Virtualized Data Center Using Logical Systems
Logical Systems enables VDC design uses virtualization technologies such as virtual LANs (VLANs), virtual routers, virtual route forwarders, inter-virtual route forwarding to provide flexible traffic isolation. For more information, see the following topics:
Two-Tiered Virtualized Data Center Solution for Large Enterprise Networks
The following describes a Juniper Networks two-tiered, high-speed, multiservice virtualized data center (VDC). A two-tiered architecture meets the low latency requirements of a virtualized server environment and supports the overlying security mandate to maintain controlled segmentation between various business units.
- Network Traffic Segmentation
- Flexibility
- Security
- Access and Availability
- Cost-Effective Incremental Scaling
- Orchestration and Automation
Network Traffic Segmentation
Juniper Networks VDC design uses virtualization technologies such as virtual LANs (VLANs), virtual routers, virtual route forwarders, inter-virtual route forwarding, and logical systems to provide flexible traffic isolation.
A fully redundant two-tiered data center design consists of Juniper Networks EX Series Ethernet Switches at the access layer for server connectivity, MX Series 5G Universal Routing Platforms as a collapsed LAN aggregation/core layer, and clustered SRX Series Firewalls to provide firewall security services across the data center trust boundaries.
Flexibility
The Juniper Networks VDC design uses 802.1Q VLANs, MPLS, BGP, Virtual Router Redundancy Protocol (VRRP), Traffic Engineering, and Fast Reroute to provide design flexibility while maintaining a standards-based approach. The design can also support a virtual private LAN service (VPLS).
Security
The Juniper Networks VDC design uses security zones to implement the policy enforcement points. The SRX cluster is responsible for all stateful packet inspection for traffic that crosses business unit trust boundaries as well as all ingress and egress traffic for the data center.
The Juniper Networks Junos operating system is configured with different administrator accounts for each logical system that supports confined access to network resources and can be customized for individual business units.
Access and Availability
In the Juniper Networks VDC design, described in Example: Configuring a Two-Tiered Virtualized Data Center for Large Enterprise Networks, top-of-rack (TOR) EX Series switches provide access to the servers and provide redundancy.
All uplinks from the TOR switches are 802.1Q trunk links that are terminated directly into each of the MX Series devices that make up the Point of Delivery (POD) at the aggregation/core layer.
A VRRP instance is defined on each VLAN within the MX Series device to act as the default router for all server hosts in a given VLAN. To allow for VRRP to work properly, each bridge domain is extended between each MX Series device through an interconnection link. The MX Series device uses an integrated routing and bridging (IRB) interface as the Layer 3 interface for each bridge domain, with VRRP configured for redundancy.
A pair of 802.3ad aggregated Ethernet bundles are used between the MX Series devices. Each MX Series device is divided into a number of Logical Systems. Logical systems in the MX Series device are used to define logical trust boundaries within the data center itself and between respective business units.
A clustered pair of SRX Series Firewalls acting as firewalls provide security services across the data center trust boundaries. Virtual routers on the SRX Series Firewalls act as customer edge (CE) routers for each business unit.
A single redundancy group for the data plane is defined on the SRX Series Firewalls with two redundant Ethernet interfaces as member interfaces. This redundancy group handles the data plane failover of the SRX Series firewall and is configured such that any loss of either northbound or southbound SRX Series interfaces forces a full failover to the secondary node. This failover is essentially a Layer 1 failover, which means that it occurs quickly and does not disrupt the routing topology above it.
Cost-Effective Incremental Scaling
The Juniper Networks VDC design supports incremental scaling of the network. This allows the VDC to be created with minimum cost to meet the current need.
The access layer can be expanded by adding EX Series switches at the top of rack.
The aggregation/core layer can be expanded by adding additional MX Series devices within a given POD.
The security services can be expanded by adding 4-port 10-Gigabit Ethernet I/O cards (IOCs) and services processing cards (SPCs) in the SRX Series Firewalls. The addition of IOCs increases the 10-Gigabit Ethernet port density. The addition of each SPC card to the chassis adds another 10 Gbps (5 Gbps Internet mix (IMIX)), 2 million sessions, and 100,000 connections per second (CPS) up to a maximum rated capacity for the platform of 150 Gbps (47.5 Gbps IMIX), 10 million sessions, and 350,000 CPS (as measured in Junos OS Release 10.2).
Orchestration and Automation
The Juniper Networks VDC design uses the Juniper Networks Junos Space management platform. Junos Space includes a portfolio of applications for scaling services, simplifying network operations, and automating support for complex network environments.
In addition, the network devices are configured to support background Secure Copy Protocol (SCP) file transfers, commit scripts, and a file archive site.
See Also
Requirements of a Two-Tiered Virtualized Data Center for Large Enterprise Networks
Large enterprises have certain specific needs for the hosting environment that the design of their data center must meet. This section describes the requirements of a company that operates as a service provider to its individual business units (BUs).
One of the primary requirements of a virtualized data center (VDC) for a large enterprise is the ability to segment the network by business unit. This includes traffic segmentation and administrative control segmentation.
Other requirements include security controls between business units, security controls between the company and the outside world, flexibility to grow and adapt the network, and a robust and cost-effective way to manage the entire network.
- Network Traffic Segmentation
- Flexibility
- Security
- Access and Availability
- Cost-Effective Incremental Scaling
- Orchestration and Automation
Network Traffic Segmentation
The requirement described here is for network resources to be isolated in several ways. Traffic must be segmented by business units. Traffic flows between network segments must be prohibited except where specifically allowed. Traffic isolation must be controlled at designated policy enforcement points. Network resources must be dedicated to a segment, but the network must have the flexibility to change the allocation of resources.
Segmented resources must be logically grouped according to policies. For example, test traffic must be isolated from production traffic. Traffic must also be isolated according to business entities, contractual requirements, legal or regulatory requirements, risk rating, and corporate standards.
The network segmentation design must not be disruptive to the business, must be integrated with the larger data center and cloud network design, must allow business units to access network resources globally, and must support new business capabilities.
Flexibility
The network design must be flexible enough to react to business and environment changes with minimal design and re-engineering efforts. The VDC design must be flexible in terms of isolating business unit workloads from other business units and general data center services and applications. The network solution must ensure that the business is minimally impacted when network and segmentation changes take place.
The VDC must be flexible enough to be implemented:
Within a single data center
Within a data hall
Across two or more data centers
Across two or more data halls within or between data centers
Between a data center and an external cloud service provider
Security
The network design must allow business units to be isolated within the hosting environment. In the event of a network security incident, business units must be isolated from the hosting environment and other business units.
Traffic flow between business unit segments must be denied by default and must be explicitly permitted only at policy enforcement points owned and controlled by the data center service provider.
The policy enforcement point must include access control capabilities and might include threat protection capabilities.
Access and Availability
The VDC must provide access to common data center services such as computation, storage, security, traffic management, operations, and applications. The network must operate across multiple global service providers and must deliver optimal, predictable, and consistent performance across the network. The VDC must be implemented across data center business units.
The network solution must meet business unit availability requirements as defined in service-level agreements.
Cost-Effective Incremental Scaling
The VDC design must be cost effective for the business to run and must enable new business capabilities. It must be possible to implement the network solution in an incremental manner with minimal impact to the business.
Orchestration and Automation
The VDC design must include a management system that supports automation for provisioning, availability and workload monitoring, and reporting. Workload and availability reports must be available by business unit.
See Also
Example: Configuring a Two-Tiered Virtualized Data Center for Large Enterprise Networks
This example provides a step-by-step procedure for configuring a two-tiered virtualized data center for large enterprise networks.
- Requirements
- Configuring a Two-Tiered Virtualized Data Center Overview
- Configuring the Access Layer
- Configuring the Aggregation Layer in the Trusted Logical Systems
- Configuring the Core Layer in the Untrusted Logical Systems
- Configuring the Security Device
Requirements
This example uses the following hardware and software components:
Two MX Series 5G Universal Routing Platforms running Junos OS Release 10.2 or later
Six EX Series Ethernet Switches running Junos OS Release 10.2 or later
Two SRX Series Firewalls running Junos OS Release 10.4 or later
Configuring a Two-Tiered Virtualized Data Center Overview
This example provides a step-by-step procedure for configuring a two-tiered virtualized data center for large enterprises. The steps in the example follow the data path from an interface connected to a server in BU2 using VLAN 17, to Logical System Trust1, through Virtual Router MX-VR2, through Virtual Router SRX-VR2, through VRF2 in the Logical System Untrust, and out to the core network.
The core network in this example simultaneously supports IP-based routing and MPLS-based label switching. The virtual routers on the SRX Series Firewall perform the functions of customer edge (CE) routers. The VPN routing and forwarding (VRF) routing instances on the MX Series devices perform the functions of service provider edge (PE) routers. The OSPF protocol serves as the interior gateway protocol to carry routes to the PE router loopback addresses that are used as the BGP next-hop address for the IP-based and MPLS-based networks supported by this example.
The steps in this example are representative of the entire network configuration. The example does not show every step for every virtual device.
The physical connections used in this example are shown in Figure 1.
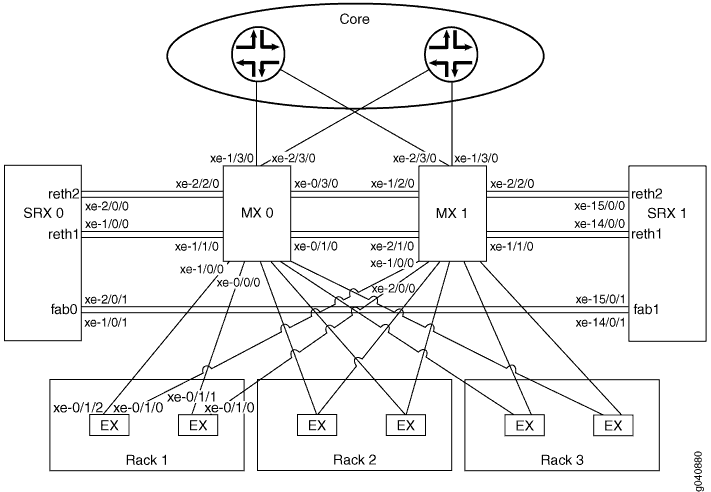
The logical connections used in this example are shown in Figure 2.
