Firewall DoS Attacks
DoS attack protection leverages stateful inspection to look for and then allow or deny all connection attempts that require crossing an interface on their way to and from the intended destination, For more information, see the following topics:
Understanding Session Table Flood Attacks
A successful DoS attack overwhelms its victim with such a massive barrage of false simulated traffic that it becomes unable to process legitimate connection requests. DoS attacks can take many forms—SYN flood, SYN-ACK-ACK flood, UDP flood, ICMP flood, and so on—but they all seek the same objective, which is to fill up their victim's session table.
When the session table is full, that host cannot create any new sessions and begins rejecting new connection requests. The source-based session limits screen option and the destination-based session limit screen option help mitigate such attacks.
Understanding Source-Based Session Limits
In addition to limiting the number of concurrent sessions from the same source IP address, you can also limit the number of concurrent sessions to the same destination IP address. One benefit of setting a source-based session limit is that it can stem an attack such as the Nimda virus (which is actually both a virus and a worm) that infects a server and then begins generating massive amounts of traffic from that server. Because all the virus-generated traffic originates from the same IP address, a source-based session limit ensures that the firewall can curb such excessive amounts of traffic. See Figure 1.
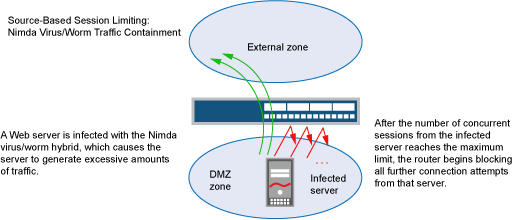
Another benefit of source-based session limiting is that it can mitigate attempts to fill up the firewall's session table if all the connection attempts originate from the same source IP address.
Determining what constitutes an acceptable number
of connection requests requires a period of observation and analysis
to establish a baseline for typical traffic flows. You also need to
consider the maximum number of concurrent sessions required to fill
up the session table of the particular Juniper Networks platform you
are using. To see the maximum number of sessions that your session
table supports, use the CLI command show security flow session
summary, and then look at the last line in the output, which
lists the number of current (allocated) sessions, the maximum number
of sessions, and the number of failed session allocations:
userhost# show security flow session summary Unicast-sessions: 0 Multicast-sessions: 0 Failed-sessions: 0 Sessions-in-use: 0 Valid sessions: 0 Pending sessions: 0 Invalidated sessions: 0 Sessions in other states: 0 Maximum-sessions: 2097152
The default maximum for source-based session limits is 128 concurrent sessions, a value that might need adjustment to suit the needs of your network environment and the platform.
Junos OS supports source-based session limits for both IPv4 and IPv6 traffic.
Example: Setting Source-Based Session Limits
This example shows how to limit the amount of sessions based on source IP.
Requirements
No special configuration beyond device initialization is required before configuring this feature.
Overview
The following example shows how to limit the number of sessions that any one server in the DMZ and in zone a can initiate. Because the DMZ contains only webservers, none of which should initiate traffic, you set the source-session limit at the lowest possible value, which is one session. On the other hand, zone a contains personal computers, servers, printers, and so on, many of which do initiate traffic. For zone a, you set the source-session limit to a maximum of 80 concurrent sessions.
Topology
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security screen ids-option 1-limit-session limit-session source-ip-based 1 set security zones security-zone dmz screen 1-limit-session set security screen ids-option 80-limit-session limit-session source-ip-based 80 set security zones security-zone zone_a screen 80-limit-session
Step-by-Step Procedure
Specify the number of concurrent sessions based on source IP for the DMZ zone.
[edit security] user@host# set screen ids-option 1-limit-session limit-session source-ip-based 1
Set the security zone for the DMZ to the configuration limit.
[edit security] user@host# set zones security-zone dmz screen 1-limit-session
Specify the number of concurrent sessions based on source IP for the zone a zone.
[edit security] user@host# set screen ids-option 80-limit-session limit-session source-ip-based 80
Set the security zone for zone a to the configuration limit.
[edit security] user@host# set zones security-zone zone_a screen 80-limit-session
Results
From configuration mode, confirm your configuration
by entering the show security screen and show security
zones commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example
to correct it.
[edit]
user@host# show security screen
ids-option 1-limit-session {
limit-session {
source-ip-based 1;
}
}
ids-option 80-limit-session {
limit-session {
source-ip-based 80;
}
}
[edit]
user@host# show security zones
security-zone dmz {
screen 1-limit-session;
}
security-zone zone_a {
screen 80-limit-session;
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Verifying Source-Based Session Limits
Purpose
Verify source-based session limits.
