
远程 IP 地址 |
动态 |
辐条1:11.1.1.1 辐条2:11.1.1.1 |
本地 IP 地址 |
11.1.1.1 |
辐条1:21.1.1.2 辐条2:31.1.1.2 |
远程 IKE ID |
可分辨名称 (DN),在分支证书的组织 (O) 字段中带有字符串“XYZ”,在组织单位 (OU) 字段中带有“Sales” |
在中心证书的 OU 字段中具有字符串“Sales”的 DN |
本地 IKE ID |
集线器证书上的 DN |
辐射证书上的 DN |
如果分支证书的主题字段在 O 字段中包含字符串“XYZ”,在 OU 字段中包含字符串“Sales”,则中心将验证分支的 IKE ID。
在此示例中,允许所有流量的默认安全策略用于所有设备。应为生产环境配置更严格的安全策略。请参阅 安全策略概述。
配置
配置建议器 (集线器)
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到 [edit] 层级的 CLI 中,然后从配置模式进入 commit 。
set interfaces ge-0/0/3 gigether-options redundant-parent reth0 set interfaces ge-0/0/4 gigether-options redundant-parent reth1 set interfaces ge-7/0/3 gigether-options redundant-parent reth0 set interfaces ge-7/0/4 gigether-options redundant-parent reth1 set interfaces reth0 redundant-ether-options redundancy-group 1 set interfaces reth0 unit 0 family inet address 10.1.1.1/24 set interfaces reth1 redundant-ether-options redundancy-group 1 set interfaces reth1 unit 0 family inet address 11.1.1.1/24 set interfaces st0 unit 1 multipoint set interfaces st0 unit 1 family inet address 172.16.1.1/24 set protocols ospf graceful-restart restart-duration 300 set protocols ospf graceful-restart notify-duration 300 set protocols ospf graceful-restart no-strict-lsa-checking set protocols ospf area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf area 0.0.0.0 interface st0.1 metric 10 set protocols ospf area 0.0.0.0 interface st0.1 retransmit-interval 1 set protocols ospf area 0.0.0.0 interface st0.1 dead-interval 40 set protocols ospf area 0.0.0.0 interface st0.1 demand-circuit set protocols ospf area 0.0.0.0 interface st0.1 dynamic-neighbors set protocols ospf area 0.0.0.0 interface reth0.0 set routing-options graceful-restart set routing-options static route 21.1.1.0/24 next-hop 11.1.1.2 set routing-options static route 31.1.1.0/24 next-hop 11.1.1.2 set routing-options router-id 172.16.1.1 set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group5 set security ike proposal IKE_PROP authentication-algorithm sha1 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate Suggester_Certificate_ID set security ike gateway SUGGESTER_GW ike-policy IKE_POL set security ike gateway SUGGESTER_GW dynamic distinguished-name wildcard O=XYZ, OU=Sales set security ike gateway SUGGESTER_GW dynamic ike-user-type group-ike-id set security ike gateway SUGGESTER_GW dead-peer-detection set security ike gateway SUGGESTER_GW local-identity distinguished-name set security ike gateway SUGGESTER_GW external-interface reth1.0 set security ike gateway SUGGESTER_GW local-address 11.1.1.1 set security ike gateway SUGGESTER_GW advpn partner disable set security ike gateway SUGGESTER_GW advpn suggester set security ike gateway SUGGESTER_GW version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha1-96 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group5 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn SUGGESTER_VPN bind-interface st0.1 set security ipsec vpn SUGGESTER_VPN ike gateway SUGGESTER_GW set security ipsec vpn SUGGESTER_VPN ike ipsec-policy IPSEC_POL set security pki ca-profile advpn ca-identity advpn set security pki ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/ set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces st0.1 set security zones security-zone trust interfaces reth0.0 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces reth1.0 set security policies default-policy permit-all
分步过程
下面的示例要求您在各个配置层级中进行导航。有关操作说明,请参阅 CLI 用户指南中的在配置模式下使用 CLI 编辑器。
要配置建议器:
配置接口。
[edit interfaces] user@host# set ge-0/0/3 gigether-options redundant-parent reth0 user@host# set ge-0/0/4 gigether-options redundant-parent reth1 user@host# set ge-7/0/3 gigether-options redundant-parent reth0 user@host# set ge-7/0/4 gigether-options redundant-parent reth1 user@host# set reth0 redundant-ether-options redundancy-group 1 user@host# set reth0 unit 0 family inet address 10.1.1.1/24 user@host# set reth1 redundant-ether-options redundancy-group 1 user@host# set reth1 unit 0 family inet address 11.1.1.1/24 user@host# set st0 unit 1 multipoint user@host# set st0 unit 1 family inet address 172.16.1.1/24
配置路由协议和静态路由。
[edit protocols ospf] user@host# set graceful-restart restart-duration 300 user@host# set graceful-restart notify-duration 300 user@host# set graceful-restart no-strict-lsa-checking user@host# set area 0.0.0.0 interface st0.1 interface-type p2mp user@host# set area 0.0.0.0 interface st0.1 metric 10 user@host# set area 0.0.0.0 interface st0.1 retransmit-interval 1 user@host# set area 0.0.0.0 interface st0.1 dead-interval 40 user@host# set area 0.0.0.0 interface st0.1 demand-circuit user@host# set area 0.0.0.0 interface st0.1 dynamic-neighbors user@host# set area 0.0.0.0 interface reth0.0 [edit routing-options] user@host# set graceful-restart user@host# set static route 21.1.1.0/24 next-hop 11.1.1.2 user@host# set static route 31.1.1.0/24 next-hop 11.1.1.2 user@host# set router-id 172.16.1.1
配置第 1 阶段选项。
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group5 user@host# set authentication-algorithm sha1 user@host# set encryption-algorithm aes-256-cbc [edit security ike policy IKE_POL] user@host# set proposals IKE_PROP user@host# set certificate local-certificate Suggester_Certificate_ID [edit security ike gateway SUGGESTER_GW] user@host# set ike-policy IKE_POL user@host# set dynamic distinguished-name wildcard O=XYZ, OU=Sales user@host# set dynamic ike-user-type group-ike-id user@host# set dead-peer-detection user@host# set local-identity distinguished-name user@host# set external-interface reth1.0 user@host# set local-address 11.1.1.1 user@host# set advpn partner disable user@host# set advpn suggester user@host# set version v2-only
配置第 2 阶段选项。
[edit security ipsec proposal IPSEC_PROP] user@host# set protocol esp user@host# set authentication-algorithm hmac-sha1-96 user@host# set encryption-algorithm aes-256-cbc [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group5 user@host# set proposals IPSEC_PROP [edit security isec vpn SUGGESTER_VPN] user@host# set bind-interface st0.1 user@host# set ike gateway SUGGESTER_GW user@host# set ike ipsec-policy IPSEC_POL
配置证书信息。
[edit security pki] user@host# set ca-profile advpn ca-identity advpn user@host# set ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/
配置区域。
[edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces st0.1 user@host# set interfaces reth0.0 [edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces reth1.0
配置默认安全策略。
[edit security policies] user@host# set default-policy permit-all
结果
在配置模式下,输入 show interfaces、 show protocols、 show routing-optionsshow security ike、 show security ipsec、 show security pki、 和show security zonesshow security policies命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明,以便进行更正。
[edit]
user@host# show interfaces
ge-0/0/3 {
gigether-options {
redundant-parent reth0;
}
}
ge-0/0/4 {
gigether-options {
redundant-parent reth1;
}
}
ge-7/0/3 {
gigether-options {
redundant-parent reth0;
}
}
ge-7/0/4 {
gigether-options {
redundant-parent reth1;
}
}
reth0 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 10.1.1.1/24;
}
}
}
reth1 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 11.1.1.1/24;
}
}
}
st0 {
unit 1 {
multipoint;
family inet {
address 172.16.1.1/24;
}
}
}
[edit]
user@host# show protocols
ospf {
graceful-restart {
restart-duration 300;
notify-duration 300;
no-strict-lsa-checking;
}
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
metric 10;
retransmit-interval 1;
dead-interval 40;
demand-circuit;
dynamic-neighbors;
}
interface reth0.0;
}
}
[edit]
user@host# show routing-options
graceful-restart;
static {
route 21.1.1.0/24 next-hop 11.1.1.2;
route 31.1.1.0/24 next-hop 11.1.1.2;
}
router-id 172.16.1.1;
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group5;
authentication-algorithm sha1;
encryption-algorithm aes-256-cbc;
}
policy IKE_POL {
proposals IKE_PROP;
certificate {
local-certificate Suggester_Certificate_ID;
}
}
gateway SUGGESTER_GW {
ike-policy IKE_POL;
dynamic {
distinguished-name {
wildcard O=XYZ, OU=Sales;
}
ike-user-type group-ike-id;
}
dead-peer-detection {
}
local-identity distinguished-name;
external-interface reth1.0
local-address 11.1.1.1;
advpn {
partner {
disable;
}
suggester {
]
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm aes-256-cbc;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group5;
}
proposals IPSEC_PROP;
}
vpn SUGGESTER_VPN {
bind-interface st0.1;
ike {
gateway SUGGESTER_GW;
ipsec-policy IPSEC_POL;
}
}
[edit]
user@host# show security pki
ca-profile advpn {
ca-identity advpn;
enrollment {
url http://10.157.92.176:8080/scep/advpn/;
}
}
[edit]
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
st0.1;
reth0.0;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth1.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
如果完成设备配置,请从配置模式输入 commit。
配置合作伙伴(分支 1)
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到 [edit] 层级的 CLI 中,然后从配置模式进入 commit 。
set interfaces ge-0/0/3 gigether-options redundant-parent reth0 set interfaces ge-0/0/4 gigether-options redundant-parent reth1 set interfaces ge-7/0/3 gigether-options redundant-parent reth0 set interfaces ge-7/0/4 gigether-options redundant-parent reth1 set interfaces reth0 redundant-ether-options redundancy-group 1 set interfaces reth0 unit 0 family inet address 25.1.1.1/24 set interfaces reth1 redundant-ether-options redundancy-group 1 set interfaces reth1 unit 0 family inet address 21.1.1.2/24 set interfaces st0 unit 1 multipoint set interfaces st0 unit 1 family inet address 172.16.1.2/24 set protocols ospf graceful-restart restart-duration 300 set protocols ospf graceful-restart notify-duration 300 set protocols ospf graceful-restart no-strict-lsa-checking set protocols ospf area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf area 0.0.0.0 interface st0.1 metric 15 set protocols ospf area 0.0.0.0 interface st0.1 retransmit-interval 1 set protocols ospf area 0.0.0.0 interface st0.1 dead-interval 40 set protocols ospf area 0.0.0.0 interface st0.1 demand-circuit set protocols ospf area 0.0.0.0 interface st0.1 dynamic-neighbors set protocols ospf area 0.0.0.0 interface reth0.0 set routing-options graceful-restart set routing-options static route 11.1.1.0/24 next-hop 21.1.1.1 set routing-options static route 31.1.1.0/24 next-hop 21.1.1.1 set routing-options router-id 172.16.1.2 set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group5 set security ike proposal IKE_PROP authentication-algorithm sha1 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate Partner1_Certificate_ID set security ike gateway PARTNER_GW ike-policy IKE_POL set security ike gateway PARTNER_GW address 11.1.1.1 set security ike gateway PARTNER_GW local-identity distinguished-name set security ike gateway PARTNER_GW remote-identity distinguished-name container OU=Sales set security ike gateway PARTNER_GW external-interface reth1 set security ike gateway PARTNER_GW local-address 21.1.1.2 set security ike gateway PARTNER_GW advpn suggester disable set security ike gateway PARTNER_GW advpn partner set security ike gateway PARTNER_GW version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha1-96 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group5 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn PARTNER_VPN bind-interface st0.1 set security ipsec vpn PARTNER_VPN ike gateway PARTNER_GW set security ipsec vpn PARTNER_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn PARTNER_VPN establish-tunnels immediately set security pki ca-profile advpn ca-identity advpn set security pki ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/ set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces st0.1 set security zones security-zone trust interfaces reth0.0 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces reth1.0 set security policies default-policy permit-all