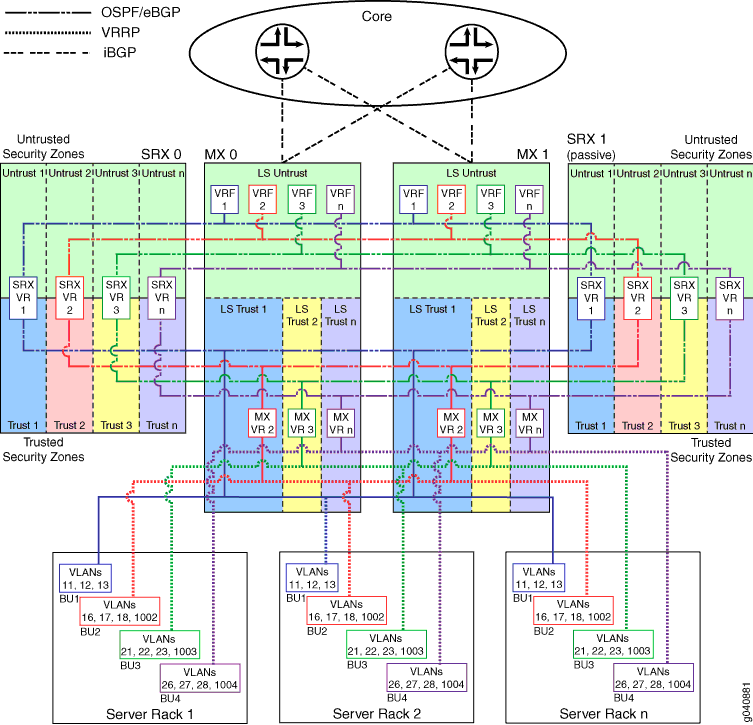
In the logical topology illustration:
Users access the data center across the enterprise core network shown at the top.
Virtual routers configured in Logical System Untrust on the MX Series devices forward the traffic to separate virtual routers configured in the Untrusted security zone on the SRX Series Firewalls. These virtual routers act as edge routers for the various business units.
Virtual routers configured on the active SRX Series Firewall forward the traffic to the Trusted security zones.
Virtual routers configured in separate logical systems on the MX Series devices forward the traffic to a bridge domain of VLANs configured on the EX Series devices.
Business unit 1 requires additional separation. In this case, the virtual router (VR) configured on the SRX Series Firewall forwards the traffic directly to the bridge domain on the EX Series devices.
The EX Series devices switch the traffic to the data center server.
The SRX Series Firewalls apply security policy to all traffic traversing the untrust to trust boundary and all traffic forwarded between logical systems.
The SRX Series Firewalls are configured in an active/passive cluster so that only one node in the cluster is active on the data forwarding plane at a time.
The SRX Series Firewalls are configured with a single redundancy group for the data plane. The redundancy group uses two Ethernet interfaces (
reth1andreth2in Figure 1) as member interfaces.
Configuring the Access Layer
Configure the access layer by doing the following:
- Configuring Interfaces
- Configuring VLANs in the Access Layer
- Configuring a Redundant Trunk Group and Disabling the Spanning Tree Protocol for the Trunk Interfaces
- Configuring Management Automation
Configuring Interfaces
Step-by-Step Procedure
This procedure explains how to configure the physical, logical, and network management interfaces for the access layer devices. This procedure shows a representative sample of the configuration. The example does not show the configuration for every interface.
Configure the access layer server-facing 10-Gigabit Ethernet interfaces.
This example configures the
ge-0/0/17interface with VLAN ID17.Include the
memberstatement and specify VLAN ID17at the[edit interfaces ge-0/0/17 unit 0 family ethernet-switching vlan]hierarchy level.[edit interfaces ge-0/0/17 unit 0] user@ex# set family ethernet-switching vlan members 17
Repeat this step for every server-facing interface by using the appropriate interface name and VLAN number.
Configure the 10-Gigabit Ethernet trunk interfaces from the EX Series device to the two MX Series devices.
This example configures the
xe-0/1/2andxe-0/1/0interfaces.Include the
port-modestatement and specify thetrunkoption at the[edit interfaces xe-0/1/2 unit 0 family ethernet-switching]and[edit interfaces xe-0/1/0 unit 0 family ethernet-switching]hierarchy levels.Include the
membersstatement and specify thealloption at the[edit interfaces xe-0/1/2 unit 0 family ethernet-switching vlan]and[edit interfaces xe-0/1/0 unit 0 family ethernet-switching]hierarchy levels.[edit interfaces xe-0/1/2 unit 0] user@ex# set family ethernet-switching port-mode trunk user@ex# set family ethernet-switching vlan members all
[edit interfaces xe-0/1/0 unit 0] user@ex# set family ethernet-switching port-mode trunk user@ex# set family ethernet-switching vlan members all
Repeat this step for every 10-Gigabit Ethernet trunk interface by using the appropriate interface name.
Enable the IPv4 address family for the loopback logical interface.
Include the
familystatement and specify theinetoption to enable IPv4 at the[edit interfaces lo0 unit 0]hierarchy level.[edit interfaces lo0 unit 0] user@ex# set family inet
Repeat this step for every EX Series device by using the appropriate address for that device.
Configure the EX Series device management Ethernet interface.
This example configures the
unit 0logical interface.Include the
familystatement and specify theinetoption at the[edit me0 unit 0]hierarchy level.Include the
addressstatement and specify10.8.108.19/24as the IPv4 address at the[edit interfaces me0 unit 0 family inet]hierarchy level.[edit interfaces me0 unit 0] user@ex# set family inet address 10.8.108.19/24
Repeat this step for every EX Series device by using the appropriate management interface address for that device.
Configuring VLANs in the Access Layer
Step-by-Step Procedure
This procedure explains how to configure the VLAN names and tag IDs and associate trunk interfaces with one of the access layer devices. This procedure shows a representative sample of the configuration. The example does not show the configuration for every VLAN.
Configure the VLAN name and tag ID (number) for each VLAN on the EX Series device.
This example configures a VLAN with the name
vlan17and tag ID17.Include the
vlan-idstatement and specify17as the VLAN tag ID at the[edit vlans vlan17]hierarchy level.[edit vlans vlan17] user@ex# set vlan-id 17
Repeat this step for every VLAN on each EX Series device by using the appropriate VLAN names and tag IDs.
Associate the logical trunk interfaces with each VLAN on the EX Series device.
This example associates logical interfaces
xe-0/1/0.0andxe-0/1/2.0withvlan17.Include the
interfacestatement and specifyxe-0/1/0.0at the[edit vlans vlan17]hierarchy level.Include the
interfacestatement and specifyxe-0/1/2.0at the[edit vlans vlan17]hierarchy level.[edit vlans vlan17] user@ex# set interface xe-0/1/0.0 user@ex# set interface xe-0/1/2.0
Repeat this step for every VLAN on each EX Series device by using the appropriate trunk interface names.
Configuring a Redundant Trunk Group and Disabling the Spanning Tree Protocol for the Trunk Interfaces
Step-by-Step Procedure
This procedure explains how to configure a redundant trunk group and disable the Rapid Spanning Tree Protocol (RSTP) on the trunk interfaces.
Configure the trunk interfaces as a redundant trunk group.
This example configures the
xe-0/1/0.0andxe-0/1/2.0trunk interfaces in a redundant trunk group namedrtgroup1.Include the
interfacestatement at the[edit ethernet-switching-options redundant-trunk-group group rtgroup1]hierarchy level and specify each trunk interface name.Include the
primarystatement at the[edit ethernet-switching-options redundant-trunk-group group rtgroup1 xe-0/1/2.0]hierarchy level.[edit ethernet-switching-options redundant-trunk-group group rtgroup1] user@ex# set interface xe-0/1/0.0 user@ex# set interface xe-0/1/2.0 primary
Repeat this step for every redundant trunk group by using the appropriate interface names.
Disable RSTP on the trunk interfaces.
On an EX Series device, RSTP is enabled by default. RSTP cannot be enabled on the same interface as routing.
This example disables RSTP on the
xe-0/1/0.0andxe-0/1/2.0trunk interfaces.Include the
disablestatement at the[edit protocols rstp interface xe-0/1/0.0]and[edit protocols rstp interface xe-0/1/2.0]hierarchy levels.[edit protocols rstp] user@ex# set interface xe-0/1/0.0 disable user@ex# set interface xe-0/1/2.0 disable
Repeat this step for every core-facing trunk interface by using the appropriate interface name.
Configuring Management Automation
Step-by-Step Procedure
This procedure explains how to configure static routes to the management network, a known host to support background Secure Copy Protocol (SCP) file transfers, a commit script, and an event archive site.
Configure static routes so the Ethernet management interface can reach the management network.
Include the
routestatement, and specify10.8.0.0/16as the IPv4 subnet address of the management network at the[edit routing-options static]hierarchy level.Include the
next-hopstatement, and specify the IPv4 host address of the next-hop router at the[edit routing-options static route 10.8.0.0/16]hierarchy level.[edit routing-options static] user@ex# set route 10.8.0.0/16 next-hop 10.8.108.254
Repeat this step for every Ethernet management interface on the EX Series devices.
Configure an SSH known host.
