Example: Configure Multinode High Availability in a Hybrid Deployment
Read this topic to learn how to configure Multinode High Availability solution on SRX Series Firewalls. The example covers configuration in active/backup mode when SRX Series Firewalls are connected to a router on one side and switch on the other side.
Overview
In a hybrid deployments, participating SRX Series Firewalls operate as independent nodes in a mixed mode of routed networks on one side and locally connected networks on the other side. An encrypted logical interchassis link (ICL) connects the nodes over a routed network.
In Multinode High Availability, activeness is determined at the services redundancy group (SRG) level. The SRX Series Firewall, on which the SRG1 is active, hosts the floating IP address and steers traffic towards it using the floating IP address. During a failover, the floating IP address moves from the old active node to the new active node and continues the communication client devices.
As of Junos OS Release 22.3R1, we support a two-node configuration in the Multinode High Availability solution.
In this example, you'll establish high availability between the SRX Series Firewalls and secure the tunnel traffic by enabling HA link encryption.
Requirements
This example uses the following hardware and software components:
- Two SRX Series Firewalls or vSRX Virtual Firewall Instances
- A Juniper Networks(R) MX960 Universal Routing Platform at one end
- A Juniper Networks(R) EX9214 Ethernet Switch at the other end
- Junos OS Release 22.3R1
Topology
Figure 1 shows the topology used in this example.
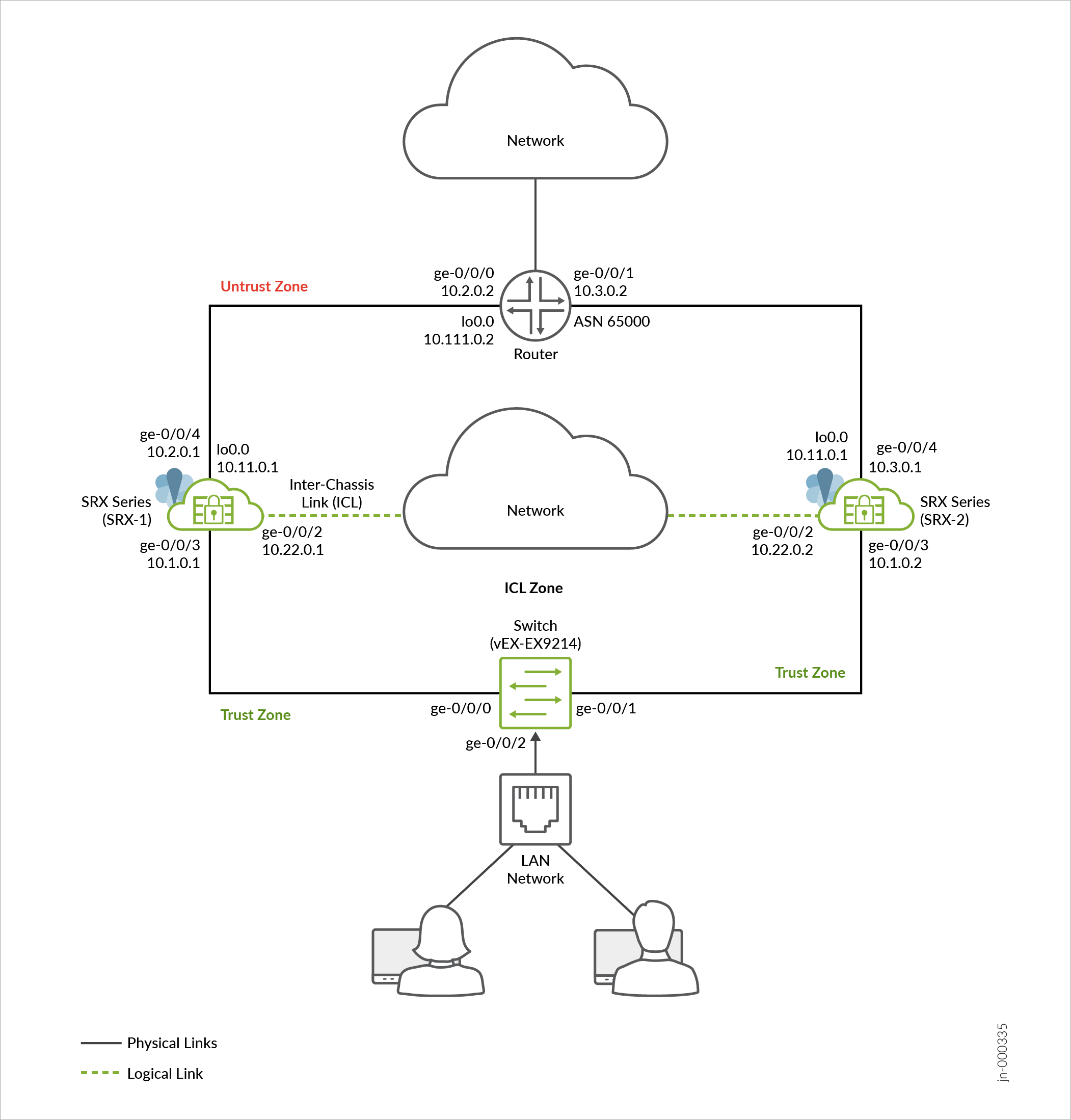
As shown in the topology, two SRX Series Firewalls connected to routers on untrust side and to a switch trust side of the network. The nodes communicate with each other using a routable IP address (floating IP address) over the network. Loopback interfaces are used to host the IP addresses on SRX Series and upstream router.