分步过程
下面的示例要求您在各个配置层级中进行导航。有关操作说明,请参阅 CLI 用户指南中的在配置模式下使用 CLI 编辑器。
要配置分支 1:
配置接口。
[edit interfaces] user@host# set ge-0/0/3 gigether-options redundant-parent reth0 user@host# set ge-0/0/4 gigether-options redundant-parent reth1 user@host# set ge-7/0/3 gigether-options redundant-parent reth0 user@host# set ge-7/0/4 gigether-options redundant-parent reth1 user@host# set reth0 redundant-ether-options redundancy-group 1 user@host# set reth0 unit 0 family inet address 25.1.1.1/24 user@host# set reth1 redundant-ether-options redundancy-group 1 user@host# set reth1 unit 0 family inet address 21.1.1.2/24 user@host# set st0 unit 1 multipoint user@host# set st0 unit 1 family inet address 172.16.1.2/24
配置路由协议和静态路由。
[edit protocols ospf] user@host# set graceful-restart restart-duration 300 user@host# set graceful-restart notify-duration 300 user@host# set graceful-restart no-strict-lsa-checking user@host# set area 0.0.0.0 interface st0.1 interface-type p2mp user@host# set area 0.0.0.0 interface st0.1 metric 15 user@host# set area 0.0.0.0 interface st0.1 retransmit-interval 1 user@host# set area 0.0.0.0 interface st0.1 dead-interval 40 user@host# set area 0.0.0.0 interface st0.1 demand-circuit user@host# set area 0.0.0.0 interface st0.1 dynamic-neighbors user@host# set protocols ospf area 0.0.0.0 interface reth0.0 [edit routing-options] user@host# set graceful-restart user@host# set static route 11.1.1.0/24 next-hop 21.1.1.1 user@host# set static route 31.1.1.0/24 next-hop 21.1.1.1 user@host# set router-id 172.16.1.2
配置第 1 阶段选项。
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group5 user@host# set authentication-algorithm sha1 user@host# set encryption-algorithm aes-256-cbc [edit security ike policy IKE_POL] user@host# set proposals IKE_PROP user@host# set certificate local-certificate Partner1_Certificate_ID [edit security ike gateway PARTNER_GW] user@host# set ike-policy IKE_POL user@host# set address 11.1.1.1 user@host# set local-identity distinguished-name user@host# set remote-identity distinguished-name container OU=Sales user@host# set external-interface reth1 user@host# set local-address 21.1.1.2 user@host# set advpn suggester disable user@host# set advpn partner user@host# set version v2-only
配置第 2 阶段选项。
[edit security ipsec proposal IPSEC_PROP] user@host# set protocol esp user@host# set authentication-algorithm hmac-sha1-96 user@host# set encryption-algorithm aes-256-cbc [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group5 user@host# set proposals IPSEC_PROP [edit security isec vpn PARTNER_VPN] user@host# set bind-interface st0.1 user@host# set ike gateway PARTNER_GW user@host# set ike ipsec-policy IPSEC_POL user@host# set establish-tunnels immediately
配置证书信息。
[edit security pki] user@host# set ca-profile advpn ca-identity advpn user@host# set ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/
配置区域。
[edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces st0.1 user@host# set interfaces reth0.0 [edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces reth1.0
配置默认安全策略。
[edit security policies] user@host# set default-policy permit-all
结果
在配置模式下,输入 show interfaces、 show protocols、 show routing-optionsshow security ike、 show security ipsec、 show security pki、 和show security zonesshow security policies命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明,以便进行更正。
[edit]
user@host# show interfaces
ge-0/0/3 {
gigether-options {
redundant-parent reth0;
}
}
ge-0/0/4 {
gigether-options {
redundant-parent reth1;
}
}
ge-7/0/3 {
gigether-options {
redundant-parent reth0;
}
}
ge-7/0/4 {
gigether-options {
redundant-parent reth1;
}
}
reth0 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 25.1.1.1/24;
}
}
}
reth1 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 21.1.1.2/24;
}
}
}
st0 {
unit 1 {
multipoint;
family inet {
address 172.16.1.2/24;
}
}
}
[edit]
user@host# show protocols
ospf {
graceful-restart {
restart-duration 300;
notify-duration 300;
no-strict-lsa-checking;
}
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
metric 15;
retransmit-interval 1;
dead-interval 40;
demand-circuit;
dynamic-neighbors;
}
interface reth0.0;
}
}
[edit]
user@host# show routing-options
graceful-restart;
static {
route 11.1.1.0/24 next-hop 21.1.1.1;
route 31.1.1.0/24 next-hop 21.1.1.1;
}
router-id 172.16.1.2;
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group5;
authentication-algorithm sha1;
encryption-algorithm aes-256-cbc;
}
policy IKE_POL {
proposals IKE_PROP;
certificate {
local-certificate Partner1_Certificate_ID;
}
}
gateway PARTNER_GW {
ike-policy IKE_POL;
address 11.1.1.1;
local-identity distinguished-name;
remote-identity distinguished-name container OU=Sales;
external-interface reth1;
local-address 21.1.1.2;
advpn {
suggester {
disable;
}
partner {
}
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm aes-256-cbc;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group5;
}
proposals IPSEC_PROP;
}
vpn PARTNER_VPN {
bind-interface st0.1;
ike {
gateway PARTNER_GW;
ipsec-policy IPSEC_POL;
}
establish-tunnels immediately;
}
[edit]
user@host# show security pki
ca-profile advpn {
ca-identity advpn;
enrollment {
url http://10.157.92.176:8080/scep/advpn/;
}
}
[edit]
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
st0.1;
reth0.0;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth1.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
如果完成设备配置,请从配置模式输入 commit。
配置合作伙伴(分支 2)
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到 [edit] 层级的 CLI 中,然后从配置模式进入 commit 。
set interfaces ge-0/0/2 unit 0 family inet address 31.1.1.2/24 set interfaces ge-0/0/4 unit 0 family inet address 36.1.1.1/24 set interfaces st0 unit 1 multipoint set interfaces st0 unit 1 family inet address 172.16.1.3/24 set protocols ospf graceful-restart restart-duration 300 set protocols ospf graceful-restart notify-duration 300 set protocols ospf graceful-restart no-strict-lsa-checking set protocols ospf area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf area 0.0.0.0 interface st0.1 metric 15 set protocols ospf area 0.0.0.0 interface st0.1 retransmit-interval 1 set protocols ospf area 0.0.0.0 interface st0.1 dead-interval 40 set protocols ospf area 0.0.0.0 interface st0.1 demand-circuit set protocols ospf area 0.0.0.0 interface st0.1 dynamic-neighbors set protocols ospf area 0.0.0.0 interface ge-0/0/4.0 set routing-options graceful-restart set routing-options static route 11.1.1.0/24 next-hop 31.1.1.1 set routing-options static route 21.1.1.0/24 next-hop 31.1.1.1 set routing-options router-id 172.16.1.3 set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group5 set security ike proposal IKE_PROP authentication-algorithm sha1 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate Partner2_Certificate_ID set security ike gateway PARTNER_GW ike-policy IKE_POL set security ike gateway PARTNER_GW address 11.1.1.1 set security ike gateway PARTNER_GW dead-peer-detection set security ike gateway PARTNER_GW local-identity distinguished-name set security ike gateway PARTNER_GW remote-identity distinguished-name container OU=Sales set security ike gateway PARTNER_GW external-interface ge-0/0/2.0 set security ike gateway PARTNER_GW local-address 31.1.1.2 set security ike gateway PARTNER_GW advpn suggester disable set security ike gateway PARTNER_GW advpn partner set security ike gateway PARTNER_GW version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha1-96 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group5 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn PARTNER_VPN bind-interface st0.1 set security ipsec vpn PARTNER_VPN ike gateway PARTNER_GW set security ipsec vpn PARTNER_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn PARTNER_VPN establish-tunnels immediately set security pki ca-profile advpn ca-identity advpn set security pki ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/ set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/4.0 set security zones security-zone trust interfaces st0.1 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces ge-0/0/2.0 set security policies default-policy permit-all
分步过程
下面的示例要求您在各个配置层级中进行导航。有关操作说明,请参阅 CLI 用户指南中的在配置模式下使用 CLI 编辑器。
要配置分支 2:
配置接口。
[edit interfaces] user@host# set ge-0/0/2 unit 0 family inet address 31.1.1.2/24 user@host# set ge-0/0/4 unit 0 family inet address 36.1.1.1/24 user@host# set st0 unit 1 multipoint user@host# set st0 unit 1 family inet address 172.16.1.3/24
配置路由协议和静态路由。
[edit protocols ospf user@host# set graceful-restart restart-duration 300 user@host# set graceful-restart notify-duration 300 user@host# set graceful-restart no-strict-lsa-checking user@host# set area 0.0.0.0 interface st0.1 interface-type p2mp user@host# set area 0.0.0.0 interface st0.1 metric 15 user@host# set area 0.0.0.0 interface st0.1 retransmit-interval 1 user@host# set area 0.0.0.0 interface st0.1 dead-interval 40 user@host# set area 0.0.0.0 interface st0.1 demand-circuit user@host# set area 0.0.0.0 interface st0.1 dynamic-neighbors user@host# set area 0.0.0.0 interface ge-0/0/4.0 [edit routing-options] user@host# set graceful-restart user@host# set static route 11.1.1.0/24 next-hop 31.1.1.1 user@host# set static route 21.1.1.0/24 next-hop 31.1.1.1 user@host# set router-id 172.16.1.3