Include the
hoststatement, and specify the IPv4 address and RSA host key options for trusted servers at the[edit security ssh-known-hosts]hierarchy level. In this example, the RSA host key is truncated to make it easier to read.[edit security ssh-known-hosts] user@ex# set host 127.0.0.1 rsa-key AAAAB3NzaC1yc2
Repeat this step for every EX Series device.
Configure outbound SSH to support Juniper Message Bundle (JMB) transfers to Juniper Support Systems (JSS).
In this example, the client ID is configured as
00187D0B670D.Include the
clientstatement, specify00187D0B670Das the client ID, and specify10.8.7.32as the IPv4 address at the[edit system services outbound-ssh]hierarchy level.Include the
portstatement and specify7804as the TCP port at the[edit system services outbound-ssh client 00187D0B670D 10.8.7.32]hierarchy level.Include the
device-idstatement and specifyFA022Das the device ID at the[edit system services outbound-ssh client 00187D0B670D]hierarchy level.Include the
secretstatement at the[edit system services outbound-ssh client 00187D0B670D ]hierarchy level.Include the
servicesstatement and specifynetconfas the available service at the[edit system services outbound-ssh client 00187D0B670D ]hierarchy level.[edit system services outbound-ssh client 00187D0B670D] user@ex# set 10.8.7.32 port 7804 user@ex# set device-id FA022D user@ex# set secret "$ABC123" user@ex# set services netconf
Repeat this step for every EX Series device.
Configure a commit script.
In this example the script file name is
jais-activate-scripts.slax.Include the
allow-transientsstatement at the[edit system scripts commit]hierarchy level.Include the
optionalstatement at the[edit system scripts commit file jais-activate-scripts.slax]hierarchy level.[edit system scripts commit] user@ex# set allow-transients user@ex# set file jais-activate-scripts.slax optional
Repeat this step for every EX Series devices.
Configure an event archive site.
In this example, the archive URL is the local
/var/tmp/directory, and the name given to the destination isjuniper-aim.Include the
archive-sitesstatement and specify the archive URL at the[edit event-options destinations juniper-aim]hierarchy level.[edit event-options destinations juniper-aim] user@ex# set archive-sites "scp://admin@127.0.0.1://var/tmp" password “12345”
Repeat this step for every EX Series device.
Configuring the Aggregation Layer in the Trusted Logical Systems
Configure the aggregation layer by doing the following:
- Configuring Interfaces in the Trusted Logical Systems
- Configuring VLANs in the Aggregation Layer
- Configuring the Virtual Router Routing Instance
- Configuring Management Interfaces
- Configuring Logical System Administrator Accounts
- Configuring Management Automation
Configuring Interfaces in the Trusted Logical Systems
Step-by-Step Procedure
This procedure explains how to configure the physical, logical, and Layer 3 routing interfaces for the logical system in the trusted security zone of the aggregation layer. This procedure shows a representative sample of the configuration. The example does not show the configuration for every interface.
Enable flexible VLAN tagging on the physical interfaces.
This example configures physical interface
xe-1/0/0.Include the
encapsulationstatement and specify theflexible-ethernet-servicesoption at the[edit interfaces xe-1/0/0]hierarchy level.Include the
flexible-vlan-taggingstatement at the[edit interfaces xe-1/0/0]hierarchy level.[edit interfaces xe-1/0/0] user@mx# set encapsulation flexible-ethernet-services user@mx# set flexible-vlan-tagging
Repeat this step for every physical interface connected to the EX series, SRX Series, and MX Series devices using the appropriate interface name.
-
Configure the 10-Gigabit Ethernet interfaces connected to the EX Series access layer device.
This example configures logical interface
17on thexe-1/0/0interface under the logical system namedTrust1.Include the
encapsulationstatement and specify thevlan-bridgeoption at the[edit logical-systems Trust1 interfaces xe-1/0/0 unit 17]hierarchy level.Include the
vlan-idstatement and specify17as the VLAN ID at the[edit logical-systems Trust1 interfaces xe-1/0/0 unit 17]hierarchy level.[edit logical-systems Trust1 interfaces xe-1/0/0 unit 17] user@mx# set encapsulation vlan-bridge user@mx# set vlan-id 17
Repeat this step for every interface connected to the access layer devices by using the appropriate interface name, logical interface number, VLAN ID, and logical system name.
-
Configure the 10-Gigabit Ethernet interfaces connected to the other MX Series device shown in Figure 1.
This example configures logical interface
17on thexe-0/1/0interface.Include the
encapsulationstatement and specify thevlan-bridgeoption at the[edit logical-systems Trust1 interfaces xe-0/1/0 unit 17]hierarchy level.Include the
vlan-idstatement and specify17as the VLAN tag ID at the[edit logical-systems Trust1 interfaces xe-0/1/0 unit 17]hierarchy level.[edit logical-systems Trust1 interfaces xe-0/1/0 unit 17] user@mx# set encapsulation vlan-bridge user@mx# set vlan-id 17
Repeat this step for every interface connected to the other MX Series device shown in Figure 1 by using the appropriate interface name, logical interface number, VLAN ID, and logical system name.
-
Configure the 10-Gigabit Ethernet interface connected to the SRX Series Firewall.
This example configures logical interface
15on thexe-1/1/0interface. Include theencapsulationstatement and specify thevlan-bridgeoption at the[edit logical-systems Trust1 interfaces xe-1/1/0 unit 15]hierarchy level.Include the
vlan-idstatement and specify15as the VLAN tag ID at the[edit logical-systems Trust1 interfaces xe-1/1/0 unit 15]hierarchy level.[edit logical-systems Trust1 interfaces xe-1/1/0 unit 15] user@mx# set encapsulation vlan-bridge user@mx# set vlan-id 15
Repeat this step for every interface connected to the SRX Series Firewall by using the appropriate interface name, logical interface number, VLAN ID, and logical system name.
-
Configure the Layer 3 integrated routing and bridging (IRB) interface address.
This example configures the
unit 17logical interface with10.17.2.2/24as the IPv4 address under the logical system namedTrust1. Include theaddressstatement and specify10.17.2.2/24as the IPv4 address at the[edit logical-systems Trust1 interfaces irb unit 17 family inet]hierarchy level.[edit logical-systems Trust1 interfaces irb unit 17 family inet] user@mx# set address 10.17.2.2/24
Repeat this step for every Layer 3 IBR by using the appropriate logical interface name and IPv4 address.
Configure the IRB interface to participate in Virtual Router Redundancy Protocol (VRRP).
This example configures the
unit 17logical interface with17as the VRRP group name.Include the
virtual-addressstatement and specify10.17.2.1as the IPv4 address of the virtual router at the[edit logical-systems Trust1 interfaces irb unit 17 family inet address 10.17.2.2/24 vrrp-group 17]hierarchy level.Include the
accept-datastatement at the[edit logical-systems Trust1 interfaces irb unit 17 family inet address 10.17.2.2/24 vrrp-group 17]hierarchy level so the interface will accept packets destined for the virtual IP address.Include the
prioritystatement and specify200as the router’s priority at the[edit logical-systems Trust1 interfaces irb unit 17 family inet address 10.17.2.2/24 vrrp-group 17]hierarchy level.Include the
fast-intervalstatement and specify200as the interval between VRRP advertisements at the[edit logical-systems Trust1 interfaces irb unit 17 family inet address 10.17.2.2/24 vrrp-group 17]hierarchy level.Include the
preemptstatement at the[edit logical-systems Trust1 interfaces irb unit 17 family inet address 10.17.2.2/24 vrrp-group 17]hierarchy level.[edit logical-systems Trust1 interfaces irb unit 17 family inet address 10.17.2.2/24 vrrp-group 17] user@mx# set virtual-address 10.17.2.1 user@mx# set accept-data user@mx# set priority 200 user@mx# set fast-interval 200 user@mx# set preempt
Repeat this step for every Layer 3 IBR interface by using the appropriate logical interface name, IPv4 address, VRRP group name, and priority.
Configuring VLANs in the Aggregation Layer
Step-by-Step Procedure
This procedure explains how to configure the VLAN names and tag IDs and associate trunk interfaces and Layer 3 routing interfaces with each VLAN. This procedure shows a representative sample of the configuration. The example does not show the configuration for every VLAN.
-
Configure the VLAN name and tag ID (number) for each VLAN on the MX Series device.
This example configures a VLAN with the name
vlan17and tag ID17in the Logical SystemTrust1. Include thevlan-idstatement and specify17as the VLAN ID at the[edit logical-systems Trust1 bridge-domains vlan17]hierarchy level.[edit logical-systems Trust1 bridge-domains vlan17] user@mx# set vlan-id 17
Repeat this step for every VLAN on each MX Series device by using the appropriate VLAN names and tag IDs.
-
Associate the logical trunk interfaces with each VLAN on the MX Series device.
This example associates logical interface
xe-1/0/0.17that is connected to the EX Series device and logical interfacexe-0/1/0.17that is connected to the other MX Series device withvlan17.Include the
interfacestatement and specifyxe-1/0/0.17at the[edit logical-systems Trust1 bridge-domains vlan17]hierarchy level.Include the
interfacestatement and specifyxe-0/1/0.17at the[edit logical-systems Trust1 bridge-domains vlan17]hierarchy level.[edit logical-systems Trust1 bridge-domains vlan17] user@mx# set interface xe-1/0/0.17 user@mx# set interface xe-0/1/0.17
Repeat this step for every server-facing VLAN on each MX Series device by using the appropriate trunk interface names.
Associate a Layer 3 interface with each VLAN on the MX Series device.
This example associates the
irb.17interface withvlan17.Include the
routing-interfacestatement and specifyirb.17at the[edit logical-systems Trust1 bridge-domains vlan17]hierarchy level.[edit logical-systems Trust1 bridge-domains vlan17] user@mx# set routing-interface irb.17
Repeat this step for every server-facing VLAN on each MX Series device by using the appropriate Layer 3 interface name.