In general, you can use Aggregated Ethernet (AE) or a revenue Ethernet port on the SRX Series Firewalls to setup an ICL connection. In this example, we've used GE ports for the ICL. We've also configured a routing instance for the ICL path to ensure maximum segmentation. In a typical high availability deployment, you have multiple routers and switches on the northbound and southbound sides of the network. For this example, we are using one router and one switch.
You'll perform the following tasks to build a Multinode High Availability setup:
- Configure a pair of SRX Series Firewalls as local and peer nodes by assigning IDs.
- Configure services redundancy groups (SRGs).
- Configure a loopback interface (lo0.0) to host a floating IP address on the Layer 3 side.
- Configure virtual IP addresses for activeness determination and enforcement on the Layer 2 side.
- Configure a signal route required for activeness enforcement and use it along with the route exists policy.
- Configure a VPN profile for the high availability (ICL) traffic using IKEv2.
- Configure BFD monitoring options.
- Configure a routing policy and routing options.
- Configure appropriate security policies to manage traffic in your network.
-
Configure stateless firewall filtering and quality of service (QoS) as per your network requirements.
-
Configure interfaces and zones according to your network requirement. You must allow services such as IKE for link encryption and SSH for configuration synchronization as host-inbound system services on the security zone that is associated with the ICL.
In this example, you use static routes on SRX-1 and SRX-2 and advertise these routes into BGP to add the metric to determine which SRX Series Firewall is in the preferred path. Alternatively you can use route reflectors on the SRX Series Firewalls to advertise the routes learned via BGP and accordingly configure the routing policy to match on BGP.
You can configure the following options on SRG0 and SRG1:
-
SRG1: Active/backup signal route, deployment type, activeness priority, preemption, virtual IP address (for default gateway deployments), activeness probing and process packet on backup.
-
SRG1: BFD monitoring, IP monitoring, and interface monitoring options on SRG1.
-
SRG0: shutdown on failure and install on failure route options.
When you configure monitoring (BFD or IP or Interface) options under SRG1, we recommend not to configure the shutdown-on-failure option under SRG0.
For interchassis link (ICL), we recommend the following configuration settings:
- Use a loopback (lo0) interface using an aggregated Ethernet interface (ae0), or any revenue Ethernet interface to establish the ICL. Do not to use the dedicated HA ports (control and fabric ports) if available on your SRX Series Firewall).
- Set MTU of 1514
- Allow the following services on the security zone associated with interfaces
used for ICL
-
IKE, high-availability, SSH
-
Protocols depends on routing protocol you need
-
BFD to monitor the neighboring routes
-
Configuration
Before You Begin
Junos IKE package is required on your SRX Series Firewalls for Multinode High Availability configuration. This package is available as a default package or as an optional package on SRX Series Firewalls. See Support for Junos IKE Package for details.
If the package is not installed by default on your SRX Series firewall, use the following command to install it. You require this step for ICL encryption.
user@host> request system software add optional://junos-ike.tgz Verified junos-ike signed by PackageProductionECP256_2022 method ECDSA256+SHA256 Rebuilding schema and Activating configuration... mgd: commit complete Restarting MGD ... WARNING: cli has been replaced by an updated version: CLI release 20220208.163814_builder.r1239105 built by builder on 2022-02-08 17:07:55 UTC Restart cli using the new version ? [yes,no] (yes)
CLI Quick Configuration
To quickly configure this
example, copy the following commands, paste them into a text file, remove any
line breaks, change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit]
hierarchy level, and then enter commit from configuration
mode.