配置第 1 阶段选项。
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group5 user@host# set authentication-algorithm sha1 user@host# set encryption-algorithm aes-256-cbc [edit security ike policy IKE_POL] user@host# set proposals IKE_PROP user@host# set certificate local-certificate Partner2_Certificate_ID [edit security ike gateway PARTNER_GW] user@host# set ike-policy IKE_POL user@host# set address 11.1.1.1 user@host# set local-identity distinguished-name user@host# set remote-identity distinguished-name container OU=Sales user@host# set external-interface ge-0/0/2.0 user@host# set local-address 31.1.1.2 user@host# set advpn suggester disable user@host# set advpn partner user@host# set version v2-only
配置第 2 阶段选项。
[edit security ipsec proposal IPSEC_PROP] user@host# set protocol esp user@host# set authentication-algorithm hmac-sha1-96 user@host# set encryption-algorithm aes-256-cbc [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group5 user@host# set proposals IPSEC_PROP [edit security isec vpn PARTNER_VPN] user@host# set bind-interface st0.1 user@host# set ike gateway PARTNER_GW user@host# set ike ipsec-policy IPSEC_POL user@host# set establish-tunnels immediately
配置证书信息。
[edit security pki] user@host# set ca-profile advpn ca-identity advpn user@host# set ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/
配置区域。
[edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces ge-0/0/4.0 user@host# set interfaces st0.1 [edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces ge-0/0/2.0
配置默认安全策略。
[edit security policies] user@host# set default-policy permit-all
结果
在配置模式下,输入 show interfaces、 show protocols、 show routing-optionsshow security ike、 show security ipsec、 show security pki、 和show security zonesshow security policies命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明,以便进行更正。
[edit]
user@host# show interfaces
ge-0/0/2 {
unit 0 {
family inet {
address 31.1.1.2/24;
}
}
}
ge-0/0/4{
unit 0 {
family inet {
address 36.1.1.1/24;
}
}
}
st0 {
unit 1 {
multipoint;
family inet {
address 172.16.1.3/24;
}
}
}
[edit]
user@host# show protocols
ospf {
graceful-restart {
restart-duration 300;
notify-duration 300;
no-strict-lsa-checking;
}
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
metric 15;
retransmit-interval 1;
dead-interval 40;
demand-circuit;
dynamic-neighbors;
}
interface ge-0/0/4.0;
}
}
[edit]
user@host# show routing-options
graceful-restart;
static {
route 11.1.1.0/24 next-hop 31.1.1.1;
route 21.1.1.0/24 next-hop 31.1.1.1;
}
router-id 172.16.1.3;
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group5;
authentication-algorithm sha1;
encryption-algorithm aes-256-cbc;
}
policy IKE_POL {
proposals IKE_PROP;
certificate {
local-certificate Partner2_Certificate_ID
}
}
gateway PARTNER_GW {
ike-policy IKE_POL;
address 11.1.1.1;
local-identity distinguished-name;
remote-identity distinguished-name container OU=Sales;
external-interface ge-0/0/2.0;
local-address 31.1.1.2;
advpn {
suggester{
disable;
}
partner {
}
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm aes-256-cbc;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group5;
}
proposals IPSEC_PROP;
}
vpn PARTNER_VPN {
bind-interface st0.1;
ike {
gateway PARTNER_GW;
ipsec-policy IPSEC_POL;
}
establish-tunnels immediately;
}
[edit]
user@host# show security pki
ca-profile advpn {
ca-identity advpn;
enrollment {
url http://10.157.92.176:8080/scep/advpn/;
}
}
[edit]
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/4.0;
st0.1;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
如果完成设备配置,请从配置模式输入 commit。
验证
确认配置工作正常。首先,验证是否已在 AutoVPN 中心和分支之间建立隧道。当流量通过中心从一个分支传递到另一个分支时,可以在分支之间建立快捷方式。验证快捷方式伙伴是否已在它们之间建立隧道,以及伙伴上是否安装了到对等方的路由。
验证中心和分支之间的隧道
目的
验证是否已在 AutoVPN 中心和分支之间建立隧道。从一个辐条到另一个辐条的初始流量必须通过中枢。
操作
在操作模式下,在中心辐射上输入 show security ike security-associations 和 show security ipsec security-associations 命令。
在集线器上输入以下命令:
user@host> show security ike security-associations node1: -------------------------------------------------------------------------- Index State Initiator cookie Responder cookie Mode Remote Address 10957048 UP 2d58d8fbc396762d 46145be580c68be0 IKEv2 31.1.1.2 10957049 UP fa05ee6d0f2cfb22 16f5ca836b118c0e IKEv2 21.1.1.2
user@host> show security ike security-associations detail
node1:
--------------------------------------------------------------------------
IKE peer 31.1.1.2, Index 10957048, Gateway Name: SUGGESTER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Suggester, Peer Capability: Partner
Suggester Shortcut Suggestions Statistics:
Suggestions sent : 0
Suggestions accepted: 0
Suggestions declined: 0
Role: Responder, State: UP
Initiator cookie: 2d58d8fbc396762d, Responder cookie: 46145be580c68be0
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 11.1.1.1:500, Remote: 31.1.1.2:500
Lifetime: Expires in 28196 seconds
Peer ike-id: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2030
Output bytes : 2023
Input packets: 4
Output packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 11.1.1.1:500, Remote: 31.1.1.2:500
Local identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Remote identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
IKE peer 21.1.1.2, Index 10957049, Gateway Name: SUGGESTER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Suggester, Peer Capability: Partner
Suggester Shortcut Suggestions Statistics:
Suggestions sent : 0
Suggestions accepted: 0
Suggestions declined: 0
Role: Responder, State: UP
Initiator cookie: fa05ee6d0f2cfb22, Responder cookie: 16f5ca836b118c0e
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 11.1.1.1:500, Remote: 21.1.1.2:500
Lifetime: Expires in 28219 seconds
Peer ike-id: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2030
Output bytes : 2023
Input packets: 4
Output packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 11.1.1.1:500, Remote: 21.1.1.2:500
Local identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Remote identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations node1: -------------------------------------------------------------------------- Total active tunnels: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <201326593 ESP:aes-cbc-256/sha1 44ccf265 2999/ unlim - root 500 31.1.1.2 >201326593 ESP:aes-cbc-256/sha1 a9d301b0 2999/ unlim - root 500 31.1.1.2 <201326594 ESP:aes-cbc-256/sha1 98a2b155 3022/ unlim - root 500 21.1.1.2 >201326594 ESP:aes-cbc-256/sha1 de912bcd 3022/ unlim - root 500 21.1.1.2
user@host> show security ipsec security-associations detail
node1:
--------------------------------------------------------------------------
ID: 201326593 Virtual-system: root, VPN Name: SUGGESTER_VPN
Local Gateway: 11.1.1.1, Remote Gateway: 31.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 2, Fail#: 0, Def-Del#: 0 Flag: 0x608a29
Tunnel events:
Tue Jan 13 2015 12:57:48 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:57:48 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:57:48 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: 44ccf265, AUX-SPI: 0
Hard lifetime: Expires in 2991 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2414 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: a9d301b0, AUX-SPI: 0
Hard lifetime: Expires in 2991 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2414 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
ID: 201326594 Virtual-system: root, VPN Name: SUGGESTER_VPN
Local Gateway: 11.1.1.1, Remote Gateway: 21.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 3, Fail#: 0, Def-Del#: 0 Flag: 0x608a29
Tunnel events:
Tue Jan 13 2015 12:58:11 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:58:11 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:58:11 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: 98a2b155, AUX-SPI: 0
Hard lifetime: Expires in 3014 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2436 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: de912bcd, AUX-SPI: 0
Hard lifetime: Expires in 3014 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2436 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 28 destinations, 28 routes (27 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
25.1.1.0/24 *[OSPF/10] 00:00:27, metric 11
> to 172.16.1.2 via st0.1
36.1.1.0/24 *[OSPF/10] 00:00:27, metric 11
> to 172.16.1.3 via st0.1
172.16.1.2/32 *[OSPF/10] 00:00:27, metric 10
> to 172.16.1.2 via st0.1
172.16.1.3/32 *[OSPF/10] 00:00:27, metric 10
> to 172.16.1.3 via st0.1
224.0.0.5/32 *[OSPF/10] 00:00:48, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.3 st0.1 Full 172.16.1.3 128 - 172.16.1.2 st0.1 Full 172.16.1.2 128 -
在分支 1 上输入以下命令:
user@host> show security ike security-associations node0: -------------------------------------------------------------------------- Index State Initiator cookie Responder cookie Mode Remote Address 578872 UP fa05ee6d0f2cfb22 16f5ca836b118c0e IKEv2 11.1.1.1
user@host> show security ike security-associations detail
node0:
--------------------------------------------------------------------------
IKE peer 11.1.1.1, Index 578872, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Partner, Peer Capability: Suggester
Partner Shortcut Suggestions Statistics:
Suggestions received: 0
Suggestions accepted: 0
Suggestions declined: 0
Role: Initiator, State: UP
Initiator cookie: fa05ee6d0f2cfb22, Responder cookie: 16f5ca836b118c0e
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 21.1.1.2:500, Remote: 11.1.1.1:500
Lifetime: Expires in 28183 seconds
Peer ike-id: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2023
Output bytes : 2030
Input packets: 4
Output packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Initiator, Message ID: 0
Local: 21.1.1.2:500, Remote: 11.1.1.1:500
Local identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations node0: -------------------------------------------------------------------------- Total active tunnels: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <67108866 ESP:aes-cbc-256/sha1 de912bcd 2985/ unlim - root 500 11.1.1.1 >67108866 ESP:aes-cbc-256/sha1 98a2b155 2985/ unlim - root 500 11.1.1.1
user@host> show security ipsec security-associations detail
node0:
--------------------------------------------------------------------------
ID: 67108866 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 21.1.1.2, Remote Gateway: 11.1.1.1
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x8608a29
Tunnel events:
Tue Jan 13 2015 12:58:11 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:58:11 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:58:11 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: de912bcd, AUX-SPI: 0
Hard lifetime: Expires in 2980 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2358 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 98a2b155, AUX-SPI: 0
Hard lifetime: Expires in 2980 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2358 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 29 destinations, 29 routes (28 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
10.1.1.0/24 *[OSPF/10] 00:11:46, metric 16
> to 172.16.1.1 via st0.1
36.1.1.0/24 *[OSPF/10] 00:11:46, metric 26
> to 172.16.1.1 via st0.1
172.16.1.1/32 *[OSPF/10] 00:11:46, metric 15
> to 172.16.1.1 via st0.1
172.16.1.3/32 *[OSPF/10] 00:11:46, metric 25
> to 172.16.1.1 via st0.1
224.0.0.5/32 *[OSPF/10] 00:16:52, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.1 st0.1 Full 172.16.1.1 128 -
在分支 2 上输入以下命令:
user@host> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 2299162 UP 2d58d8fbc396762d 46145be580c68be0 IKEv2 11.1.1.1
user@host> show security ike security-associations detail
IKE peer 11.1.1.1, Index 2299162, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Partner, Peer Capability: Suggester
Partner Shortcut Suggestions Statistics:
Suggestions received: 0
Suggestions accepted: 0
Suggestions declined: 0
Role: Initiator, State: UP
Initiator cookie: 2d58d8fbc396762d, Responder cookie: 46145be580c68be0
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 31.1.1.2:500, Remote: 11.1.1.1:500
Lifetime: Expires in 28135 seconds
Peer ike-id: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2023
Output bytes : 2030
Input packets: 4
Output packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Initiator, Message ID: 0
Local: 31.1.1.2:500, Remote: 11.1.1.1:500
Local identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations Total active tunnels: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <67108866 ESP:aes-cbc-256/sha1 a9d301b0 2936/ unlim - root 500 11.1.1.1 >67108866 ESP:aes-cbc-256/sha1 44ccf265 2936/ unlim - root 500 11.1.1.1
user@host> show security ipsec security-associations detail
ID: 67108866 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 31.1.1.2, Remote Gateway: 11.1.1.1
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x8608a29
Tunnel events:
Tue Jan 13 2015 12:57:48 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:57:48 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:57:48 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: a9d301b0, AUX-SPI: 0
Hard lifetime: Expires in 2933 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2311 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 44ccf265, AUX-SPI: 0
Hard lifetime: Expires in 2933 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2311 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 36 destinations, 36 routes (35 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
10.1.1.0/24 *[OSPF/10] 00:00:09, metric 16
> to 172.16.1.1 via st0.1
25.1.1.0/24 *[OSPF/10] 00:00:09, metric 26
> to 172.16.1.1 via st0.1
172.16.1.1/32 *[OSPF/10] 00:00:09, metric 15
> to 172.16.1.1 via st0.1
172.16.1.2/32 *[OSPF/10] 00:00:09, metric 25
> to 172.16.1.1 via st0.1
224.0.0.5/32 *[OSPF/10] 00:17:52, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.1 st0.1 Full 172.16.1.1 128 -
意义
该 show security ike security-associations 命令会列出所有活动的 IKE 第 1 阶段 SA。该 show security ipsec security-associations 命令将列出所有活动的 IKE 第 2 阶段 SA。中心显示两个活动隧道,每个分支一个。每个分支都显示一条通往中心的活动隧道。
如果未列出 IKE 第 1 阶段的 SA,则第 1 阶段建立存在问题。检查配置中的 IKE 策略参数和外部接口设置。第 1 阶段提议参数必须在中心辐射上匹配。
如果未列出 IKE 第 2 阶段的 SA,则第 2 阶段建立存在问题。检查配置中的 IKE 策略参数和外部接口设置。第 2 阶段提议参数必须在中心辐射上匹配。
该 show route protocol ospf 命令显示路由表中从 OSPF 协议获知的条目。该 show ospf neighbor 命令显示有关 OSPF 邻接方的信息。
验证合作伙伴之间的快捷方式隧道
目的
当 AutoVPN 中枢注意到流量通过其一个分支退出隧道并使用另一个分支进入隧道时,它可以充当快捷方式建议器。将在两个快捷方式伙伴之间建立新的 IPsec SA 或快捷方式。在每个伙伴上,到其伙伴后面网络的路由现在指向快捷方式隧道,而不是伙伴和建议器(集线器)之间的隧道。
操作
在操作模式下,在辐射上输入 show security ike security-associations、 show security ipsec security-associations、 show route protocol ospf和 show ospf neighbor 命令。
在集线器上输入以下命令:
user@host> show security ike security-associations node0: -------------------------------------------------------------------------- Index State Initiator cookie Responder cookie Mode Remote Address 10957048 UP 2d58d8fbc396762d 46145be580c68be0 IKEv2 31.1.1.2 10957049 UP fa05ee6d0f2cfb22 16f5ca836b118c0e IKEv2 21.1.1.2
user@host> show security ike security-associations detail
node0:
--------------------------------------------------------------------------
IKE peer 31.1.1.2, Index 10957048, Gateway Name: SUGGESTER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Suggester, Peer Capability: Partner
Suggester Shortcut Suggestions Statistics:
Suggestions sent : 1
Suggestions accepted: 1
Suggestions declined: 0
Role: Responder, State: UP
Initiator cookie: 2d58d8fbc396762d, Responder cookie: 46145be580c68be0
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 11.1.1.1:500, Remote: 31.1.1.2:500
Lifetime: Expires in 27781 seconds
Peer ike-id: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 260
Output bytes : 548
Input packets: 3
Output packets: 3
IPSec security associations: 0 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 11.1.1.1:500, Remote: 31.1.1.2:500
Local identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Remote identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
IKE peer 21.1.1.2, Index 10957049, Gateway Name: SUGGESTER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Suggester, Peer Capability: Partner
Suggester Shortcut Suggestions Statistics:
Suggestions sent : 1
Suggestions accepted: 1
Suggestions declined: 0
Role: Responder, State: UP
Initiator cookie: fa05ee6d0f2cfb22, Responder cookie: 16f5ca836b118c0e
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 11.1.1.1:500, Remote: 21.1.1.2:500
Lifetime: Expires in 27804 seconds
Peer ike-id: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 244
Output bytes : 548
Input packets: 3
Output packets: 3
IPSec security associations: 0 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 11.1.1.1:500, Remote: 21.1.1.2:500
Local identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Remote identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations node0: -------------------------------------------------------------------------- s Total active tunnels: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <201326593 ESP:aes-cbc-256/sha1 44ccf265 2584/ unlim - root 500 31.1.1.2 >201326593 ESP:aes-cbc-256/sha1 a9d301b0 2584/ unlim - root 500 31.1.1.2 <201326594 ESP:aes-cbc-256/sha1 98a2b155 2607/ unlim - root 500 21.1.1.2 >201326594 ESP:aes-cbc-256/sha1 de912bcd 2607/ unlim - root 500 21.1.1.2
user@host> show security ipsec security-associations detail
node0:
--------------------------------------------------------------------------
ID: 201326593 Virtual-system: root, VPN Name: SUGGESTER_VPN
Local Gateway: 11.1.1.1, Remote Gateway: 31.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x608a29
Tunnel events:
Tue Jan 13 2015 13:09:48 -0800: Bind-interface's address received. Information updated (1 times)
Tue Jan 13 2015 13:09:48 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Direction: inbound, SPI: 44ccf265, AUX-SPI: 0
Hard lifetime: Expires in 2578 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2001 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: a9d301b0, AUX-SPI: 0
Hard lifetime: Expires in 2578 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2001 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
ID: 201326594 Virtual-system: root, VPN Name: SUGGESTER_VPN
Local Gateway: 11.1.1.1, Remote Gateway: 21.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x608a29
Tunnel events:
Tue Jan 13 2015 13:09:48 -0800: Bind-interface's address received. Information updated (1 times)
Tue Jan 13 2015 13:09:48 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Direction: inbound, SPI: 98a2b155, AUX-SPI: 0
Hard lifetime: Expires in 2601 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2023 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: de912bcd, AUX-SPI: 0
Hard lifetime: Expires in 2601 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2023 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 28 destinations, 28 routes (27 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
25.1.1.0/24 *[OSPF/10] 00:04:49, metric 11
> to 172.16.1.2 via st0.1
36.1.1.0/24 *[OSPF/10] 00:04:49, metric 11
> to 172.16.1.3 via st0.1
172.16.1.2/32 *[OSPF/10] 00:04:49, metric 10
> to 172.16.1.2 via st0.1
172.16.1.3/32 *[OSPF/10] 00:04:49, metric 10
> to 172.16.1.3 via st0.1
224.0.0.5/32 *[OSPF/10] 00:05:10, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.3 st0.1 Full 172.16.1.3 128 - 172.16.1.2 st0.1 Full 172.16.1.2 128 -
在分支 1 上输入以下命令:
user@host> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 578872 UP fa05ee6d0f2cfb22 16f5ca836b118c0e IKEv2 11.1.1.1 578873 UP 895e4d9c7c5da7a4 17de7f18b45139b4 IKEv2 31.1.1.2
user@host> show security ike security-associations detail
node0:
--------------------------------------------------------------------------
IKE peer 11.1.1.1, Index 578872, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Partner, Peer Capability: Suggester
Partner Shortcut Suggestions Statistics:
Suggestions received: 1
Suggestions accepted: 1
Suggestions declined: 0
Role: Initiator, State: UP
Initiator cookie: fa05ee6d0f2cfb22, Responder cookie: 16f5ca836b118c0e
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 21.1.1.2:500, Remote: 11.1.1.1:500
Lifetime: Expires in 27906 seconds
Peer ike-id: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2495
Output bytes : 2274
Input packets: 6
Output packets: 7
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Initiator, Message ID: 0
Local: 21.1.1.2:500, Remote: 11.1.1.1:500
Local identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Flags: IKE SA is created
IKE peer 31.1.1.2, Index 578873, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Shortcut, Local Capability: Partner, Peer Capability: Partner
Role: Initiator, State: UP
Initiator cookie: 895e4d9c7c5da7a4, Responder cookie: 17de7f18b45139b4
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 21.1.1.2:500, Remote: 31.1.1.2:500
Lifetime: Expires in 28787 seconds
Peer ike-id: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 1855
Output bytes : 1990
Input packets: 2
Output packets: 2