-
Associate the logical interfaces with each interconnection VLAN on the MX Series device.
This example associates logical interface
xe-1/1/0.15that is connected to the SRX Series Firewall and logical interfacexe-0/1/0.15that is connected to the other MX Series device withvlan15.Include the
interfacestatement and specifyxe-1/1/0.15at the[edit logical-systems Trust1 bridge-domains vlan15]hierarchy level.Include the
interfacestatement and specifyxe-0/1/0.15at the[edit logical-systems Trust1 bridge-domains vlan15]hierarchy level.[edit logical-systems Trust1 bridge-domains vlan15] user@mx# set interface xe-1/1/0.15 user@mx# set interface xe-0/1/0.15
Repeat this step for every interconnect VLAN on each MX Series device by using the appropriate interconnect interface names.
Associate a Layer 3 interface with each interconnection VLAN on the MX Series device to support active participation in the OSPF protocol.
This example associates the
irb.15interface withvlan15.Include the
routing-interfacestatement and specifyirb.15at the[edit logical-systems Trust1 bridge-domains vlan15]hierarchy level.[edit logical-systems Trust1 bridge-domains vlan15] user@mx# set routing-interface irb.15
Repeat this step for every server-facing VLAN on each MX Series device by using the appropriate Layer 3 interface name.
Configuring the Virtual Router Routing Instance
Step-by-Step Procedure
This procedure explains how to configure a single virtual router routing instance. This procedure shows a representative sample of the example configuration. The example does not show the configuration for every device.
Configure the routing instance type.
This example configures the routing instance with the name
MX-VR2. Include theinstance-typestatement and specifyvirtual-routeras the type at the[edit logical-systems Trust1 routing-instances MX-VR2]hierarchy level.[edit logical-systems Trust1 routing-instances MX-VR2] user@mx# set instance-type virtual-router
Repeat this step for every virtual router in each MX Series device by using the appropriate virtual router name.
Add the IRB interfaces used by the virtual router routing instance.
Include the
interfacestatement and specify the name of each IRB interface at the[edit routing-instances MX-VR2]hierarchy level.[edit logical-systems Trust1 routing-instances MX-VR2] user@mx# set interface irb.15 user@mx# set interface irb.16 user@mx# set interface irb.17 user@mx# set interface irb.18 user@mx# set interface irb.1002
Repeat this step for every virtual router in each MX Series device by using the appropriate interface names.
Configure the IGP protocol active interface used by the virtual router routing instance so the routing tables can be populated with the routes to the servers.
This example configures one IRB interface to actively participate in the OSPF protocol area
0.0.0.0.Include the
interfacestatement and specify the name of the IRB interface at the[edit logical-systems Trust1 routing-instances MX-VR2 protocols ospf area 0.0.0.0]hierarchy level.[edit routing-instances MX-VR2 protocols ospf area 0.0.0.0] user@mx# set interface irb.15
Repeat this step for every virtual router in each MX Series device by using the appropriate virtual router name.
Configure the interior gateway protocol passive interfaces that are associated with each VLAN within the virtual router routing instance.
This example configures the IRB interfaces to passively participate in the OSPF protocol area
0.0.0.0.Include the
passivestatement at the[edit logical-systems Trust1 routing-instances MX-VR2 protocols ospf area 0.0.0.0 interface irb-name]hierarchy level.[edit logical-systems Trust1 routing-instances MX-VR2 protocols ospf area 0.0.0.0] user@mx# set interface irb.16 passive user@mx# set interface irb.17 passive user@mx# set interface irb.18 passive user@mx# set interface irb.1002 passive
Repeat this step for every virtual router in each MX Series device by using the appropriate virtual router name.
Configure the logical system router identifier.
Include the
router-idstatement and specify10.200.11.101as the router identifier at the[edit logical-systems Trust1 routing-instances MX-VR2 routing-options]hierarchy level.[edit logical-systems Trust1 routing-instances MX-VR2 routing-options] user@mx# set router-id 10.200.11.101
Repeat this step for every virtual router in each MX Series device by using the appropriate router identifier.
Configuring Management Interfaces
Step-by-Step Procedure
This procedure explains how to configure static routes to the management network and the IPv4 address family for the loopback logical interface. This procedure shows a representative sample of the configuration. The example does not show the configuration for every interface.
Configure static routes so the Ethernet management interface can reach the management network.
Include the
routestatement and specify10.0.0.0/8as the IPv4 subnet address of the management network at the[edit routing-options static]hierarchy level.Include the
next-hopstatement, and specify the IPv4 host address of the next-hop router at the[edit routing-options static route 10.0.0.0/8]hierarchy level.Include the
retainandno-readvertisestatements at the[edit routing-options static route 10.0.0.0/8]hierarchy level.[edit routing-options static] user@mx# set route 10.0.0.0/8 next-hop 10.8.3.254 user@mx# set route 10.0.0.0/8 retain user@mx# set route 10.0.0.0/8 no-readvertise
Repeat this step for every MX Series device.
Configure the MX Series device management Ethernet interface. This example configures the
unit 0logical interface.Include the
familystatement and specify theinetoption at the[edit fxp0 unit 0]hierarchy level.Include the
addressstatement and specify10.8.3.212/24as the IPv4 address at the[edit interfaces fxp0 unit 0]hierarchy level.[edit interfaces fxp0 unit 0] user@mx# set family inet address 10.8.3.212/24
Repeat this step for every MX Series device by using the appropriate management interface address for that device.
Configure the loopback logical interface.
Include the
familystatement and specify theinetoption at the[edit interfaces lo0 unit 0]hierarchy level.[edit interfaces lo0 unit 0] user@mx# set family inet
Repeat this step for every MX Series device.
Configuring Logical System Administrator Accounts
Step-by-Step Procedure
This procedure explains how to configure administrator account classes that are confined to the context of the logical system to which they are assigned and administrator accounts for each logical system.
Create administrator account classes.
In this example, the
trust1-adminuser class is created withallpermissions for theTrust1logical system.Include the
classstatement and specifytrust1-adminas the class name at the[edit system login]hierarchy level.Include the
logical-systemstatement and specifyTrust1as the logical system name at the[edit system login class trust1-admin]hierarchy level.Include the
permissionsstatement and specify thealloption at the[edit system login class trust1-admin]hierarchy level.[edit system] user@mx# set login class trust1-admin logical-system Trust1 user@mx# set login class trust1-admin permissions all
Repeat this step for the trust2-admin and untrust-admin classes on each MX Series device by using the appropriate logical-system name.
Create administrator accounts that correspond to each logical system in the MX Series device.
In this example, the
trust1user account is created and assigned thetrust1-adminclass.Include the
classstatement and specifytrust1-adminas the user class at the[edit system login user trust1]hierarchy level.Include the
encrypted-passwordstatement and enter the encrypted password string at the[edit system login user trust1 authentication]hierarchy level.[edit system] user@mx# set login user trust1 class trust1-admin user@mx# set login user trust1 authentication encrypted-password 12345
Repeat this step for the trust2 and untrust user accounts on each MX Series device.
Configuring Management Automation
Step-by-Step Procedure
This procedure explains how to configure a known host to support background SCP file transfers, a commit script, and an archive site.
Configure a commit script.
In this example, the script file name is
jais-activate-scripts.slax.Include the
allow-transientsstatement at the[edit system scripts commit]hierarchy level.Include the
optionalstatement at the[edit system scripts commit file jais-activate-scripts.slax]hierarchy level.[edit system scripts commit] user@mx# set allow-transients user@mx# set file jais-activate-scripts.slax optional
Configure an event archive site.
In this example the archive URL is the local
/var/tmp/directory, and the name given to the destination isjuniper-aim.Include the
archive-sitesstatement and specify the archive URL at the[edit event-options destinations juniper-aim]hierarchy level.[edit event-options destinations juniper-aim] user@mx# set archive-sites "scp://admin@127.0.0.1://var/tmp" password “12345”
Configuring the Core Layer in the Untrusted Logical Systems
Configure the core layer by doing the following:
- Configuring Interfaces in the Untrusted Logical Systems
- Configuring VLANs in the Core Layer
- Configuring Protocols in the Untrusted Logical System
Configuring Interfaces in the Untrusted Logical Systems
Step-by-Step Procedure
This procedure explains how to configure the physical, logical, and Layer 3 routing interfaces for the logical system in the untrusted security zone of the core layer. This procedure shows a representative sample of the configuration. The example does not show the configuration for every interface.
-
Configure the 10-Gigabit redundant Ethernet interfaces connected to the other MX Series device shown in Figure 1.
This example configures logical interface
19on thexe-0/3/0interface under the logical system namedUntrustto participate in VLAN 19. Include theencapsulationstatement and specify thevlan-bridgeoption at the[edit logical-systems Untrust interfaces xe-0/3/0 unit 19]hierarchy level.Include the
vlan-idstatement and specify19as the VLAN tag ID at the[edit logical-systems Untrust interfaces xe-0/3/0 unit 19]hierarchy level.[edit logical-systems Untrust interfaces xe-0/3/0 unit 19] user@mx# set encapsulation vlan-bridge user@mx# set vlan-id 19
Repeat this step for every redundant Ethernet interface connected to the other MX Series device by using the appropriate interface name, logical interface number, VLAN ID, and logical system name.
-
Configure the 10-Gigabit Ethernet interfaces connected to the SRX Series Firewall.
This example configures logical interface
19on thexe-2/2/0interface under the logical system namedUntrustto participate in VLAN 19.Include the
encapsulationstatement and specify thevlan-bridgeoption at the[edit logical-systems Untrust interfaces xe-2/2/0 unit 19]hierarchy level.Include the
vlan-idstatement and specify19as the VLAN tag ID at the[edit logical-systems Untrust interfaces xe-2/2/0 unit 19]hierarchy level.[edit logical-systems Untrust interfaces xe-2/2/0 unit 19] user@mx# set encapsulation vlan-bridge user@mx# set vlan-id 19
Repeat this step for every redundant Ethernet interface connected to the SRX Series Firewall by using the appropriate interface name, logical interface number, VLAN ID, and logical system name.