On SRX-1 Device
set chassis high-availability local-id 1 set chassis high-availability local-id local-ip 10.22.0.1 set chassis high-availability peer-id 2 peer-ip 10.22.0.2 set chassis high-availability peer-id 2 interface ge-0/0/2.0 set chassis high-availability peer-id 2 vpn-profile IPSEC_VPN_ICL set chassis high-availability peer-id 2 liveness-detection minimum-interval 400 set chassis high-availability peer-id 2 liveness-detection multiplier 5 set chassis high-availability services-redundancy-group 0 peer-id 2 set chassis high-availability services-redundancy-group 1 deployment-type hybrid set chassis high-availability services-redundancy-group 1 peer-id 2 set chassis high-availability services-redundancy-group 1 virtual-ip 1 ip 10.1.0.200/16 set chassis high-availability services-redundancy-group 1 virtual-ip 1 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 1 virtual-ip 1 use-virtual-mac set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.2.0.2 src-ip 10.2.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.2.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.2.0.2 interface ge-0/0/4.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 200 set security ike proposal MNHA_IKE_PROP description mnha_link_encr_tunnel set security ike proposal MNHA_IKE_PROP authentication-method pre-shared-keys set security ike proposal MNHA_IKE_PROP dh-group group14 set security ike proposal MNHA_IKE_PROP authentication-algorithm sha-256 set security ike proposal MNHA_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal MNHA_IKE_PROP lifetime-seconds 3600 set security ike policy MNHA_IKE_POL description mnha_link_encr_tunnel set security ike policy MNHA_IKE_POL proposals MNHA_IKE_PROP set security ike policy MNHA_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway MNHA_IKE_GW ike-policy MNHA_IKE_POL set security ike gateway MNHA_IKE_GW version v2-only set security ipsec proposal MNHA_IPSEC_PROP description mnha_link_encr_tunnel set security ipsec proposal MNHA_IPSEC_PROP protocol esp set security ipsec proposal MNHA_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal MNHA_IPSEC_PROP lifetime-seconds 3600 set security ipsec policy MNHA_IPSEC_POL description mnha_link_encr_tunnel set security ipsec policy MNHA_IPSEC_POL proposals MNHA_IPSEC_PROP set security ipsec vpn IPSEC_VPN_ICL ha-link-encryption set security ipsec vpn IPSEC_VPN_ICL ike gateway MNHA_IKE_GW set security ipsec vpn IPSEC_VPN_ICL ike ipsec-policy MNHA_IPSEC_POL set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces ge-0/0/4.0 set security zones security-zone untrust interfaces lo0.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/3.0 set security zones security-zone halink host-inbound-traffic system-services ike set security zones security-zone halink host-inbound-traffic system-services ping set security zones security-zone halink host-inbound-traffic system-services high-availability set security zones security-zone halink host-inbound-traffic system-services ssh set security zones security-zone halink host-inbound-traffic protocols bfd set security zones security-zone halink host-inbound-traffic protocols bgp set security zones security-zone halink interfaces ge-0/0/2.0 set interfaces ge-0/0/2 description ha_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.1/24 set interfaces ge-0/0/3 description trust set interfaces ge-0/0/3 unit 0 family inet address 10.1.0.1/16 set interfaces ge-0/0/4 description untrust set interfaces ge-0/0/4 unit 0 family inet address 10.2.0.1/16 set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.11.0.1/32 set interfaces lo0 unit 0 family inet address 10.11.0.2/32 set interfaces lo0 unit 0 family inet address 10.11.0.3/32 set policy-options policy-statement mnha-route-policy term 1 from protocol static set policy-options policy-statement mnha-route-policy term 1 from protocol direct set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from protocol static set policy-options policy-statement mnha-route-policy term 2 from protocol direct set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from protocol static set policy-options policy-statement mnha-route-policy term 3 from protocol direct set policy-options policy-statement mnha-route-policy term 3 then metric 30 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists if-route-exists address-family inet table inet.0 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.2.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 65000 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.2.0.2 set routing-options autonomous-system 65000 set routing-options static route 10.4.0.0/16 next-hop 10.2.0.2 set routing-options static route 10.111.0.2/32 next-hop 10.2.0.2
On SRX-2 Device
set chassis high-availability local-id 2 set chassis high-availability local-id local-ip 10.22.0.2 set chassis high-availability peer-id 1 peer-ip 10.22.0.1 set chassis high-availability peer-id 1 interface ge-0/0/2.0 set chassis high-availability peer-id 1 vpn-profile IPSEC_VPN_ICL set chassis high-availability peer-id 1 liveness-detection minimum-interval 400 set chassis high-availability peer-id 1 liveness-detection multiplier 5 set chassis high-availability services-redundancy-group 0 peer-id 1 set chassis high-availability services-redundancy-group 1 deployment-type hybrid set chassis high-availability services-redundancy-group 1 peer-id 1 set chassis high-availability services-redundancy-group 1 virtual-ip 1 ip 10.1.0.200/16 set chassis high-availability services-redundancy-group 1 virtual-ip 1 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 1 virtual-ip 1 use-virtual-mac set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.3.0.2 src-ip 10.3.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.3.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.3.0.2 interface ge-0/0/4.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 activeness-priority 1 set security ike proposal MNHA_IKE_PROP description mnha_link_encr_tunnel set security ike proposal MNHA_IKE_PROP authentication-method pre-shared-keys set security ike proposal MNHA_IKE_PROP dh-group group14 set security ike proposal MNHA_IKE_PROP authentication-algorithm sha-256 set security ike proposal MNHA_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal MNHA_IKE_PROP lifetime-seconds 3600 set security ike policy MNHA_IKE_POL description mnha_link_encr_tunnel set security ike policy MNHA_IKE_POL proposals MNHA_IKE_PROP set security ike policy MNHA_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway MNHA_IKE_GW ike-policy MNHA_IKE_POL set security ike gateway MNHA_IKE_GW version v2-only set security ipsec proposal MNHA_IPSEC_PROP description mnha_link_encr_tunnel set security ipsec proposal MNHA_IPSEC_PROP protocol esp set security ipsec proposal MNHA_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal MNHA_IPSEC_PROP lifetime-seconds 3600 set security ipsec policy MNHA_IPSEC_POL description mnha_link_encr_tunnel set security ipsec policy MNHA_IPSEC_POL proposals MNHA_IPSEC_PROP set security ipsec vpn IPSEC_VPN_ICL ha-link-encryption set security ipsec vpn IPSEC_VPN_ICL ike gateway MNHA_IKE_GW set security ipsec vpn IPSEC_VPN_ICL ike ipsec-policy MNHA_IPSEC_POL set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces ge-0/0/4.0 set security zones security-zone untrust interfaces lo0.