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Initiator, Message ID: 0
Local: 21.1.1.2:500, Remote: 31.1.1.2:500
Local identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations node0: -------------------------------------------------------------------------- Total active tunnels: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <67108866 ESP:aes-cbc-256/sha1 de912bcd 2709/ unlim - root 500 11.1.1.1 >67108866 ESP:aes-cbc-256/sha1 98a2b155 2709/ unlim - root 500 11.1.1.1 <67108868 ESP:aes-cbc-256/sha1 75d0177b 3590/ unlim - root 500 31.1.1.2 >67108868 ESP:aes-cbc-256/sha1 e4919d73 3590/ unlim - root 500 31.1.1.2
user@host> show security ipsec security-associations detail
node0:
--------------------------------------------------------------------------
ID: 67108866 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 21.1.1.2, Remote Gateway: 11.1.1.1
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x8608a29
Tunnel events:
Tue Jan 13 2015 12:58:11 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:58:11 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:58:11 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: de912bcd, AUX-SPI: 0
Hard lifetime: Expires in 2701 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2079 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 98a2b155, AUX-SPI: 0
Hard lifetime: Expires in 2701 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2079 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
ID: 67108868 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 21.1.1.2, Remote Gateway: 31.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Auto Discovery VPN:
Type: Shortcut, Shortcut Role: Initiator
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x40608a29
Tunnel events:
Tue Jan 13 2015 13:12:52 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 13:12:52 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 13:12:52 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: 75d0177b, AUX-SPI: 0
Hard lifetime: Expires in 3582 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2959 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: e4919d73, AUX-SPI: 0
Hard lifetime: Expires in 3582 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2959 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 29 destinations, 29 routes (28 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
10.1.1.0/24 *[OSPF/10] 00:03:29, metric 16
> to 172.16.1.1 via st0.1
36.1.1.0/24 *[OSPF/10] 00:00:35, metric 16
> to 172.16.1.3 via st0.1
172.16.1.1/32 *[OSPF/10] 00:03:29, metric 15
> to 172.16.1.1 via st0.1
172.16.1.3/32 *[OSPF/10] 00:00:35, metric 15
> to 172.16.1.3 via st0.1
224.0.0.5/32 *[OSPF/10] 00:20:22, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.3 st0.1 Full 172.16.1.3 128 - 172.16.1.1 st0.1 Full 172.16.1.1 128
在分支 2 上输入以下命令:
user@host> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 2299162 UP 2d58d8fbc396762d 46145be580c68be0 IKEv2 11.1.1.1 2299163 UP 895e4d9c7c5da7a4 17de7f18b45139b4 IKEv2 21.1.1.2
user@host> show security ike security-associations detail
IKE peer 11.1.1.1, Index 2299162, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Partner, Peer Capability: Suggester
Partner Shortcut Suggestions Statistics:
Suggestions received: 1
Suggestions accepted: 1
Suggestions declined: 0
Role: Initiator, State: UP
Initiator cookie: 2d58d8fbc396762d, Responder cookie: 46145be580c68be0
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 31.1.1.2:500, Remote: 11.1.1.1:500
Lifetime: Expires in 27835 seconds
Peer ike-id: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2571
Output bytes : 2290
Input packets: 7
Output packets: 7
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Initiator, Message ID: 0
Local: 31.1.1.2:500, Remote: 11.1.1.1:500
Local identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Flags: IKE SA is created
IKE peer 21.1.1.2, Index 2299163, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Shortcut, Local Capability: Partner, Peer Capability: Partner
Role: Responder, State: UP
Initiator cookie: 895e4d9c7c5da7a4, Responder cookie: 17de7f18b45139b4
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 31.1.1.2:500, Remote: 21.1.1.2:500
Lifetime: Expires in 28739 seconds
Peer ike-id: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2066
Output bytes : 1931
Input packets: 3
Output packets: 3
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 31.1.1.2:500, Remote: 21.1.1.2:500
Local identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations Total active tunnels: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <67108866 ESP:aes-cbc-256/sha1 a9d301b0 2638/ unlim - root 500 11.1.1.1 >67108866 ESP:aes-cbc-256/sha1 44ccf265 2638/ unlim - root 500 11.1.1.1 <67108868 ESP:aes-cbc-256/sha1 e4919d73 3542/ unlim - root 500 21.1.1.2 >67108868 ESP:aes-cbc-256/sha1 75d0177b 3542/ unlim - root 500 21.1.1.2
user@host> show security ipsec security-associations detail
ID: 67108866 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 31.1.1.2, Remote Gateway: 11.1.1.1
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x8608a29
Tunnel events:
Tue Jan 13 2015 12:57:48 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:57:48 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:57:48 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: a9d301b0, AUX-SPI: 0
Hard lifetime: Expires in 2632 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2010 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 44ccf265, AUX-SPI: 0
Hard lifetime: Expires in 2632 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2010 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
ID: 67108868 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 31.1.1.2, Remote Gateway: 21.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Auto Discovery VPN:
Type: Shortcut, Shortcut Role: Responder
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x40608aa9
Tunnel events:
Tue Jan 13 2015 13:12:52 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 13:12:52 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 13:12:52 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: e4919d73, AUX-SPI: 0
Hard lifetime: Expires in 3536 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2958 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 75d0177b, AUX-SPI: 0
Hard lifetime: Expires in 3536 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2958 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 36 destinations, 36 routes (35 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
10.1.1.0/24 *[OSPF/10] 00:03:55, metric 16
> to 172.16.1.1 via st0.1
25.1.1.0/24 *[OSPF/10] 00:01:02, metric 16
> to 172.16.1.2 via st0.1
172.16.1.1/32 *[OSPF/10] 00:03:55, metric 15
> to 172.16.1.1 via st0.1
172.16.1.2/32 *[OSPF/10] 00:01:02, metric 15
> to 172.16.1.2 via st0.1
224.0.0.5/32 *[OSPF/10] 00:21:38, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.2 st0.1 Full 172.16.1.2 128 - 172.16.1.1 st0.1 Full 172.16.1.1 128 -
意义
该 show security ike security-associations 命令会列出所有活动的 IKE 第 1 阶段 SA。该 show security ipsec security-associations 命令将列出所有活动的 IKE 第 2 阶段 SA。中心仍显示两个活动隧道,每个分支一个。每个分支显示两个活动隧道,一个到中心,一个到其快捷方式伙伴。
该 show route protocol ospf 命令显示向合作伙伴和中心添加的路由。
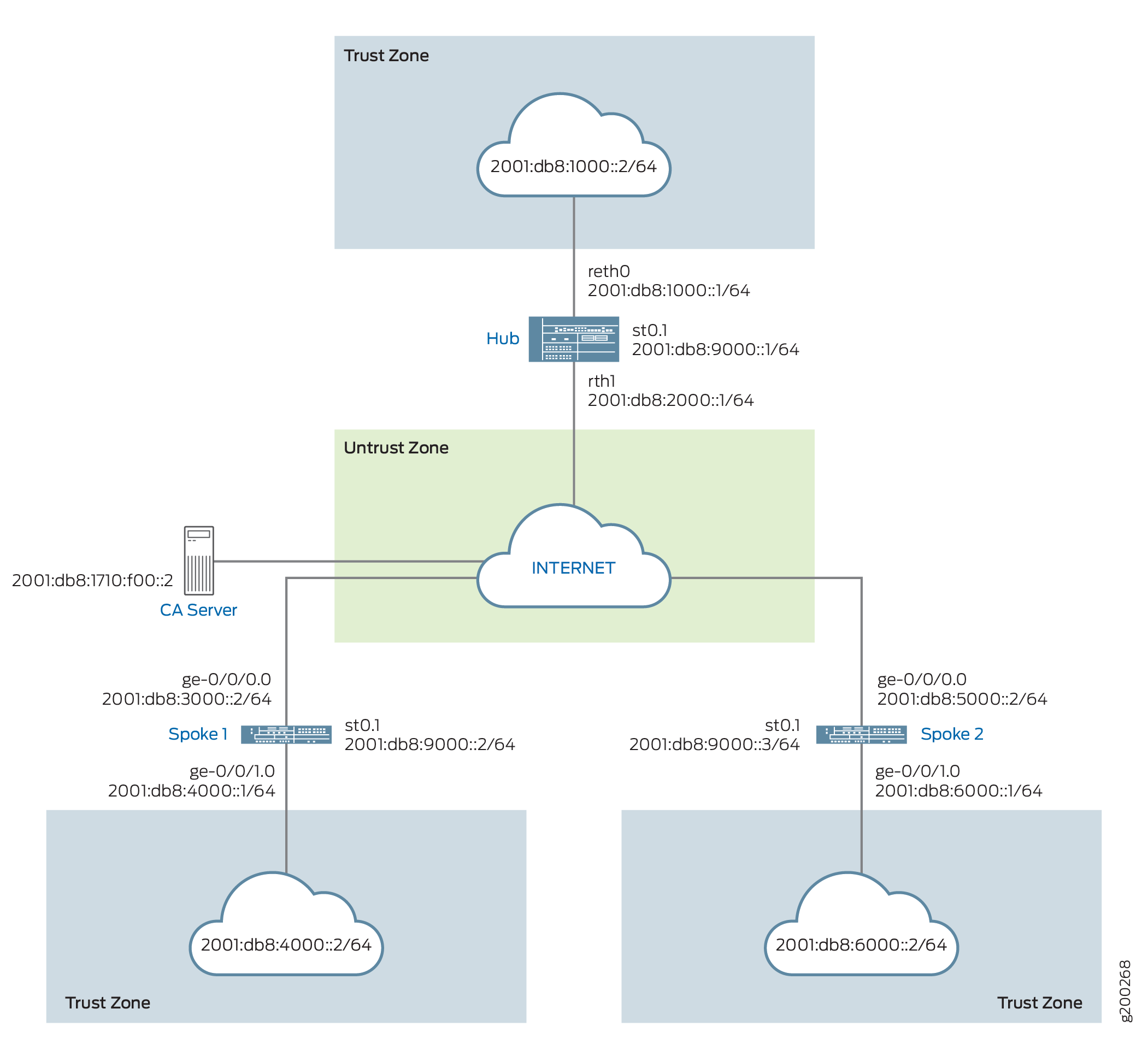
示例:使用 OSPFv3 配置 ADVPN 以实现 IPv6 流量
此示例说明如何配置 ADVPN 中心和两个分支以创建快捷方式隧道并更改主机的路由拓扑以到达另一端,而无需通过中心发送流量。此示例使用 OSPFv3 配置适用于 IPv6 的 ADVPN 环境,以通过 VPN 隧道转发数据包。
要求
此示例使用以下硬件和软件组件:
-
三个受支持的 SRX 系列防火墙作为 ADVPN 中心辐射型防火墙
-
Junos OS 版本 18.1R1 或更高版本(如果您的防火墙运行 kmd 进程)。
-
Junos OS 24.2R1 或更高版本(如果您的防火墙运行 iked 进程)。
准备工作:
-
提交本地证书请求时,获取证书颁发机构 (CA) 的地址及其所需的信息(例如质询密码)。
您应该熟悉用于通过 VPN 隧道转发数据包的动态路由协议。
概述
此示例显示了 ADVPN 中心的配置以及两个分支的后续配置。
在此示例中,第一步是使用简单证书注册协议 (SCEP) 在每个设备中注册数字证书。分支的证书在主题字段中包含组织单位 (OU) 值“SLT”;中心配置了组 IKE ID,以匹配 OU 字段中的值“SLT”。
分支与中心建立 IPsec VPN 连接,使它们能够相互通信以及访问中心上的资源。在 ADVPN 中心和所有分支上配置的第 1 阶段和第 2 阶段 IKE 隧道选项必须具有相同的值。 表 4 显示了此示例中使用的选项。
|
选项 |
value |
|---|---|
|
IKE 提案: |
|
|
身份验证方法 |
RSA 数字证书 |
|
Diffie-Hellman (DH) 组 |
19 |
|
身份验证算法 |
SHA-384 |
|
加密算法 |
AES 256 全血细胞计数 |
|
IKE 策略: |
|
|
模式 |
主要 |
|
IPsec 提议: |
|
|
协议 |
ESP |
|
生命周期秒数 |
3000 |
|
加密算法 |
AES 256 GCM |
|
IPsec 策略: |
|
|
完全向前保密 (PFS) 组 |
19 |
在所有设备上配置相同的证书颁发机构 (CA)。
表 5 显示在中心和所有辐射上配置的选项。
|
选项 |
枢纽 |
所有辐条 |
|---|---|---|
|
IKE 网关: |
||
|
远程 IP 地址 |
动态 |
2001:db8:2000::1 |
|
远程 IKE ID |
分支证书上的可分辨名称 (DN),组织单位 (OU) 字段中的字符串 |
集线器证书上的 DN |
|
本地 IKE ID |
集线器证书上的 DN |
分支证书上的 DN |
|
外部接口 |
RETH1 |
辐条1:ge-0/0/0.0 辐条2:ge-0/0/0.0 |
|
VPN: |
||
|
绑定接口 |
st0.1 |
st0.1 |
|
建立隧道 |
(未配置) |
立即建立隧道 |
表 6 显示了每个分支上不同的配置选项。
|
选项 |
辐条 1 |
辐条 2 |
|---|---|---|
|
ST0.1 接口 |
2001:db8:9000::2/64 |
2001:db8:9000::3/64 |
|
与内部网络的接口 |
(ge-0/0/1.0) 2001:db8:4000::1/64 |
(ge-0/0/1.0) 2001:db8:6000::1/64 |
|
互联网接口 |
(ge-0/0/0.0) 2001:db8:3000::2/64 |
(ge-0/0/0.0) 2001:db8:5000::2/64 |
所有设备的路由信息都通过 VPN 隧道进行交换。
在此示例中,允许所有流量的默认安全策略用于所有设备。应为生产环境配置更严格的安全策略。请参阅 安全策略概述。
配置
若要配置 ADVPN,请执行以下任务:
第一部分介绍如何在中心辐射设备上使用简单证书注册协议 (SCEP) 联机获取 CA 和本地证书。
使用 SCEP 注册设备证书
分步过程
若要在中心使用 SCEP 注册数字证书,请执行以下操作:
-
配置 CA。
[edit] user@host# set security pki ca-profile ca-profile1 ca-identity ca-profile1 user@host# set security pki ca-profile ca-profile1 enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set security pki ca-profile ca-profile1 revocation-check disable user@host# commit
-
注册 CA 证书。
user@host> request security pki ca-certificate enroll ca-profile ca-profile1
在提示符下键入 yes 以加载 CA 证书。
-
生成密钥对。
user@host> request security pki generate-key-pair certificate-id Local1
-
注册本地证书。
user@host> request security pki local-certificate enroll ca-profile ca-profile1 certificate-id Local1 domain-name example.net email hub@example.net ip-address 10.1.1.1 subject DC=example.net,CN=hub,OU=SLT,O=example,L=Bengaluru,ST=KA,C=IN challenge-password <password>
-
验证本地证书。
user@host> show security pki local-certificate detail Certificate identifier: Local1 Certificate version: 3 Serial number: 40a6d5f300000000258d Issuer: Common name: CASERVER1, Domain component: net, Domain component: internal Subject: Organization: example, Organizational unit: SLT, Country: IN, State: KA, Locality: Bengaluru, Common name: hub, Domain component: example.net Subject string: C=IN, DC=example.net, ST=KA, L=Bengaluru, O=example, OU=SLT, CN=hub Alternate subject: "hub@example.net", example.net, 10.1.1.1 Validity: Not before: 11- 6-2012 09:39 Not after: 11- 6-2013 09:49 Public key algorithm: rsaEncryption(1024 bits) 30:81:89:02:81:81:00:c9:c9:cc:30:b6:7a:86:12:89:b5:18:b3:76 01:2d:cc:65:a8:a8:42:78:cd:d0:9a:a2:c0:aa:c4:bd:da:af:88:f3 2a:78:1f:0a:58:e6:11:2c:81:8f:0e:7c:de:86:fc:48:4c:28:5b:8b 34:91:ff:2e:91:e7:b5:bd:79:12:de:39:46:d9:fb:5c:91:41:d1:da 90:f5:09:00:9b:90:07:9d:50:92:7d:ff:fb:3f:3c:bc:34:e7:e3:c8 ea:cb:99:18:b4:b6:1d:a8:99:d3:36:b9:1b:36:ef:3e:a1:fd:48:82 6a:da:22:07:da:e0:d2:55:ef:57:be:09:7a:0e:17:02:03:01:00:01 Signature algorithm: sha1WithRSAEncryption Distribution CRL: http://ca-server1/CertEnroll/CASERVER1.crl file://\\ca-server1\CertEnroll\CASERVER1.crl Fingerprint: e1:f7:a1:a6:1e:c3:97:69:a5:07:9b:09:14:1a:c7:ae:09:f1:f6:35 (sha1) a0:02:fa:8d:5c:63:e5:6d:f7:f4:78:56:ac:4e:b2:c4 (md5) Auto-re-enrollment: Status: Disabled Next trigger time: Timer not started