Configure the 10-Gigabit Ethernet interfaces connected to the IP-based/MPLS-based core network.
This example configures logical interface
0on thexe-1/3/0interface under the logical system namedUntrust.Include the
addressstatement and specify10.200.4.1/30as the IPv4 address at the[edit logical-systems Untrust interfaces xe-1/3/0 unit 0 family inet]hierarchy level.Include the
familystatement and specify themplsoption at the[edit logical-systems Untrust interfaces xe-1/3/0 unit 0]hierarchy level.[edit logical-systems Untrust interfaces xe-1/3/0 unit 0] user@mx# set family inet address 10.200.4.1/30 user@mx# set family mpls
Repeat this step for every 10-Gigabit Ethernet interface connected to the service provider network by using the appropriate interface name, logical interface number, IPv4 address, and logical system name.
Configure the Layer 3 IRB interface address.
This example configures the
unit 19logical interface that participates in VLAN 19 with10.19.2.1/24as the IPv4 address under the logical system namedUntrust.Include the
addressstatement and specify10.19.2.1/24as the IPv4 address at the[edit logical-systems Untrust interfaces irb unit 19 family inet]hierarchy level.[edit logical-systems Untrust interfaces irb unit 19 family inet] user@mx# set address 10.19.2.1/24
Repeat this step for every Layer 3 IRB interface by using the appropriate logical interface name and IPv4 address.
Configure an IP address for the loopback logical interface of the Logical System
Untrust.Include the
addressstatement and specify10.200.11.1/32as the IPv4 address at the[edit logical-systems Untrust interfaces lo0 unit 1 family inet]hierarchy level.[edit logical-systems Untrust interfaces lo0 unit 1 family inet] user@mx# set address 10.200.11.1/32
Repeat this step for every MX Series device by using the appropriate IPv4 address.
Configuring VLANs in the Core Layer
Step-by-Step Procedure
This procedure explains how to configure the VLAN names and tag IDs and associate interfaces and Layer 3 routing interfaces with each core interconnect VLAN. This procedure shows a representative sample of the configuration. The example does not show the configuration for every VLAN.
Configure the VLAN name and tag ID (number) for each core interconnect VLAN on the MX Series device.
This example configures a VLAN with the name
vlan14and tag ID14in the Logical SystemUntrust.Include the
vlan-idstatement and specify14as the VLAN ID at the[edit logical-systems Untrust bridge-domains vlan14]hierarchy level.[edit logical-systems Untrust bridge-domains vlan14] user@mx# set vlan-id 14
Repeat this step for every VLAN on each MX Series device by using the appropriate VLAN names and tag IDs.
-
Associate the logical interfaces with each VLAN on the MX Series device.
This example associates logical interface
xe-0/3/0.14that is connected to the other MX Series device andxe-2/2/0.14that is connected to the SRX Series Firewall withvlan14.Include the
interfacestatement and specifyxe-0/3/0.14at the[edit logical-systems Untrust bridge-domains vlan14]hierarchy level.Include the
interfacestatement and specifyxe-2/2/0.14at the[edit logical-systems Untrust bridge-domains vlan14]hierarchy level.[edit logical-systems Untrust bridge-domains vlan14] user@mx# set interface xe-0/3/0.14 user@mx# set interface xe-2/2/0.14
Repeat this step for every core interconnect VLAN on each MX Series device by using the appropriate interface names.
Associate a Layer 3 interface with each VLAN on the MX Series device.
This example associates the
irb.14interface withvlan14.Include the
routing-interfacestatement and specifyirb.14at the[edit logical-systems Untrust bridge-domains vlan14]hierarchy level.[edit logical-systems Untrust bridge-domains vlan14] user@mx# set routing-interface irb.14
Repeat this step for every core interconnect VLAN on each MX Series device by using the appropriate Layer 3 interface name.
Configuring Protocols in the Untrusted Logical System
Step-by-Step Procedure
This procedure explains how to configure the BGP, MPLS, RSVP, and OSPF protocols for the Logical System Untrust. This procedure shows a representative sample of the configuration. The example does not show the configuration for every device.
Add interfaces to the OSPF protocol on the MX Series device.
This example adds logical interfaces
xe-1/3/0.0andlo0.1to the OSPF protocol used in the core network.Include the
interfacestatement and specify thexe-1/3/0.0andlo0.1interfaces at the[edit logical-systems Untrust protocols ospf area 0.0.0.0]hierarchy level.[edit logical-systems Untrust protocols ospf area 0.0.0.0] user@mx# set interface xe-1/3/0.0 user@mx# set interface lo0.1
Repeat this step for every 10-Gigabit Ethernet interface connected to the core layer devices by using the appropriate interface name.
Configure the Generic Router Encapsulation (GRE) tunnel.
This example enables a dynamic GRE tunnel named
GRE1.Include the
grestatement to specify the tunnel type at the[edit logical-systems Untrust routing-options dynamic-tunnel GRE1]hierarchy level.Include the
source-addressstatement and specify10.200.11.1as the IPv4 source address at the[edit logical-systems Untrust routing-options dynamic-tunnel GRE1]hierarchy level.Include the
destination-networksstatement and specify0.0.0.0/0as the destination prefix at the[edit logical-systems Untrust routing-options dynamic-tunnel GRE1]hierarchy level.[edit logical-systems Untrust routing-options dynamic-tunnel GRE1] user@mx# set source-address 10.200.11.1 user@mx# set gre user@mx# set destination-networks 0.0.0.0/0
Repeat this step for each MX Series device by using the appropriate source address.
Configure the Logical System local autonomous system number and router identifier.
Include the
autonomous-systemstatement and specify64500as the autonomous system number at the[edit logical-systems Untrust routing-options]hierarchy level.Include the
router-idstatement and specify10.200.11.101as the router identifier at the[edit logical-systems Untrust routing-options]hierarchy level.[edit logical-systems Untrust] user@mx# set routing-options autonomous-system 64500 user@mx# set routing-options router-id 10.200.11.101
Repeat this step for each MX Series device by using the appropriate router identifier and autonomous system number 64500.
Configure the internal BGP peer group.
Include the
typestatement and specify theinternaloption at the[edit logical-systems Untrust protocols bgp group int]hierarchy level.Include the
local-addressstatement and specify the router ID (10.200.11.1) of Logical System Untrust as the local address at the[edit logical-systems Untrust protocols bgp group int]hierarchy level.Include the
unicaststatement at the[edit logical-systems Untrust protocols bgp group int family inet]and[edit logical-systems Untrust protocols bgp group int family inet-vpn]hierarchy levels.Include the
local-asstatement and specify64500as the local autonomous system number at the[edit logical-systems Untrust protocols bgp group int]hierarchy level.Include the
peer-asstatement and specify64500as the peer autonomous system number at the[edit logical-systems Untrust protocols bgp group int]hierarchy level.Include the
neighborstatement and specify the neighbor IPv4 addresses at the[edit logical-systems Untrust protocols bgp group int]hierarchy level.The neighbor addresses are the router ID addresses of the other MX Series device in the local data center, MX Series devices in a remote data center, and routers located in the IP-based/MPLS-based core network.
[edit logical-systems Untrust protocols bgp group int] user@mx# set type internal user@mx# set local-address 10.200.11.1 user@mx# set family inet unicast user@mx# set family inet-vpn unicast user@mx# set local-as 64500 user@mx# set peer-as 64500 user@mx# set neighbor 10.200.11.2 user@mx# set neighbor 10.200.11.3 user@mx# set neighbor 10.200.11.4
Repeat this step for every MX Series device.
Add interfaces to the MPLS protocol used in the service provider core network.
This example adds the
xe-1/3/0.0andxe-2/3/0.0interfaces that are connected to the service provider core network.Include the
interfacestatement and specify thexe-1/3/0.0andxe-2/3/0.0interfaces at the[edit logical-systems Untrust protocols mpls]hierarchy level.[edit logical-systems Untrust protocols mpls] user@mx# set interface xe-1/3/0.0 user@mx# set interface xe-2/3/0.0
Repeat this step for every MX Series device.
Create an MPLS LSP to the router that is located in the MPLS-based core network.
This example creates an LSP named
to-core-router.Include the
tostatement and specify10.200.11.3as the IPv4 address of the core router at the[edit logical-systems Untrust protocols mpls label-switched-path to-core-router]hierarchy level.Include the
no-cspfstatement at the[edit logical-systems Untrust protocols mpls]hierarchy level.[edit logical-systems Untrust protocols mpls] user@mx# set label-switched-path to-core-router to 10.200.11.3 user@mx# set no-cspf
Repeat this step for every MX Series device.
Add interfaces to the RSVP protocol used in the MPLS-based core network.
Include the
interfacestatement and specify thexe-1/3/0.0andxe-2/3/0.0interfaces at the[edit logical-systems Untrust protocols rsvp]hierarchy level.[edit logical-systems Untrust protocols rsvp] user@mx# set interface xe-1/3/0.0 user@mx# set interface xe-2/3/0.0
Repeat this step for every MX Series device.
Configuring the Security Device
The following procedures explain how to configure the redundant Ethernet interfaces, node cluster, security zones, security policies, and routing policies for the trusted security zone of the access layer.
- Configuring the Redundant Ethernet Interface Link Aggregation Group
- Configuring the SRX Series Cluster
- Creating Security Zones and Configuring the In-Bound Traffic Policy Action
- Configuring the Security Zone Policies
- Creating the Routing Policies
- Configuring the Virtual Router Routing Instance
- Results
Configuring the Redundant Ethernet Interface Link Aggregation Group
Step-by-Step Procedure
This procedure explains how to configure the redundant Ethernet interface link aggregation group. This procedure shows a representative sample of the configuration. The example does not show the configuration for every interface.