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/3.0 set security zones security-zone halink host-inbound-traffic system-services ike set security zones security-zone halink host-inbound-traffic system-services ping set security zones security-zone halink host-inbound-traffic system-services high-availability set security zones security-zone halink host-inbound-traffic system-services ssh set security zones security-zone halink host-inbound-traffic protocols bfd set security zones security-zone halink host-inbound-traffic protocols bgp set security zones security-zone halink interfaces ge-0/0/2.0 set interfaces ge-0/0/2 description ha_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.2/24 set interfaces ge-0/0/3 description trust set interfaces ge-0/0/3 unit 0 family inet address 10.1.0.2/16 set interfaces ge-0/0/4 description untrust set interfaces ge-0/0/4 unit 0 family inet address 10.3.0.1/16 set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.11.0.1/32 set interfaces lo0 unit 0 family inet address 10.11.0.2/32 set interfaces lo0 unit 0 family inet address 10.11.0.3/32 set policy-options route-filter-list loopback 10.11.0.0/24 orlonger set policy-options route-filter-list ipsec 10.4.0.0/16 orlonger set policy-options policy-statement mnha-route-policy term 1 from protocol static set policy-options policy-statement mnha-route-policy term 1 from protocol direct set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from protocol static set policy-options policy-statement mnha-route-policy term 2 from protocol direct set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from protocol static set policy-options policy-statement mnha-route-policy term 3 from protocol direct set policy-options policy-statement mnha-route-policy term 3 then metric 35 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists if-route-exists address-family inet table inet.0 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.3.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 65000 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.3.0.2 set routing-options autonomous-system 65000 set routing-options static route 10.4.0.0/16 next-hop 10.3.0.2 set routing-options static route 10.111.0.2/32 next-hop 10.3.0.2
The following sections show configuration snippets on the router and switch required for setting up Multinode High Availability setup in the network.
On the Router (MX960)
set interfaces ge-0/0/0 description HA set interfaces ge-0/0/0 unit 0 family inet address 10.2.0.2/16 set interfaces ge-0/0/1 description HA set interfaces ge-0/0/1 unit 0 family inet address 10.3.0.2/16 set interfaces ge-0/0/2 description trust set interfaces ge-0/0/2 unit 0 family inet address 10.4.0.1/16 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.2/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.2/32 preferred set routing-options autonomous-system 65000 set protocols bgp group mnha_r0 type internal set protocols bgp group mnha_r0 local-address 10.2.0.2 set protocols bgp group mnha_r0 local-as 65000 set protocols bgp group mnha_r0 bfd-liveness-detection minimum-interval 500 set protocols bgp group mnha_r0 bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group mnha_r0 bfd-liveness-detection multiplier 3 set protocols bgp group mnha_r0 neighbor 10.2.0.1 set protocols bgp group mnha_r0_b type internal set protocols bgp group mnha_r0_b local-address 10.3.0.2 set protocols bgp group mnha_r0_b local-as 65000 set protocols bgp group mnha_r0_b bfd-liveness-detection minimum-interval 500 set protocols bgp group mnha_r0_b bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group mnha_r0_b bfd-liveness-detection multiplier 3 set protocols bgp group mnha_r0_b neighbor 10.3.0.1
On the Switch (EX9214)
set interfaces ge-0/0/0 description lan set interfaces ge-0/0/0 mtu 9192 set interfaces ge-0/0/0 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/0 unit 0 family ethernet-switching vlan members lan set interfaces ge-0/0/1 description lan set interfaces ge-0/0/1 mtu 9192 set interfaces ge-0/0/1 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members lan set interfaces ge-0/0/2 description lan set interfaces ge-0/0/2 mtu 9192 set interfaces ge-0/0/2 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/2 unit 0 family ethernet-switching vlan members lan set vlans lan vlan-id 1001
Configuration
Step-by-Step Procedure
We're showing the configuration of SRX-01 in the step-by-step procedure.
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
-
Configure Interfaces.
[edit] user@host# set interfaces ge-0/0/3 description "trust" unit 0 family inet address 10.1.0.1/16 user@host# set interfaces ge-0/0/4 description "untrust" unit 0 family inet address 10.2.0.1/16 user@host# set interfaces ge-0/0/2 description "ha_link" unit 0 family inet address 10.22.0.1/24
The interfaces ge-0/0/3 connects to the switch, ge-0/0/4 connects the router and the ge-0/0/2 interface is used for the ICL.
-
Configure the loopback interfaces.
[edit] user@host# set interfaces lo0 description "untrust" unit 0 family inet address 10.11.0.1/32 user@host# set interfaces lo0 description "untrust" unit 0 family inet address 10.11.0.2/32 user@host# set interfaces lo0 description "untrust" unit 0 family inet address 10.11.0.3/32
Assign the IP address (10.11.0.1) to the loopback interface. This IP address acts as the floating IP address.
Using the loopback interface ensures that at any given point, traffic from the adjacent routers will be steered toward the floating IP address (that is, toward the active node).
- Configure the security policies.
[edit] user@host# set security policies default-policy permit-all user@host# set security policies global policy All match source-address any user@host# set security policies global policy All match destination-address any user@host# set security policies global policy All match application any user@host# set security policies global policy All then permit
Ensure you have configured security policies as per your network requirements. In this example, you'll configure a policy to permit all traffic.
-
Configure security zones, assign interfaces to the zones, and specify the allowed system services for the security zones.
