Operating System Identification Probes
Prior to launching an exploit, an attacker might probe the targeted host, trying to learn its operating system. Various operating systems react to TCP anomalies in different ways. With that knowledge, an attacker can decide which further attack might inflict more damage to the device, the network, or both, For more information, see the following topics:
Understanding Operating System Identification Probes
Before launching an exploit, attackers might try to probe the targeted host to learn its operating system (OS). With that knowledge, they can better decide which attack to launch and which vulnerabilities to exploit. Junos OS can block reconnaissance probes commonly used to gather information about OS types.
Understanding Domain Name System Resolve
Prior to Junos OS Release 12.1X47, DNS resolution was performed with only UDP as a transport. Messages carried by UDP are restricted to 512 bytes; longer messages are truncated and the traffic class (TC) bit is set in the header. The maximum length of UDP DNS response messages is 512 bytes, but the maximum length of TCP DNS response messages is 65,535 bytes. A DNS resolver knows whether the response is complete if the TC bit is set in the header. Hence, a TCP DNS response can carry more information than a UDP DNS response.
There are three types of DNS resolve behaviors:
UDP DNS resolve
TCP DNS resolve
UDP/TCP DNS resolve
A policy uses UDP/TCP DNS resolve to resolve IP addresses. In UDP/TCP DNS resolve, UDP DNS resolve is first used, and when it gets truncated TCP DNS resolve is used.
A Routing Engine policy supports a maximum of 1024 IPv4 address prefixes and 256 IPv6 address prefixes that can be sent to the PFE. If the maximum number of IPv4 or IPv6 address prefixes exceeds the limits, the addresses over the limitations will not be sent to the PFE and a syslog message is generated. The maximum number of addresses in a TCP DNS response is 4094 for IPv4 addresses and 2340 for IPv6 addresses, but only 1024 IPv4 addresses and 256 IPv6 addresses are loaded to the PFE.
Understanding TCP Headers with SYN and FIN Flags Set
Both the SYN and FIN control flags are not normally set in the same TCP segment header. The SYN flag synchronizes sequence numbers to initiate a TCP connection. The FIN flag indicates the end of data transmission to finish a TCP connection. Their purposes are mutually exclusive. A TCP header with the SYN and FIN flags set is anomalous TCP behavior, causing various responses from the recipient, depending on the OS. See Figure 1.
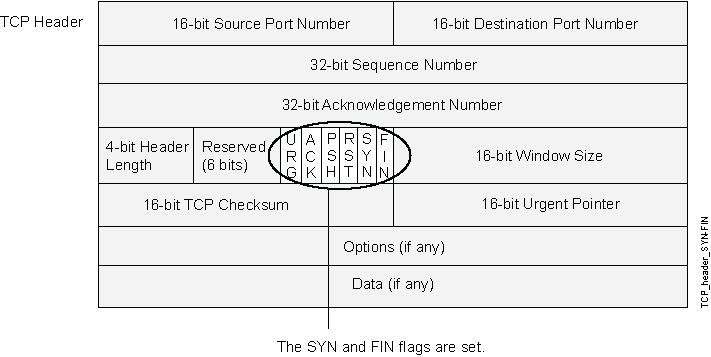
An attacker can send a segment with both flags set to see what kind of system reply is returned and thereby determine what kind of OS is on the receiving end. The attacker can then use any known system vulnerabilities for further attacks.
When you enable this screen option, Junos OS checks if the SYN and FIN flags are set in TCP headers. If it discovers such a header, it drops the packet.
Junos OS supports TCP header with SYN and FIN flags set protection for both IPv4 and IPv6 traffic.
Example: Blocking Packets with SYN and FIN Flags Set
This example shows how to create a screen to block packets with the SYN and FIN flags set.
Requirements
Before you begin, understand how TCP headers with SYN and FIN flags work. See Understanding TCP Headers with SYN and FIN Flags Set.