-
Configure the number of aggregated Ethernet interfaces supported on the node.
This example enables support for two interfaces.
Include the
device-countstatement and specify2as the number of interfaces supported at the[edit chassis aggregated-devices ethernet]hierarchy level.[edit chassis aggregated-devices ethernet] user@srx# set device-count 2
Repeat this step for every SRX Series Firewall by using the appropriate device count.
Assign 10-Gigabit Ethernet child interfaces to the redundant Ethernet (reth) parent interface.
This example assigns the
xe-1/0/010-Gigabit Ethernet child interface to thereth1parent interface on Node0.Include the
redundant-parentstatement and specifyreth1as the parent interface at the[edit interfaces xe-1/0/0 gigether-options]hierarchy level.[edit interfaces xe-1/0/0 gigether-options] user@srx# set redundant-parent reth1
Repeat this step for every redundant Ethernet interface by using the appropriate interface name and redundant parent name.
Configure the redundant Ethernet parent interface options.
This example configures the
reth1redundant parent interface.Include the
redundancy-groupstatement and specify1as the group number at the[edit interfaces reth1 redundant-ether-options]hierarchy level.Include the
vlan-taggingstatement at the[edit interfaces reth1]hierarchy level.[edit interfaces reth1] user@srx# set redundant-ether-options redundancy-group 1 user@srx# set vlan-tagging
Repeat this step for every redundant parent interface by using the appropriate redundant parent name and redundancy group number.
Configure the redundant Ethernet parent logical interfaces.
This example configures the
unit 15logical interface.Include the
addressstatement and specify10.15.2.2/24as the IPv4 address at the[edit interfaces reth1 unit 15 family inet]hierarchy level.Include the
vlan-idstatement and specify15as the VLAN identifier at the[edit interfaces reth1 unit 15]hierarchy level.[edit interfaces reth1 unit 15] user@srx# set family inet address 10.15.2.2/24 user@srx# set vlan-id 15
Repeat this step for every redundant parent interface by using the appropriate redundant parent name, IPv4 address, and VLAN identifier.
Configuring the SRX Series Cluster
Step-by-Step Procedure
This procedure explains how to configure fabric connections between the nodes in the cluster. This procedure shows a representative sample of the configuration. The example does not show the configuration for every interface.
Configure the 10-Gigabit Ethernet interface to serve as the fabric between the cluster nodes.
This example configures
xe-1/0/1as the child fabric interface andfab0as the parent fabric interface. The connection is from SRX0 to SRX1.Include the
member-interfacesstatement and specify thexe-1/0/1interface at the[edit interfaces fab0 fabric-options]hierarchy level.[edit interfaces fab0 fabric-options] user@srx# set member-interfaces xe-1/0/1
Repeat this step for every 10-Gigabit Ethernet interface that is part of the cluster fabric by using the appropriate child interface name and parent interface name.
-
Configure the number of redundant Ethernet interfaces that the cluster supports.
This example configures
4as the number of interfaces.Include the
reth-countstatement and specify4as the number of interfaces at the[edit chassis cluster]hierarchy level.[edit chassis cluster] user@srx# set reth-count 4
Repeat this step for every SRX Series Firewall in the cluster.
-
Configure the node priority for the redundancy group to determine which node is primary and which is secondary.
This example configures
node 0with a higher priority.Include the
prioritystatement and specify200at the[edit chassis cluster redundancy-group 1 node 0]hierarchy level.Include the
prioritystatement and specify100at the[edit chassis cluster redundancy-group 1 node 1]hierarchy level.[edit chassis cluster redundancy-group 1] user@srx# set node 0 priority 200 user@srx# set node 1 priority 100
Repeat this step for every redundancy group on every SRX Series Firewall in the cluster.
-
Allow a node with a higher priority to initiate a failover to become the primary node for the redundancy group.
Include the
preemptstatement at the[edit chassis cluster redundancy-group 1]hierarchy level.[edit chassis cluster redundancy-group 1] user@srx# set preempt
Repeat this step for every redundancy group on every SRX Series Firewall in the cluster.
-
Enable control link recovery to be done automatically.
Include the
control-link-recoverystatement at the[edit chassis cluster]hierarchy level.[edit chassis cluster] user@srx# set control-link-recovery
Repeat this step for every redundancy group on every SRX Series Firewall in the cluster.
-
Enable interface monitoring to monitor the health of the interfaces and trigger redundancy group failover.
This example configures the
xe-1/0/0interface with a weight of255.Include the
weightstatement at the[edit chassis cluster redundancy-group 1 interface-monitor xe-1/0/0]hierarchy level.[edit chassis cluster redundancy-group 1 interface-monitor xe-1/0/0] user@srx# set weight 255
Repeat this step for every redundancy group interface on every SRX Series Firewall in the cluster.
Creating Security Zones and Configuring the In-Bound Traffic Policy Action
Step-by-Step Procedure
This procedure explains how to configure the trusted and untrusted security zones on the SRX Series Firewall. This procedure shows a representative sample of the configuration. The example does not show the configuration for every zone.
Assign a redundant Ethernet logical interface to a trusted zones.
This example assigns the
reth1.15interface to theTrust2zone.Include the
interfacesstatement and specifyreth1.15as the interface in the zone at the[edit security zones security-zone Trust2]hierarchy level.[edit security zones security-zone Trust2] user@srx# set interfaces reth1.15
Repeat this step for every trusted security zone by using the appropriate zone name and redundant Ethernet logical interface name.
Assign a redundant Ethernet logical interface to the untrusted zones.
This example assigns the
reth2.19interface to theUntrust2zone.Include the
interfacesstatement and specifyreth2.19as the interface in the zone at the[edit security zones security-zone Untrust2]hierarchy level.[edit security zones security-zone Untrust2] user@srx# set interfaces reth2.19
Repeat this step for every untrusted security zone by using the appropriate zone name and redundant Ethernet logical interface name.
-
Enable all inbound system services traffic in the trusted security zone.
This example enables all services for the
Trust2zone.Include the
system-servicesstatement and specify thealloption at the[edit security zones security-zone Trust2 host-inbound-traffic]hierarchy level.[edit security zones security-zone Trust2 host-inbound-traffic] user@srx# set system-services all
Repeat this step for every security zone on the SRX Series Firewall where system services are allowed.
-
Enable all protocols for inbound traffic in the trusted security zone.
This example enables all protocols for the
Trust2zone.Include the
protocolsstatement and specify thealloption at the[edit security zones security-zone Trust2 host-inbound-traffic]hierarchy level.[edit security zones security-zone Trust2 host-inbound-traffic] user@srx# set protocols all
Repeat this step for every security zone on the SRX Series Firewall where all protocols are allowed for inbound traffic.
Configuring the Security Zone Policies
Step-by-Step Procedure
This procedure explains how to configure the security zone policies on the SRX Series Firewall. This procedure shows a representative sample of the configuration. The example does not show the configuration for every policy.
Define which zone traffic is coming from and which zone traffic is going to for the policy being created.
This example defines the from zone as
Trust2and the to zone asUntrust2.On a single command line, include the
from-zonestatement and specifyTrust2, include theto-zonestatement and specifyUntrust2, include thepolicystatement and specifydenyftpas the policy name, and included thematchstatement at the[edit security policies]hierarchy level.[edit security policies] user@srx# set from-zone Trust2 to-zone Untrust2 policy denyftp match
Repeat this step for every policy that controls traffic between zones.
Configure the policy match criteria for denying traffic.
This example matches the Junos OS FTP application from any source to any destination address in a policy named
denyftp.Include the
source-addressstatement and specifyanyas the IPv4 address at the[edit security policies from-zone Trust2 to-zone Untrust2 policy denyftp match]hierarchy level.Include the
destination-addressstatement and specifyanyas the IPv4 address at the[edit security policies from-zone Trust2 to-zone Untrust2 policy denyftp match]hierarchy level.Include the
applicationstatement and specifyjunos-ftpas the application at the[edit security policies from-zone Trust2 to-zone Untrust2 policy denyftp match]hierarchy level.[edit security policies from-zone Trust2 to-zone Untrust2 policy denyftp match] user@srx# set source-address any user@srx# set destination-address any user@srx# set application junos-ftp
Repeat this step for every protocol matching policy by using the correct protocol.
Block specific applications from passing from the Trust2 zone to the Untrust2 zone.
This example denies the Junos OS FTP application from the
Trust2zone to theUntrust2zone.Include the
denystatement at the[edit security policies from-zone Trust2 to-zone Untrust2 policy denyftp then]hierarchy level.[edit security policies from-zone Trust2 to-zone Untrust2 policy denyftp then] user@srx# set deny
Repeat this step for every deny policy.
Configure the policy match criteria for allowing traffic.
This example matches any application from any source to any destination address in a policy named
allow_all.Include the
source-addressstatement and specifyanyas the IPv4 address at the[edit security policies from-zone Trust2 to-zone Untrust2 policy allow_all match]hierarchy level.Include the
destination-addressstatement and specifyanyas the IPv4 address at the[edit security policies from-zone Trust2 to-zone Untrust2 policy allow_all match]hierarchy level.Include the
applicationstatement and specifyanyas the application at the[edit security policies from-zone Trust2 to-zone Untrust2 policy allow_all match]hierarchy level.[edit security policies from-zone Trust2 to-zone Untrust2 policy allow_all match] user@srx# set source-address any user@srx# set destination-address any user@srx# set application any
Repeat this step for every application matching policy.
Permit any application traffic to pass from the Trust2 zone to the Untrust2 zone.