[edit] user@host# set security zones security-zone untrust host-inbound-traffic system-services ike user@host# set security zones security-zone untrust host-inbound-traffic system-services ping user@host# set security zones security-zone untrust host-inbound-traffic protocols bfd user@host# set security zones security-zone untrust host-inbound-traffic protocols bgp user@host# set security zones security-zone untrust interfaces ge-0/0/4 user@host# set security zones security-zone untrust interfaces lo0.0 user@host# set security zones security-zone trust host-inbound-traffic system-services all user@host# set security zones security-zone trust host-inbound-traffic protocols all user@host# set security zones security-zone trust interfaces ge-0/0/3 user@host# set security zones security-zone halink host-inbound-traffic system-services ike user@host# set security zones security-zone halink host-inbound-traffic system-services ping user@host# set security zones security-zone halink host-inbound-traffic system-services high-availability user@host# set security zones security-zone halink host-inbound-traffic system-services ssh user@host# set security zones security-zone halink host-inbound-traffic protocols bfd user@host# set security zones security-zone halink host-inbound-traffic protocols bgp user@host# set security zones security-zone halink interfaces ge-0/0/2
Assign the interfaces ge-0/0/3 and ge-0/0/4 to the
trustanduntrustzones respectively. Assign the lo0.0 interface to the untrust zone to connect over the public IP network. Assign the interface ge-0/0/2 to the halink zone. You use this zone to set up the ICL. -
Configure routing options.
[edit] user@host# set routing-options autonomous-system 65000 user@host# set routing-options static route 10.4.0.0/16 next-hop 10.2.0.2 user@host# set routing-options static route 10.111.0.2 next-hop 10.2.0.2
-
Configure both local node and peer node details such as node ID, lP addresses of the local node and peer node, and the interface for the peer node.
[edit] user@host# set chassis high-availability local-id 1 user@host# set chassis high-availability local-id local-ip 10.22.0.1 user@host# set chassis high-availability peer-id 2 peer-ip 10.22.0.2 user@host# set chassis high-availability peer-id 2 interface ge-0/0/2.0
You'll use the ge-0/0/2 interface for communicating with the peer node using the ICL.
-
Attach the IPsec VPN profile IPSEC_VPN_ICL to the peer node.
[edit] user@host# set chassis high-availability peer-id 2 vpn-profile IPSEC_VPN_ICL
You'll need this configuration to establish a secure ICL link between the nodes.
-
Configure Bidirectional Forwarding Detection (BFD) protocol options for the peer node.
[edit] user@host# set chassis high-availability peer-id 2 liveness-detection minimum-interval 400 user@host# set chassis high-availability peer-id 2 liveness-detection multiplier 5
-
Associate the peer node ID 2 to the services redundancy group 0 (SRG0).
[edit] user@host# set chassis high-availability services-redundancy-group 0 peer-id 2
-
Configure the services redundancy group 1 (SRG1).
[edit] user@host# set chassis high-availability services-redundancy-group 1 deployment-type hybrid user@host# set chassis high-availability services-redundancy-group 1 peer-id 2 user@host# set chassis high-availability services-redundancy-group 1 virtual-ip 1 ip 10.1.0.200/16 user@host# set chassis high-availability services-redundancy-group 1 virtual-ip 1 interface ge-0/0/3.0 user@host# set chassis high-availability services-redundancy-group 1 virtual-ip 1 use-virtual-mac
Assign a virtual IP (VIP) address and an interface for SRG1.
Note: Configuring theuse-virtual-macoption is the recommended option in most cases, except where the surrounding infrastructure would not support a moving virtual MAC address active on a port in addition to the local MAC address. -
Configure IP and BFD monitoring parameters for SRG1 to check the reachability of an IP address and to detect failures in network.
[edit] user@host# set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 user@host# set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 user@host# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.2.0.2 src-ip 10.2.0.1 user@host# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.2.0.2 session-type singlehop user@host# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.2.0.2 interface ge-0/0/4.0
You can configure BFD liveliness by specifying source and destination IP addresses and the interface connecting to the peer device.
For IP monitoring, specify the interfaces used for connecting the neighboring router and switch. -
Configure an active signal route required for activeness enforcement.
[edit] user@host# set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 user@host# set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 user@host# set chassis high-availability services-redundancy-group 1 preemption user@host# set chassis high-availability services-redundancy-group 1 activeness-priority 200
The active signal route IP address you assign is used for route preference advertisement.
Note: You must specify the active signal route along with the route-exists policy in the policy-options statement. When you configure theactive-signal-routewithif-route-existscondition, the HA module adds this route to the routing table. -
Configure policy options.
[edit] user@host# set policy-options condition active_route_exists if-route-exists address-family inet 10.39.1.1 table inet.0 user@host# set policy-options condition backup_route_exists if-route-exists address-family inet 10.39.1.2 table inet.0 user@host# set policy-options policy-statement mnha-route-policy term 1 from protocol static user@host# set policy-options policy-statement mnha-route-policy term 1 from protocol direct user@host# set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists user@host# set policy-options policy-statement mnha-route-policy term 1 then accept metric 10 user@host# set policy-options policy-statement mnha-route-policy term 2 from protocol static user@host# set policy-options policy-statement mnha-route-policy term 2 from protocol direct user@host# set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists user@host# set policy-options policy-statement mnha-route-policy term 2 then accept metric 20 user@host# set policy-options policy-statement mnha-route-policy term 3 from protocol static user@host# set policy-options policy-statement mnha-route-policy term 3 from protocol direct user@host# set policy-options policy-statement mnha-route-policy term 3 then accept metric 30 user@host# set policy-options policy-statement mnha-route-policy term default then reject
-
Configure BFD peering sessions options and specify liveness detection timers.