分步过程
要使用分支 1 上的 SCEP 注册数字证书,请执行以下操作:
-
配置 CA。
[edit] user@host# set security pki ca-profile ca-profile1 ca-identity ca-profile1 user@host# set security pki ca-profile ca-profile1 enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set security pki ca-profile ca-profile1 revocation-check disable user@host# commit
-
注册 CA 证书。
user@host> request security pki ca-certificate enroll ca-profile ca-profile1
在提示符下键入 yes 以加载 CA 证书。
-
生成密钥对。
user@host> request security pki generate-key-pair certificate-id Local1
-
注册本地证书。
user@host> request security pki local-certificate enroll ca-profile ca-profile1 certificate-id Local1 domain-name example.net email spoke1@example.net ip-address 10.2.2.1 subject DC=example.net,CN=spoke1,OU=SLT,O=example,L=Mysore,ST=KA,C=IN challenge-password <password>
-
验证本地证书。
user@host> show security pki local-certificate detail Certificate identifier: Local1 Certificate version: 3 Serial number: 40a7975f00000000258e Issuer: Common name: CASERVER1, Domain component: net, Domain component: internal Subject: Organization: example, Organizational unit: SLT, Country: IN, State: KA, Locality: Mysore, Common name: spoke1, Domain component: example.net Subject string: C=IN, DC=example.net, ST=KA, L=Mysore, O=example, OU=SLT, CN=spoke1 Alternate subject: "spoke1@example.net", example.net, 10.2.2.1 Validity: Not before: 11- 6-2012 09:40 Not after: 11- 6-2013 09:50 Public key algorithm: rsaEncryption(1024 bits) 30:81:89:02:81:81:00:d8:45:09:77:cd:36:9a:6f:58:44:18:91:db b0:c7:8a:ee:c8:d7:a6:d2:e2:e7:20:46:2b:26:1a:92:e2:4e:8a:ce c9:25:d9:74:a2:81:ad:ea:e0:38:a0:2f:2d:ab:a6:58:ac:88:35:f4 90:01:08:33:33:75:2c:44:26:f8:25:18:97:96:e4:28:de:3b:35:f2 4a:f5:92:b7:57:ae:73:4f:8e:56:71:ab:81:54:1d:75:88:77:13:64 1b:6b:01:96:15:0a:1c:54:e3:db:f8:ec:ec:27:5b:86:39:c1:09:a1 e4:24:1a:19:0d:14:2c:4b:94:a4:04:91:3f:cb:ef:02:03:01:00:01 Signature algorithm: sha1WithRSAEncryption Distribution CRL: http://ca-server1/CertEnroll/CASERVER1.crl file://\\ca-server1\CertEnroll\CASERVER1.crl Fingerprint: b6:24:2a:0e:96:5d:8c:4a:11:f3:5a:24:89:7c:df:ea:d5:c0:80:56 (sha1) 31:58:7f:15:bb:d4:66:b8:76:1a:42:4a:8a:16:b3:a9 (md5) Auto-re-enrollment: Status: Disabled Next trigger time: Timer not started主题字段中显示的组织单位 (OU) 为
SLT。中心上的 IKE 配置包括ou=SLT用于标识分支。
分步过程
要使用分支 2 上的 SCEP 注册数字证书,请执行以下操作:
-
配置 CA。
[edit] user@host# set security pki ca-profile ca-profile1 ca-identity ca-profile1 user@host# set security pki ca-profile ca-profile1 enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set security pki ca-profile ca-profile1 revocation-check disable user@host# commit
-
注册 CA 证书。
user@host> request security pki ca-certificate enroll ca-profile ca-profile1
在提示符下键入 yes 以加载 CA 证书。
-
生成密钥对。
user@host> request security pki generate-key-pair certificate-id Local1
-
注册本地证书。
user@host> request security pki local-certificate enroll ca-profile ca-profile1 certificate-id Local1 domain-name example.net email spoke2@example.net ip-address 10.3.3.1 subject DC=example.net,CN=spoke2,OU=SLT,O=example,L=Tumkur,ST=KA,C=IN challenge-password <password>
-
验证本地证书。
user@host> show security pki local-certificate detail Certificate identifier: Local1 Certificate version: 3 Serial number: 40bb71d400000000258f Issuer: Common name: CASERVER1, Domain component: net, Domain component: internal Subject: Organization: example, Organizational unit: SLT, Country: IN, State: KA, Locality: Tumkur, Common name: spoke2, Domain component: example.net Subject string: C=IN, DC=example.net, ST=KA, L=Tumkur, O=example, OU=SLT, CN=spoke2 Alternate subject: "spoke2@example.net", example.net, 10.3.3.1 Validity: Not before: 11- 6-2012 10:02 Not after: 11- 6-2013 10:12 Public key algorithm: rsaEncryption(1024 bits) 30:81:89:02:81:81:00:b6:2e:e2:da:e6:ac:57:e4:5d:ff:de:f6:89 27:d6:3e:1b:4a:3f:b2:2d:b3:d3:61:ed:ed:6a:07:d9:8a:d2:24:03 77:1a:fe:84:e1:12:8a:2d:63:6e:bf:02:6b:15:96:5a:4f:37:a0:46 44:09:96:c0:fd:bb:ab:79:2c:5d:92:bd:31:f0:3b:29:51:ce:89:8e 7c:2b:02:d0:14:5b:0a:a9:02:93:21:ea:f9:fc:4a:e7:08:bc:b1:6d 7c:f8:3e:53:58:8e:f1:86:13:fe:78:b5:df:0b:8e:53:00:4a:46:11 58:4a:38:e9:82:43:d8:25:47:7d:ef:18:f0:ef:a7:02:03:01:00:01 Signature algorithm: sha1WithRSAEncryption Distribution CRL: http://ca-server1/CertEnroll/CASERVER1.crl file://\\ca-server1\CertEnroll\CASERVER1.crl Fingerprint: 1a:6d:77:ac:fd:94:68:ce:cf:8a:85:f0:39:fc:e0:6b:fd:fe:b8:66 (sha1) 00:b1:32:5f:7b:24:9c:e5:02:e6:72:75:9e:a5:f4:77 (md5) Auto-re-enrollment: Status: Disabled Next trigger time: Timer not started主题字段中显示的组织单位 (OU) 为
SLT。中心上的 IKE 配置包括ou=SLT用于标识分支。
配置集线器
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到 [edit] 层级的 CLI 中,然后从配置模式进入 commit 。
set chassis cluster reth-count 2 set chassis cluster node 0 set chassis cluster node 1 set chassis cluster redundancy-group 0 node 0 priority 254 set chassis cluster redundancy-group 0 node 1 priority 1 set chassis cluster redundancy-group 1 node 0 priority 254 set chassis cluster redundancy-group 1 node 1 priority 1 set security pki ca-profile ROOT-CA ca-identity ROOT-CA set security pki ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll set security pki ca-profile ROOT-CA enrollment retry 5 set security pki ca-profile ROOT-CA enrollment retry-interval 0 set security pki ca-profile ROOT-CA revocation-check disable set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group19 set security ike proposal IKE_PROP authentication-algorithm sha-384 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 6000 set security ike policy IKE_POL mode main set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate HUB set security ike gateway IKE_GWA_1 ike-policy IKE_POL set security ike gateway IKE_GWA_1 dynamic distinguished-name wildcard OU=SLT set security ike gateway IKE_GWA_1 dynamic ike-user-type group-ike-id set security ike gateway IKE_GWA_1 dead-peer-detection always-send set security ike gateway IKE_GWA_1 dead-peer-detection interval 10 set security ike gateway IKE_GWA_1 dead-peer-detection threshold 3 set security ike gateway IKE_GWA_1 local-identity distinguished-name set security ike gateway IKE_GWA_1 external-interface reth1 set security ike gateway IKE_GWA_1 advpn partner disable set security ike gateway IKE_GWA_1 version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal IPSEC_PROP lifetime-seconds 3000 set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group19 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPNA_1 bind-interface st0.1 set security ipsec vpn IPSEC_VPNA_1 ike gateway IKE_GWA_1 set security ipsec vpn IPSEC_VPNA_1 ike ipsec-policy IPSEC_POL set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols ospf3 set security zones security-zone untrust interfaces reth1.0 set security zones security-zone untrust interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols ospf3 set security zones security-zone trust interfaces reth0.0 set interfaces ge-0/0/0 gigether-options redundant-parent reth1 set interfaces ge-0/0/1 gigether-options redundant-parent reth0 set interfaces ge-7/0/0 gigether-options redundant-parent reth1 set interfaces ge-7/0/1 gigether-options redundant-parent reth0 set interfaces reth0 redundant-ether-options redundancy-group 1 set interfaces reth0 unit 0 family inet set interfaces reth0 unit 0 family inet6 address 2001:db8:1000::1/64 set interfaces reth1 redundant-ether-options redundancy-group 1 set interfaces reth1 unit 0 family inet set interfaces reth1 unit 0 family inet6 address 2001:db8:2000::1/64 set interfaces st0 unit 1 multipoint set interfaces st0 unit 1 family inet6 address 2001:db8:9000::1/64 set routing-options rib inet6.0 static route 2001:db8:3000::0/64 next-hop 2001:db8:2000::2 set routing-options rib inet6.0 static route 2001:db8:5000::0/64 next-hop 2001:db8:2000::2 set protocols ospf3 area 0.0.0.0 interface reth0.0 set protocols ospf3 area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf3 area 0.0.0.0 interface st0.1 dynamic-neighbors
分步过程
下面的示例要求您在各个配置层级中进行导航。有关操作说明,请参阅在配置模式下使用 CLI 编辑器。
要配置集线器,请执行以下操作:
-
配置接口。
[edit interfaces] user@host# set ge-0/0/0 gigether-options redundant-parent reth1 user@host# set ge-0/0/1 gigether-options redundant-parent reth0 user@host# set ge-7/0/0 gigether-options redundant-parent reth1 user@host# set ge-7/0/1 gigether-options redundant-parent reth0 user@host# set reth0 redundant-ether-options redundancy-group 1 user@host# set reth0 unit 0 family inet user@host# set reth0 unit 0 family inet6 address 2001:db8:1000::1/64 user@host# set reth1 redundant-ether-options redundancy-group 1 user@host# set reth1 unit 0 family inet user@host# set reth1 unit 0 family inet6 address 2001:db8:2000::1/64 user@host# set st0 unit 1 multipoint user@host# set st0 unit 1 family inet6 address 2001:db8:9000::1/64
-
配置路由协议。
[edit protocols ospf3] user@host# set ospf3 area 0.0.0.0 interface reth0.0 user@host# set ospf3 area 0.0.0.0 interface st0.1 interface-type p2mp user@host# set ospf3 area 0.0.0.0 interface st0.1 dynamic-neighbors [edit routing-options] user@host# set rib inet6.0 static route 2001:db8:3000::0/64 next-hop 2001:db8:2000::2 user@host# set rib inet6.0 static route 2001:db8:5000::0/64 next-hop 2001:db8:2000::2
-
配置第 1 阶段选项。
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group19 user@host# set authentication-algorithm sha-384 user@host# set encryption-algorithm aes-256-cbc user@host# set lifetime-seconds 6000 [edit security ike policy IKE_POL] user@host# set mode main user@host# set proposals IKE_PROP user@host# set certificate local-certificate HUB [edit security ike gateway IKE_GWA_1] user@host# set ike-policy IKE_POL user@host# set dynamic distinguished-name wildcard OU=SLT user@host# set ike-user-type group-ike-id user@host# set dead-peer-detection always-send user@host# set dead-peer-detection interval 10 user@host# set dead-peer-detection threshold 3 user@host# set local-identity distinguished-name user@host# set external-interface reth1 user@host# set version v2-only
