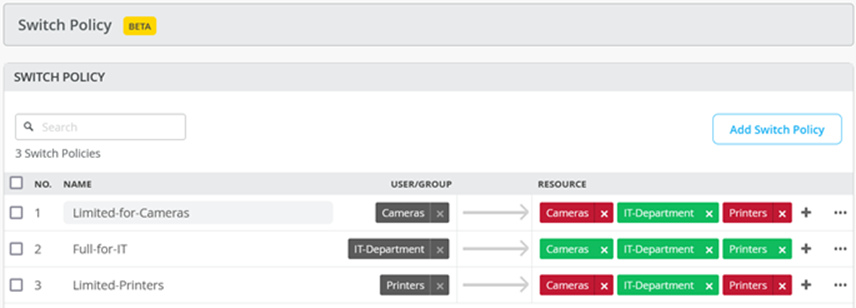
APPENDIX: Switch Template Configuration Examples
All configuration examples of this section are made in a switch template that is assigned to all switches. Switch templates can be configured via the Organization > Switch Templates tab of the Juniper Mist portal.

Third-Party RADIUS Server Configuration
At the beginning of the switch template, you can configure third-party RADIUS servers. The minimum items that must be configured are:
- Select Authentication Servers=
Radius - Add at least one new authentication server:
- Configure the hostname or IP address through which this RADIUS server responds to requests.
- Set a shared secret between the switch and the server to allow communication.
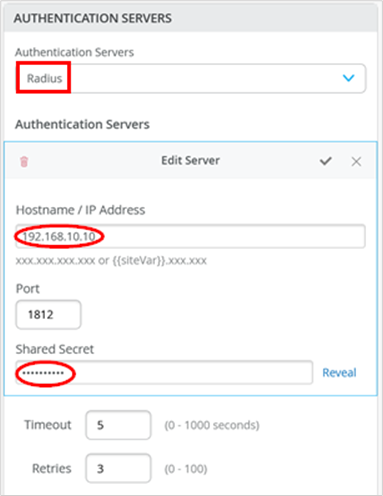
You must perform a similar process on the RADIUS server for each client. Configure the RADIUS server, the IP address of the client and the shared secret. Ensure you define the vendor-specific dictionary for the switch that acts as the RADIUS client.
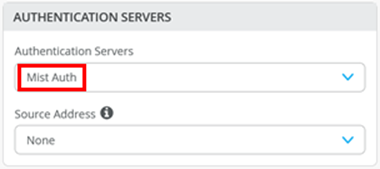
Mist Authentication Configuration
There is not much to configure if you intend to use Juniper Mist Access Assurance:
- Select as Authentication Servers=
Mist Auth
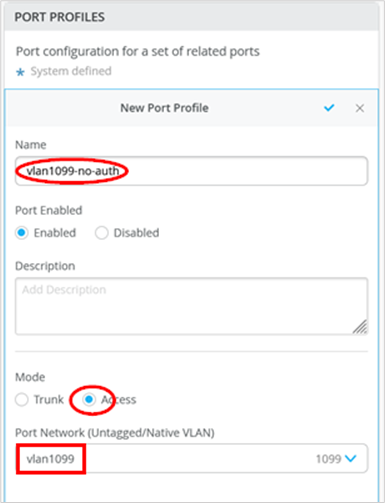
Port Profiles Used for Testing
The following port profiles were used during testing:
- All static GBP tag assignments used one without any special authentication:
- Port Profile Name=
vlan1099-no-auth - Mode=
Access - Port Network=
vlan1099
- Port Profile Name=
- All dynamic GBP tag assignments with 802.1X supplicants used:
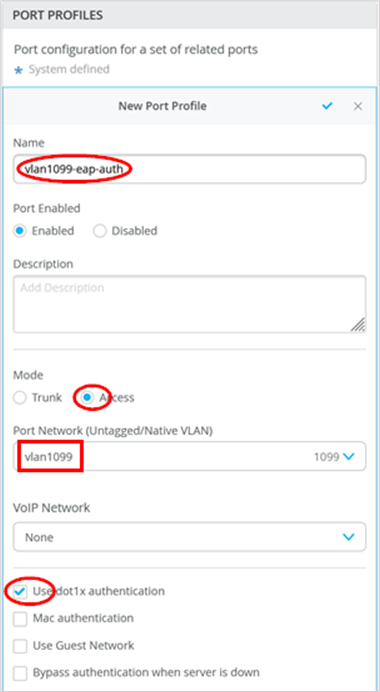
- Port Profile Name=
vlan1099-eap-auth - Mode=
Access - Port Network=
vlan1099 - Use dot1x authentication=
Enabled