[edit] user@host# set protocols bgp group untrust type internal user@host# set protocols bgp group untrust local-address 10.2.0.1 user@host# set protocols bgp group untrust export mnha-route-policy user@host# set protocols bgp group untrust neighbor 10.2.0.2 user@host# set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 user@host# set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 user@host# set protocols bgp group untrust bfd-liveness-detection multiplier 3 user@host# set protocols bgp group untrust local-as 65000
-
Define Internet Key Exchange (IKE) configuration for Multinode High Availability. An IKE configuration defines the algorithms and keys used to establish a secure connection.
[edit] user@host# set security ike proposal MNHA_IKE_PROP description mnha_link_encr_tunnel user@host# set security ike proposal MNHA_IKE_PROP authentication-method pre-shared-keys user@host# set security ike proposal MNHA_IKE_PROP dh-group group14 user@host# set security ike proposal MNHA_IKE_PROP authentication-algorithm sha-256 user@host# set security ike proposal MNHA_IKE_PROP encryption-algorithm aes-256-cbc user@host# set security ike proposal MNHA_IKE_PROP lifetime-seconds 3600 user@host# set security ike policy MNHA_IKE_POL description mnha_link_encr_tunnel user@host# set security ike policy MNHA_IKE_POL proposals MNHA_IKE_PROP user@host# set security ike policy MNHA_IKE_POL pre-shared-key ascii-text "$ABC123" user@host# set security ike gateway MNHA_IKE_GW ike-policy MNHA_IKE_POL user@host# set security ike gateway MNHA_IKE_GW version v2-only
v2-only. -
Specify the IPsec proposal protocol and encryption algorithm. Specify IPsec options to create a IPsec tunnel between two participant devices to secure VPN communication.
[edit] user@host# set security ipsec proposal MNHA_IPSEC_PROP description mnha_link_encr_tunnel user@host# set security ipsec proposal MNHA_IPSEC_PROP protocol esp user@host# set security ipsec proposal MNHA_IPSEC_PROP encryption-algorithm aes-256-gcm user@host# set security ipsec proposal MNHA_IPSEC_PROP lifetime-seconds 3600 user@host# set security ipsec policy MNHA_IPSEC_POL description mnha_link_encr_tunnel user@host# set security ipsec policy MNHA_IPSEC_POL proposals MNHA_IPSEC_PROP user@host# set security ipsec vpn IPSEC_VPN_ICL ha-link-encryption user@host# set security ipsec vpn IPSEC_VPN_ICL ike gateway MNHA_IKE_GW user@host# set security ipsec vpn IPSEC_VPN_ICL ike ipsec-policy MNHA_IPSEC_POL
The same VPN name IPSEC_VPN_ICL must be mentioned for vpn_profile in chassis high availability configuration. Specifying the
ha-link-encryptionoption encrypts the ICL to secure high availability traffic flow between the nodes.
Configuration Options for Software Upgrades
In Multinode High Availability, during software upgrade, you can divert the traffic by closing down interfaces on the node. Here, traffic cannot pass through the nodes. Check Software Upgrade in Multinode High Availability for details.
- Configure all traffic interfaces under “shutdown-on-failure” option.
user@srx-02# set chassis high-availability services-redundancy-group 0 shutdown-on-failure <interface-name>
[edit] user@srx-02# set chassis high-availability services-redundancy-group 0 shutdown-on-failure ge-0/0/3 user@srx-02# set chassis high-availability services-redundancy-group 0 shutdown-on-failure ge-0/0/4
CAUTION:Do not use interfaces assigned for the interchassis link (ICL).
Results (SRX-1)
From configuration mode, confirm your configuration by entering the following commands. If the output does not display the intended configuration, repeat the configuration instructions in this example to correct it.