-
配置第 2 阶段选项。
[edit security ipsec proposal IPSEC_PROP] user@host# set protocol esp user@host# set encryption-algorithm aes-256-gcm user@host# set lifetime-seconds 3000 [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group19 user@host# set proposals IPSEC_PROP [edit security ipsec vpn IPSEC_VPNA_1] user@host# set bind-interface st0.1 user@host# set ike gateway IKE_GWA_1 user@host# set ike ipsec-policy IPSEC_POL
-
配置区域。
[edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces reth1.0 user@host# set interfaces st0.1 [edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces reth0.0
-
配置默认安全策略。
[edit security policies] user@host# set default-policy permit-all
-
配置 CA 配置文件。
[edit security pki] user@host# set ca-profile ROOT-CA ca-identity ROOT-CA user@host# set ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set ca-profile ROOT-CA enrollment retry 5 user@host# set ca-profile ROOT-CA enrollment retry-interval 0 user@host# set pki ca-profile ROOT-CA revocation-check disable
-
配置机箱群集
[edit chassis cluster] set reth-count 2 set node 0 set node 1 set redundancy-group 0 node 0 priority 254 set redundancy-group 0 node 1 priority 1 set redundancy-group 1 node 0 priority 254 set redundancy-group 1 node 1 priority 1
结果
在配置模式下,输入 show interfaces、 show protocols、 show routing-optionsshow security ike、 show security ipsec、 show security zones、 和show security policiesshow security pki show chassis cluster命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
[edit]
user@host# show interfaces
ge-0/0/0 {
gigether-options {
redundant-parent reth1;
}
}
ge-0/0/1 {
gigether-options {
redundant-parent reth0;
}
}
reth0 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet;
family inet6 {
address 2001:db8:1000::1/64;
}
}
}
reth1 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet;
family inet6 {
address 2001:db8:2000::1/64;
}
}
}
st0 {
unit 1 {
multipoint;
family inet6 {
address 2001:db8:9000::1/64 {
primary;
}
}
}
}
[edit]
user@host# show protocols
ospf3 {
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
demand-circuit;
dynamic-neighbors;
}
interface ge-0/0/1.0;
interface reth0.0;
}
}
[edit]
user@host# show routing-options
rib inet6.0 {
static {
route 2001:db8:3000::/64 next-hop 2001:db8:2000::2;
route 2001:db8:5000::/64 next-hop 2001:db8:2000::2;
}
}
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group19;
authentication-algorithm sha-384;
encryption-algorithm aes-256-cbc;
lifetime-seconds 6000;
}
policy IKE_POL {
mode main;
proposals IKE_PROP;
certificate {
local-certificate HUB;
}
}
gateway IKE_GWA_1 {
ike-policy IKE_POL;
dynamic {
distinguished-name {
wildcard OU=SLT;
}
ike-user-type group-ike-id;
}
dead-peer-detection {
always-send;
interval 10;
threshold 3;
}
local-identity distinguished-name;
external-interface reth1;
advpn {
partner {
disable;
}
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3000;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group19;
}
proposals IPSEC_PROP;
}
vpn IPSEC_VPNA_1 {
bind-interface st0.1;
ike {
gateway IKE_GWA_1;
ipsec-policy IPSEC_POL;
}
}
[edit]
user@host# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
st0.1;
reth1.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
reth0.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
[edit]
user@host# show security pki
ca-profile ROOT-CA {
ca-identity ROOT-CA;
enrollment {
url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll;
retry 5;
retry-interval 0;
}
revocation-check {
disable;
}
}
如果完成设备配置,请从配置模式输入 commit。
配置分支 1
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到 [edit] 层级的 CLI 中,然后从配置模式进入 commit 。
set security pki ca-profile ROOT-CA ca-identity ROOT-CA set security pki ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll set security pki ca-profile ROOT-CA enrollment retry 5 set security pki ca-profile ROOT-CA enrollment retry-interval 0 set security pki ca-profile ROOT-CA revocation-check disable set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group19 set security ike proposal IKE_PROP authentication-algorithm sha-384 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 6000 set security ike policy IKE_POL mode main set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate SPOKE1 set security ike gateway IKE_GW_SPOKE_1 ike-policy IKE_POL set security ike gateway IKE_GW_SPOKE_1 address 2001:db8:2000::1 set security ike gateway IKE_GW_SPOKE_1 dead-peer-detection always-send set security ike gateway IKE_GW_SPOKE_1 dead-peer-detection interval 10 set security ike gateway IKE_GW_SPOKE_1 dead-peer-detection threshold 3 set security ike gateway IKE_GW_SPOKE_1 local-identity distinguished-name set security ike gateway IKE_GW_SPOKE_1 remote-identity distinguished-name container OU=SLT set security ike gateway IKE_GW_SPOKE_1 external-interface ge-0/0/0.0 set security ike gateway IKE_GW_SPOKE_1 advpn suggester disable set security ike gateway IKE_GW_SPOKE_1 version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal IPSEC_PROP lifetime-seconds 3000 set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group19 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN_SPOKE_1 bind-interface st0.1 set security ipsec vpn IPSEC_VPN_SPOKE_1 ike gateway IKE_GW_SPOKE_1 set security ipsec vpn IPSEC_VPN_SPOKE_1 ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN_SPOKE_1 establish-tunnels immediately set security policies default-policy permit-all set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols ospf3 set security zones security-zone trust interfaces ge-0/0/1.0 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols ospf3 set security zones security-zone untrust interfaces st0.1 set security zones security-zone untrust interfaces ge-0/0/0.0 set interfaces ge-0/0/0 unit 0 family inet6 address 2001:db8:3000::2/64 set interfaces ge-0/0/1 unit 0 family inet6 address 2001:db8:4000::1/64 set interfaces st0 unit 1 multipoint set interfaces st0 unit 1 family inet6 address 2001:db8:9000::2/64 set routing-options rib inet6.0 static route 2001:db8:2000::0/64 next-hop 2001:db8:3000::1 set protocols ospf3 area 0.0.0.0 interface ge-0/0/1.0 set protocols ospf3 area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf3 area 0.0.0.0 interface st0.1 dynamic-neighbors
分步过程
下面的示例要求您在各个配置层级中进行导航。有关操作说明,请参阅在配置模式下使用 CLI 编辑器。
要配置分支 1:
-
配置接口。
[edit interfaces] user@host# set ge-0/0/0 unit 0 family inet6 address 2001:db8:3000::2/64 user@host# set ge-0/0/1 unit 0 family inet6 address 2001:db8:4000::1/64 user@host# set st0 unit 1 multipoint user@host# set st0 unit 1 family inet6 address 2001:db8:9000::2/64
-
配置路由协议。
[edit protocols ospf3] set area 0.0.0.0 interface ge-0/0/1.0 set area 0.0.0.0 interface st0.1 interface-type p2mp set area 0.0.0.0 interface st0.1 dynamic-neighbors [edit routing-options] user@host# set rib inet6.0 static route 2001:db8:2000::/64 next-hop 2001:db8:3000::1
-
配置第 1 阶段选项。
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group19 user@host# set authentication-algorithm sha-384 user@host# set encryption-algorithm aes-256-cbc user@host# set lifetime-seconds 6000 [edit security ike policy IKE_POL] user@host# set mode main user@host# set proposals IKE_PROP user@host# set certificate local-certificate SPOKE1 [edit security ike gateway IKE_GW_SPOKE_1] user@host# set ike-policy IKE_POL user@host# set address 2001:db8:2000::1 user@host# set dead-peer-detection always-send user@host# set dead-peer-detection interval 10 user@host# set dead-peer-detection threshold 3 user@host# set local-identity distinguished-name user@host# set remote-identity distinguished-name container OU=SLT user@host# set external-interface ge-0/0/0.0 user@host# set advpn suggester disable user@host# set version v2-only
-
配置第 2 阶段选项。
[edit security ipsec proposal IPSEC_PROPl] user@host# set protocol esp user@host# set encryption-algorithm aes-256-gcm user@host# set lifetime-seconds 3000 [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group19 user@host# set proposals IPSEC_PROP [edit security ipsec vpn IPSEC_VPN_SPOKE_1] user@host# set bind-interface st0.1 user@host# set ike gateway IKE_GW_SPOKE_1 user@host# set ike ipsec-policy IPSEC_POL user@host# set establish-tunnels immediately
-
配置区域。
[edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces st0.1 user@host# set interfaces ge-0/0/0.0 [edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces ge-0/0/1.0
-
配置默认安全策略。
[edit security policies] user@host# set default-policy permit-all
-
配置 CA 配置文件。
[edit security pki] user@host# set ca-profile ROOT-CA ca-identity ROOT-CA user@host# set ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set ca-profile ROOT-CA enrollment retry 5 user@host# set ca-profile ROOT-CA enrollment retry-interval 0 user@host# set ca-profile ROOT-CA revocation-check disable
结果
在配置模式下,输入 show interfaces、 show protocols、 show routing-optionsshow security ike、 show security ipsec、 show security zones、 和show security policiesshow security pki命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
[edit]
user@host# show interfaces
ge-0/0/0 {
unit 0 {
family inet6 {
address 2001:db8:3000::2/64;
}
}
}
ge-0/0/1 {
unit 0 {
family inet6 {
address 2001:db8:4000::1/64;
}
}
}
st0 {
unit 1 {
multipoint;
family inet6 {
address 2001:db8:9000::2/64;
}
}
}
[edit]
user@host# show protocols
ospf3 {
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
dynamic-neighbors;
}
interface ge-0/0/1.0;
}
}
[edit]
user@host# show routing-options
rib inet6.0 {
static {
route 2001:db8:2000::/64 next-hop [ 2001:db8:3000::1 2001:db8:5000::1 ];
}
}
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group19;
authentication-algorithm sha-384;
encryption-algorithm aes-256-cbc;
lifetime-seconds 6000;
}
policy IKE_POL {
mode main;
proposals IKE_PROP;
certificate {
local-certificate SPOKE1;
}
}
gateway IKE_GW_SPOKE_1 {
ike-policy IKE_POL;
address 2001:db8:2000::1;
dead-peer-detection {
always-send;
interval 10;
threshold 3;
}
local-identity distinguished-name;
remote-identity distinguished-name container OU=SLT;
external-interface ge-0/0/0.0;
advpn {
suggester {
disable;
}
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3000;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group19;
}
proposals IPSEC_PROP;
}
vpn IPSEC_VPN_SPOKE_1 {
bind-interface st0.1;
ike {
gateway IKE_GW_SPOKE_1;
ipsec-policy IPSEC_POL;
}
establish-tunnels immediately;
}
[edit]
user@host# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
st0.1;
ge-0/0/0.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