This example allows any application traffic from the
Trust2zone to theUntrust2zone.Include the
permitstatement at the[edit security policies from-zone Trust2 to-zone Untrust2 policy allow_all then]hierarchy level.[edit security policies from-zone Trust2 to-zone Untrust2 policy allow_all then] user@srx# set permit
Repeat this step for every permit policy.
Creating the Routing Policies
Step-by-Step Procedure
This procedure explains how to creates the routing policies on the SRX Series Firewall that can be applied to the appropriate routing instances. This procedure shows a representative sample of the configuration. The example does not show the configuration for every policy.
-
Create a policy to set the local preference for BGP routes to 120.
This example creates a policy named
local-pref-120that sets the BGP local preference value for received routes advertised by BGP to120.Include the
protocolstatement and specifybgpas the value at the[edit policy-options policy-statement local-pref-120 term term1 from]hierarchy level.Include the
local-preferencestatement and specify120as the value at the[edit policy-options policy-statement local-pref-120 term term1 then]hierarchy level.[edit policy-options policy-statement local-pref-120] user@srx# set term term1 from protocol bgp user@srx# set term term1 then local-preference 120
Repeat this step for each SRX Series Firewall.
-
Configure the match criteria for a policy named
default-ospfto accept all aggregate (generated) routes.Include the
protocolstatement and specifyaggregateas the protocol to match at the[edit policy-options policy-statement default-ospf term term1 from]hierarchy level.Include the
route-filterstatement and specify0.0.0.0/0 exactas the match criteria at the[edit policy-options policy-statement default-ospf term term1 from]hierarchy level.[edit policy-options policy-statement default-ospf term term1 from] user@srx# set protocol aggregate user@srx# set route-filter 0.0.0.0/0 exact
Repeat this step for each SRX Series Firewall.
-
Configure the action for a policy to set the metric to
0, and set the external route type to1.This example configures a policy named
default-ospfthat sets the metric to0, sets the external route to type1, and accepts aggregate routes into the routing table.Include the
metricstatement and specify0as the external type at the[edit policy-options policy-statement default-ospf term term1 then]hierarchy level.Include the
typestatement and specify1as the external route type at the[edit policy-options policy-statement default-ospf term term1 then external]hierarchy level.Include the
acceptstatement at the[edit policy-options policy-statement default-ospf term term1 then]hierarchy level.[edit policy-options policy-statement default-ospf term term1 then] user@srx# set metric 0 user@srx# set external type 1 user@srx# set accept
Repeat this step for each SRX Series Firewall.
-
Create a policy that accepts OSPF routes with specified prefixes.
This example creates a policy named
trust2-ebgp-outthat accepts OSPF routes with the route prefixes that correspond to the subnets for each trust VLAN.Include the
protocolstatement and specifyospfas the protocol at the[edit policy-options policy-statement trust2-ebgp-out term term1 from]hierarchy level.Include the
route-filterstatement and specify the VLAN subnet addresses and theexactmatch keyword at the[edit policy-options policy-statement trust2-ebgp-out term term1 from]hierarchy level.Include the
acceptstatement at the[edit policy-options policy-statement trust2-ebgp-out term term1 then]hierarchy level.[edit policy-options policy-statement trust2-ebgp-out term term1] user@srx# set from protocol ospf user@srx# set from route-filter 10.16.2.0/24 exact user@srx# set from route-filter 10.17.2.0/24 exact user@srx# set from route-filter 10.18.2.0/24 exact user@srx# set then accept
Repeat this step for each SRX Series Firewall.
-
Create a policy that accepts BGP routes if the route type is external.
This example creates a policy named
check-bgp-routesthat accepts BGP routes only if the route type is external.Include the
protocolstatement and specifybgpas the protocol at the[edit policy-options policy-statement check-bgp-routes term term1 from]hierarchy level.Include the
route-typestatement and specify theexternaloption at the[edit policy-options policy-statement check-bgp-routes term term1 from]hierarchy level.Include the
acceptstatement at the[edit policy-options policy-statement check-bgp-routes term term1 then]hierarchy level.[edit policy-options policy-statement check-bgp-routes term term1] user@srx# set from protocol bgp user@srx# set from route-type external user@srx# set then accept
Repeat this step for each SRX Series Firewall.
-
Create a policy that accepts routes from other virtual router routing instances.
This example creates a policy named
from_srx_vr1that accepts routes from routing instanceSRX-VR1.Include the
instancestatement and specifySRX-VR1as the routing instance name at the[edit policy-options policy-statement from_srx_vr1 term term1 from]hierarchy level.Include the
acceptstatement at the[edit policy-options policy-statement from_srx_vr1 term term1 then]hierarchy level.[edit policy-options policy-statement from_srx_vr1 term term1] user@srx# set from instance SRX-VR1 user@srx# set then accept
Repeat this step for each virtual router in each SRX Series Firewall.
Configuring the Virtual Router Routing Instance
Step-by-Step Procedure
This procedure explains how to configure a single virtual router routing instance. This procedure shows a representative sample of the example configuration. The example does not show the configuration for every virtual router routing instance.
-
Configure the routing instance type.
This example configures the routing instance with the name SRX-VR2.
Include the
instance-typestatement and specifyvirtual-routeras the type at the[edit routing-instances SRX-VR2]hierarchy level.[edit routing-instances SRX-VR2] user@srx# set instance-type virtual-router
Repeat this step for every virtual router in each SRX Series Firewall by using the appropriate virtual router name.
-
Add the redundant Ethernet interfaces used by the virtual router routing instance.
This example adds
reth1.15andreth2.19interfaces to theSRX-VR2routing instance.Include the
interfacestatement and specify the name of the redundant Ethernet interface at the[edit routing-instances SRX-VR2]hierarchy level.[edit routing-instances SRX-VR2] user@srx# set interface reth1.15 user@srx# set interface reth2.19
Repeat this step for every virtual router in each SRX Series Firewall by using the appropriate virtual router name and interface names.
-
Configure the routing options used by the virtual router routing instance.
This example configures the autonomous system number and enables the graceful restart feature on the
SRX-VR2routing instance.Include the
autonomous-systemstatement and specify65019as the autonomous system number at the[edit routing-instances SRX-VR2 routing-options]hierarchy level.Include the
graceful-restartstatement at the[edit routing-instances SRX-VR2 routing-options]hierarchy level.[edit routing-instances SRX-VR2 routing-options] user@srx# set autonomous-system 65019 user@srx# set graceful-restart
Repeat this step for every virtual router in each SRX Series Firewall by using the appropriate virtual router name and interface names.
-
Apply the routing policy that accepts external BGP routes and uses them as generated routes for the routing instance.
This example applies the policy named
check-bgp-routesto theSRX-VR2routing instance.Include the
policystatement and specifycheck-bgp-routesat the[edit routing-instances SRX-VR2 routing-options generate route 0.0.0.0/0]hierarchy level.Include the
graceful-restartstatement at the[edit routing-instances SRX-VR2 routing-options]hierarchy level.[edit routing-instances SRX-VR2 routing-options] user@srx# set generate route 0.0.0.0/0 policy user@srx# set graceful-restart
Repeat this step for every virtual router in each SRX Series Firewall by using the appropriate virtual router name and interface names.
-
Apply the routing policy that accepts routes from other routing instances.
This example applies the policy named
from_srx_vr1to theSRX-VR2routing instance.Include the
instance-importstatement and specifyfrom_srx_vr1at the[edit routing-instances SRX-VR2 routing-options]hierarchy level.[edit routing-instances SRX-VR2 routing-options] user@srx# set instance-import from_srx_vr1
Repeat this step for every virtual router in each SRX Series Firewall except the SRX-VR1 instance.
-
Configure the IGP protocol export policy used by the virtual router routing instance in the trusted security zone.
This example configures the
default-ospfpolicy.Include the
exportstatement and specifydefault-ospfas the policy name at the[edit routing-instances SRX-VR2 protocols ospf]hierarchy level.[edit routing-instances SRX-VR2 protocols ospf] user@srx# set export default-ospf
Repeat this step for every virtual router in each SRX Series Firewall by using the appropriate virtual router name and policy name.
-
Configure the IGP protocol active and passive interfaces used by the virtual router routing instance in the trusted security zone.
This example configures the
reth1.15redundant Ethernet interface to actively participate in the OSPF protocol area 0.0.0.0, and thereth2.19redundant Ethernet interface to passively participate.Include the
interfacestatement and specifyreth1.15at the[edit routing-instances SRX-VR2 protocols ospf area 0.0.0.0]hierarchy level.Include the
interfacestatement and specifyreth2.19at the[edit routing-instances SRX-VR2 protocols ospf area 0.0.0.0]hierarchy level.Include the
passivestatement at the[edit routing-instances SRX-VR2 protocols ospf area 0.0.0.0 reth2.19]hierarchy level.[edit routing-instances SRX-VR2 protocols ospf area 0.0.0.0] user@srx# set interface reth1.15 user@srx# set interface reth2.19 passive
Repeat this step for every virtual router in each SRX Series Firewall by using the appropriate virtual router name and interface names.
-
Configure the BGP protocol peer groups used by the virtual router routing instance in the untrusted security zone.
Include the
typestatement and specify theexternaloption at the[edit routing-instances SRX-VR2 protocols bgp group MX0-vrf]hierarchy level.Include the
peer-asstatement and specify64500as the peer autonomous system number at the[edit routing-instances SRX-VR2 protocols bgp group MX0-vrf]hierarchy level.Include the
neighborstatement and specify10.19.2.1as the IPv4 neighbor address at the[edit routing-instances SRX-VR2 protocols bgp group MX0-vrf]hierarchy level. The neighbor address is the IRB Logical interface address of the VRF routing instance on the MX Series device.[edit routing-instances SRX-VR2 protocols bgp group MX0-vrf] user@srx# set type external user@srx# set peer-as 64500 user@srx# set neighbor 10.19.2.1
Repeat this step for every virtual router in each SRX Series Firewall by using the appropriate virtual router name, instance type, neighbor address, and peer AS number.
