Junos OS Overview
Junos OS is the single operating system that powers Juniper’s broad portfolio of physical and virtual networking and security products.
Junos OS Overview
Juniper Networks provides high-performance network devices that create a responsive and trusted environment for accelerating the deployment of services and applications over a single network. The Junos® operating system (Junos OS) is the foundation of these high-performance networks.
Junos OS includes the following architecture variations:
-
Junos OS FreeBSD 10 or later on bare metal. This is Junos OS based on an upgraded FreeBSD kernel. Most Junos OS-based hardware platforms run Junos OS with upgraded FreeBSD. Junos OS with upgraded FreeBSD can run also as a guest virtual machine (VM) on a Linux VM host. For more on which platforms run Junos OS with upgraded FreeBSD, search for Junos kernel upgrade to FreeBSD 10+ in Feature Explorer: Junos kernel upgrade to FreeBSD 10+.
-
Junos OS Evolved. See Introducing Junos® OS Evolved and the Junos® OS Evolved Software Installation and Upgrade Guide for more information about Junos OS Evolved.
Unlike other complex, monolithic software architectures, Junos OS incorporates key design and developmental differences to deliver increased network availability, operational efficiency, and flexibility. The following are key advantages to this approach:
- One Operating System
- One Modular Software Architecture
- Secure Boot and Bootloader
- Hardware Root of Trust
- FIPS 140-2 Security Compliance
One Operating System
Unlike other network operating systems that share a common name but splinter into many different programs, Junos OS is a single, cohesive operating system that is shared across all network devices and product lines. This allows Juniper Networks engineers to develop software features once and share these features across all product lines simultaneously. Because features are common to a single source, they generally are implemented the same way for all product lines, thus reducing the training required to learn different tools and methods for each product. Because all Juniper Networks products use the same code base, interoperability between products is not an issue.
One Modular Software Architecture
Although individual modules of Junos OS communicate through well-defined interfaces, each module runs in its own protected memory space, preventing one module from disrupting another. This separation enables the independent restart of each module as necessary. This is in contrast to monolithic operating systems where a malfunction in one module can ripple to other modules and cause a full system crash or restart. This modular architecture then provides for high performance, high availability, security, and device scalability not found in other operating systems.
The Junos OS is preinstalled on your Juniper Networks device when you receive it from the factory. Thus, when you first power on the device, all software starts automatically. You simply need to configure the software so that the device can participate in the network.
You can upgrade the device software as new features are added or software problems are fixed. You normally obtain new software by downloading the software installation packages from the Juniper Networks Support Web page onto your device or onto another system on your local network. You then install the software upgrade onto the device.
Juniper Networks routing platforms run only binaries supplied by Juniper Networks, and currently do not support third-party binaries. Each Junos OS image includes a digitally signed manifest of executables that are registered with the system only if the signature can be validated. Junos OS will not execute any binary without a registered signature. This feature protects the system against unauthorized software and activity that might compromise the integrity of your device.
Secure Boot and Bootloader
The system's boot-up process involves several stages, starting with the activation of the CPU as the boot processor, communicating with the PCH to bring up the system. The CPU jumps to the BIOS routine stored in the Primary SPI flash. In case of Primary flash failure, the boot FPGA switches to the Secondary flash for recovery, but it does not load the bootloader.
The bootloader plays a critical role in the system's boot-up process, ensuring secure and orderly execution of the operating system. The boot order and mechanisms like Secure Boot, USB, SSD, and PXE boot provide flexibility and resilience to the system's startup procedure. Additionally, GRUB configurations allow users to customize and troubleshoot the boot process as needed
Secure Boot is a significant system security enhancement based on the UEFI standard (see the Unified Extensible Firmware Interface Forum website). It works by safeguarding the BIOS itself from tampering or modification and then maintaining that protection throughout the boot process.
The Secure Boot process begins with Secure Flash, which ensures that unauthorized changes cannot be made to the firmware. Authorized releases of Junos OS carry a digital signature produced by either Juniper Networks directly or one of its authorized partners. At each point of the boot-up process, each component verifies the next link is sound by checking the signature to ensure that the binaries have not been modified. The boot process cannot continue unless the signature is correct. This "chain of trust" continues until the operating system takes control. In this way, overall system security is enhanced, increasing resistance to some firmware-based persistent threats.
Figure 1 shows a simplified version of this “chain of trust.”