ge-0/0/1.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
[edit]
user@host# show security pki
ca-profile ROOT-CA {
ca-identity ROOT-CA;
enrollment {
url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll;
retry 5;
retry-interval 0;
}
revocation-check {
disable;
}
}
如果完成设备配置,请从配置模式输入 commit。
配置分支 2
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到 [edit] 层级的 CLI 中,然后从配置模式进入 commit 。
set security pki ca-profile ROOT-CA ca-identity ROOT-CA set security pki ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll set security pki ca-profile ROOT-CA enrollment retry 5 set security pki ca-profile ROOT-CA enrollment retry-interval 0 set security pki ca-profile ROOT-CA revocation-check disable set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group19 set security ike proposal IKE_PROP authentication-algorithm sha-384 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 6000 set security ike policy IKE_POL mode main set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate SPOKE2 set security ike gateway IKE_GW_SPOKE_2 ike-policy IKE_POL set security ike gateway IKE_GW_SPOKE_2 address 2001:db8:2000::1 set security ike gateway IKE_GW_SPOKE_2 dead-peer-detection always-send set security ike gateway IKE_GW_SPOKE_2 dead-peer-detection interval 10 set security ike gateway IKE_GW_SPOKE_2 dead-peer-detection threshold 3 set security ike gateway IKE_GW_SPOKE_2 local-identity distinguished-name set security ike gateway IKE_GW_SPOKE_2 remote-identity distinguished-name container OU=SLT set security ike gateway IKE_GW_SPOKE_2 external-interface ge-0/0/0.0 set security ike gateway IKE_GW_SPOKE_2 advpn suggester disable set security ike gateway IKE_GW_SPOKE_2 version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal IPSEC_PROP lifetime-seconds 3000 set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group19 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN_SPOKE_2 bind-interface st0.1 set security ipsec vpn IPSEC_VPN_SPOKE_2 ike gateway IKE_GW_SPOKE_2 set security ipsec vpn IPSEC_VPN_SPOKE_2 ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN_SPOKE_2 establish-tunnels immediately set security policies default-policy permit-all set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols ospf3 set security zones security-zone trust interfaces ge-0/0/1.0 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols ospf3 set security zones security-zone untrust interfaces st0.1 set security zones security-zone untrust interfaces ge-0/0/0.0 set interfaces ge-0/0/0 unit 0 family inet6 address 2001:db8:5000::2/64 set interfaces ge-0/0/1 unit 0 family inet6 address 2001:db8:6000::1/64 set interfaces st0 unit 1 family inet6 address 2001:db8:9000::3/64 set routing-options rib inet6.0 static route 2001:db8:2000::/64 next-hop 2001:db8:5000::1 set protocols ospf3 area 0.0.0.0 interface ge-0/0/1.0 set protocols ospf3 area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf3 area 0.0.0.0 interface st0.1 dynamic-neighbors
分步过程
下面的示例要求您在各个配置层级中进行导航。有关操作说明,请参阅在配置模式下使用 CLI 编辑器。
要配置分支 2:
-
配置接口。
[edit interfaces] user@host# set ge-0/0/0 unit 0 family inet6 address 2001:db8:5000::2/64 user@host# set ge-0/0/1 unit 0 family inet6 address 2001:db8:6000::1/64 user@host# set st0 unit 1 family inet6 address 2001:db8:9000::3/64
-
配置路由协议。
[edit protocols ospf3] user@host# set area 0.0.0.0 interface st0.1 interface-type p2mp user@host# set area 0.0.0.0 interface st0.1 dynamic-neighbors user@host# set area 0.0.0.0 interface ge-0/0/1.0 [edit routing-options] user@host# set rib inet6.0 static route 2001:db8:2000::/64 next-hop 2001:db8:5000::1
-
配置第 1 阶段选项。
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group19 user@host# set authentication-algorithm sha-384 user@host# set encryption-algorithm aes-256-cbc user@host# set lifetime-seconds 6000 [edit security ike policy IKE_POL] user@host# set mode main user@host# set proposals IKE_PROP user@host# set certificate local-certificate SPOKE2 [edit security ike gateway IKE_GW_SPOKE_2] user@host# set ike-policy IKE_POL user@host# set address 2001:db8:2000::1 user@host# set dead-peer-detection always-send user@host# set dead-peer-detection interval 10 user@host# set dead-peer-detection threshold 3 user@host# set local-identity distinguished-name user@host# set remote-identity distinguished-name container OU=SLT user@host# set external-interface ge-0/0/0.0 user@host# set advpn suggester disable user@host# set version v2-only
-
配置第 2 阶段选项。
[edit security ipsec proposal IPSEC_PROPl] user@host# set protocol esp user@host# set encryption-algorithm aes-256-gcm user@host# set lifetime-seconds 3000 [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group19 user@host# set proposals IPSEC_PROP [edit security ipsec vpn IPSEC_VPN_SPOKE_2] user@host# set bind-interface st0.1 user@host# set ike gateway IKE_GW_SPOKE_2 user@host# set ike ipsec-policy IPSEC_POL user@host# set establish-tunnels immediately
-
配置区域。
[edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces st0.1 user@host# set interfaces ge-0/0/0.0 [edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces ge-0/0/1.0
-
配置默认安全策略。
[edit security policies] user@host# set default-policy permit-all
-
配置 CA 配置文件。
[edit security pki] user@host# set ca-profile ROOT-CA ca-identity ROOT-CA user@host# set ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set ca-profile ROOT-CA enrollment retry 5 user@host# set ca-profile ROOT-CA enrollment retry-interval 0 user@host# set ca-profile ROOT-CA revocation-check disable
结果
在配置模式下,输入 show interfaces、 show protocols、 show routing-optionsshow security ike、 show security ipsec、 show security zones、 和show security policiesshow security pki命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
[edit]
user@host# show interfaces
ge-0/0/0 {
unit 0 {
family inet6 {
address 2001:db8:5000::2/64;
}
}
}
ge-0/0/1 {
unit 0 {
family inet6 {
address 2001:db8:6000::1/64;
}
}
}
st0 {
unit 1 {
family inet6 {
address 2001:db8:9000::3/64;
}
}
}
[edit]
user@host# show protocols
ospf3 {
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
dynamic-neighbors;
}
interface ge-0/0/1.0;
}
}
[edit]
user@host# show routing-options
rib inet6.0 {
static {
route 2001:db8:2000::/64 next-hop [ 2001:db8:3000::1 2001:db8:5000::1 ];
}
}
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group19;
authentication-algorithm sha-384;
encryption-algorithm aes-256-cbc;
lifetime-seconds 6000;
}
policy IKE_POL {
mode main;
proposals IKE_PROP;
certificate {
local-certificate SPOKE2;
}
}
gateway IKE_GW_SPOKE_2 {
ike-policy IKE_POL;
address 2001:db8:2000::1;
dead-peer-detection {
always-send;
interval 10;
threshold 3;
}
local-identity distinguished-name;
remote-identity distinguished-name container OU=SLT;
external-interface ge-0/0/0.0;
advpn {
suggester {
disable
}
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3000;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group19;
}
proposals IPSEC_PROP;
}
vpn IPSEC_VPN_SPOKE_2 {
bind-interface st0.1;
ike {
gateway IKE_GW_SPOKE_2;
ipsec-policy IPSEC_POL;
}
establish-tunnels immediately;
}
[edit]
user@host# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
ge-0/0/0.0;
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
ge-0/0/1.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
[edit]
user@host# show security pki
ca-profile ROOT-CA {
ca-identity ROOT-CA;
enrollment {
url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll;
retry 5;
retry-interval 0;
}
revocation-check {
disable;
}
}
如果完成设备配置,请从配置模式输入 commit。
验证
确认配置工作正常。
验证 IKE 状态
目的
验证 IKE 状态。
操作
在操作模式下,输入 show security ike sa 命令。
user@host> show security ike sa Index State Initiator cookie Responder cookie Mode Remote Address 4295070 UP 2001:db8:1ad4ba7a115fa229 2001:db8:32e6382a058bb296 Main 2001:db8:3000::2 295069 UP 2001:db8:88a1520c20cbbe04 2001:db8:7fa4c8e365393c48 Main 2001:db8:5000::2
意义
该 show security ike sa 命令会列出所有活动的 IKE 第 1 阶段 SA。如果未列出任何 SA,则第 1 阶段建立存在问题。检查配置中的 IKE 策略参数和外部接口设置。第 1 阶段提议参数必须在中心辐射上匹配。
验证 IPsec 状态
目的
验证 IPsec 状态。
操作
在操作模式下,输入 show security ipsec sa 命令。
user@host> show security ipsec sa Total active tunnels: 2 Total Ipsec sas: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <67108881 ESP:aes-gcm-256/None 3dba3f80 2979/ unlim - root 500 2001:db8:5000::2 >67108881 ESP:aes-gcm-256/None 46746d5d 2979/ unlim - root 500 2001:db8:5000::2 <67108882 ESP:aes-gcm-256/None 16dceb60 2992/ unlim - root 500 2001:db8:3000::2 >67108882 ESP:aes-gcm-256/None 681209c2 2992/ unlim - root 500 2001:db8:3000::2
意义
该 show security ipsec sa 命令将列出所有活动的 IKE 第 2 阶段 SA。如果未列出任何 SA,则第 2 阶段建立存在问题。检查配置中的 IKE 策略参数和外部接口设置。第 2 阶段提议参数必须在中心辐射上匹配。
验证 IPsec 下一跳隧道
目的
验证 IPsec 下一跃点隧道。
操作
在操作模式下,输入 show security ipsec next-hop-tunnels 命令。
user@host> show security ipsec next-hop-tunnels Next-hop gateway interface IPSec VPN name Flag IKE-ID XAUTH username 2001:db8:9000::2 st0.1 IPSEC_VPNA_1 Auto C=US, DC=example.net, ST=CA, L=Sunnyvale, O=example, OU=SLT, CN=SPOKE1 Not-Available 2001:db8:9000::3 st0.1 IPSEC_VPNA_1 Auto C=US, DC=example.net, ST=CA, L=Sunnyvale, O=example, OU=SLT, CN=SPOKE2 Not-Available 2001:db8::5668:ad10:fcd8:10c8 st0.1 IPSEC_VPNA_1 Auto C=US, DC=example.net, ST=CA, L=Sunnyvale, O=example, OU=SLT, CN=SPOKE2 Not-Available 2001:db8::5668:ad10:fcd8:112f st0.1 IPSEC_VPNA_1 Auto C=US, DC=example.net, ST=CA, L=Sunnyvale, O=example, OU=SLT, CN=SPOKE1 Not-Available
意义
下一跃点网关是分支接口的 st0 IP 地址。下一跃点应与正确的 IPsec VPN 名称相关联。
验证 OSPFv3
目的
验证 OSPFv3 是否引用分支接口的 st0 IP 地址。
操作
在操作模式下,输入 show ospf3 neighbor interface 命令。
user@host> show ospf3 neighbor interface
ID Interface State Pri Dead
2001:db8:9000:2 st0.1 Full 128 -
Neighbor-address 2001:db8::5668:ad10:fcd8:110e
2001:db8:20:54:49.693 INFO ${ret} = ID Interface State Pri Dead
2001:db8:9000:3 st0.1 Full 128 -
Neighbor-address 2001:db8::5668:ad10:fcd8:110e启用 OSPF 以在建立 ADVPN 快捷方式隧道后快速更新路由
问题
Description
OSPF 最多可能需要 9 秒才能更新路由表中的快捷方式路由。流量最多可能需要 10 秒才能转发到快捷方式隧道。
症状
在两个快捷方式伙伴之间建立快捷方式隧道后,OSPF 将启动 OSPF 你好数据包。由于建立快捷方式隧道和 OSPF 邻居安装的时间,隧道中的第一个数据包可能会被丢弃。这可能会导致 OSPF 再次尝试建立 OSPF 邻接关系。
默认情况下,OSPF 重试建立邻接关系的时间间隔为 10 秒。建立快捷方式隧道后,OSPF 可能需要 10 秒以上才能在伙伴之间建立邻接关系。
解决方案
配置较小的重试间隔(如 1 或 2 秒)可以使 OSPF 通过快捷方式隧道更快地建立邻接关系。例如,使用以下配置:
[edit] set protocols ospf area 0.0.0.0 interface st0.1 retransmit-interval 1 set protocols ospf area 0.0.0.0 interface st0.1 dead-interval 40
另请参阅
ADVPN 行为中的特定平台组播
使用 功能资源管理器 确认平台和版本对特定功能的支持。
使用下表查看您的平台特定于平台的行为。
|
平台 |
差异 |
|---|---|
|
SRX 系列 |
|
变更历史表
是否支持某项功能取决于您使用的平台和版本。 使用 Feature Explorer 查看您使用的平台是否支持某项功能。
p2mp 接口类型,用于采用 kmd 进程的 IPsec VPN。