New Features and Enhancements in JSA 7.4.0
The following new features and enhancements make it easier for administrators to manage their JSA 7.4.0 deployment.
To view a list of all new features in this release, see What’s New Guide.
Global System Notifications configuration
Global System Notifications are now local, making them host specific and more useful. As a result, the thresholds are now set automatically by JSA and the Global System Notification section of the Admin tab was removed.
Secure email server
Send email to distribute alerts, reports, notifications, and event messages to mail servers that require authentication.
You can configure an email server for your entire JSA deployment, or multiple email servers.
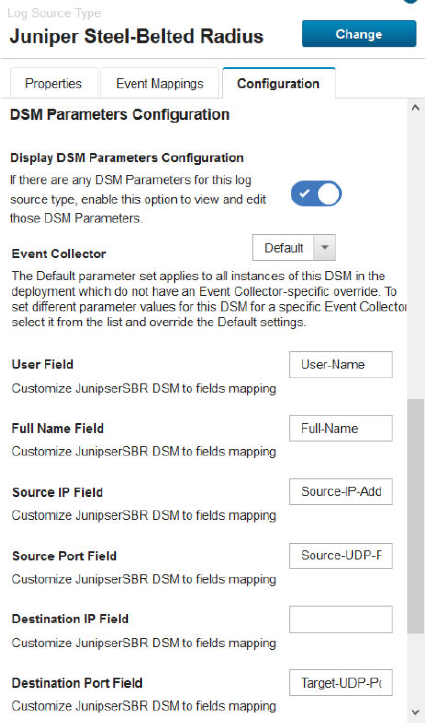
DSM Parameter support in the DSM Editor
In JSA 7.4.0, if your log source type has DSM parameters, you can use the DSM Editor to configure the DSM parameters. Enable the Display DSM Parameters Configuration option to view and edit the DSM parameters.
Reverse tunnel initiation
The SSH tunnel between two managed hosts can now be initiated from the remote host instead of the local host. For example, you have a connection from an Event Processor in a secure environment to an Event Collector that is outside of the secure environment. You also have a firewall rule that prevents you from having a host outside the secure environment connect to a host in the secure environment. In JSA 7.4.0, you can switch which host creates the tunnel so that the connection is established from the Event Processor by selecting the Remote Tunnel Initiation checkbox for the Event Collector.
Improved flow timestamp handling
Two new configuration settings provide more control over the way that flow timestamps are handled when Netflow V9 begins sending records with overflowed system uptime values. The new settings eliminate the need to reset the first and last switched times.
The new configuration options and the default values are shown here:
NORMALISE_OVERFLOWED_UPTIMES=YES
UPTIME_OVERFLOW_THRESHOLD_MSEC=86400000
The timestamps are corrected when the system uptime value is less than the first and last switched packet times by more than the value that is specified in the UPTIME_OVERFLOW_THRESHOLD_MSEC configuration. The timestamps are corrected based on the assumption that the system uptime wrapped around the maximum 32-bit value.