Action
Enter the show security screen ids-option 1-limit-session , show security screen ids-option 80-limit-session, and show security zones commands from operational mode.
user@host> show security screen ids-option 1-limit-session Screen object status: Name Value Session source limit threshold 1 user@host> show security screen ids-option 80-limit-session Screen object status: Name Value Session source limit threshold 80 user@host> show security zones Security zone: dmz Send reset for non-SYN session TCP packets: Off Policy configurable: Yes Screen: 1-limit-session Interfaces bound: 0 Interfaces:
Meaning
The sample output shows the source session limit values for DMZ zone and zone a.
Understanding Destination-Based Session Limits
In addition to limiting the number of concurrent sessions from the same source IP address, you can also limit the number of concurrent sessions to the same destination IP address. A wily attacker can launch a distributed denial-of-service (DDoS) attack. In a DDoS attack, the malicious traffic can come from hundreds of hosts, known as “zombie agents,” that are surreptitiously under the control of an attacker. In addition to the SYN, UDP, and ICMP flood detection and prevention screen options, setting a destination-based session limit can ensure that Junos OS allows only an acceptable number of concurrent connection requests—no matter what the source—to reach any one host. See Figure 2.
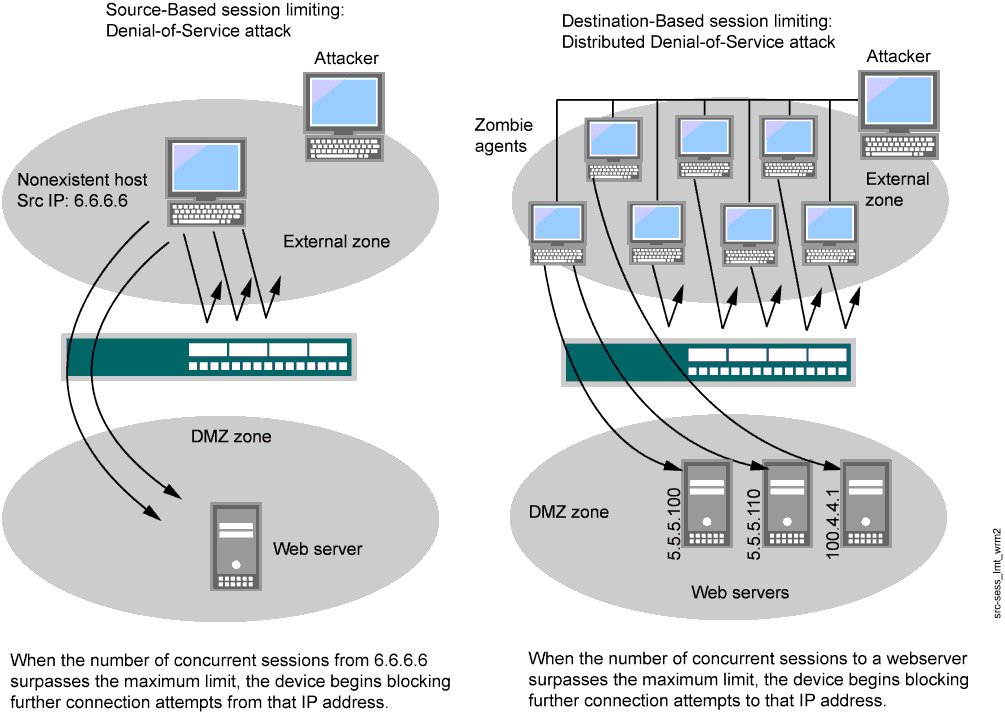
The default maximum for destination-based session limits is 128 concurrent sessions, a value that might need adjustment to suit the needs of your network environment and the platform.
Example: Setting Destination-Based Session Limits
This example shows how to set the destination-based session limits.
Requirements
No special configuration beyond device initialization is required before configuring this feature.
Overview
In this example, you limit the amount of traffic to a webserver at 1.2.2.5. The server is in the DMZ. The example assumes that after observing the traffic flow from the external zone to this server for a month, you have determined that the average number of concurrent sessions it receives is 2000. Also, you set the new session limit at 2000 concurrent sessions. Although traffic spikes might sometimes exceed that limit, the example assumes that you are opting for firewall security over occasional server inaccessibility.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration
mode.
set security screen ids-option 2000-limit-session limit-session destination-ip-based 2000 set security zones security-zone external_zone screen 2000-limit-session
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. To set the destination-based session limits:
Specify the number of concurrent sessions.