- Port Profile Name=
- All dynamic GBP tag assignments via MAC address used:
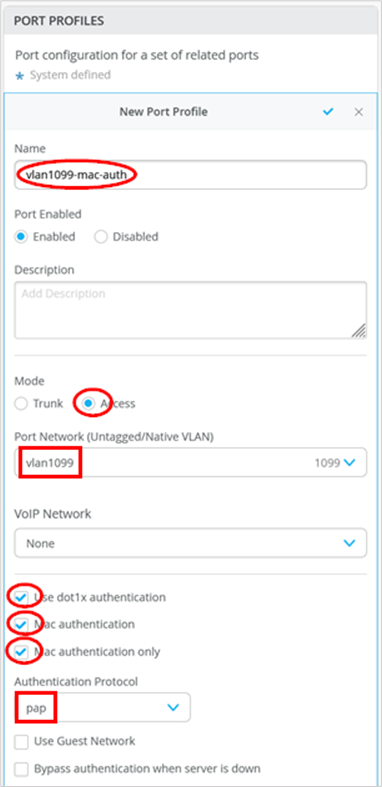
- Port Profile Name=
vlan1099-mac-auth - Mode=
access - Port Network=vlan1099
- Use dot1x authentication=
Enabled - Mac authentication=
Enabled - Mac authentication only=
EnabledThis prevents the switch from attempting an EAP-based authentication which would fail and cause 60 seconds of delay.
- Authentication Protocol=
papThis was easier to configure on the RADIUS server side.
- Port Profile Name=
- Finally, for the access point, we used the following port profile:
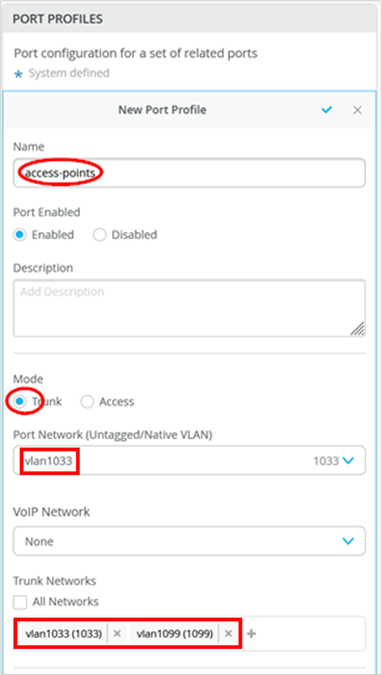
- Port Profile Name=
access-points - Mode=
Trunk - Port Network=
vlan1033 - Trunk Networks=
vlan1033andvlan1099
- Port Profile Name=
GBP Tag Assignments
We’ve used different GBP tag assignment configurations depending on the test cases.
Figure 2 shows a list of GBP tag assignments that were used for testing the RADIUS servers with MAB and 802.1X clients.
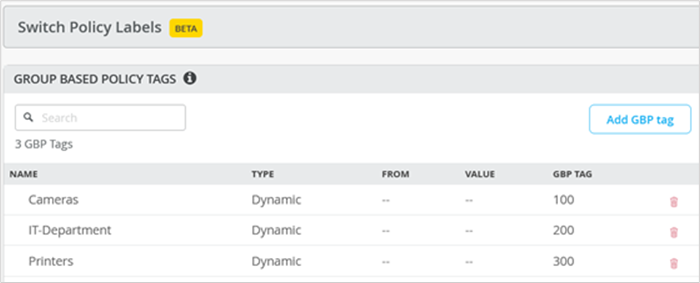
Figure 3 shows a list of GBP tag assignments that were used for testing static, IP address-based assignments.
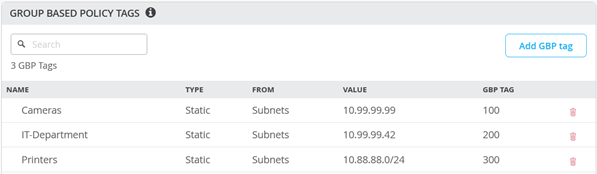
- For the entire GBP tag assignment testing, more permutations of static assignments were used but we do not list them here.
If you use VLAN ID-based (network-based) assignments and the access switch is an EX4100 Switch which cannot utilize those features, the Juniper Mist cloud will automatically filter out those invalid Junos OS commands, so they are not pushed to the switch. The remaining configuration stays intact as intended.
GBP Policy Assignments
Most of the time, the following matrix of SGT policy enforcements to block or allow traffic between GBP tags were used.