Burst Handling
JSA uses burst handling to ensure that no data is lost when the system exceeds the allocated events per second (EPS) or flows per minute (FPM) license limits.
When JSA receives a data spike that causes it to exceed the allocated EPS and FPM limits, the extra events and flows are moved to a temporary queue to be processed when the incoming data rate slows. When burst handling is triggered, a system notification alerts you that the appliance exceeded the EPS or FPM license limit.
The backlog in the temporary queue is processed in the order that the events or flows were received. The older data at the start of the queue is processed before the most recent data at the end of the queue. The rate at which the queue empties or fills is impacted by several factors, including the volume and duration of the data spike, the capacity of the appliance, and the payload size.
Hardware appliances normally can handle burst rates at least 50% greater than the appliance's stated EPS and FPM capability, and can store up to 5GB in the temporary queue. The actual burst rate capability depends upon the system load. VM appliances can achieve similar results if the VM is adequately sized and meets the performance requirements.
The burst recovery rate is the difference between the allocated rate and the incoming rate. When the volume of incoming data slows, the system processes the backlog of events or flows in the queue as fast as the recovery rate allows. The smaller the recovery rate, the longer it takes to empty the queue.
Example: Incoming Data Spike
Every morning, between 8am and 9am, a company's network experiences a data spike as employees log in and begin to use the network resources.
The company's deployment includes a JSA Event and Flow Processor combo appliance that is allocated 5,000 events per second (EPS) and 100,000 flows per minute (FPM). The average capacity for this appliance is 4,000 EPS and 70,000 FPM.
During the data spike, which peaks around 9am, the appliance routinely receives up to 6,000 EPS and 120,000 FPM. JSA automatically moves the extra events and flows (1,000 EPS and 20,000 FPM) to the burst handling queue, and generates a system notification to alert the administrator that the appliance exceeded the allocated capacity.
The following images show a two-hour window when the incoming event and flow data exceeds the licensed capacity, which triggers a system notification, and a recovery period after the data volume returns to normal.
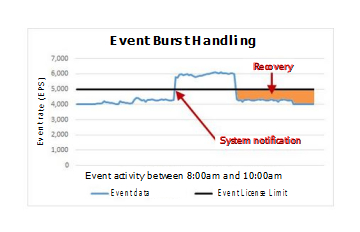
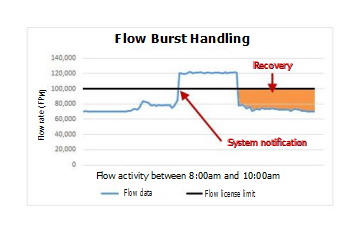
The recovery rate is the difference between the allocated EPS or FPM amount and the current incoming data rate. In this example, when the event and flow rates return to normal, the recovery rate is 1,000 EPS and 30,000 FPM.
5,000 licensed events - 4,000 incoming events = 1,000 EPS recovery rate 100,000 licensed flows - 70,000 incoming flows = 30,000 FPM recovery rate
Offenses are not generated until the data is processed by the appliance, so it is important to allocate enough EPS and FPM to the appliance to ensure that it can recover from a data spike quickly.