[edit]
user@host# show chassis high-availability
local-id 1 local-ip 10.22.0.1;
peer-id 2 {
peer-ip 10.22.0.2;
interface ge-0/0/2.0;
vpn-profile IPSEC_VPN_ICL;
liveness-detection {
minimum-interval 400;
multiplier 5;
}
}
services-redundancy-group 0 {
peer-id {
2;
}
}
services-redundancy-group 1 {
deployment-type hybrid;
peer-id {
2;
}
virtual-ip 1 {
ip 10.1.0.200/16;
interface ge-0/0/3.0;
}
monitor {
bfd-liveliness 10.2.0.2 {
src-ip 10.2.0.1;
session-type singlehop;
interface ge-0/0/4.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
preemption;
activeness-priority 200;
}
[edit]
user@host# show security ike
proposal MNHA_IKE_PROP {
description mnha_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy MNHA_IKE_POL {
description mnha_link_encr_tunnel;
proposals MNHA_IKE_PROP ;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway MNHA_IKE_GW {
ike-policy MNHA_IKE_POL ;
version v2-only;
}
[edit]
user@host# show security ipsec
proposal MNHA_IPSEC_PROP {
description mnha_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy MNHA_IPSEC_POL {
description mnha_link_encr_tunnel;
proposals MNHA_IPSEC_PROP;
}
vpn IPSEC_VPN_ICL {
ha-link-encryption;
ike {
gateway MNHA_IKE_GW;
ipsec-policy MNHA_IPSEC_POL;
}
}
[edit]
user@host# show policy-options
policy-statement mnha-route-policy {
term 1 {
from {
protocol [ static direct ];
condition active_route_exists;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
protocol [ static direct ];
condition backup_route_exists;
}
then {
metric 20;
accept;
}
}
term 3 {
from protocol [ static direct ];
then {
metric 30;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
user@host# show routing-options
autonomous-system 65000;
static {
route 10.4.0.0/16 next-hop 10.2.0.2;
route 10.111.0.2/32 next-hop 10.2.0.2;
}
[edit]
user@host# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/4.0;
lo0.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/3.0;
}
}
security-zone halink {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@host# show interfaces
ge-0/0/2 {
description ha_link;
unit 0 {
family inet {
address 10.22.0.1/24;
}
}
}
ge-0/0/3 {
description trust;
unit 0 {
family inet {
address 10.1.0.1/16;
}
}
}
ge-0/0/4 {
description untrust;
unit 0 {
family inet {
address 10.2.0.1/16;
}
}
}
lo0 {
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
address 10.11.0.2/32;
address 10.11.0.3/32;
}
}
}
If you are done configuring the device, enter commit from
configuration mode.
Results (SRX-2)
From configuration mode, confirm your configuration by entering the following commands. If the output does not display the intended configuration, repeat the configuration instructions in this example to correct it.
[edit]
user@host# show chassis high-availability
local-id 2 local-ip 10.22.0.2;
peer-id 1 {
peer-ip 10.22.0.1;
interface ge-0/0/2.0;
vpn-profile IPSEC_VPN_ICL;
liveness-detection {
minimum-interval 400;
multiplier 5;
}
}
services-redundancy-group 0 {
peer-id {
1;
}
}
services-redundancy-group 1 {
deployment-type hybrid;
peer-id {
1;
}
virtual-ip 1 {
ip 10.1.0.200/16;
interface ge-0/0/3.0;
use-virtual-mac;
}
monitor {
bfd-liveliness 10.3.0.2 {
src-ip 10.3.0.1;
session-type singlehop;
interface ge-0/0/4.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
activeness-priority 1;
}
[edit]
user@host# show security ike
proposal MNHA_IKE_PROP {
description mnha_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy MNHA_IKE_POL {
description mnha_link_encr_tunnel;
proposals MNHA_IKE_PROP ;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway MNHA_IKE_GW {
ike-policy MNHA_IKE_POL ;
version v2-only;
}
[edit]
user@host# show security ipsec
proposal MNHA_IPSEC_PROP {
description mnha_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy MNHA_IPSEC_POL {
description mnha_link_encr_tunnel;
proposals MNHA_IPSEC_PROP;
}
vpn IPSEC_VPN_ICL {
ha-link-encryption;
ike {
gateway MNHA_IKE_GW;
ipsec-policy MNHA_IPSEC_POL;
}
}
[edit]
user@host# show policy-options
route-filter-list loopback {
10.11.0.0/24 orlonger;
}
route-filter-list ipsec {
10.4.0.0/16 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
protocol [ static direct ];
condition active_route_exists;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
protocol [ static direct ];
condition backup_route_exists;
}
then {
metric 20;
accept;
}
}
term 3 {
from protocol [ static direct ];
then {
metric 35;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@host# show routing-options
autonomous-system 65000;
static {
route 10.4.0.0/16 next-hop 10.3.0.2;
route 10.111.0.2/32 next-hop 10.3.0.2;
}
[edit]
user@host# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/4.0;
lo0.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/3.0;
}
}
security-zone halink {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@host# show interfaces
[edit]
root@10.52.45.32# show interfaces
ge-0/0/2 {
description ha_link;
unit 0 {
family inet {
address 10.22.0.2/24;
}
}
}
ge-0/0/3 {
description trust;
unit 0 {
family inet {
address 10.1.0.2/16;
}
}
}
ge-0/0/4 {
description untrust;
unit 0 {
family inet {
address 10.3.0.1/16;
}
}
}
lo0 {
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
address 10.11.0.2/32;
address 10.11.0.3/32;
}
}
}
If you are done configuring the device, enter
commit from configuration mode.
user@host# commit warning: High Availability Mode changed, please reboot the device to avoid undesirable behavior commit complete
Verification
Confirm that the configuration is working properly.
- Check Multinode High Availability Details
- Check Multinode High Availability Peer Node Status
- Check Multinode High Availability Service Redundancy Groups
- Verify the Multinode High Availability Status Before and After Failover
- Verify Interchassis Link (ICL) Encryption Status
- Verify Link Encryption Tunnel Statistics
Check Multinode High Availability Details
Purpose
View and verify the details of the Multinode High Availability setup configured on your security device.
Action
From operational mode, run the following command:
On SRX-1
user@host> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.1
HA Peer Information:
Peer Id: 2 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: HYBRID
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
On SRX-2
user@host> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.2
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: HYBRID
Status: BACKUP
Activeness Priority: 1
Preemption: DISABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Meaning
Verify these details from the command output:
-
Local node and peer node details such as IP address and ID.