-
Configure the BGP protocol peer groups export and import policies used by the virtual router routing instance in the untrusted security zone.
Include the
exportstatement and specifytrust2-ebgp-outas the export policy name at the[edit routing-instances SRX-VR2 protocols bgp group MX0-vrf]hierarchy level.Include the
importstatement and specifylocal-pref-120as the import policy name at the[edit routing-instances SRX-VR2 protocols bgp group MX0-vrf]hierarchy level.[edit routing-instances SRX-VR2 protocols bgp group MX0-vrf] user@srx# set export trust2-ebgp-out user@srx# set import local-pref-120
Repeat this step for every virtual router in each SRX Series Firewall by using the appropriate virtual router name, export policy, and import policy.
Results
The configuration steps of this example have been completed. The following section is for your reference.
The relevant sample configuration for the EX Series device follows.
EX Series Device
system {
scripts {
commit {
allow-transients;
file jais-activate-scripts.slax {
optional;
}
}
}
services {
ftp;
ssh;
telnet;
outbound-ssh {
client 00187D0B670D {
device-id FA022D;
secret "$ABC123"; ## SECRET-DATA
services netconf;
10.8.7.32 port 7804;
}
}
}
}
interfaces {
ge-0/0/17 {
unit 0 {
family ethernet-switching {
vlan {
members 17;
}
}
}
}
xe-0/1/0 {
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan {
members all;
}
}
}
}
xe-0/1/2 {
unit 0 {
enable;
family ethernet-switching {
port-mode trunk;
vlan {
members all;
}
}
}
}
lo0 {
unit 0 {
family inet {
address 127.0.0.1/32;
}
}
}
me0 {
unit 0 {
family inet {
address 10.8.108.19/24;
}
}
}
}
event-options {
destinations {
juniper-aim {
archive-sites {
"scp://admin@127.0.0.1://var/tmp" password "$ABC123"; ## SECRET-DATA
}
}
}
}
routing-options {
static {
route 10.8.0.0/16 next-hop 10.8.108.254;
}
}
protocols {
rstp {
interface xe-0/1/0.0 {
disable;
}
interface xe-0/1/2.0 {
disable;
}
}
}
security {
ssh-known-hosts {
host 127.0.0.1 {
rsa-key AAAAB3NzaC1yc2;
}
}
}
ethernet-switching-options {
redundant-trunk-group {
group rtgroup1 {
interface xe-0/1/0.0;
interface xe-0/1/2.0 {
primary;
}
}
}
}
vlans {
vlan17 {
vlan-id 17;
interface {
xe-0/1/0.0;
xe-0/1/2.0;
}
}
}
The relevant sample configuration for the MX Series device follows.
MX Series Device
groups {
re0 {
system {
host-name MX0;
}
}
re1 {
system {
host-name MX0re1;
}
}
}
apply-groups [re0 re1 ];
system {
scripts {
commit {
allow-transients;
file jais-activate-scripts.slax {
optional;
}
}
}
login {
class trust1-admin {
logical-system Trust1;
permissions all;
}
user trust1 {
uid 2000;
class trust1-admin;
authentication {
encrypted-password 12345; ## SECRET-DATA
}
}
}
}
logical-systems {
Trust1 {
interfaces {
xe-0/1/0 {
unit 17 {
encapsulation vlan-bridge;
vlan-id 17;
}
}
xe-1/0/0 {
unit 17 {
encapsulation vlan-bridge;
vlan-id 17;
}
}
xe-1/1/0 {
unit 15 {
encapsulation vlan-bridge;
vlan-id 15;
}
}
irb {
unit 15 {
family inet {
address 10.15.2.3/24;
}
}
unit 17 {
family inet {
address 10.17.2.2/24 {
vrrp-group 17 {
virtual-address 10.17.2.1;
priority 200;
fast-interval 200;
preempt;
accept-data;
}
}
}
}
}
}
routing-instances {
MX-VR2 {
instance-type virtual-router;
interface irb.15;
interface irb.16;
interface irb.17;
interface irb.18;
interface irb.1002;
protocols {
ospf {
area 0.0.0.0 {
interface irb.16 {
passive;
}
interface irb.17 {
passive;
}
interface irb.18 {
passive;
}
interface irb.1002 {
passive;
}
}
}
}
}
}
bridge-domains {
vlan15 {
vlan-id 15;
interface xe-1/1/0.15;
interface xe-0/1/0.15; ## 'xe-0/1/0.15' is not defined
routing-interface irb.15;
}
vlan17 {
vlan-id 17;
interface xe-1/0/0.17;
interface xe-0/1/0.17;
routing-interface irb.17;
}
}
}
Untrust {
interfaces {
xe-0/3/0 {
unit 19 {
encapsulation vlan-bridge;
vlan-id 19;
}
}
xe-1/3/0 {
unit 0 {
family inet {
address 10.200.4.1/30;
}
family mpls;
}
}
xe-2/2/0 {
unit 19 {
encapsulation vlan-bridge;
vlan-id 19;
}
}
irb {
unit 19 {
family inet {
address 10.19.2.1/24;
}
}
}
lo0 {
unit 1 {
family inet {
address 10.200.11.1/32;
}
}
}
}
protocols {
rsvp {
interface xe-1/3/0.0;
interface xe-2/3/0.0;
}
mpls {
no-cspf;
label-switched-path to-core-router {
to 10.200.11.3;
}
interface xe-1/3/0.0;
interface xe-2/3/0.0;
}
bgp {
group int {
type internal;
local-address 10.200.11.1;
family inet {
unicast;
}
family inet-vpn {
unicast;
}
peer-as 64500;
local-as 64500;
neighbor 10.200.11.2;
neighbor 10.200.11.3;
neighbor 10.200.11.4;
}
}
ospf {
area 0.0.0.0 {
interface xe-1/3/0.0;
interface lo0.1;
}
}
}
routing-options {
router-id 10.200.11.101;
autonomous-system 64500;
dynamic-tunnels {
GRE1 {
source-address 10.200.11.1;
gre;
destination-networks {
0.0.0.0/0;
}
}
}
}
bridge-domains {
vlan14 {
vlan-id 14;
interface xe-0/3/0.14;
interface xe-2/2/0.14;
routing-interface irb.14;
}
}
}
}
interfaces {
xe-0/1/0 {
flexible-vlan-tagging;
encapsulation flexible-ethernet-services;
}
xe-0/3/0 {
flexible-vlan-tagging;
encapsulation flexible-ethernet-services;
}
xe-1/0/0 {
flexible-vlan-tagging;
encapsulation flexible-ethernet-services;
}
xe-1/1/0 {
flexible-vlan-tagging;
encapsulation flexible-ethernet-services;
}
xe-2/2/0 {
flexible-vlan-tagging;
encapsulation flexible-ethernet-services;
}
fxp0 {
unit 0 {
family inet {
address 10.8.3.212/24;
}
}
}
lo0 {
unit 0 {
family inet;
}
}
}
event-options {
destinations {
juniper-aim {
archive-sites {
"scp://admin@127.0.0.1://var/tmp" password "$ABC123"; ## SECRET-DATA
}
}
}
}
routing-options {
static {
route 10.0.244.8/30 next-hop 10.0.134.10;
route 10.0.0.0/8 {
next-hop 10.8.3.254;
retain;
no-readvertise;
}
}
}
The relevant sample configuration for the SRX Series Firewall follows.
SRX Series Firewall
system {
host-name srx0;
chassis {
cluster {
control-link-recovery;
reth-count 4;
redundancy-group 1 {
node 0 priority 200;
node 1 priority 100;
preempt;
interface-monitor {
xe-1/0/0 weight 255;
}
}
}
}
}
interfaces {
xe-1/0/0 {
gigether-options {
redundant-parent reth1;
}
}
fab0 {
fabric-options {
member-interfaces {
xe-1/0/1;
}
}
}
lo0 {
unit 0 {
family inet {
address 127.0.0.1/32;
}
}
}
reth1 {
vlan-tagging;
redundant-ether-options {
redundancy-group 1;
}
unit 15 {
family inet {
address 10.15.2.2/24;
}
vlan-id 15;
}
}
}
policy-options {
policy-statement check-bgp-routes {
term term1 {
from {
protocol bgp;
route-type external;
}
then accept;
}
}
policy-statement default-ospf {
term term1 {
from {
protocol aggregate;
route-filter 0.0.0.0/0 exact;
}
then {
metric 0;
external {
type 1;
}
accept;
}
}
}
policy-statement from_srx_vr1 {
term term1 {
from instance SRX-VR1;
then accept;
}
}
policy-statement local-pref-120 {
term term1 {
from protocol bgp;
then {
local-preference 120;
}
}
}
policy-statement trust2-ebgp-out {
term term1 {
from {
protocol ospf;
route-filter 10.16.2.0/24 exact;
route-filter 10.17.2.0/24 exact;
route-filter 10.18.2.0/24 exact;
}
then accept;
}
}
}
security {
policies {
from-zone Trust2 to-zone Untrust2 {
policy denyftp {
match {
source-address any;
destination-address any;
application junos-ftp;
}
then {
deny;
}
}
policy allow_all {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone Trust2 {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth1.15;
}
}
security-zone Untrust2 {
interfaces reth2.19;
}
}
}
routing-instances {
SRX-VR2 {
instance-type virtual-router;
interface reth1.15;
interface reth2.19;
routing-options {
graceful-restart;
autonomous-system 65019;
instance-import from_srx_vr1;
}
protocols {
bgp {
group MX0-vrf {
import local-pref-120;
export trust2-ebgp-out;
}
}
ospf {
export default-ospf;
area 0.0.0.0 {
interface reth1.15;
interface reth2.19 {
passive;
}
}
}
}
}
}