Overview
The TCP header with the SYN and FIN flags set cause different responses from a targeted device depending on the OS it is running. The syn-fin screen is enabled for the security zone.
In this example, you create a screen called screen-1 in a security zone to block packets with the SYN and FIN flags set.
Topology
Configuration
Procedure
Step-by-Step Procedure
To block packets with both the SYN and FIN flags set:
Configure the screen.
[edit] user@host# set security screen ids-option screen-1 tcp syn-fin
Enable the screen in the security zone.
[edit ] user@host# set security zones security-zone zone-1 screen screen-1
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
Confirm that the configuration is working properly.
Verifying the Screens in the Security Zone
Purpose
Verify that the screen is enabled in the security zone.
Action
From operational mode, enter the show security
zones command.
[edit]
user@host> show security zones
Security zone: zone-1
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes
Screen: screen-1
Interfaces bound: 1
Interfaces:
ge-1/0/0.0Verifying the Security Screen Configuration
Purpose
Display the configuration information about the security screen.
Action
From operational mode, enter the show security
screen ids-option screen-name command.
[edit]
user@host> show security screen ids-option screen-1
Screen object status:
Name Value
TCP SYN FIN enabled
Understanding TCP Headers With FIN Flag Set and Without ACK Flag Set
Figure 2 shows TCP segments with the FIN control flag set (to signal the conclusion of a session and terminate the connection). Normally, TCP segments with the FIN flag set also have the ACK flag set (to acknowledge the previous packet received). Because a TCP header with the FIN flag set but not the ACK flag is anomalous TCP behavior, there is no uniform response to this. The OS might respond by sending a TCP segment with the RST flag set. Another might completely ignore it. The victim's response can provide the attacker with a clue as to its OS. (Other purposes for sending a TCP segment with the FIN flag set are to evade detection while performing address and port scans and to evade defenses on guard for a SYN flood by performing a FIN flood instead.)
Vendors have interpreted RFC 793, Transmission Control Protocol, variously when designing their TCP/IP implementations. When a TCP segment arrives with the FIN flag set but not the ACK flag, some implementations send RST segments, while others drop the packet without sending an RST.
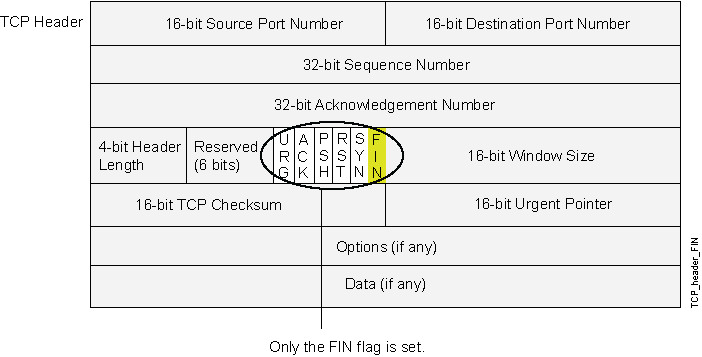
When you enable this screen option, Junos OS checks if the FIN flag is set but not the ACK flag in TCP headers. If it discovers a packet with such a header, it drops the packet.
Junos OS supports TCP header with SYN and FIN flags set protection for both IPv4 and Ipv6 traffic.
Example: Blocking Packets With FIN Flag Set and Without ACK Flag Set
This example shows how to create a screen to block packets with the FIN flag set but the ACK flag not set.
Requirements
Before you begin, understand how TCP headers work. See Understanding TCP Headers With FIN Flag Set and Without ACK Flag Set.
Overview
The TCP segments with the FIN flag set also have the ACK flag set to acknowledge the previous packet received. Because a TCP header with the FIN flag set but the ACK flag not set is anomalous TCP behavior, there is no uniform response to this. When you enable the fin-no-ack screen option, Junos OS checks if the FIN flag is set but not the ACK flag in TCP headers. If it discovers a packet with such a header, it drops the packet.