-
The field
Encrypted: YESindicates that the traffic is protected. -
The field
Deployment Type: HYBRIDindicates a hybrid mode configuration—that is, the network has a router on one side and a switch on the other. -
The field
Services Redundancy Group: 1indicates the status of the SRG1 (ACTIVE or BACKUP) on that node.
Check Multinode High Availability Peer Node Status
Purpose
View and verify the peer node details.
Action
From operational mode, run the following command:
SRX-1
user@host> user@host> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 2 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.1
Internal Peer-IP: 180.100.1.2
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 3 2
SRG Status Ack 2 3
Attribute Msg 4 2
Attribute Ack 2 1
SRX-2
user@host> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 1 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.2
Internal Peer-IP: 180.100.1.1
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 2 3
SRG Status Ack 3 2
Attribute Msg 3 1
Attribute Ack 1 2
Meaning
Verify these details from the command output:
-
Peer node details such as interface used, IP address, and ID
-
Encryption status, connection status, and cold synchronization status
-
Packet statistics across the node.
Check Multinode High Availability Service Redundancy Groups
Purpose
Verify that the SRGs are configured and working correctly.
Action
From operational mode, run the following command:
For SRG0:
user@host> show chassis high-availability services-redundancy-group 0
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 2
For SRG1:
user@host> show chassis high-availability services-redundancy-group 1 >
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: HYBRID
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: NOT INSTALLED
Virtual IP Info:
Index: 1
IP: 10.1.0.200/16
VMAC: N/A
Interface: ge-0/0/3.0
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.1.0.200
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.2.0.2 DST-IP: 10.2.0.1
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/4.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
Meaning
Verify these details from the command output:
-
Peer node details such as deployment type, status, and active and back up signal routes.
-
Virtual IP Information such as IP address and virtual MAC address.
-
IP monitoring and BFD monitoring status.
Verify the Multinode High Availability Status Before and After Failover
Purpose
Check the change in node status before and after failover in a Multinode High Availability setup.
Action
To check the Multinode High Availability status on the backup node (SRX-2), run the following command from operational mode:
user@host> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.2
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: HYBRID
Status: BACKUP
Activeness Priority: 1
Preemption: DISABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/AUnder the Services Redundancy Group: 1 section, you can see the
Status: BACKUP field. This field value indicates that the
status of SRG 1 is backup.
Initiate the failover on the active node (SRX-1 device) and again run the command on the backup node (SRX-2).
user@host> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.2
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: DOWN
Cold Sync Status: IN PROGRESS
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: HYBRID
Status: ACTIVE
Activeness Priority: 1
Preemption: DISABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: READYNote that under the Services Redundancy Group: 1 section, the
status of SRG1 has changed from BACKUP to
ACTIVE.
You can also see peer node details under the Peer Information
section. The output shows the status of peer as
BACKUP.
Verify Interchassis Link (ICL) Encryption Status
Purpose
Verify the interchassis link (ICL) status.
Action
From operational mode, run the following command:
user@host> show security ipsec security-associations ha-link-encryption detail
ID: 495003 Virtual-system: root, VPN Name: IPSEC_VPN_ICL
Local Gateway: 10.22.0.1, Remote Gateway: 10.22.0.2
Traffic Selector Name: __IPSEC_VPN_ICL__multi_node__
Local Identity: ipv4(180.100.1.1-180.100.1.1)
Remote Identity: ipv4(180.100.1.2-180.100.1.2)
TS Type: traffic-selector
Version: IKEv2
PFS group: N/A
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.16000, Tunnel MTU: 0, Policy-name: MNHA_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
HA Link Encryption Mode: Multi-Node
Location: FPC -, PIC -, KMD-Instance -
Anchorship: Thread -
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x00022d84, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3395 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2794 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 4294966277
Direction: outbound, SPI: 0x00028296, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3395 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2794 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 4294966277
Meaning
The command output provides the following information:
-
The local gateway and remote gateway details.
-
The IPsec SA pair for each threads in PIC.
-
HA link encryption mode (as shown in the following line):
HA Link Encryption Mode: Multi-Node -
Authentication and encryption algorithms used
The IP range (180.100.1.x) shown in the command output serves as the ICL IPsec traffic selector. The system dynamically assigns this IP range, and it is essential not to alter or modify it. Additionally, BFD (Bidirectional Forwarding Detection) will be automatically enabled for the broader 180.x.x.x IP range.
Verify Link Encryption Tunnel Statistics
Purpose
Verify link encryption tunnel statistics on both active and backup nodes.
Action
From operational mode, run the following command:
user@host> show security ipsec statistics ha-link-encryption ESP Statistics: Encrypted bytes: 984248 Decrypted bytes: 462519 Encrypted packets: 9067 Decrypted packets: 8797 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Meaning
If you see packet loss issues across a VPN, you can run the show
security ipsec statistics ha-link-encryption command several
times to verify that the encrypted and decrypted packet counters are
incrementing. You should also check whether the other error counters are
incrementing.
Use the show security ike active-peer ha-link-encryption
command to display details of ICL on the active peer node.
Use the clear security ipsec statistics ha-link-encryption
command to clear all IPsec statistics.