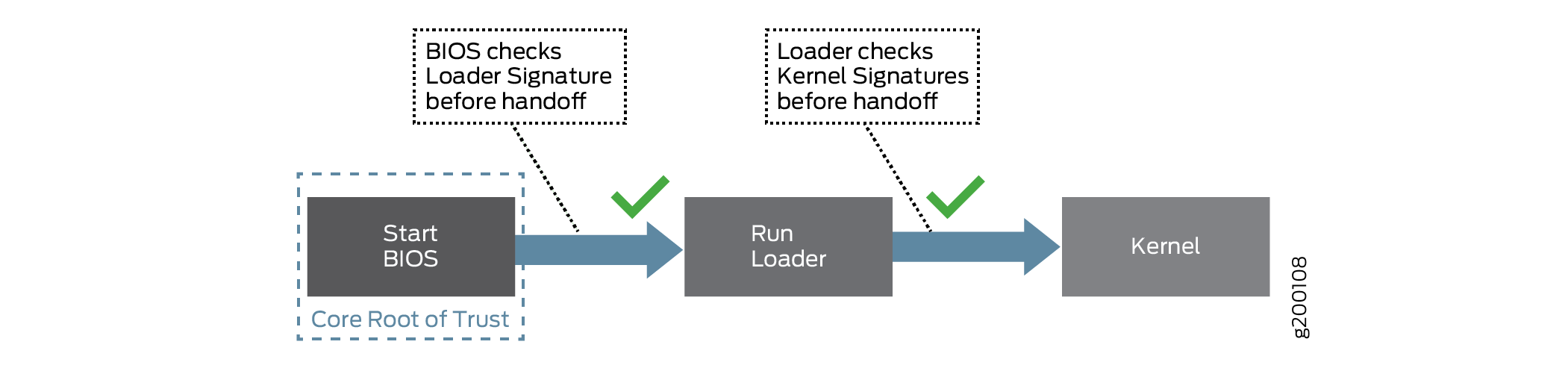
Secure Boot requires no actions on your part to implement. It is implemented on supported hardware by default.
For information on which Junos OS releases and hardware support Secure Boot, see Feature Explorer and enter Secure Boot.
Considerations for SRX Series Firewalls
Secure Boot for SRX Series Firewalls serves as a critical security mechanism designed to protect Juniper hardware and thwart the execution of unauthorized code or data. Unauthorized entities are defined as those lacking a proper Juniper digital signature or that of its authorized affiliates.
Here's a concise breakdown of how Secure Boot operates specifically for SRX1600, SRX2300, SRX4120, SRX4300 and SRX4700 devices:
-
Power-Up Sequence: Upon powering up, the CPU initiates execution with the UEFI BIOS.
-
Boot Loader: The UEFI BIOS loads the signed PE/COFF32+ executable \EFI\BOOT\BOOTX64.EFI. This executable contains a modified GRUB2, which allows only file read I/O to files with proper detached signatures.
-
Detached Signatures: GRUB2 detached signatures are stored as ${object}.psig, utilizing a binary (non-armored) OpenPGP format.
-
GPG Key Storage: Additional GPG Keys, in conjunction with the trusted GPG public key compiled into GRUB2, may be stored in \EFI\BOOT\grub-trusted.gpg.
-
Trust Establishment: Trust in \EFI\BOOT\grub-trusted.gpg is established by verifying \EFI\BOOT\grub-trusted.gpg.psig using the grub-root key embedded in \EFI\BOOT\BOOTX64.EFI.
-
GRUB2 Configuration: The GRUB2 startup configuration, located in \EFI\BOOT\grub-startup.cfg, is responsible for loading the signed Linux kernel and, optionally, a signed initrd image.
-
File Loading Restrictions: BOOTX64.EFI consistently insists on properly signed files and refrains from loading any unsigned files, excluding GRUB config or GRUB environment files.
Installation and Activation
To enable Secure Boot for SRX2300 and SRX4120 devices, navigate to the BIOS menu and select Restore Secure Boot to Factory Settings under the Administer Secure Boot menu.
Once Secure Boot is enabled, it cannot be disabled.
Hardware Root of Trust
Hardware root of trust (HRoT) is a hardware-based security feature integrated in the system, which acts as a trusted foundation to verify the integrity of the firmware and ensure its secure operation. This feature provides an unalterable root of trust starting from the hardware, protecting against potential security vulnerabilities within the system. HRoT acts as a critical component for guaranteeing the authenticity of the system firmware and configuration.
Unlike software-based trust mechanisms, HRoT is implemented directly in the hardware, making it highly resistant to tampering. The primary function of HRoT is to verify the integrity of the firmware, ensuring it hasn't been compromised or modified unauthorizedly. This feature is used to implement a secure boot process where only verified and trusted firmware can be loaded.
Ensure the following message is displayed during the early bootstrap of the device to know that HRoT and secure boot are enforced.
JUNIPER HARDWARE ROOT OF TRUST WITH SECURE BOOT ENFORCED
FIPS 140-2 Security Compliance
For advanced network security, a special version of Junos OS, called Junos-FIPS 140-2, is available. Junos-FIPS 140-2 provides customers with software tools to configure a network of Juniper Networks devices in a FIPS environment. FIPS support includes:
Upgrade package to convert Junos OS to Junos-FIPS 140-2
Revised installation and configuration procedures
Enforced security for remote access
FIPS user roles (Crypto Officer, User, and Maintenance)
FIPS-specific system logging and error messages
IPsec configuration for Routing Engine–to–Routing Engine communication
Enhanced password creation and encryption
Junos-FIPS is packaged in a domestic image only: a single Junos OS image supports both domestic and FIPS features. Users that have the FIPS credentials and permission to login can flip between a regular Junos image and FIPS image.
Junos-FIPS has special password requirements. FIPS passwords must be between 10 and 20 characters in length. Passwords must use at least three of the five defined character sets (uppercase letters, lowercase letters, digits, punctuation marks, and other special characters). If Junos-FIPS is installed on the device, you cannot configure passwords unless they meet this standard.