[edit] user@host# set security screen ids-option 2000-limit-session limit-session destination-ip-based 2000
Set the security zone for the external zone.
[edit] user@host# set security zones security-zone external_zone screen 2000-limit-session
Results
From configuration mode, confirm your configuration
by entering the show security screen and show security
zones commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example
to correct it.
[edit]
user@host# show security screen
ids-option 2000-limit-session {
limit-session {
destination-ip-based 2000;
}
}
[edit]
user@host# show security zones
security-zone external_zone {
screen 2000-limit-session;
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Verifying Destination-Based Session Limits
Purpose
Verify destination-based session limits.
Action
Enter the show security screen ids-option 2000-limit-session and show security zones commands from operational mode.
user@host> show security screen ids-option 2000-limit-session
node0:
--------------------------------------------------------------------------
Screen object status:
Name Value
Session destination limit threshold 2000
Value
user@host> show security zones
Security zone: external_zone
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes
Screen: 2000-limit-session
Interfaces bound: 0
Interfaces:
Meaning
The sample output shows the destination session limit values for external zone.
Understanding SYN-ACK-ACK Proxy Flood Attacks
When an authentication user initiates a Telnet or an FTP connection, the user sends a SYN segment to the Telnet or FTP server. Junos OS intercepts the SYN segment, creates an entry in its session table, and proxies a SYN-ACK segment to the user. The user then replies with an ACK segment. At this point, the initial three-way handshake is complete. Junos OS sends a login prompt to the user. If the user, with malicious intent, does not log in but instead continues initiating SYN-ACK-ACK sessions, the firewall session table can fill up to the point where the device begins rejecting legitimate connection requests.
To prevent such an attack, you can enable the SYN-ACK-ACK proxy protection screen option. After the number of connections from the same IP address reaches the SYN-ACK-ACK proxy threshold, Junos OS rejects further connection requests from that IP address. By default, the threshold is 512 connections from any single IP address. You can change this threshold (to any number between 1 and 250,000) to better suit the requirements of your network environment.
Junos OS supports SYN-ACK-ACK proxy protection for both IPv4 and IPv6 addresses.
Protecting Your Network Against a SYN-ACK-ACK Proxy Flood Attack
This example shows how to protect your network against a SYN-ACK-ACK proxy flood attack.
Requirements
No special configuration beyond device initialization is required before configuring this feature.
Overview
In this example, you enable protection against a SYN-ACK-ACK proxy flood. The value unit is connections per source address. The default value is 512 connections from any single address.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security screen ids-option 1000-syn-ack-ack-proxy tcp syn-ack-ack-proxy threshold 1000 set security zones security-zone zone screen 1000-syn-ack-ack-proxy
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. To protect against a SYN-ACK-ACK proxy flood attack:
Specify the source session limits.
[edit] user@host# set security screen ids-option 1000-syn-ack-ack-proxy tcp syn-ack-ack-proxy threshold 1000
Set the security zone for zone screen.
[edit] user@host# set security zones security-zone zone screen 1000-syn-ack-ack-proxy
Results
From configuration mode, confirm your configuration
by entering the show security screen and show security
zones commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example
to correct it.
[edit]
user@host# show security screen
ids-option 1000-syn-ack-ack-proxy {
tcp {
syn-ack-ack-proxy threshold 1000;
}
}
[edit]
user@host# show security zones
security-zone zone {
screen 1000-syn-ack-ack-proxy;
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Verifying SYN-ACK-ACK Proxy Flood Attack
Purpose
Verify SYN-ACK-ACK proxy flood attack.
Action
Enter the show security screen ids-option 1000-syn-ack-ack-proxy and show security zones commands from operational mode.
user@host> show security screen ids-option 1000-syn-ack-ack-proxy node0: -------------------------------------------------------------------------- Screen object status: Name Value TCP SYN-ACK-ACK proxy threshold 1000 user@host> show security zones Security zone: zone Send reset for non-SYN session TCP packets: Off Policy configurable: Yes Screen: 1000-syn-ack-ack-proxy Interfaces bound: 0 Interfaces:
Meaning
The sample output shows that there is no attack from SYN-ACK-ACK-proxy flood.