In this example, you create a screen called screen-1 to block packets with the FIN flag set but the ACK flag not set.
Configuration
Procedure
Step-by-Step Procedure
To block packets with the FIN flag set but the ACK flag not set:
Configure the screen.
[edit ] user@host# set security screen ids-option screen-1 tcp fin-no-ack
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
Confirm that the configuration is working properly.
Verifying the Screens in the Security Zone
Purpose
Verify that the screen is enabled in the security zone.
Action
From operational mode, enter the show security
zones command.
[edit]
user@host> show security zones
Security zone: zone-1
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes
Screen: screen-1
Interfaces bound: 1
Interfaces:
ge-1/0/0.0Verifying the Security Screen Configuration
Purpose
Display the configuration information about the security screen.
Action
From operational mode, enter the show security
screen ids-option screen-name command.
[edit]
user@host> show security screen ids-option screen-1
Screen object status:
Name Value
TCP FIN no ACK enabled
Understanding TCP Header with No Flags Set
A normal TCP segment header has at least one flag control set. A TCP segment with no control flags set is an anomalous event. Because different operating systems respond differently to such anomalies, the response (or lack of response) from the targeted device can provide a clue as to the type of OS it is running. See Figure 3.
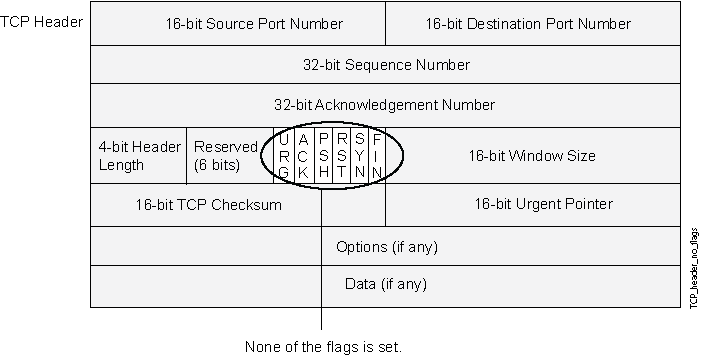
When you enable the device to detect TCP segment headers with no flags set, the device drops all TCP packets with a missing or malformed flags field.
Junos OS supports TCP header with no flags set protection for both IPv4 and IPv6 traffic.
Example: Blocking Packets with No Flags Set
This example shows how to create a screen to block packets with no flags set.
Requirements
Before you begin, understand how a TCP header with no flags set works. See Understanding TCP Header with No Flags Set.
Overview
A normal TCP segment header has at least one flag control set. A TCP segment with no control flags set is an anomalous event. Because different operating systems respond differently to such anomalies, the response (or lack of response) from the targeted device can provide a clue as to the type of OS it is running.
When you enable the device to detect TCP segment headers with no flags set, the device drops all TCP packets with a missing or malformed flags field.
In this example, you create a screen called screen-1 to block packets with no flags set.
Configuration
Procedure
Step-by-Step Procedure
To block packets with no flags set:
Configure the screen.
[edit ] user@host# set security screen ids-option screen-1 tcp tcp-no-flag
Enable the screen in the security zone.
[edit ] user@host# set security zones security-zone zone-1 screen screen-1
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
Confirm that the configuration is working properly.
Verifying the Screens in the Security Zone
Purpose
Verify that the screen is enabled in the security zone.
Action
From operational mode, enter the show security
zones command.
[edit]
user@host> show security zones
Security zone: zone-1
Send reset for non-SYN session TCP packets: Off
Policy configurable: Yes
Screen: screen-1
Interfaces bound: 1
Interfaces:
ge-1/0/0.0Verifying the Security Screen Configuration
Purpose
Display the configuration information about the security screen.
Action
From operational mode, enter the show security
screen ids-option screen-name command.
[edit]
user@host> show security screen ids-option screen-1
Screen object status:
Name Value
TCP no flag enabled
